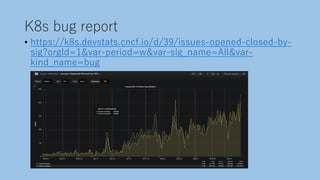
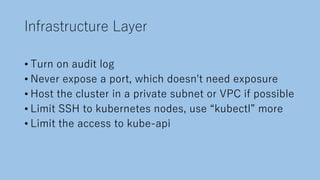
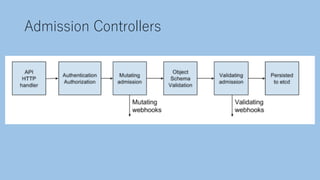
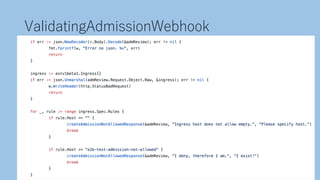
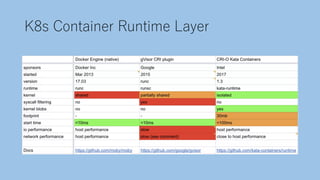
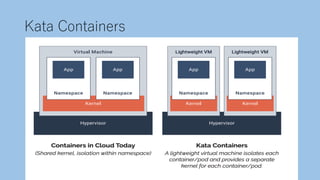
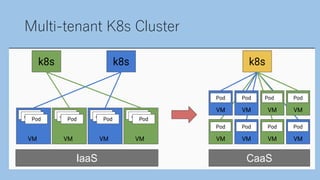
The document discusses securing a Kubernetes cluster from multiple layers of risk. It covers securing the infrastructure layer by limiting access and exposure, the control plane layer by enabling TLS and RBAC, the workload layer using pod security policies and network policies, the container runtime layer with tools like Kata Containers, the user misconfiguration layer by avoiding defaults and validating configurations, and useful security tools. The presenter then provides contact information for potential job opportunities.