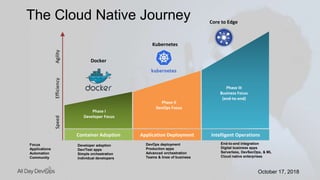
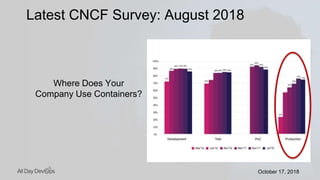
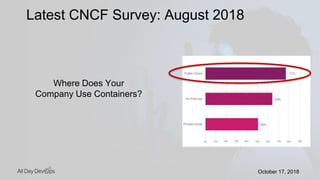
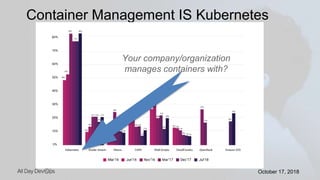
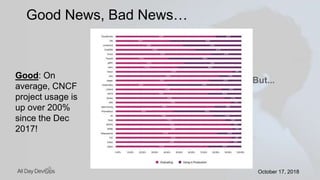
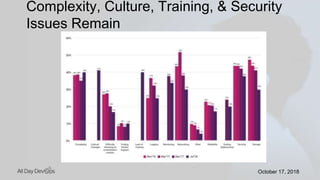
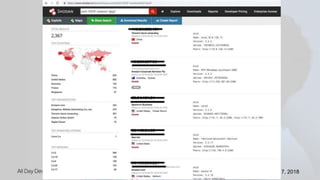
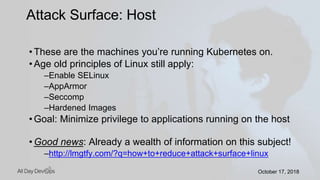
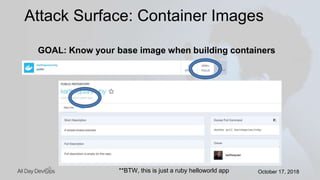
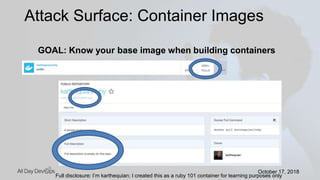
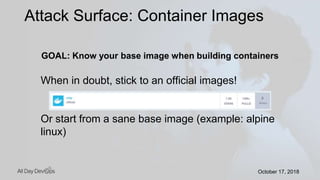
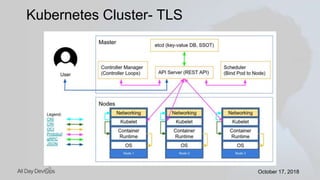
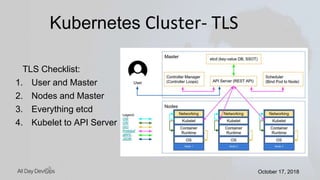
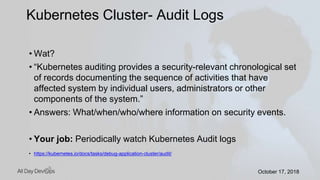
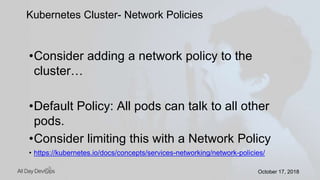
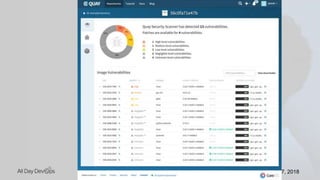
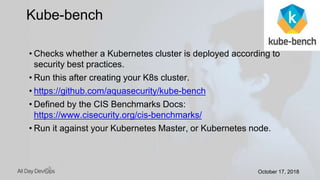
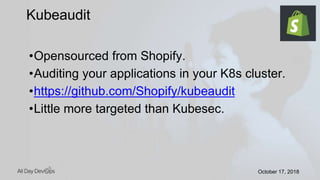
Karthik Gaekwad gave a presentation on securing Kubernetes clusters. He discussed reducing the attack surface by hardening hosts, using official container images with specific versions, limiting privileges, and periodically checking for vulnerabilities. He explained how Kubernetes features like TLS, authentication, authorization, auditing, network policies and pod security policies can help. Open source tools like Clair, Kube-bench, Kubesec and Kubeaudit were presented to analyze vulnerabilities and check configuration best practices. The overall message was to take a layered approach to security using the platform capabilities and tooling available.