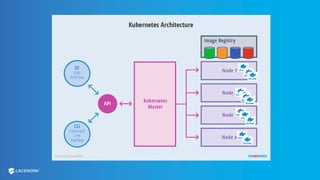
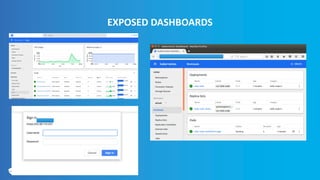
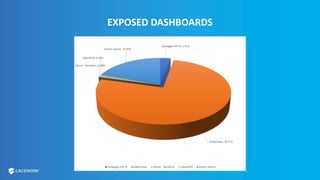
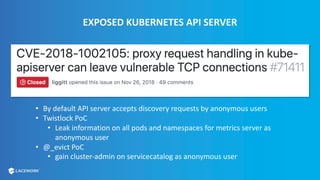
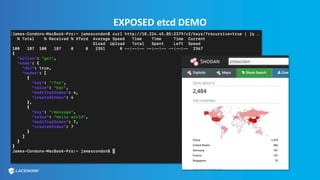
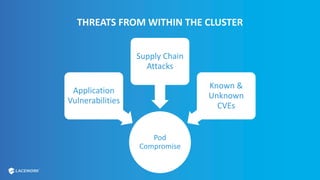
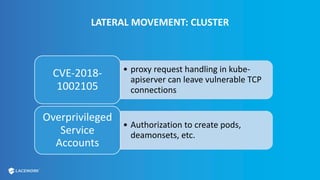
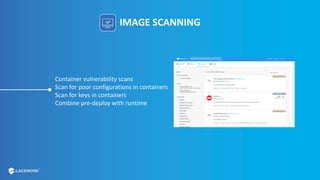
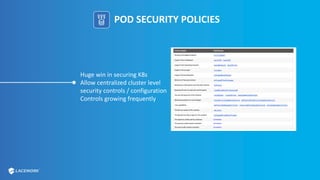
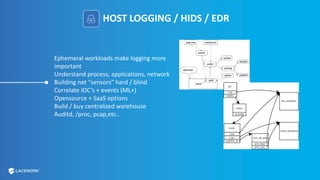
This document provides an overview and best practices for securing Kubernetes (K8s) clusters. It discusses common threats like exposed dashboards, APIs, and etcd stores. It also covers risks from within the cluster like compromised nodes and pods or vulnerabilities in container images. The document recommends 10 essential practices for securing K8s like image scanning, role-based access control, security boundaries, upgrades, pod security policies, node hardening, audit logging, and host/container logging. It emphasizes the importance of a security-aware development process and provides resources for further information.