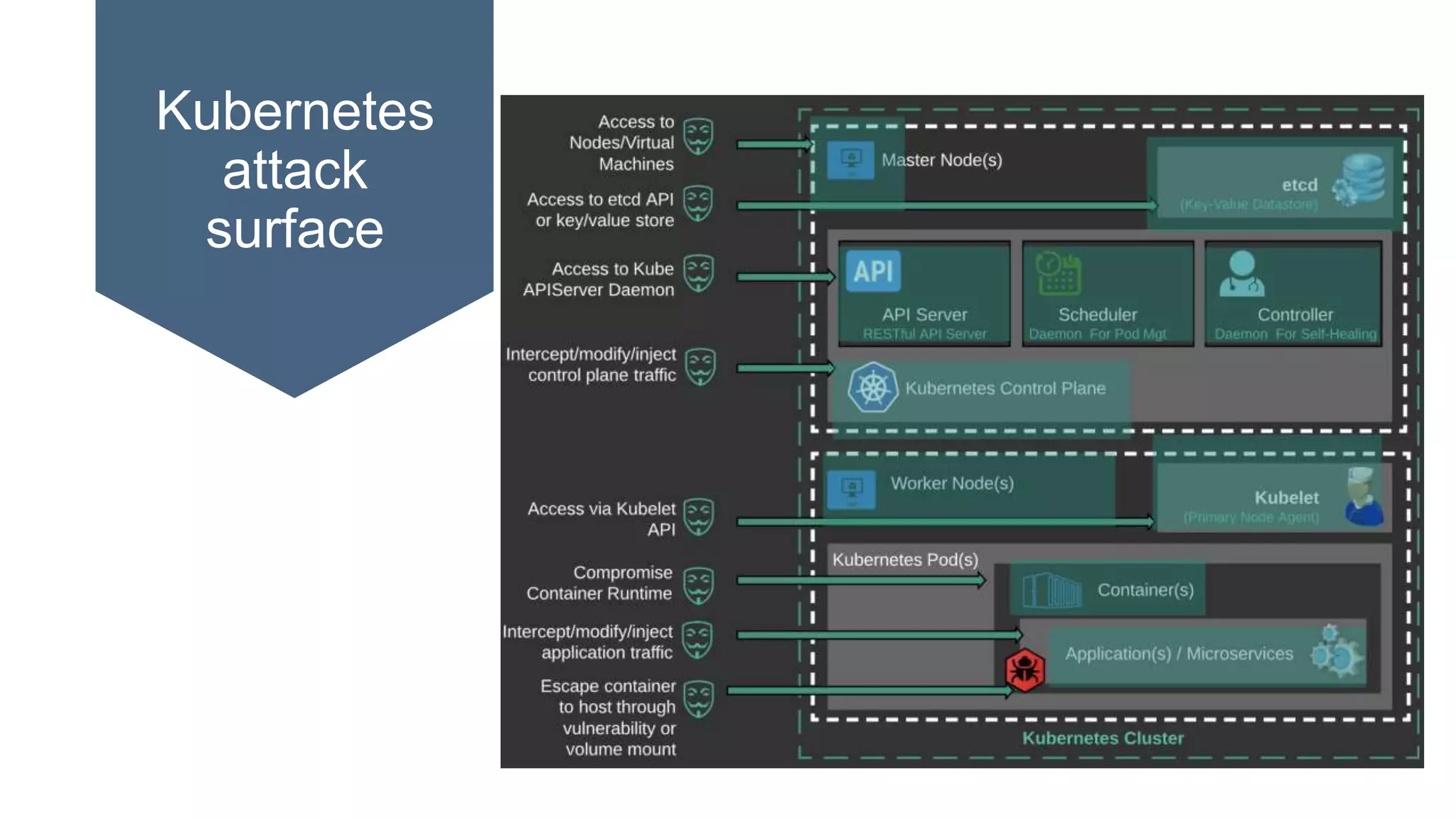
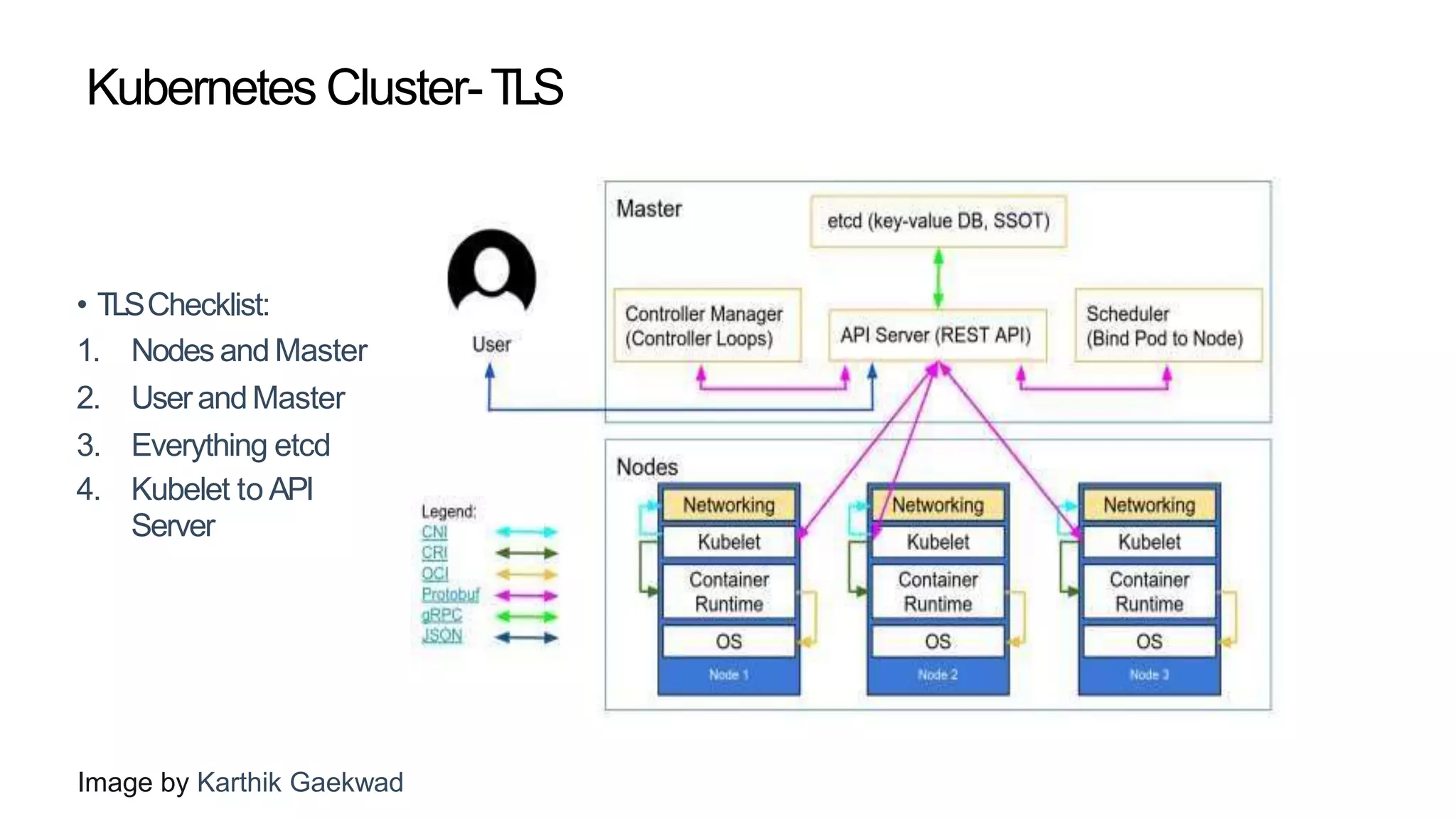
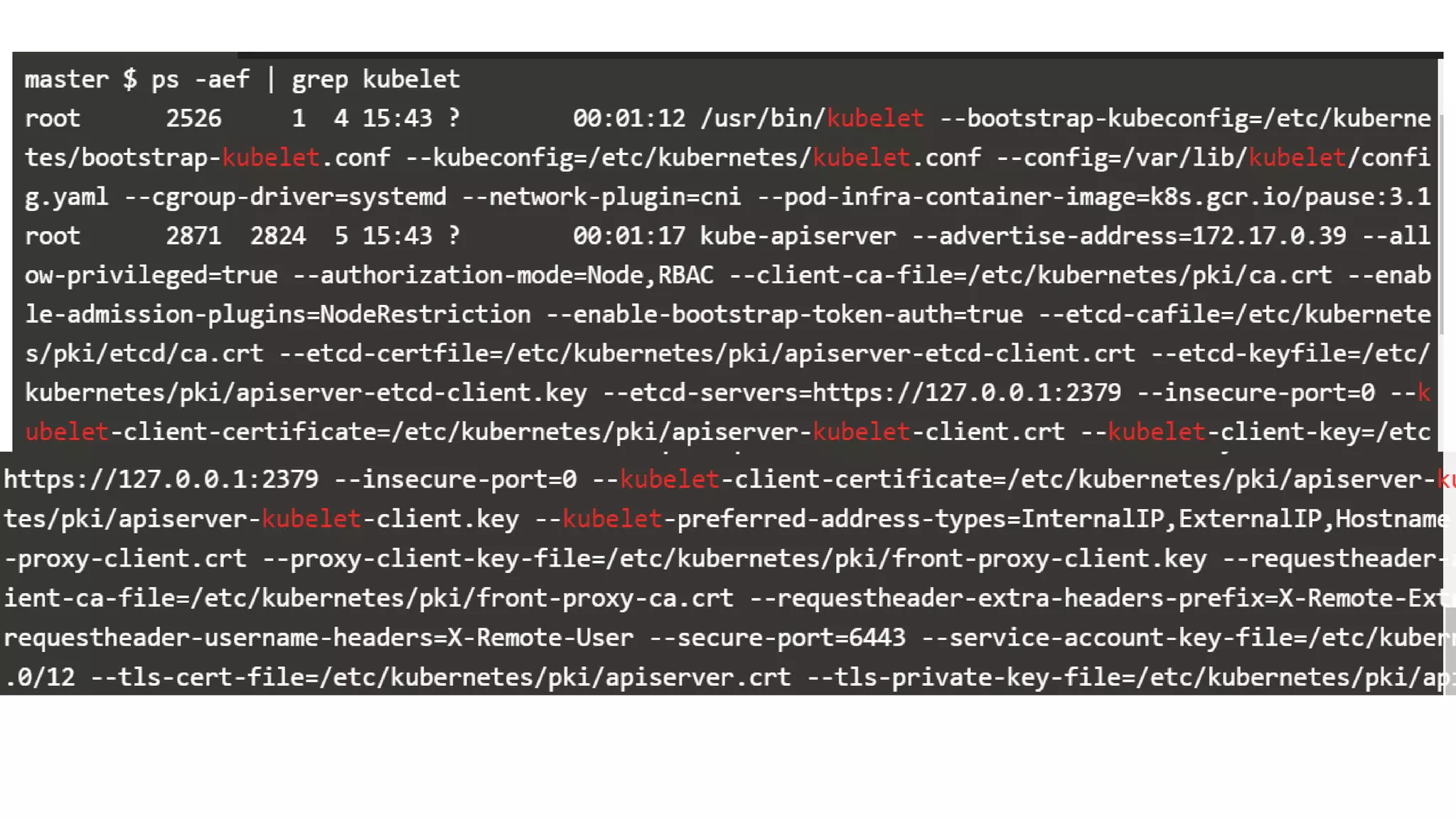
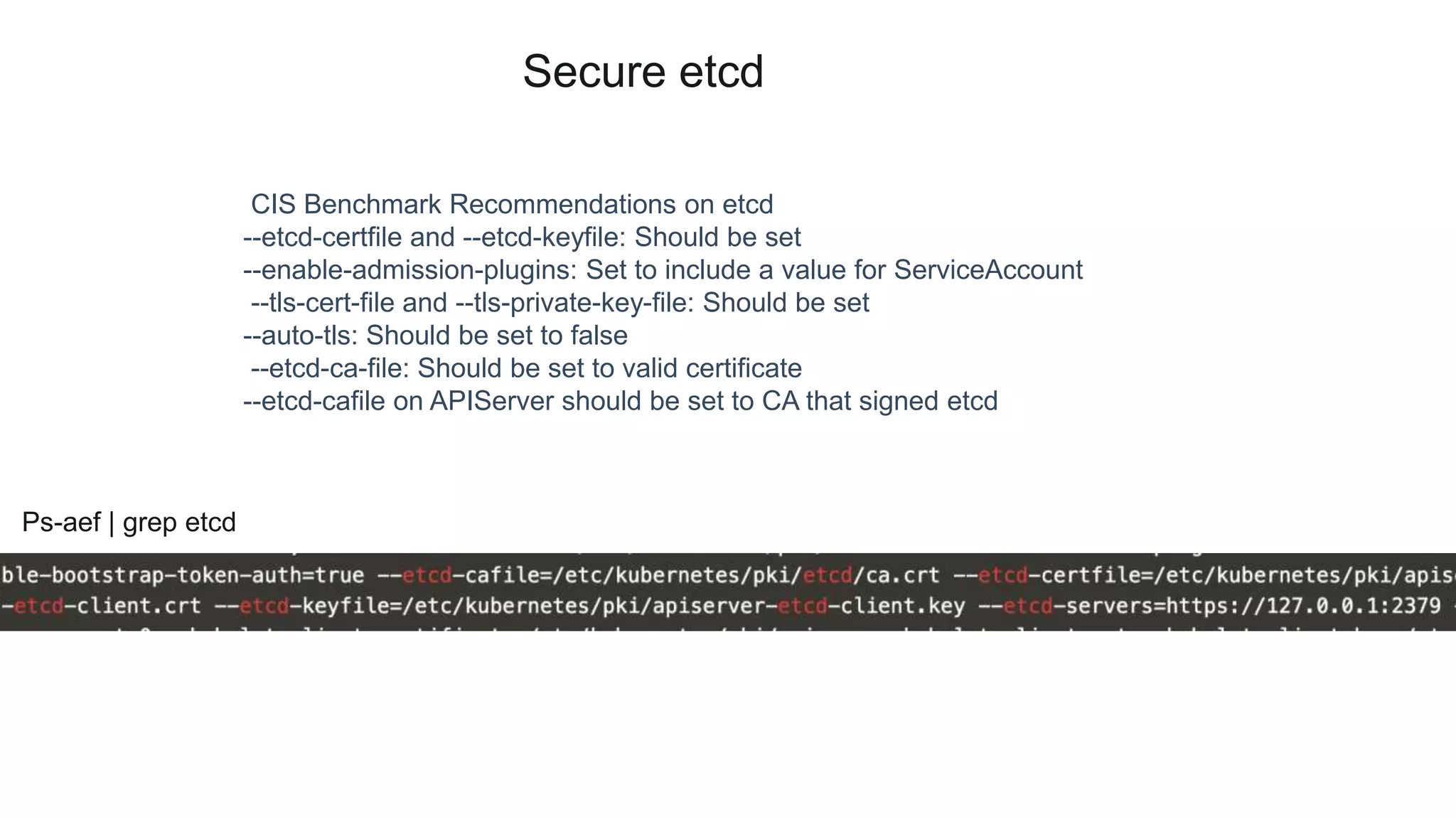
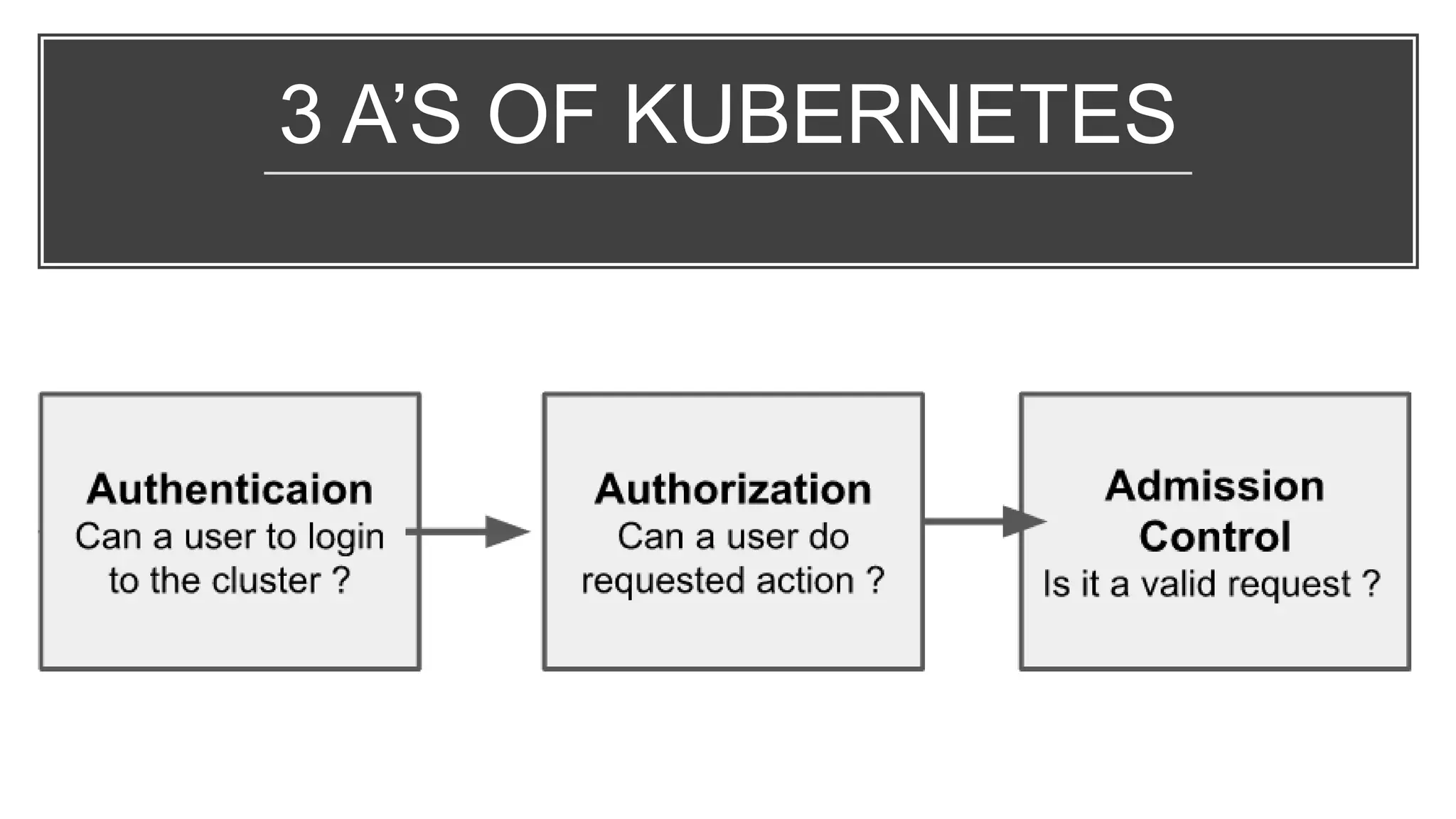
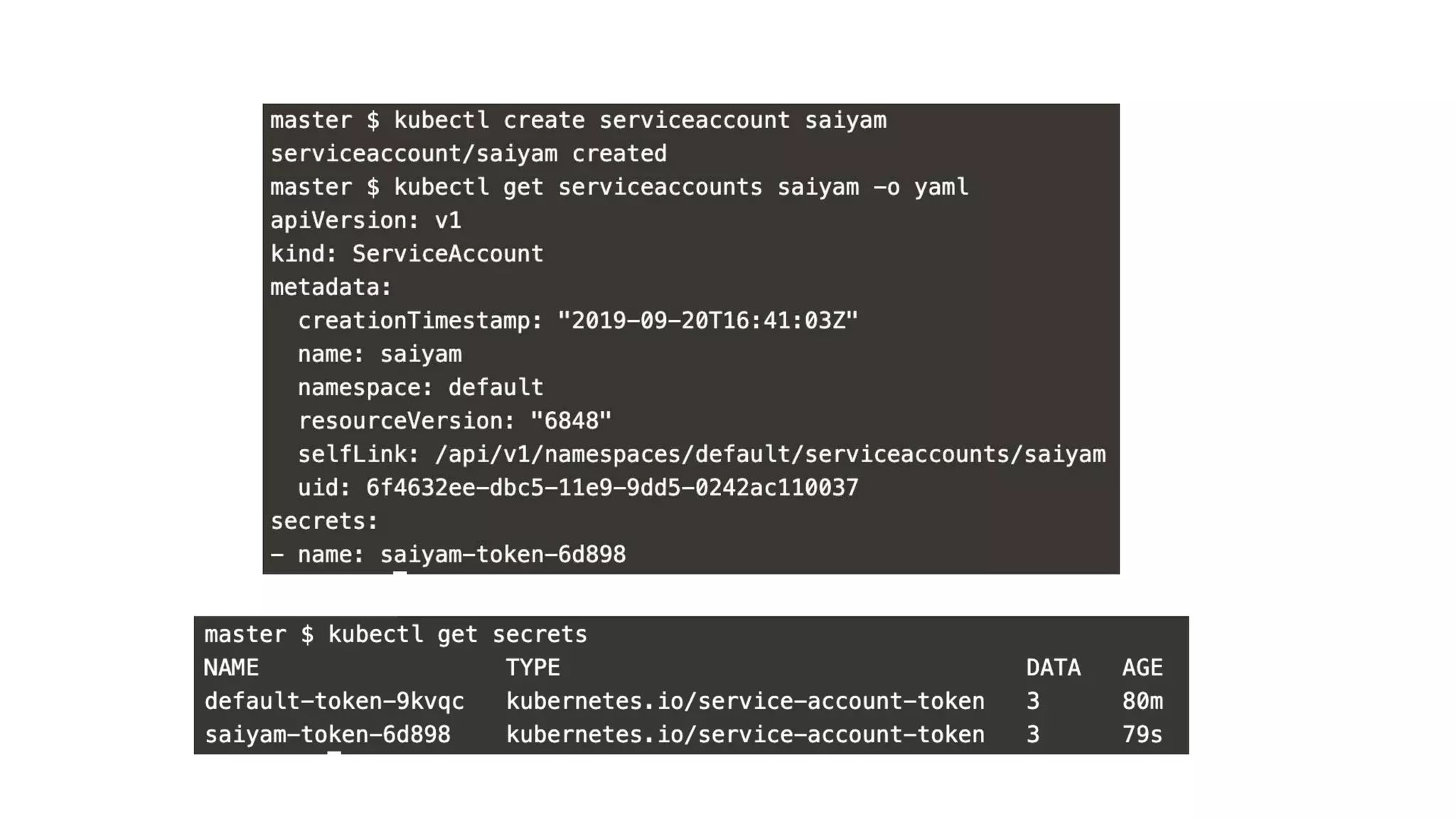
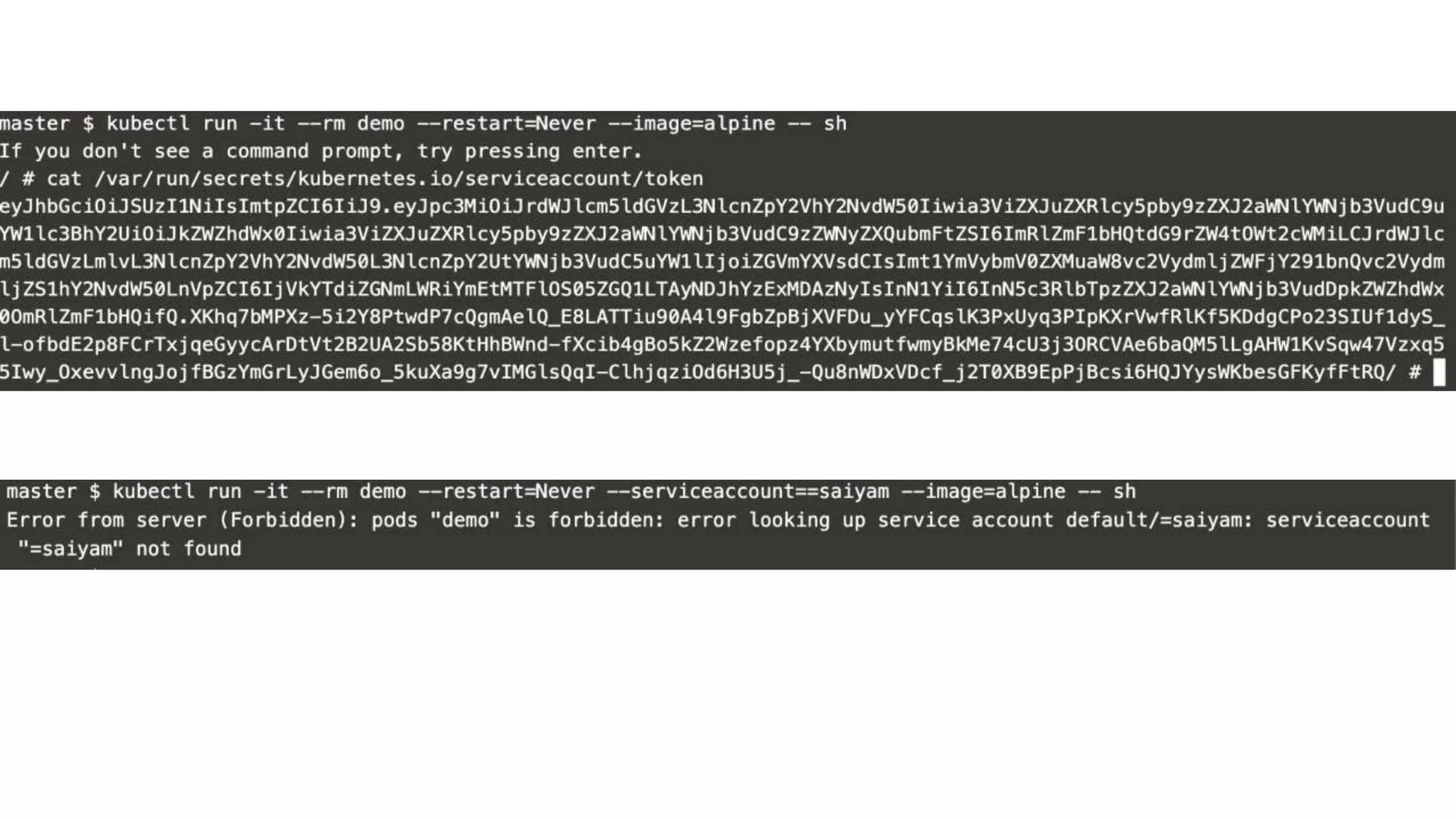
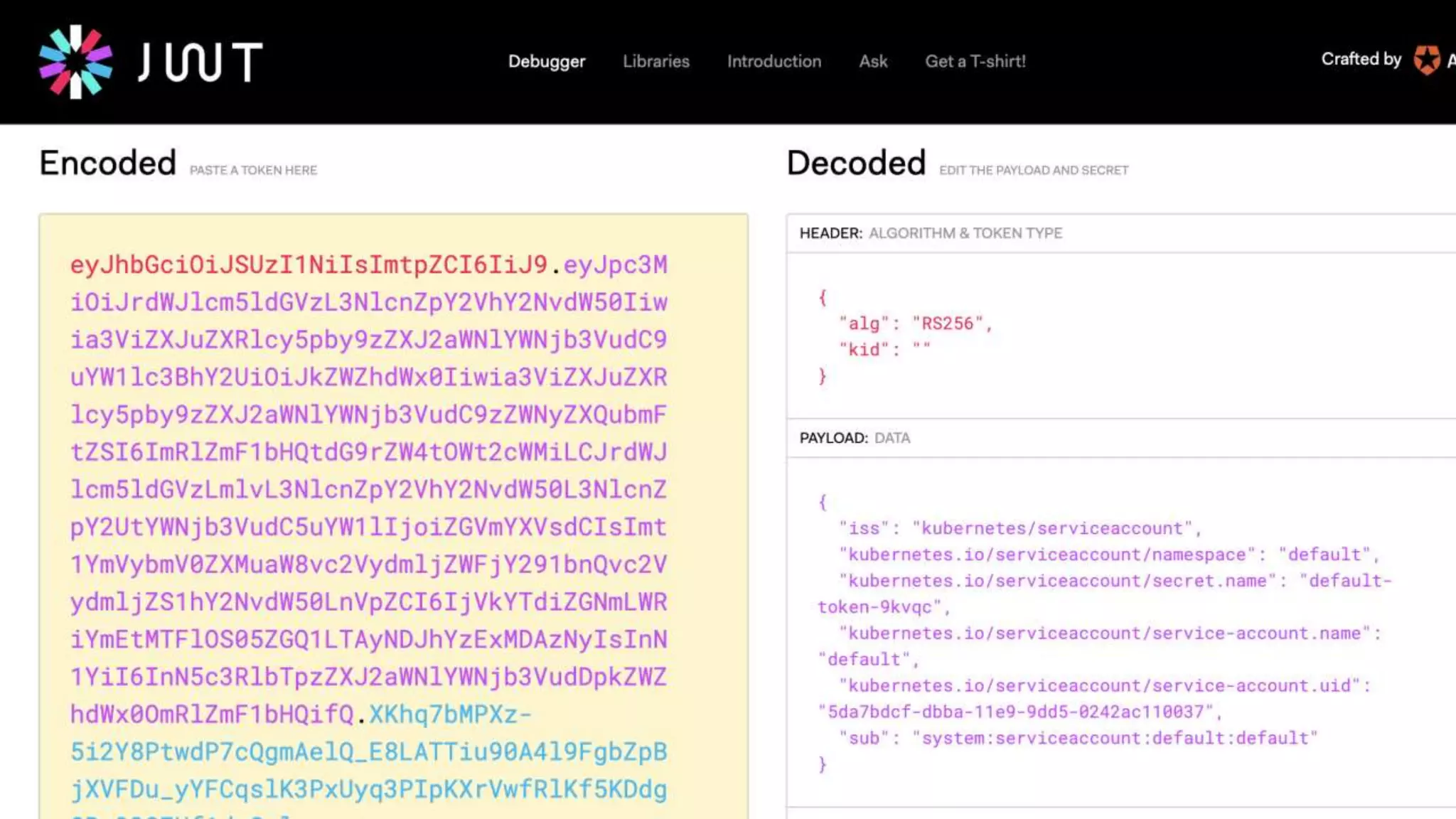
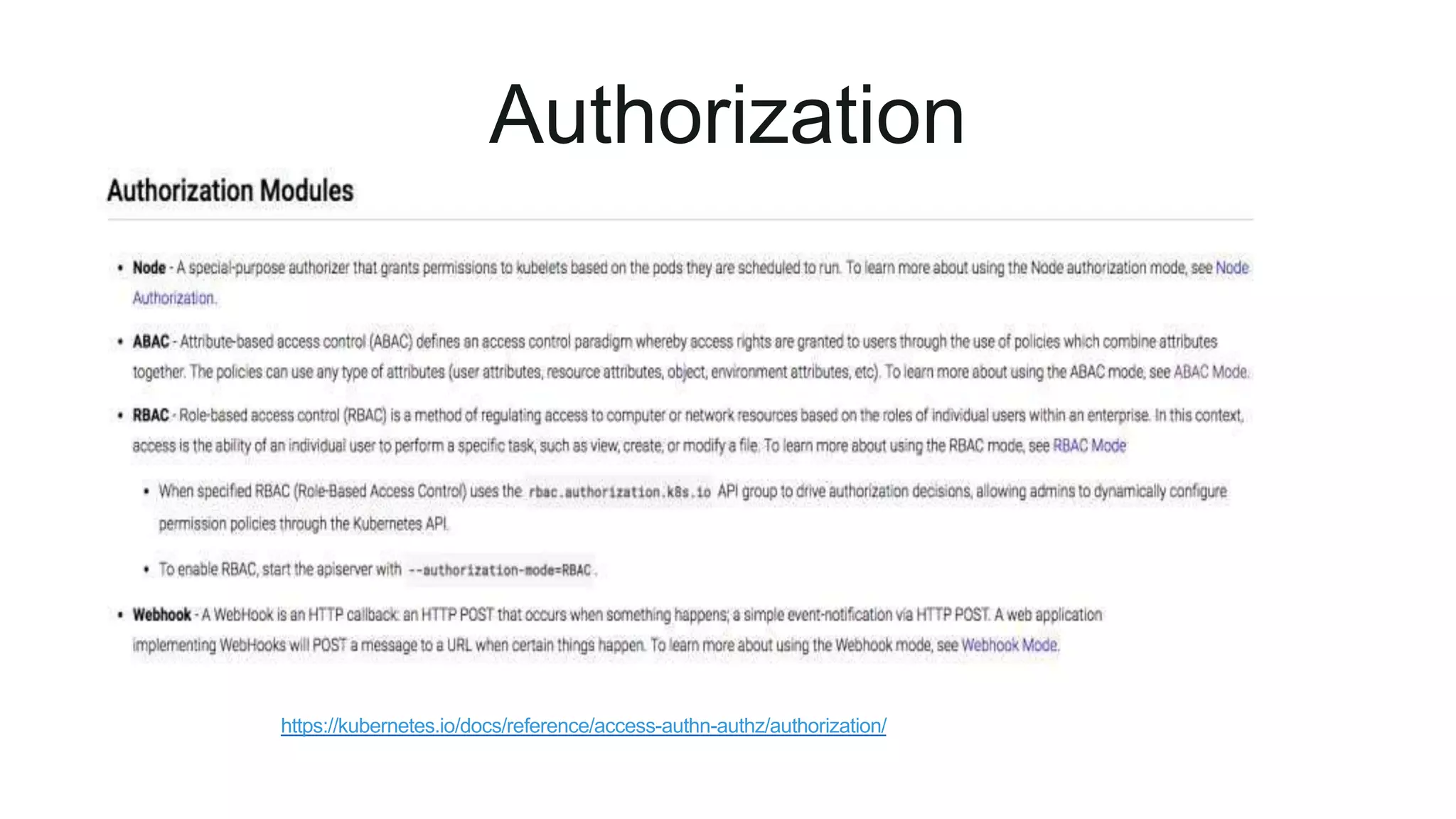
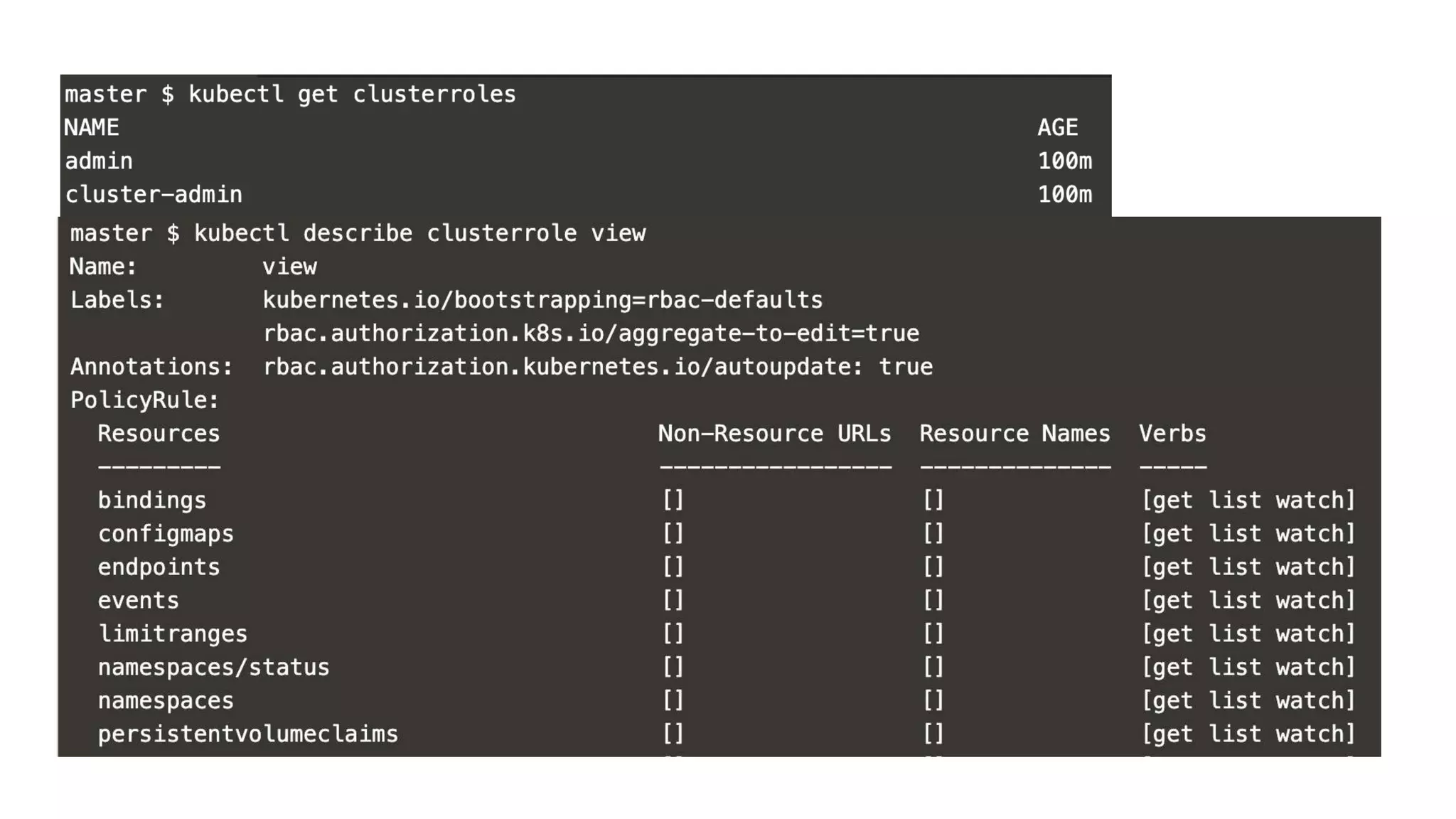
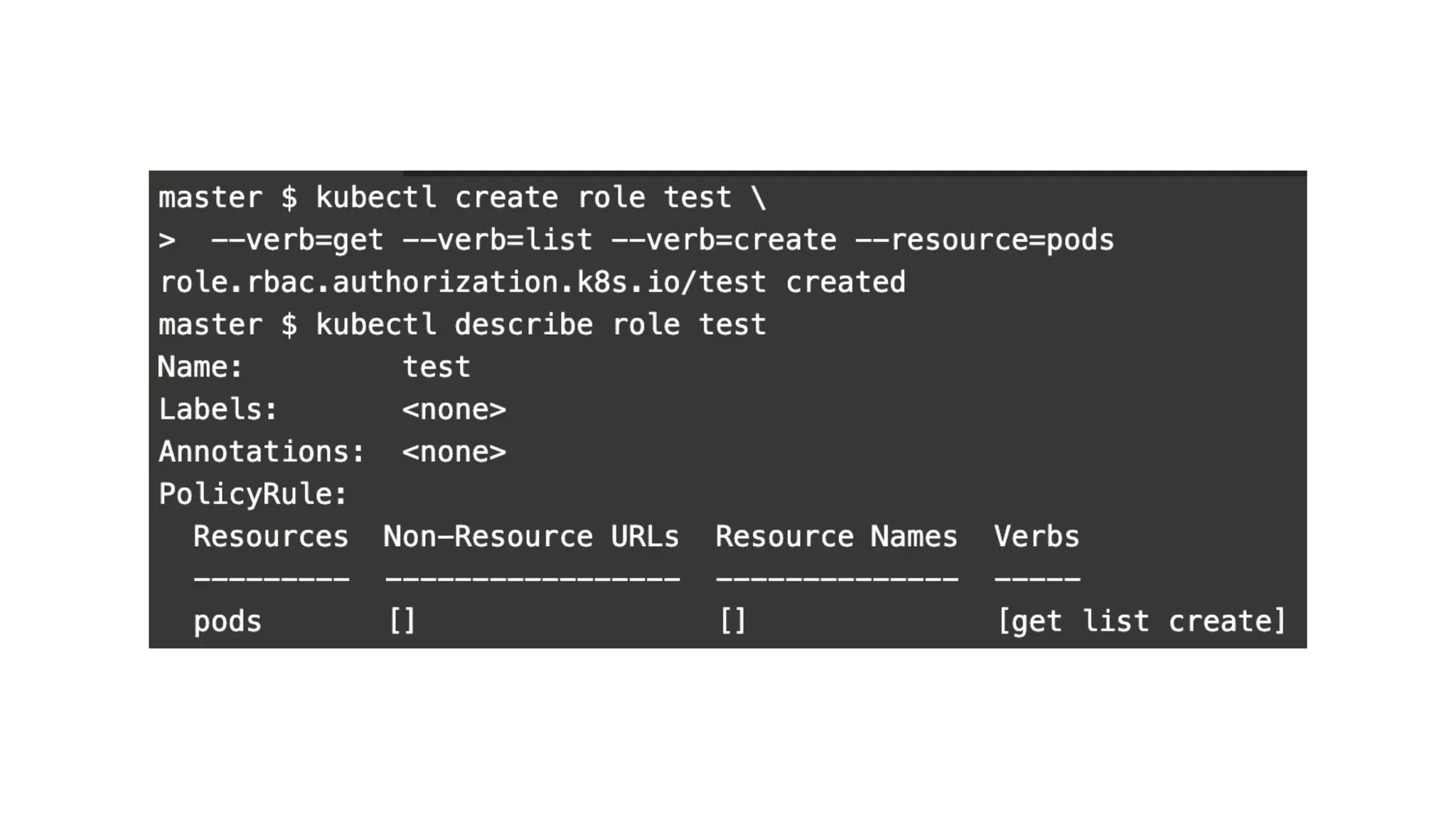
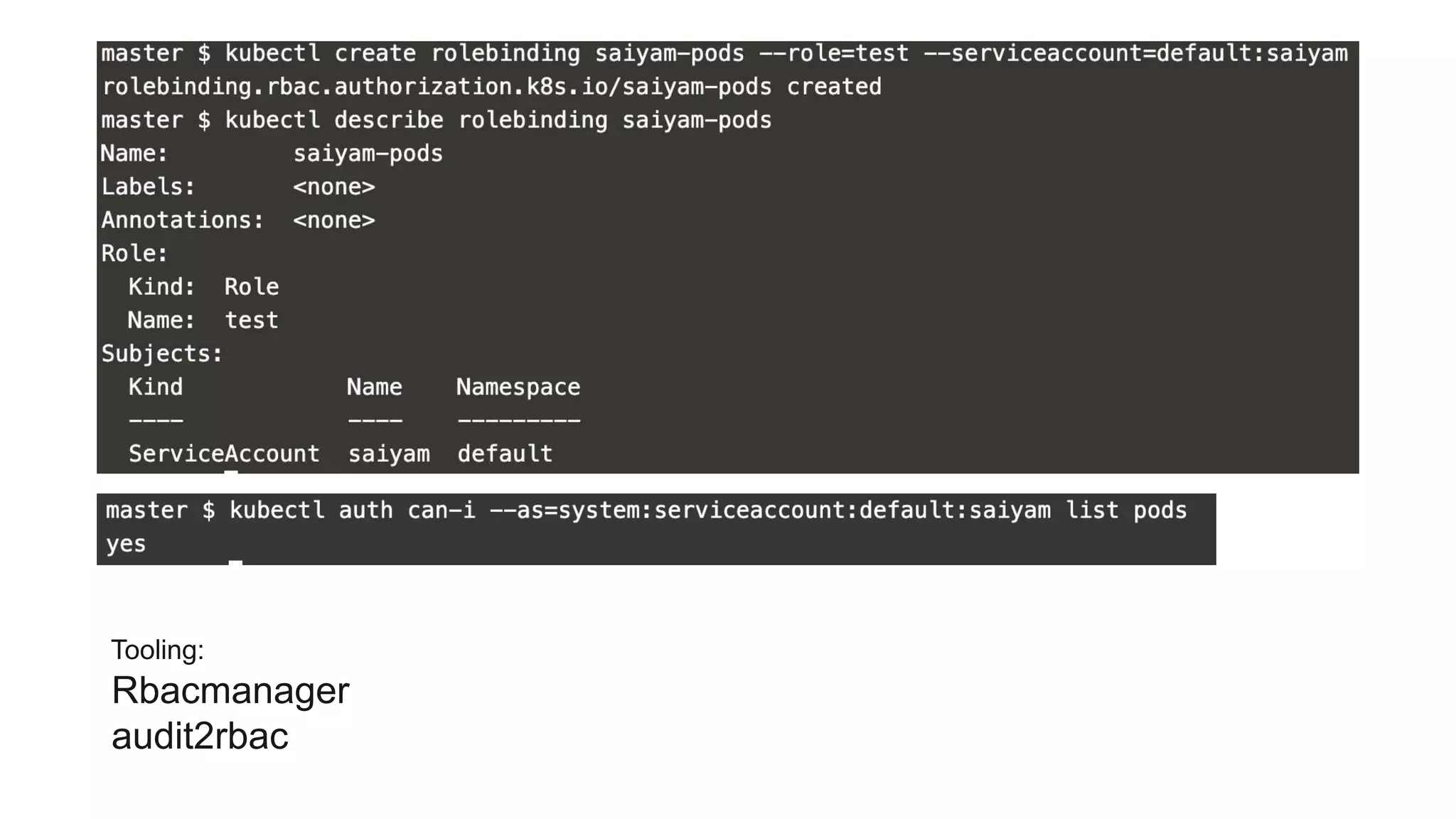
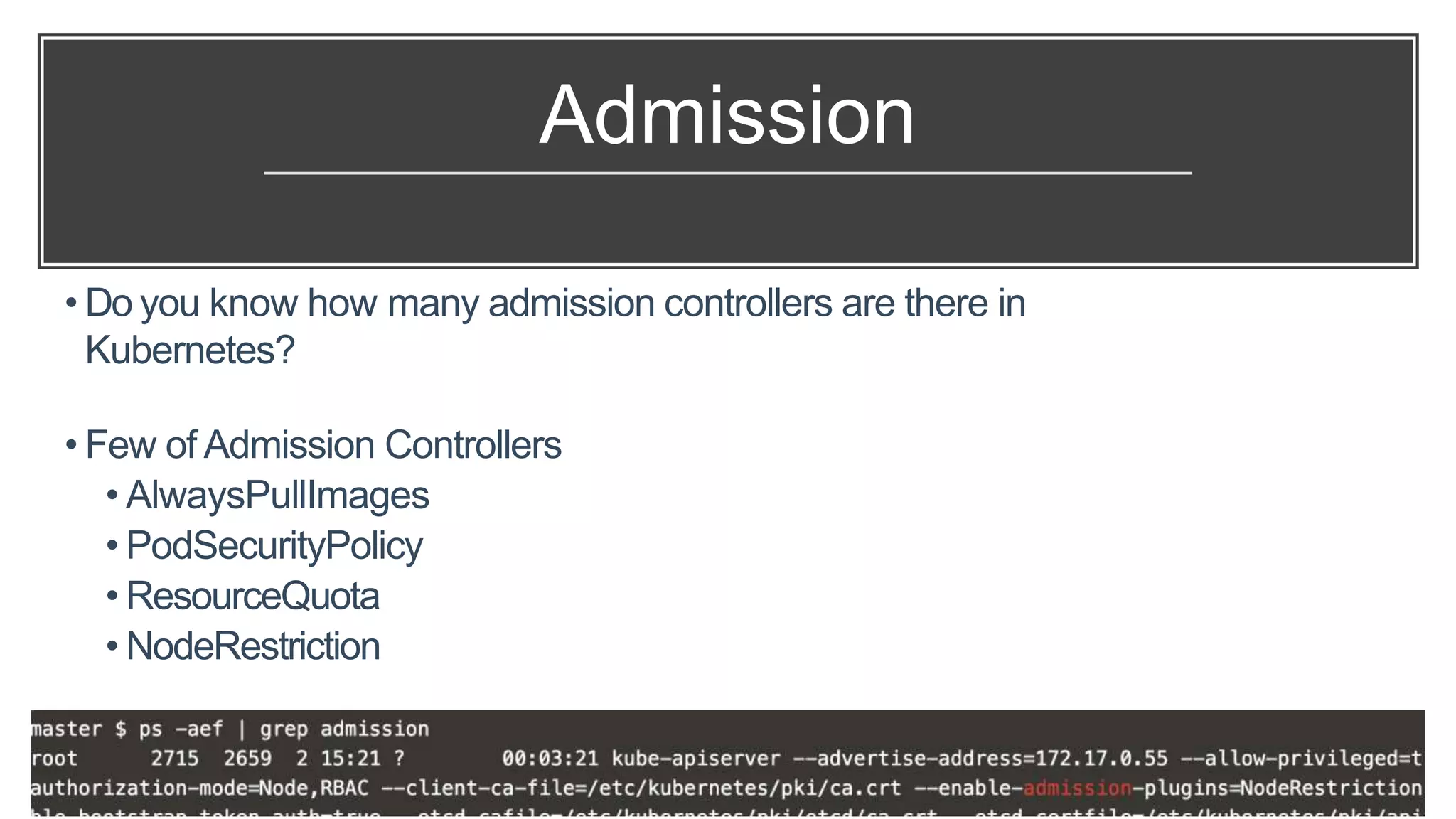
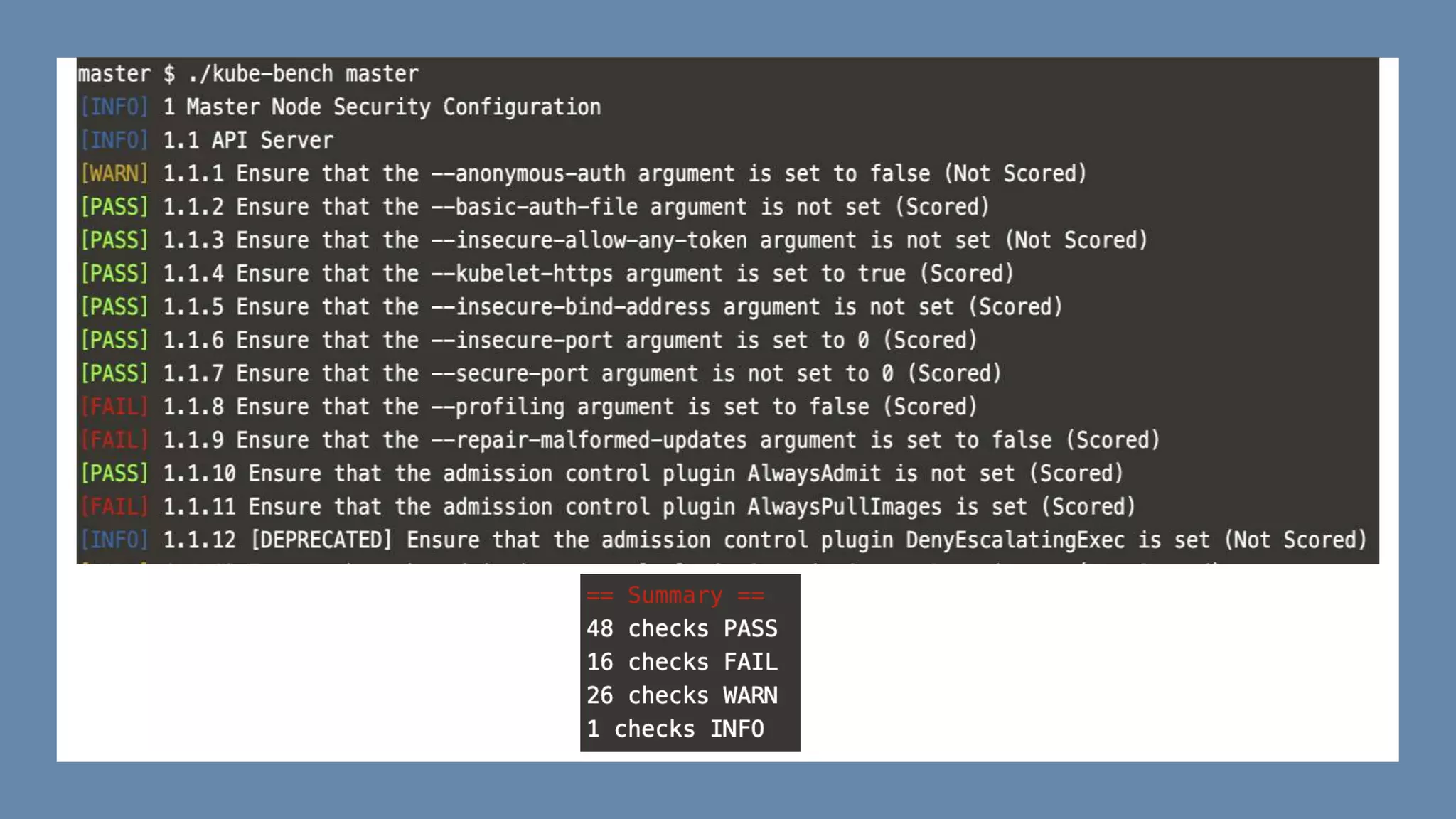
This document provides an overview of Kubernetes security concepts including the Kubernetes attack surface, TLS certificates, securing the Kubelet and etcd, authentication, authorization, admission controllers, tooling landscape, pod security policies, network policies, and secrets. It discusses key configuration recommendations and checks for securing different components like disabling privileged mode, setting TLS certificates, CIS benchmarks for etcd, and authentication methods in Kubernetes. The different types of admission controllers and CNCF security tooling are also briefly introduced.