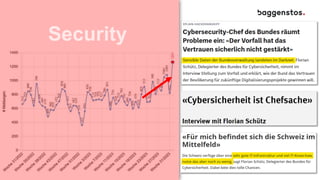
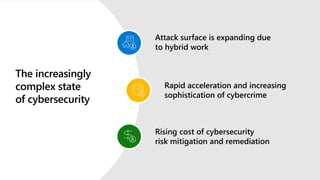
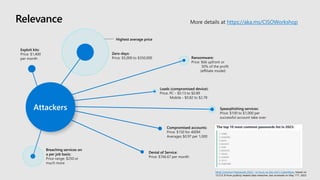
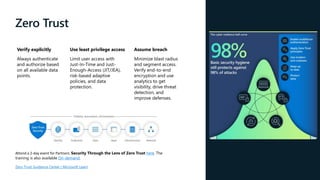
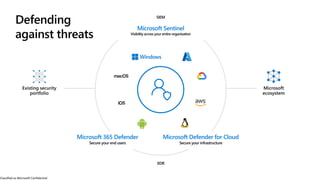
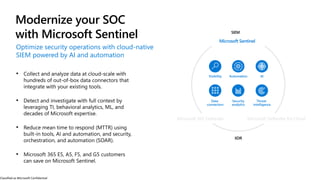
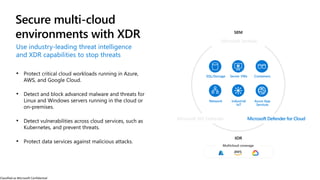
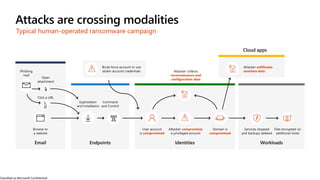
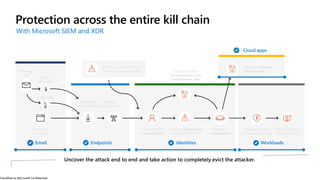
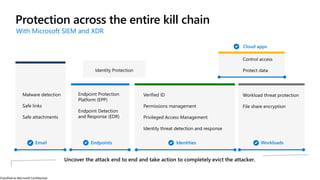
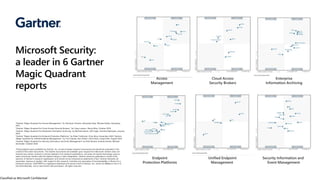
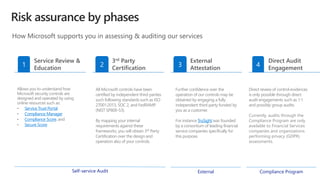
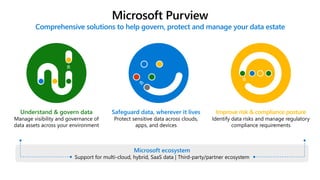
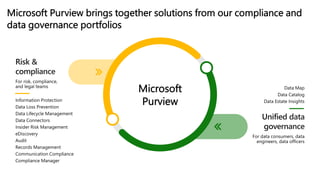
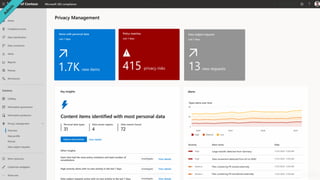
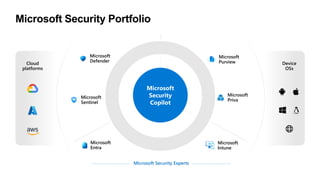
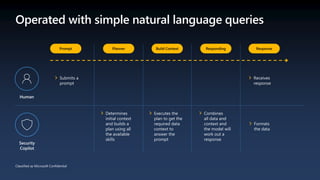
The document discusses the growing cybersecurity threats faced by businesses, particularly SMBs, due to the increase in hybrid work environments and sophisticated cybercriminal techniques. It highlights the importance of implementing security measures, such as Microsoft 365 security solutions and compliance tools, to mitigate risks like ransomware and phishing attacks. Additionally, the document outlines best practices for organizations to enhance their security posture, including regular monitoring and employee training on cybersecurity awareness.