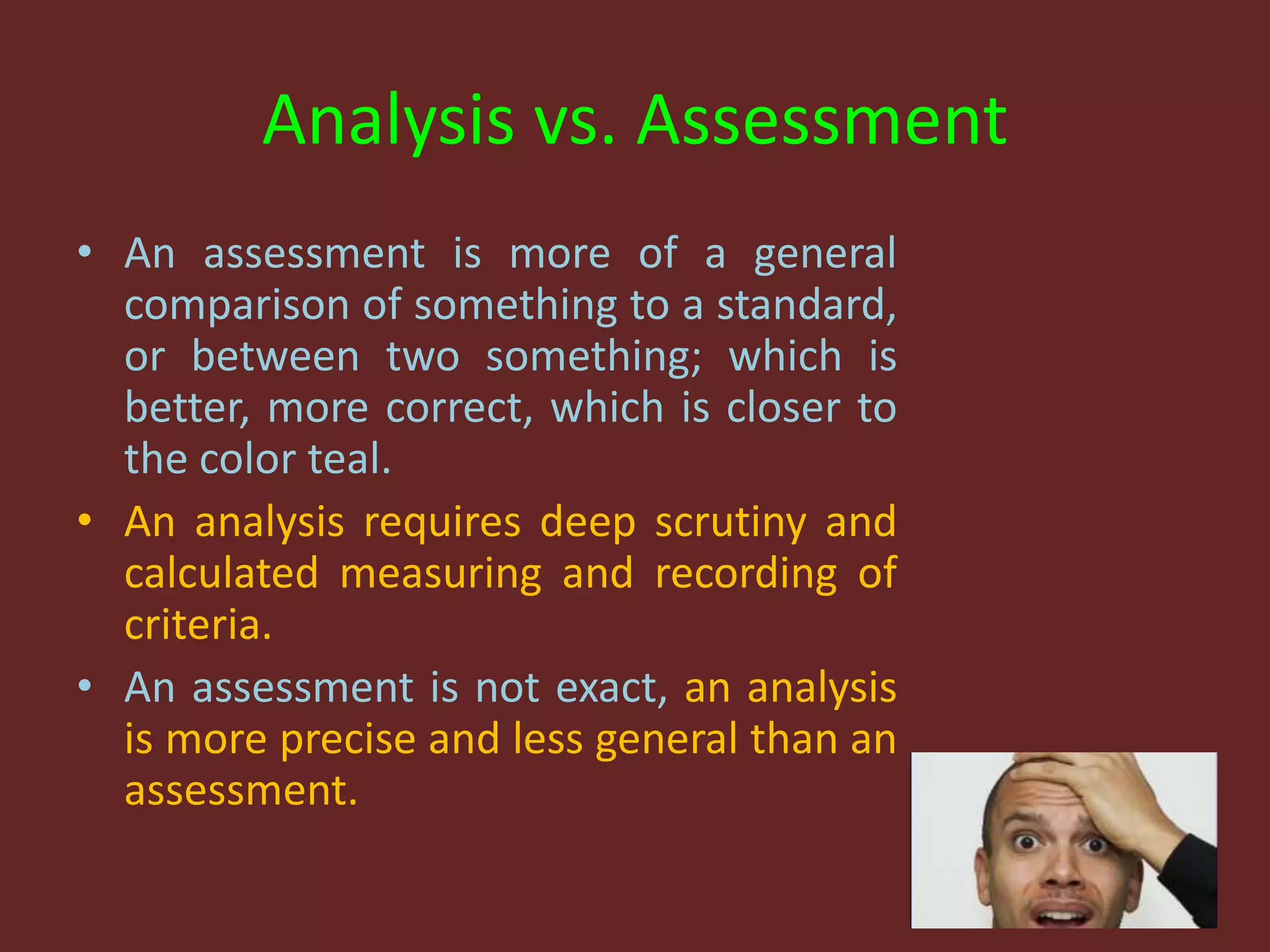
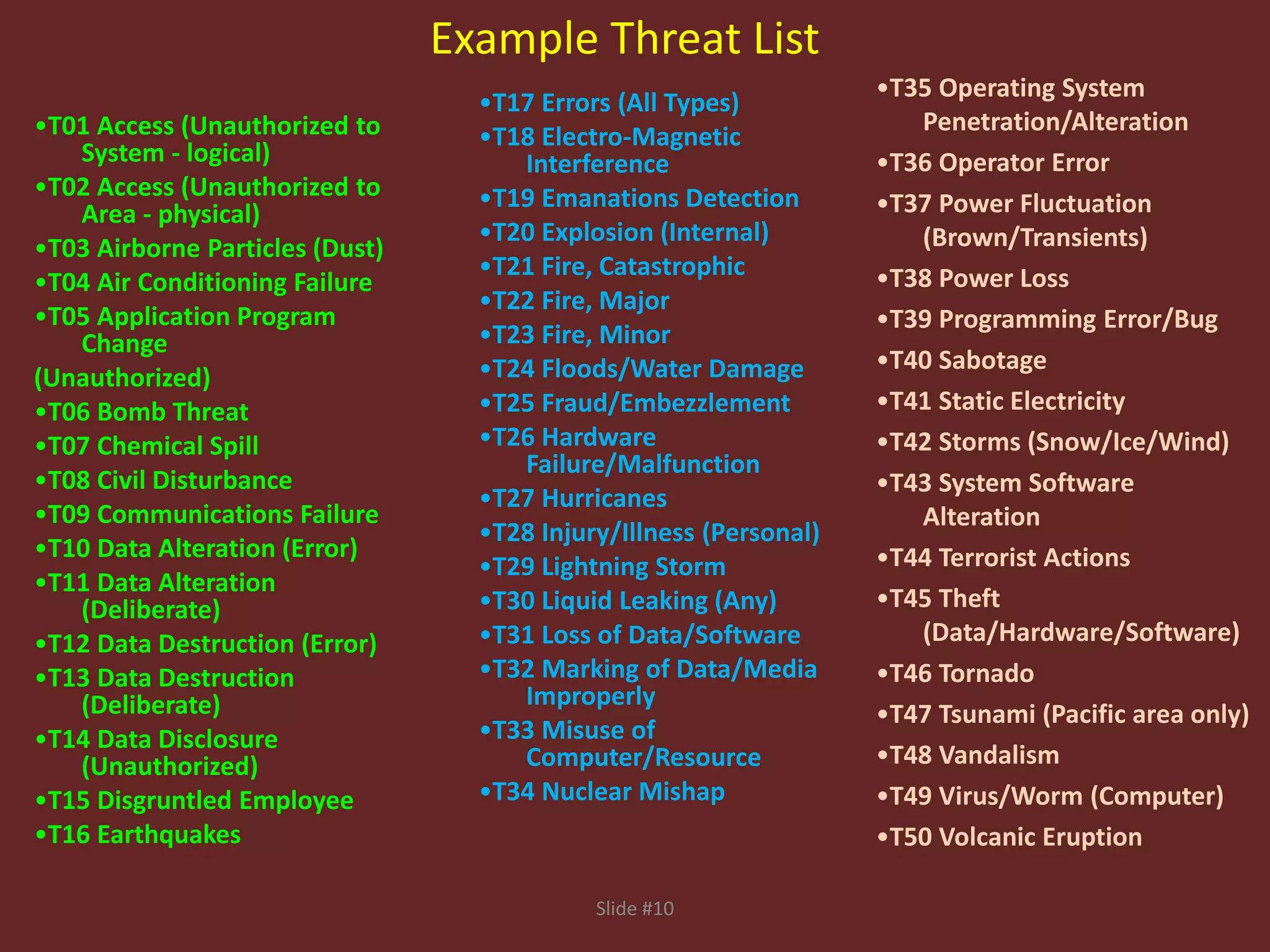
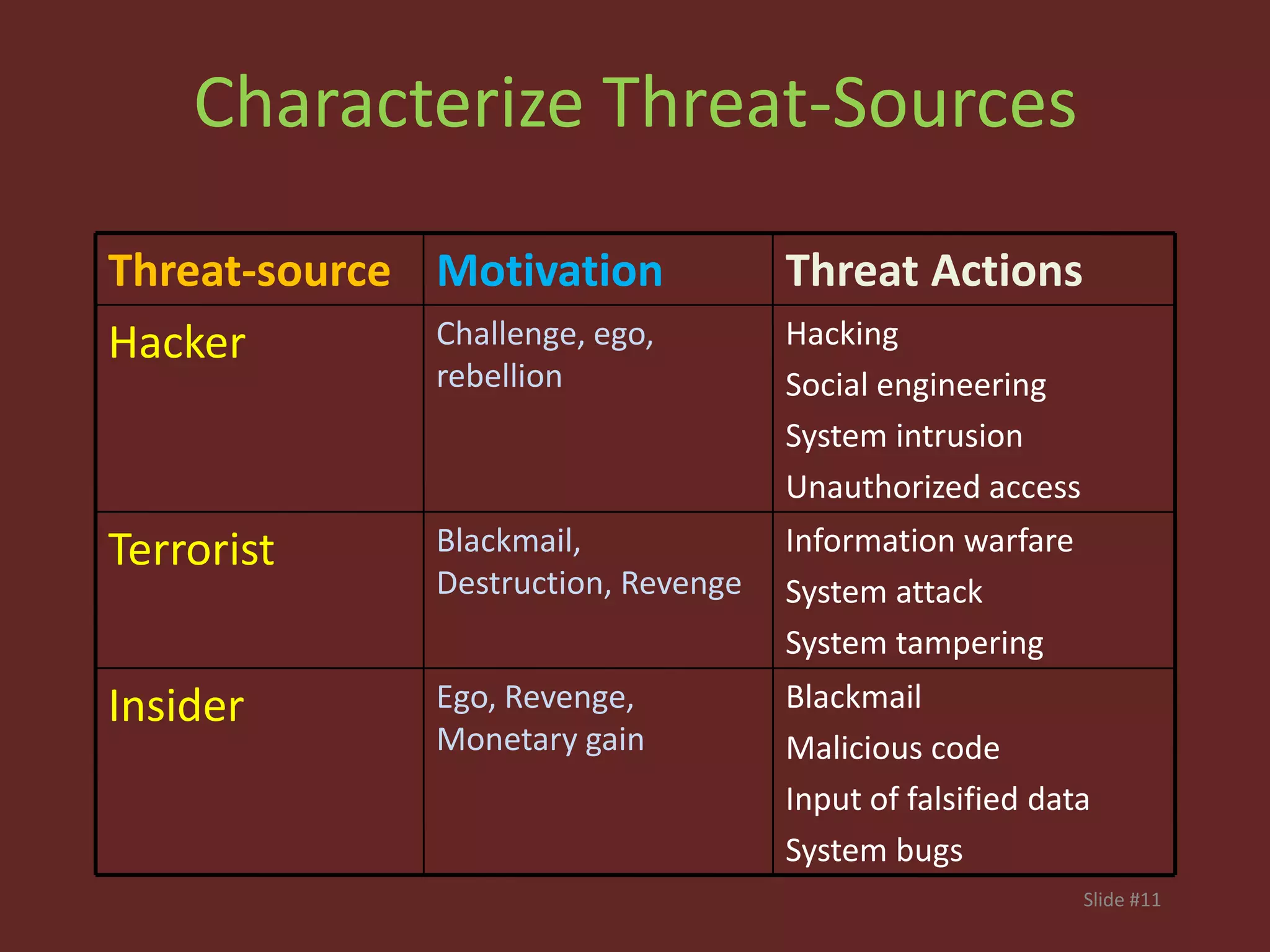
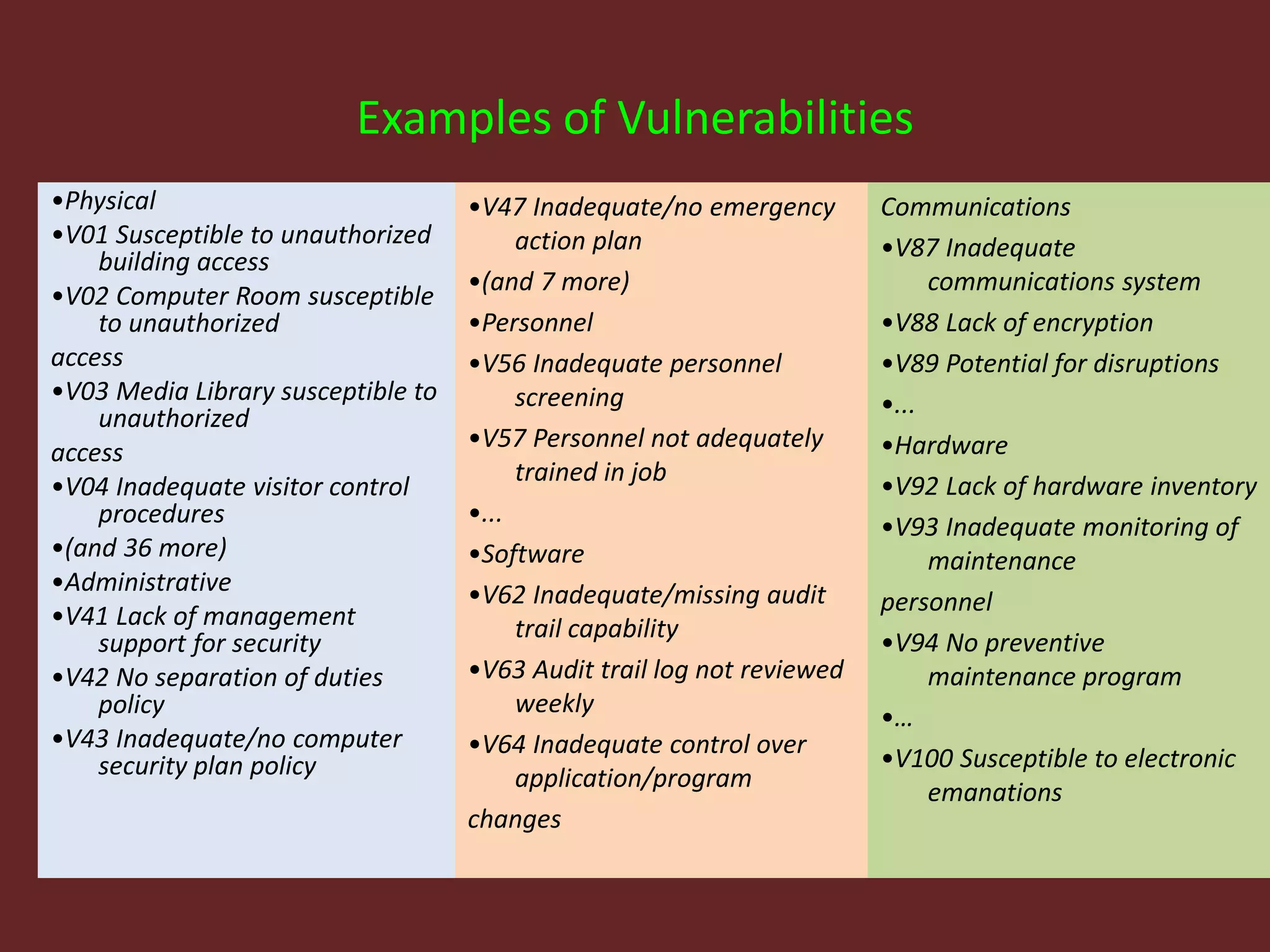
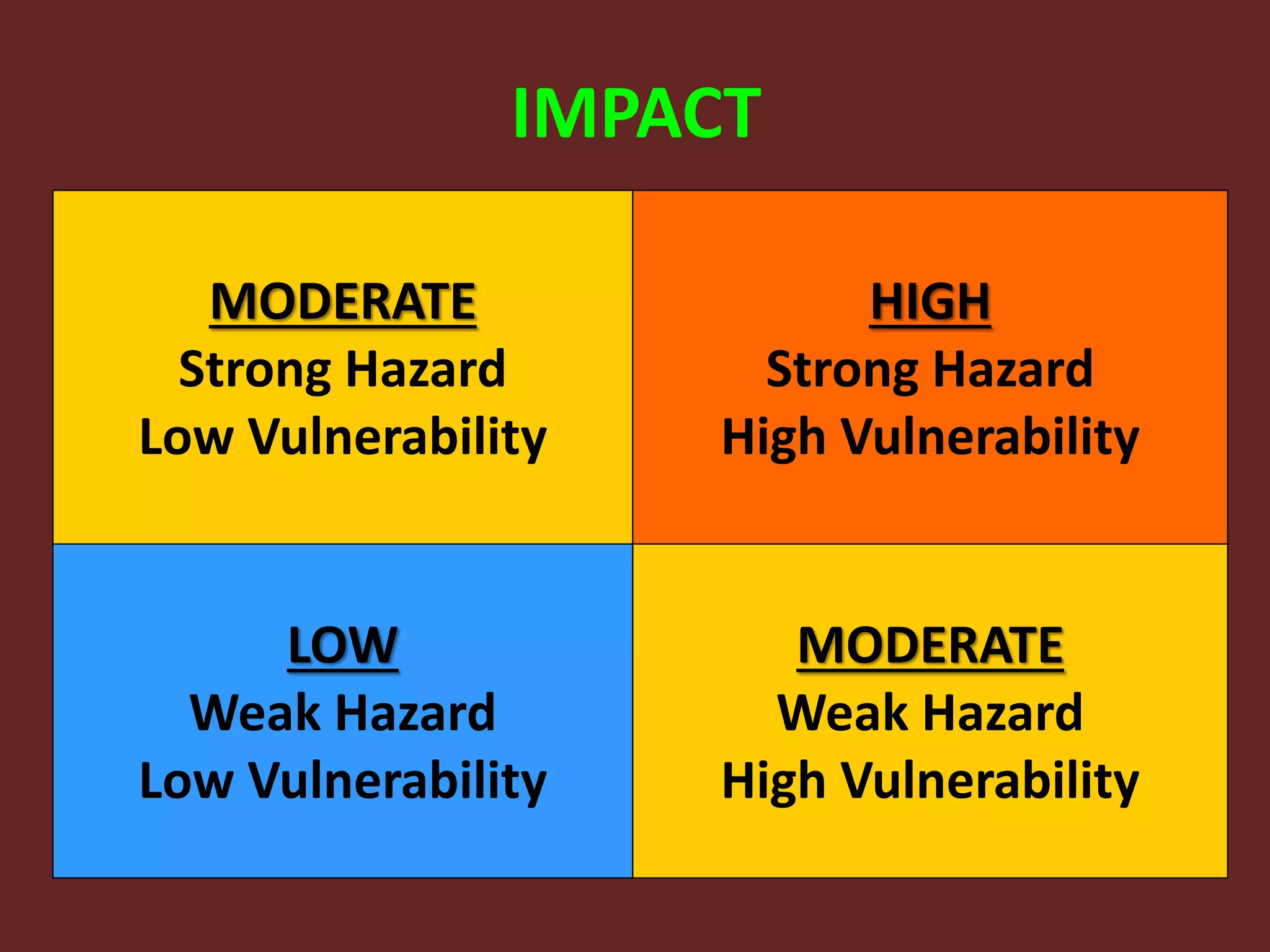
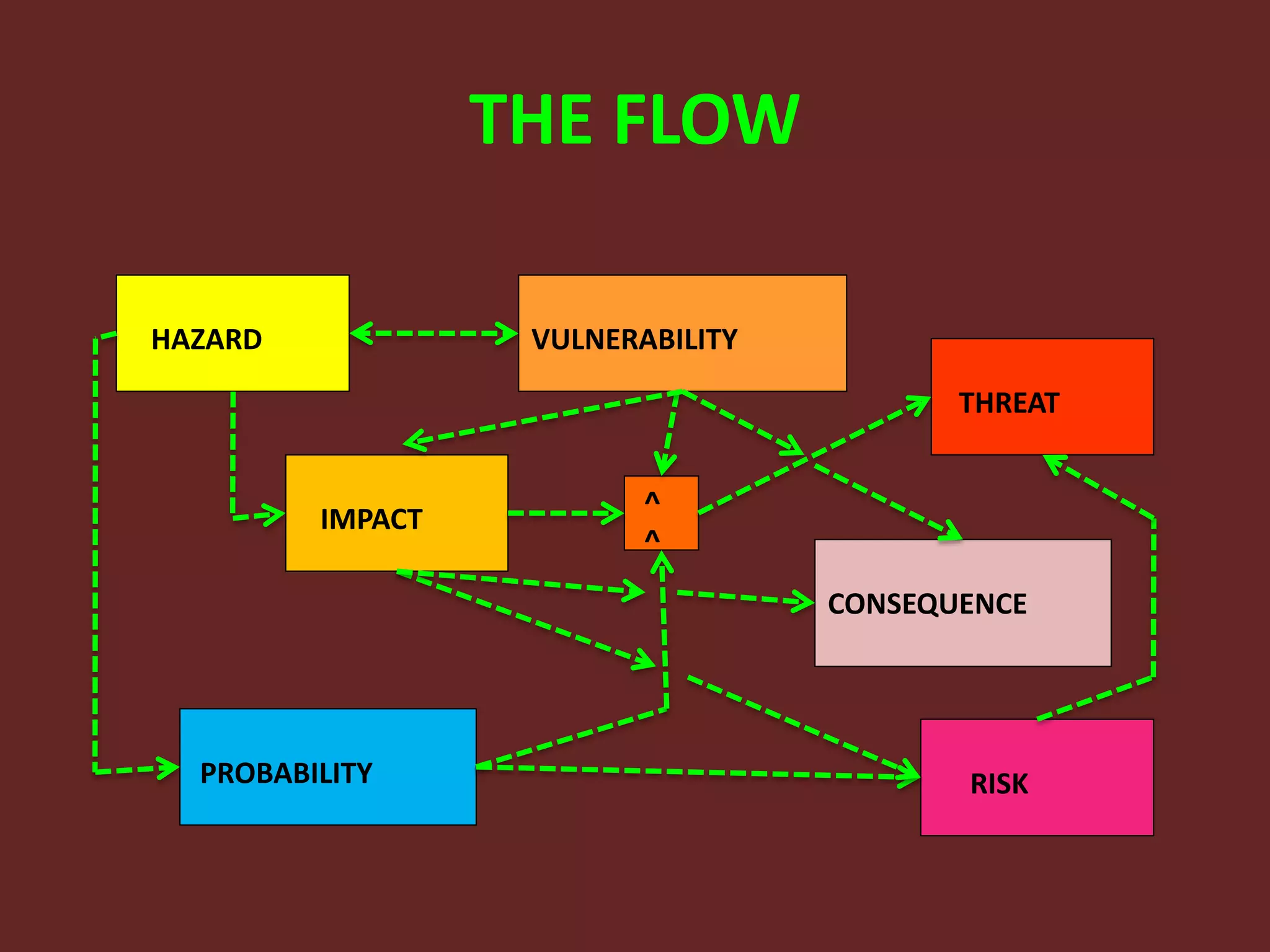
This document discusses the fundamentals of risk, threat, and vulnerability (R-T-A) analysis. It defines key terms like risks, threats, vulnerabilities, impacts, probabilities, and consequences. It explains that threats generally cannot be controlled, but risks and vulnerabilities can be mitigated or treated by identifying weaknesses and taking proactive measures. The core components in R-T-A analysis are hazards, vulnerabilities, threats, impacts, probabilities, risks, and consequences.