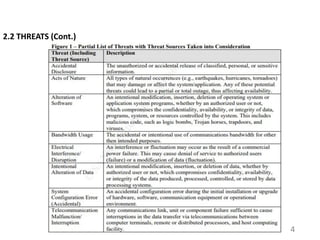
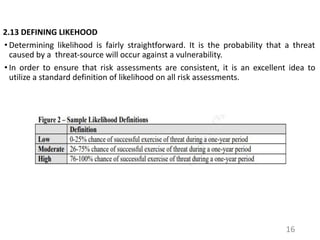
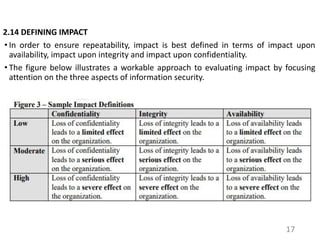
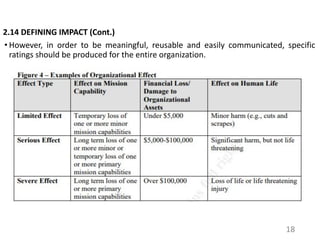
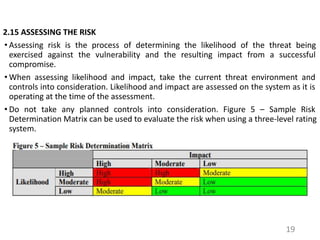
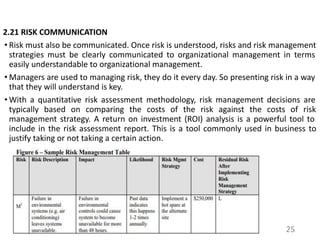
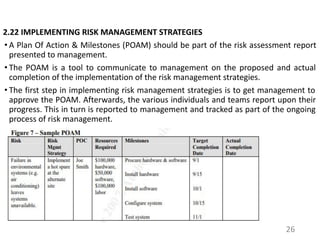
This document provides an introduction to information systems risk management. It defines key risk management terms like risk, threat, vulnerability, likelihood, and impact. It explains the processes of risk assessment, including qualitative and quantitative approaches. It also outlines strategies for managing risks, including mitigation, transference, acceptance, and avoidance. Effective communication of risks and implementation of risk management strategies through a Plan of Action & Milestones is discussed as important aspects of the overall risk management process.