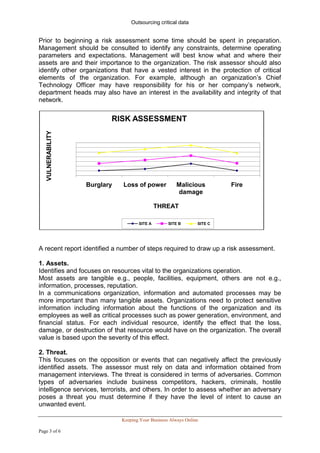
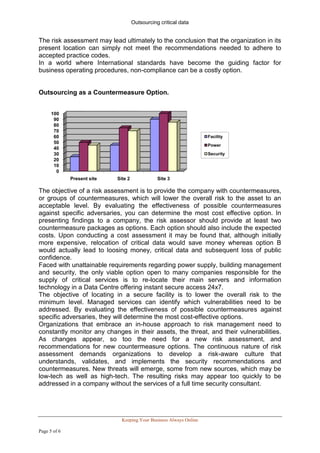
The document discusses the importance of conducting risk assessments and implementing countermeasures to protect critical data and assets from threats. It outlines the key steps in risk assessment including identifying assets, threats, vulnerabilities, and risks. Outsourcing critical data to a managed service provider that locates data in secure environments is presented as an effective countermeasure that can minimize risks by placing security in the hands of security professionals and ensuring constant monitoring and uninterrupted access. The document advocates for regular risk assessments and risk management to account for changing threats over time.