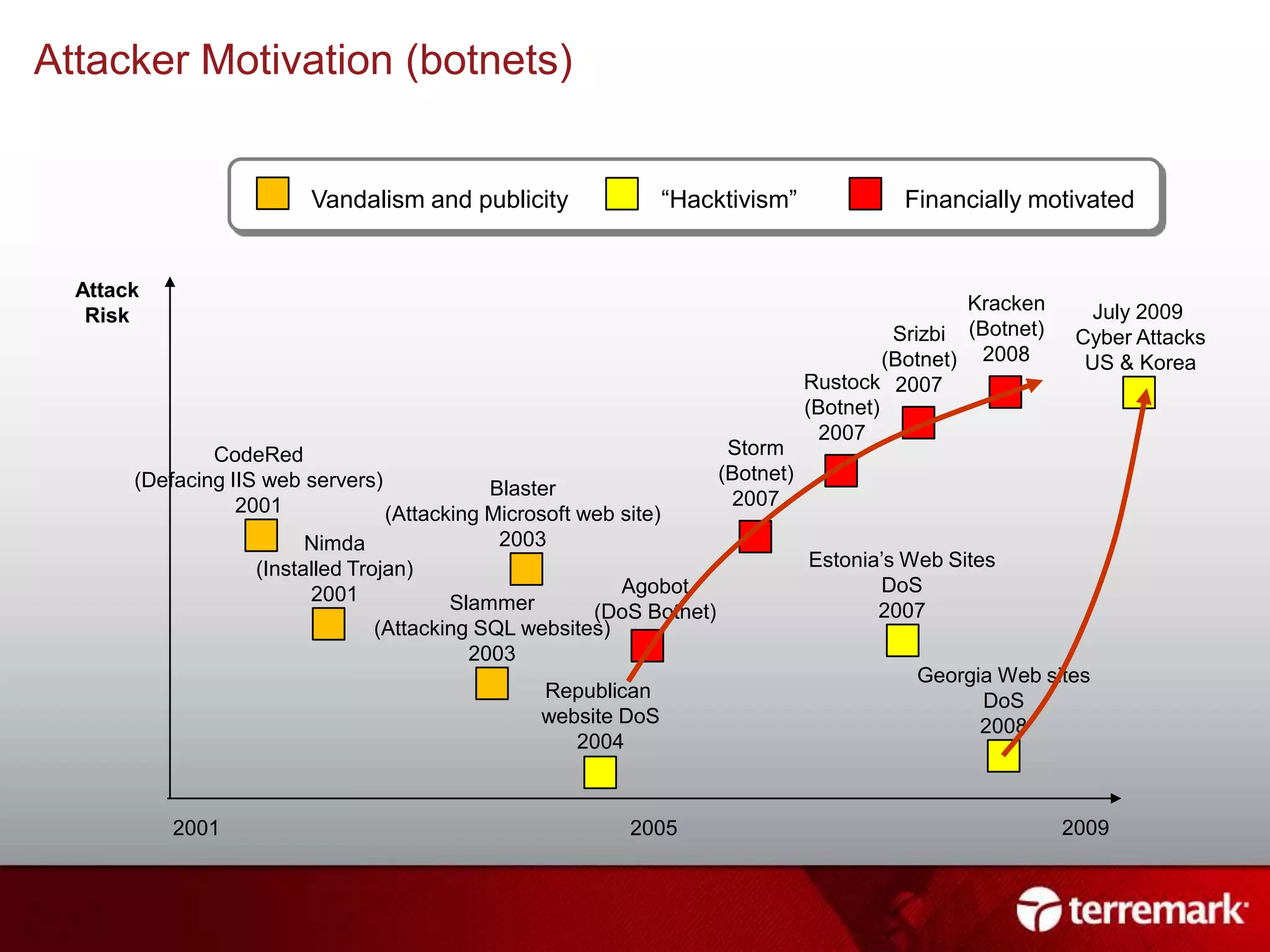
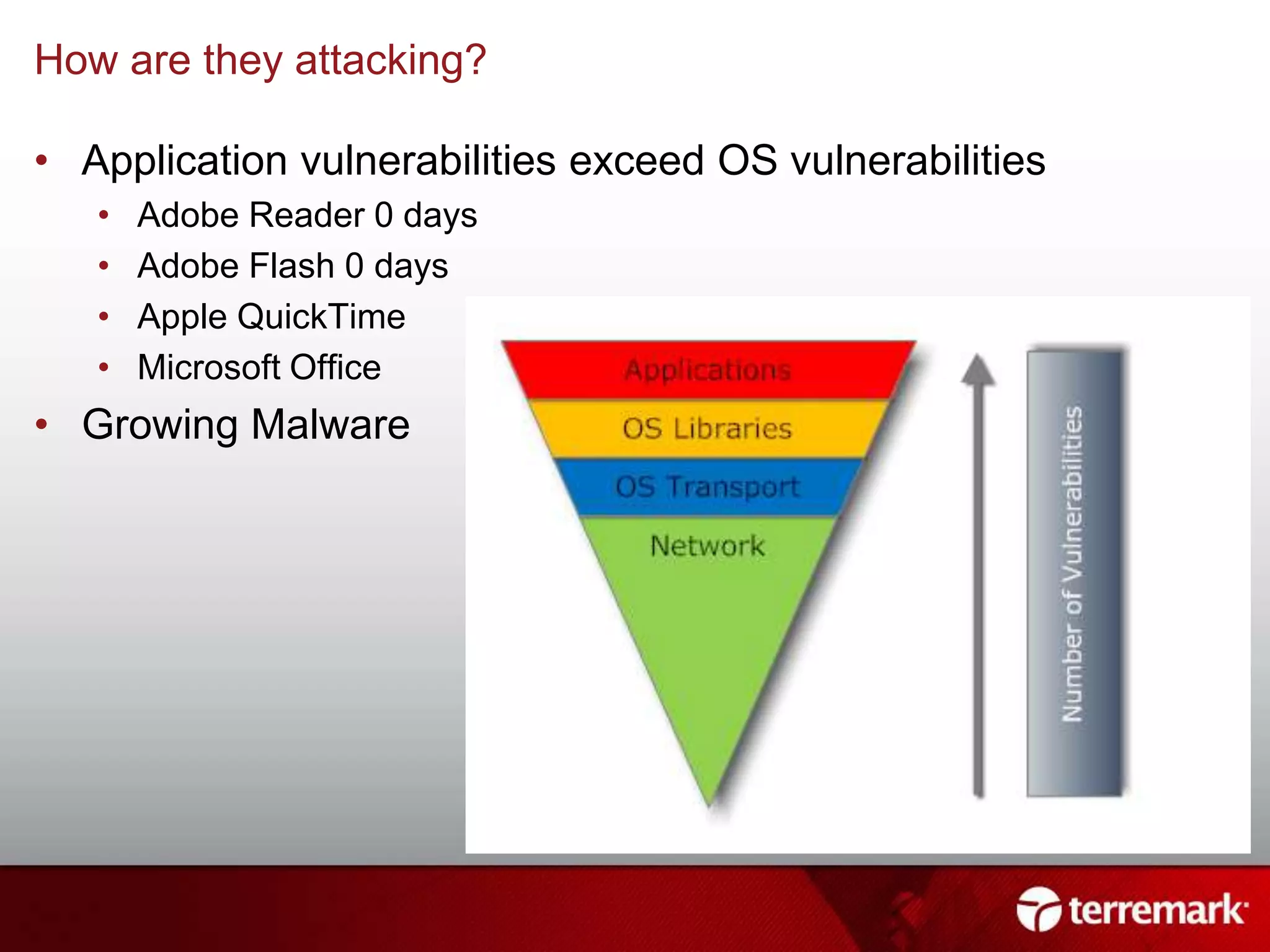
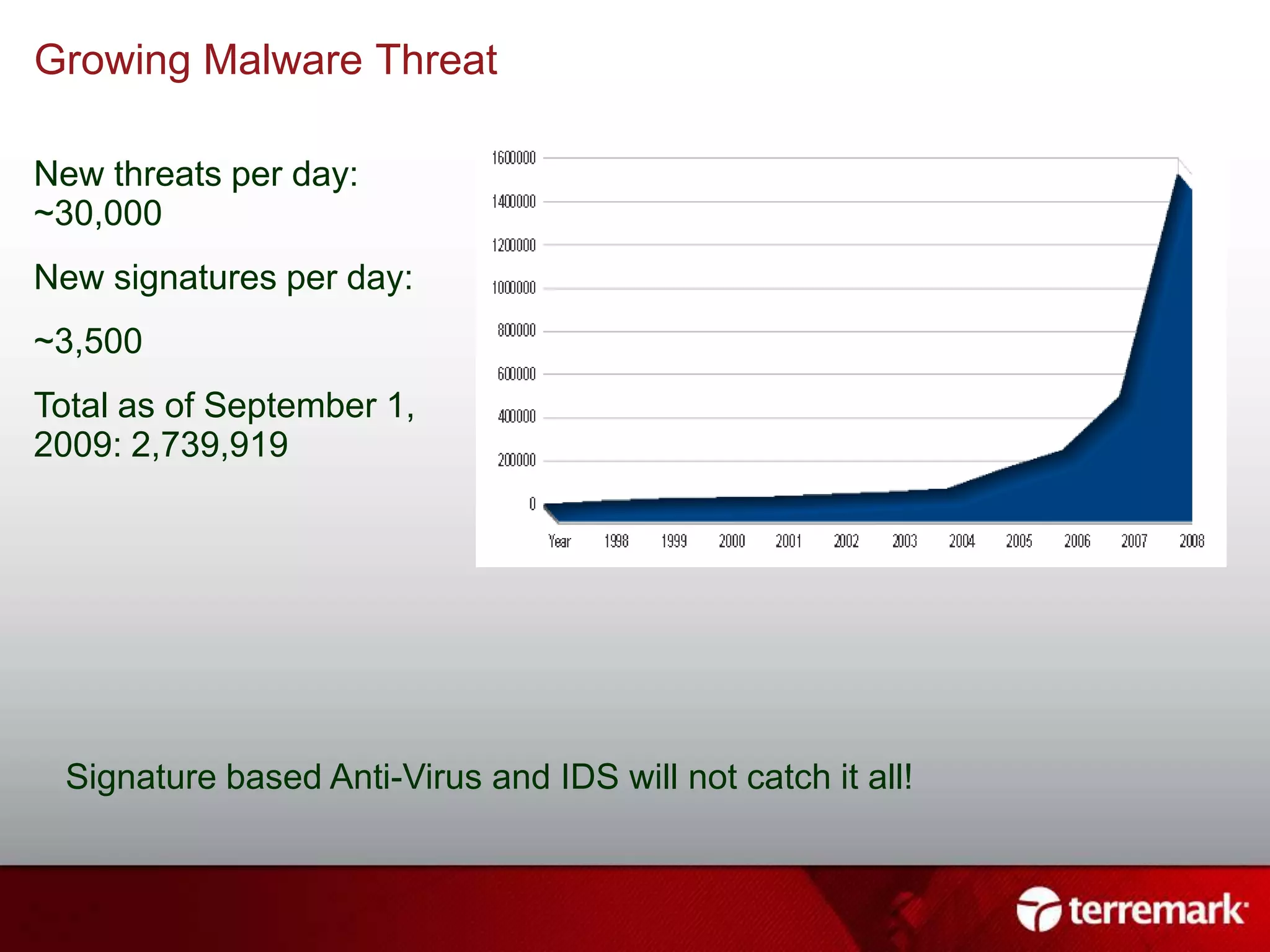
This document summarizes an information security presentation about emerging threats to infrastructure. It discusses growing malware threats, how attacks are carried out through social engineering and exploiting vulnerabilities, and advanced persistent threats targeting critical systems. It emphasizes that compliance does not equal security and organizations must focus on proactive security practices like patching, user awareness training, and incident response planning to defend against sophisticated attacks.