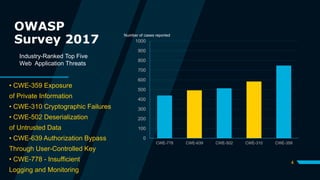
The document outlines Acme Payroll Company's (APC) implementation of threat modeling using the PASTA approach. It describes APC's systems, identifies potential threats, analyzes vulnerabilities, and proposes a strategy for conducting simulated attacks against APC's network and systems. The strategy involves scanning for vulnerabilities, attempting to exploit them using tools like Nessus and Metasploit, and using social engineering techniques like phishing emails to try and obtain credentials or sensitive information from employees. The goal is to help APC identify weaknesses before real attackers can compromise their systems.