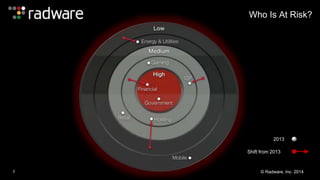
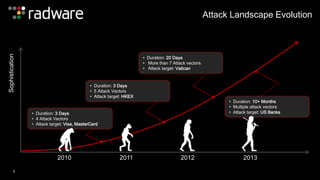
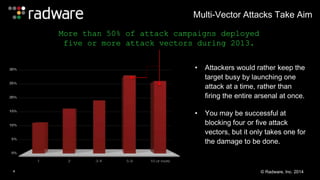
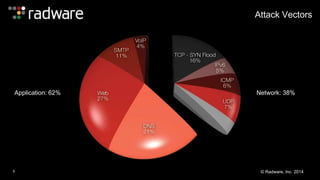
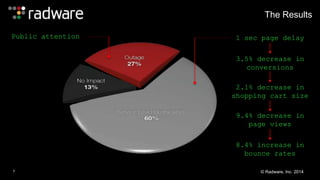
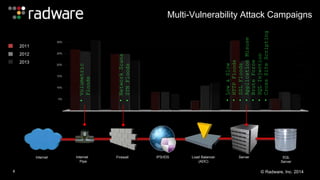
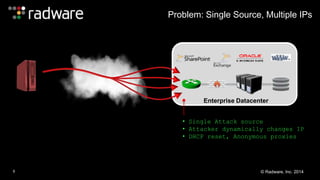
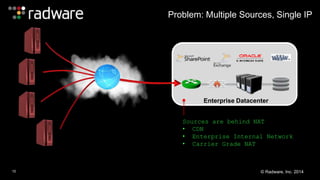
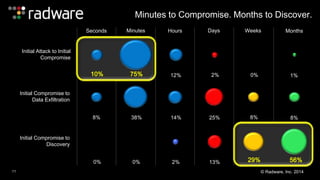
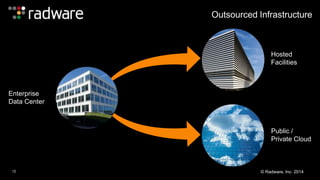
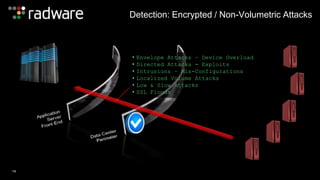
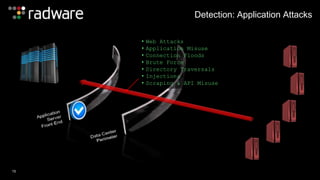
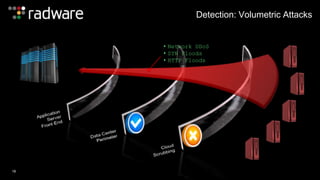
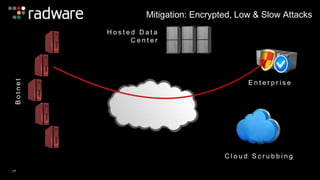
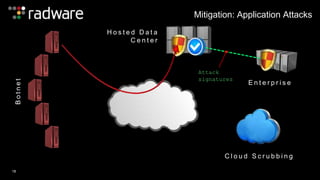
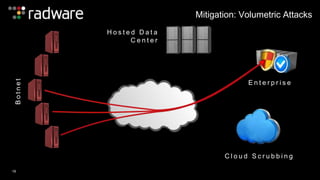
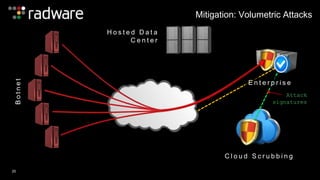
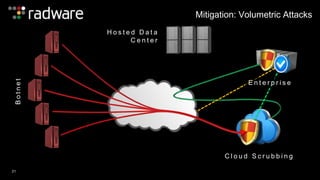
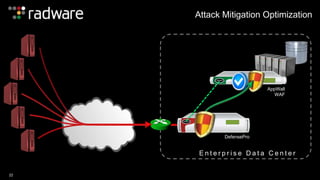
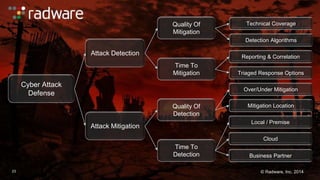
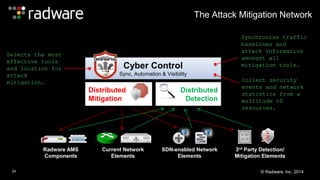
The document outlines the increasing sophistication and multi-vector nature of cyber attacks, emphasizing that over 50% of attacks in 2013 involved multiple vectors. It highlights the dangers of encrypted web application attacks and the importance of detecting and mitigating threats effectively, noting significant impacts on businesses such as reduced conversions and increased bounce rates. Recommendations for cyber attack readiness include understanding vulnerabilities, ensuring data protection, and utilizing expert resources for effective defense.