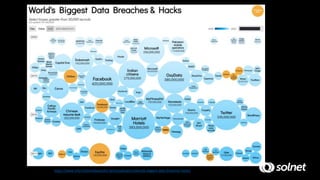
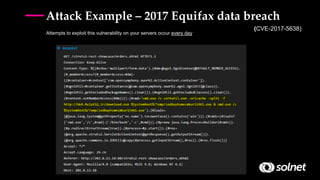
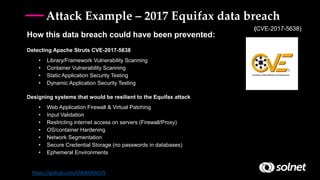
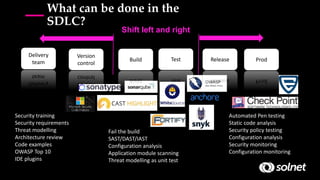
DevSecOps aims to integrate security practices into DevOps workflows to deliver value faster and safer. It addresses challenges like keeping security practices aligned with continuous delivery models and empowered DevOps teams. DevSecOps incorporates security checks and tools into development pipelines to find and fix issues early. This helps prevent breaches like the 2017 Equifax hack, which exploited a known vulnerability. DevSecOps promotes a culture of collaboration, shared responsibility, and proactive security monitoring throughout the software development lifecycle.