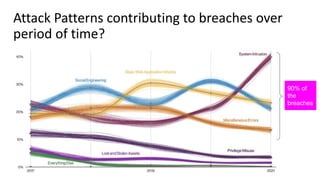
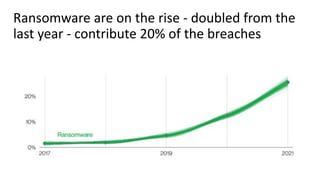
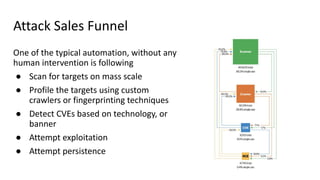
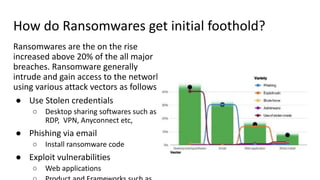
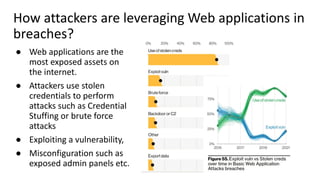
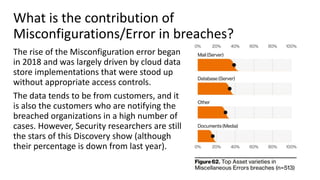
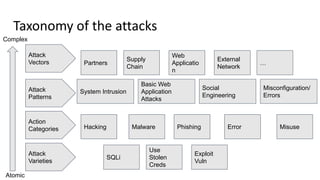
The document discusses over 3000 breaches, highlighting five attack vectors and the evolving tactics of attackers, particularly through web applications. Ransomware incidents have surged, with attackers leveraging stolen credentials, phishing, and vulnerabilities to gain initial access and install backdoors. It stresses the importance of continuous security assessments, improving visibility on misconfigurations, and adapting defense strategies to combat the complexity and unpredictability of modern cyber threats.


![System Intrusion: JMX Remote Code Execution
Domain
[demobank.co
m]
Subdomain
Discovery
[telesales.demo
bank.com]
Web App Endpoint
Discovery
[https://telesales.demoban
k.com:8080/index.html]
Technology
Detection
[Jboss 3.x]
Active Scanning
specific to
Jboss
JMX Console
[/jmx_console]
Default
Credentials
+
JMX
Console
Admin
Access
Remote
Code
Execution](https://image.slidesharecdn.com/5attackvectorsbehind3000breaches-221226071923-469b20a0/85/5-attack-vectors-behind-3000-breaches-pdf-6-320.jpg)
![Multi Stage Attack: Mobile Portal Access
Domain
[demobank.co
m]
Mobile App
Discovery
[ozone app]
API Endpoints
[https://services.demoban
k.com/AdStringO/info]
Directory
Traversal
Vulnerability
Log Files
Discovery
High Entropy
Strings
Detection
Plaintext
Credentials
Internal Web
Application
Endpoint
[mobile.demoba
nk.com]
+
Internal Web
Application
Admin Access](https://image.slidesharecdn.com/5attackvectorsbehind3000breaches-221226071923-469b20a0/85/5-attack-vectors-behind-3000-breaches-pdf-7-320.jpg)
![Multi Stage Attack: AWS Admin Access
Domain
[demobank.co
m]
Subdomain
Discovery
[telesales.demo
bank.com]
S3 Bucket Discovery
[https://telesales-prod.s3.a
mazonaws.com]
S3 Content
Download &
Analysis
Dev Mobile APK
Discovery
[dev-telesales.a
pk]
Web App
Endpoint
Discovery
[https://profile.d
emobank.com]
SSRF
Vulnerability
Detection [ Url
Param]
Low Privilege
AWS Keys
AWS Resources
Discovery
Internal S3
Bucket
Discovery
[internal-demob
ank]
S3 Content
Download &
Analysis
Remote
Code
Execution](https://image.slidesharecdn.com/5attackvectorsbehind3000breaches-221226071923-469b20a0/85/5-attack-vectors-behind-3000-breaches-pdf-8-320.jpg)