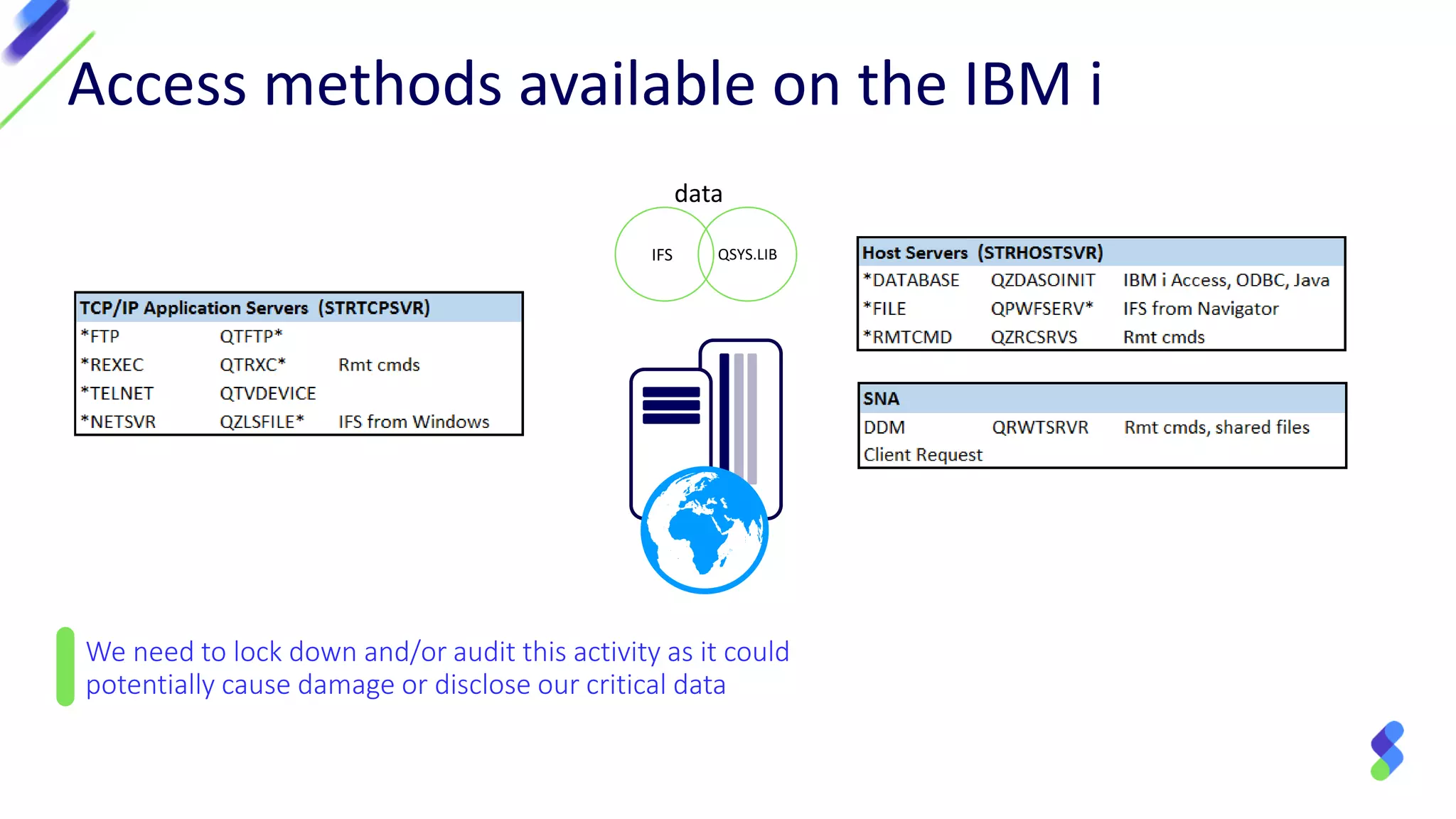
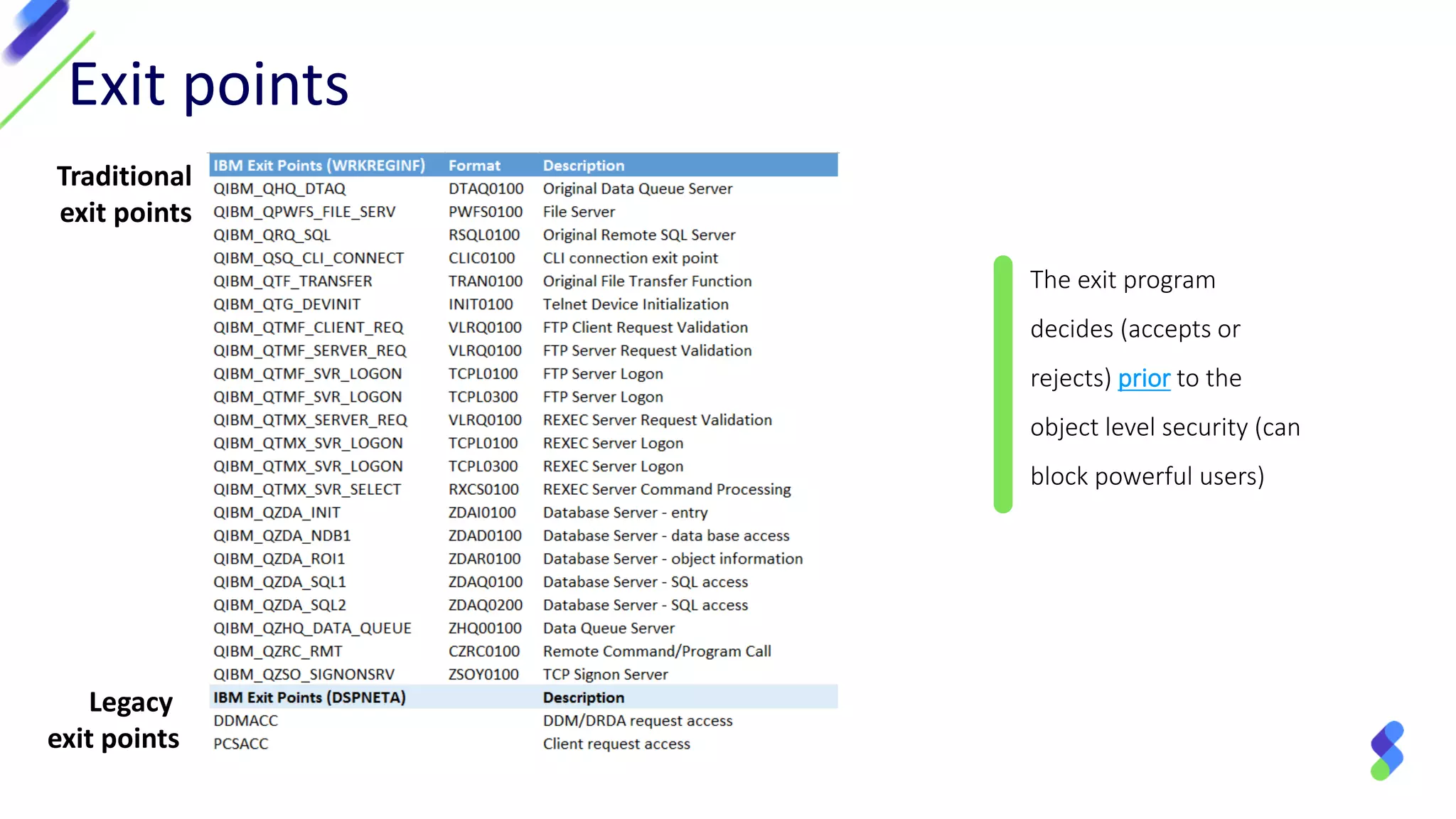
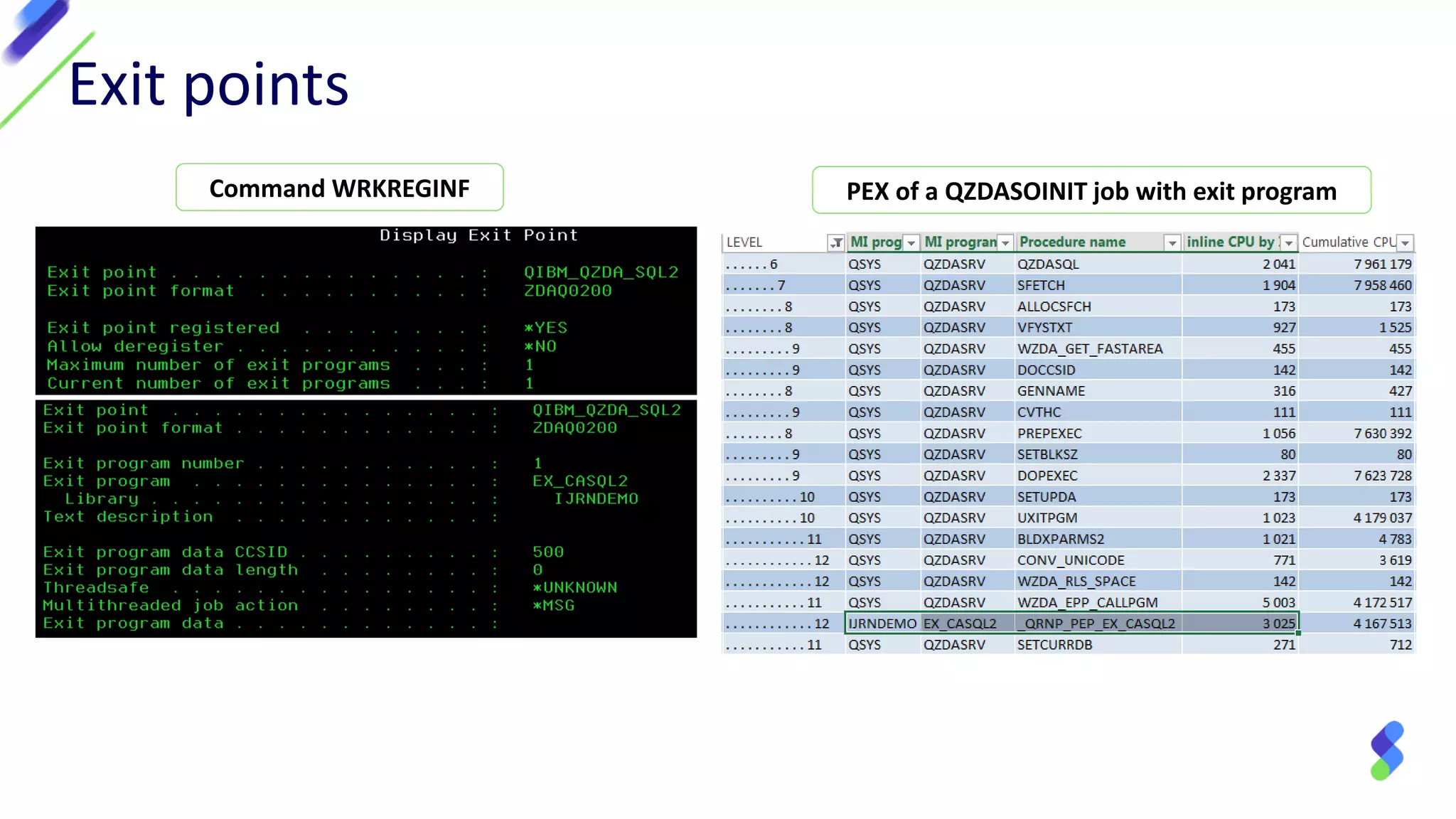
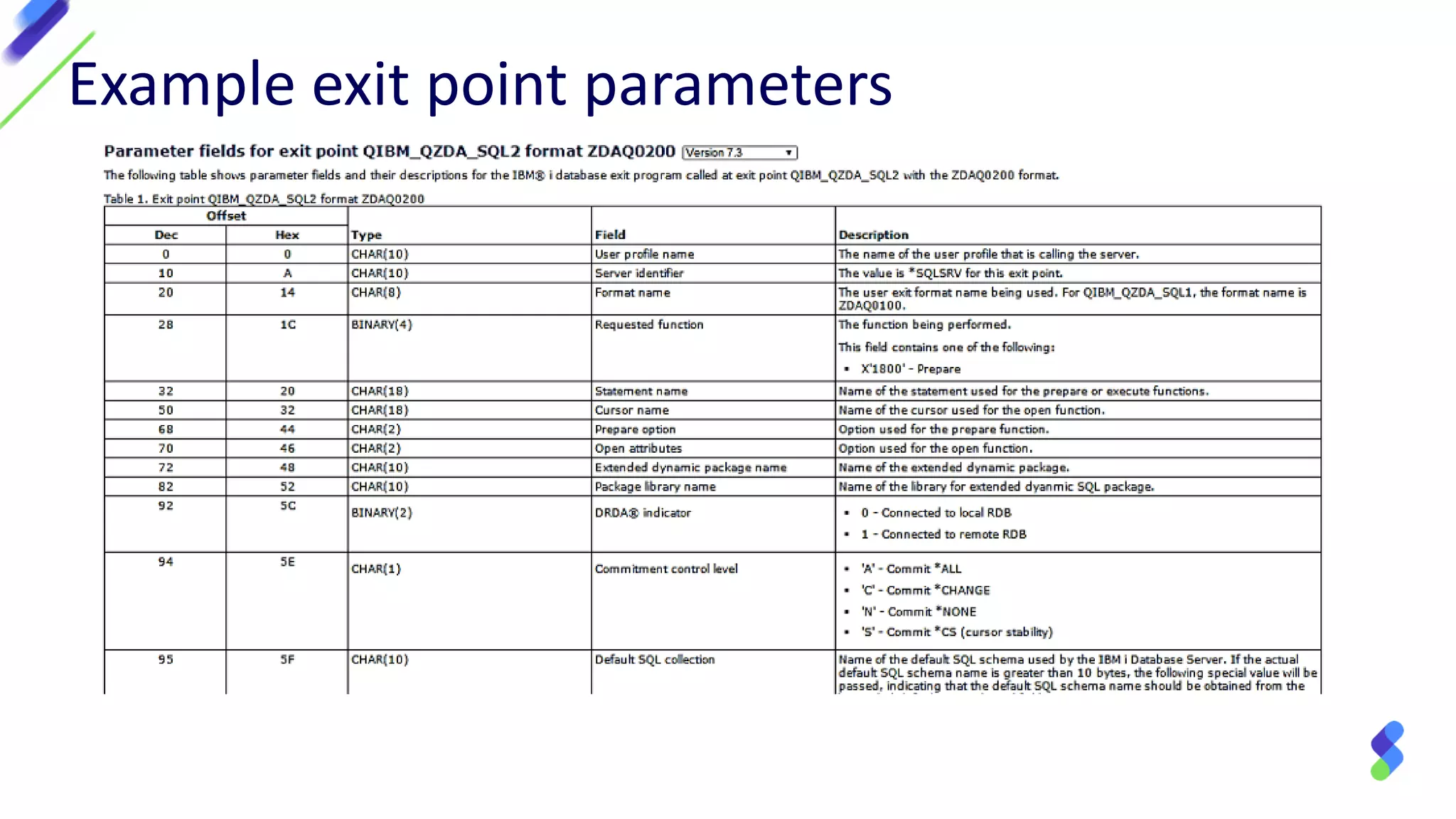
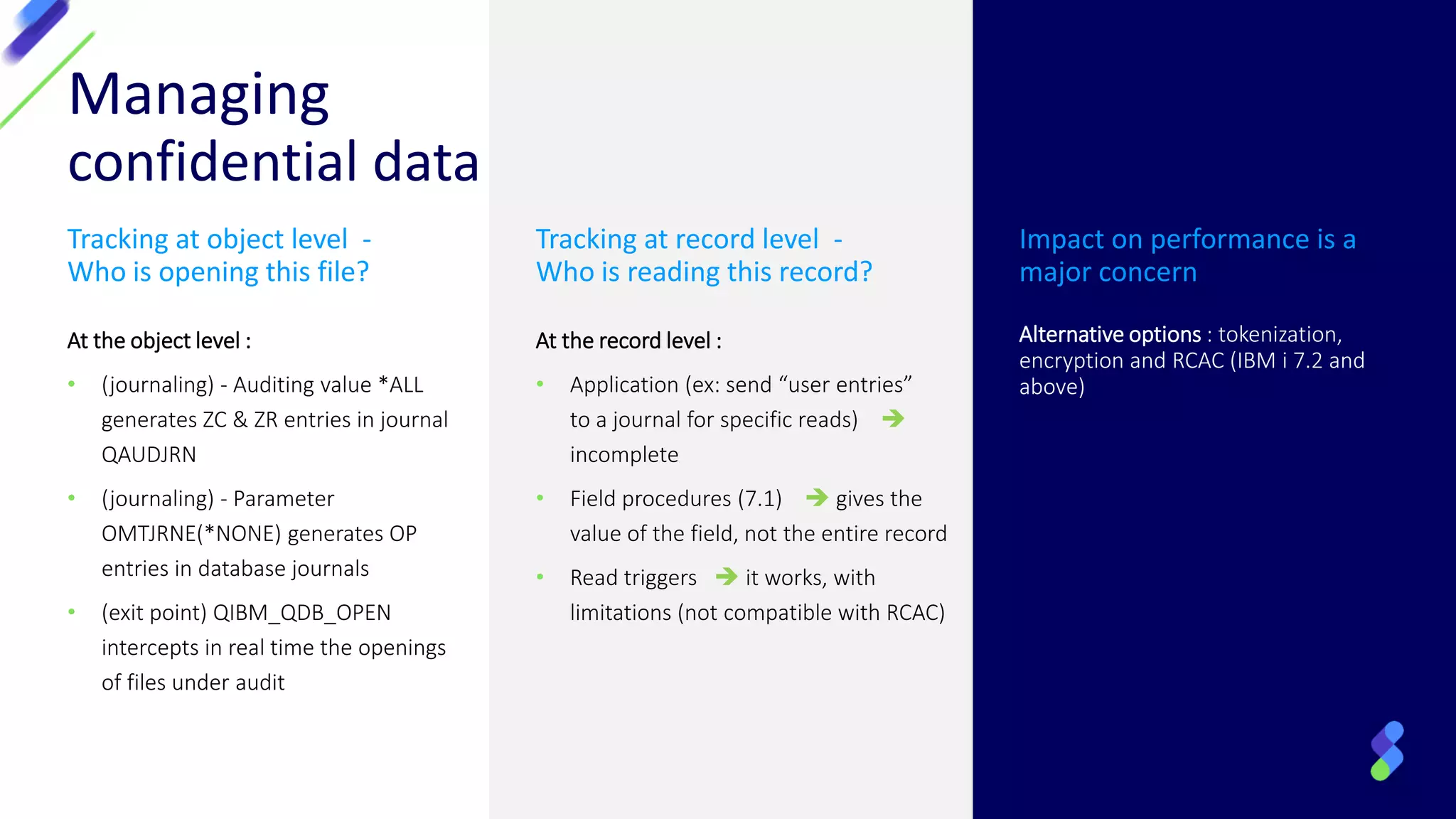
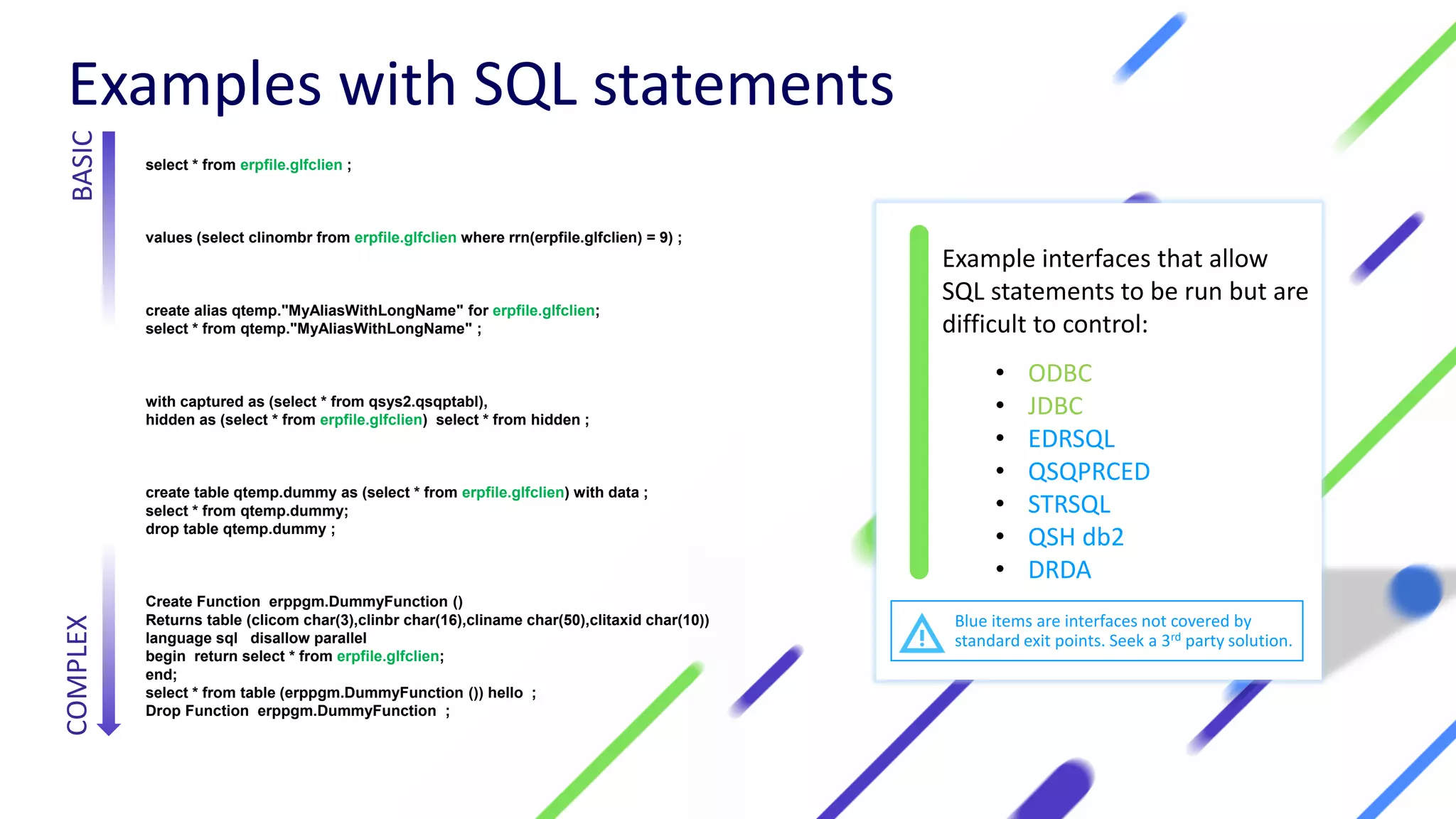
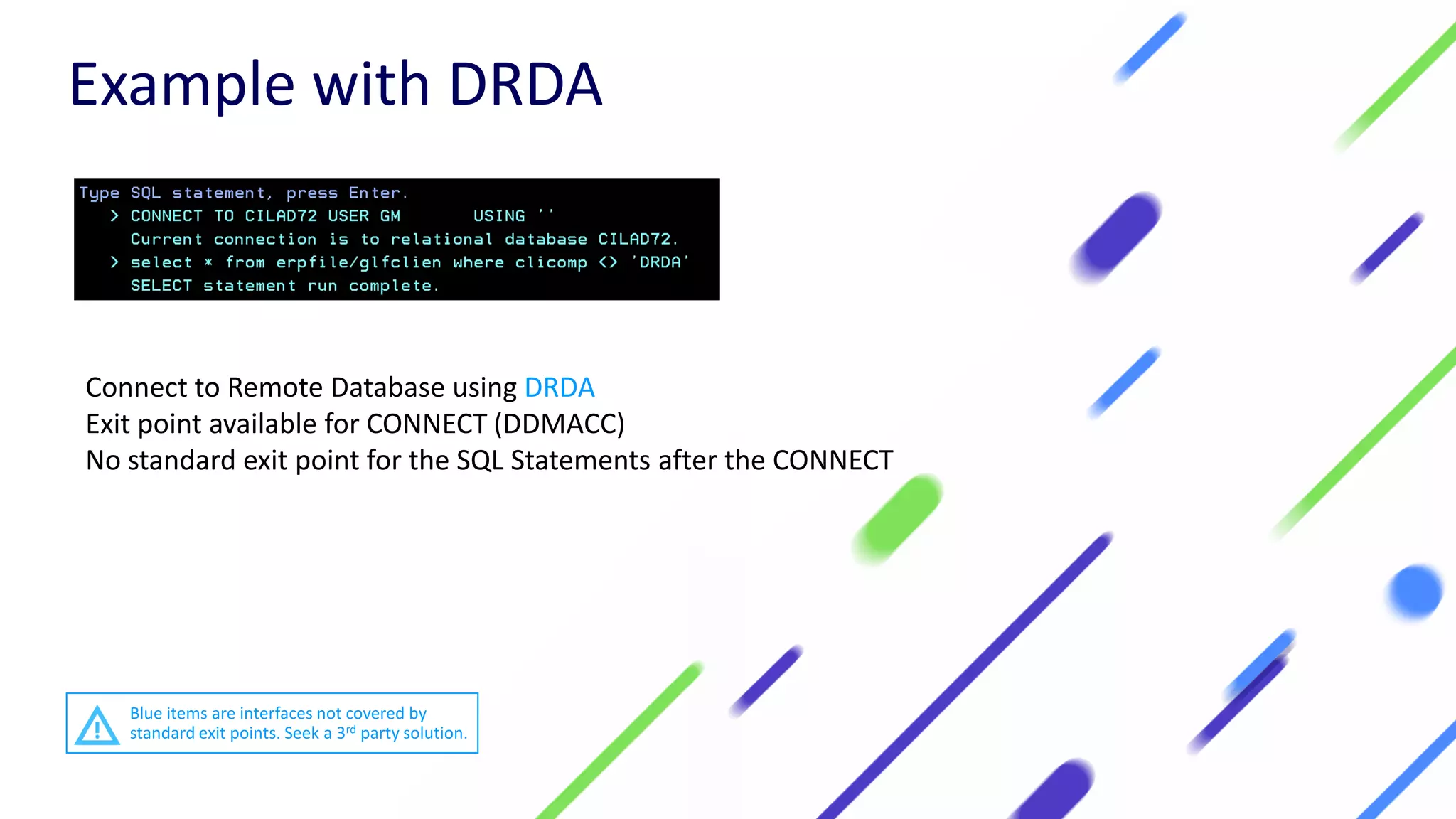
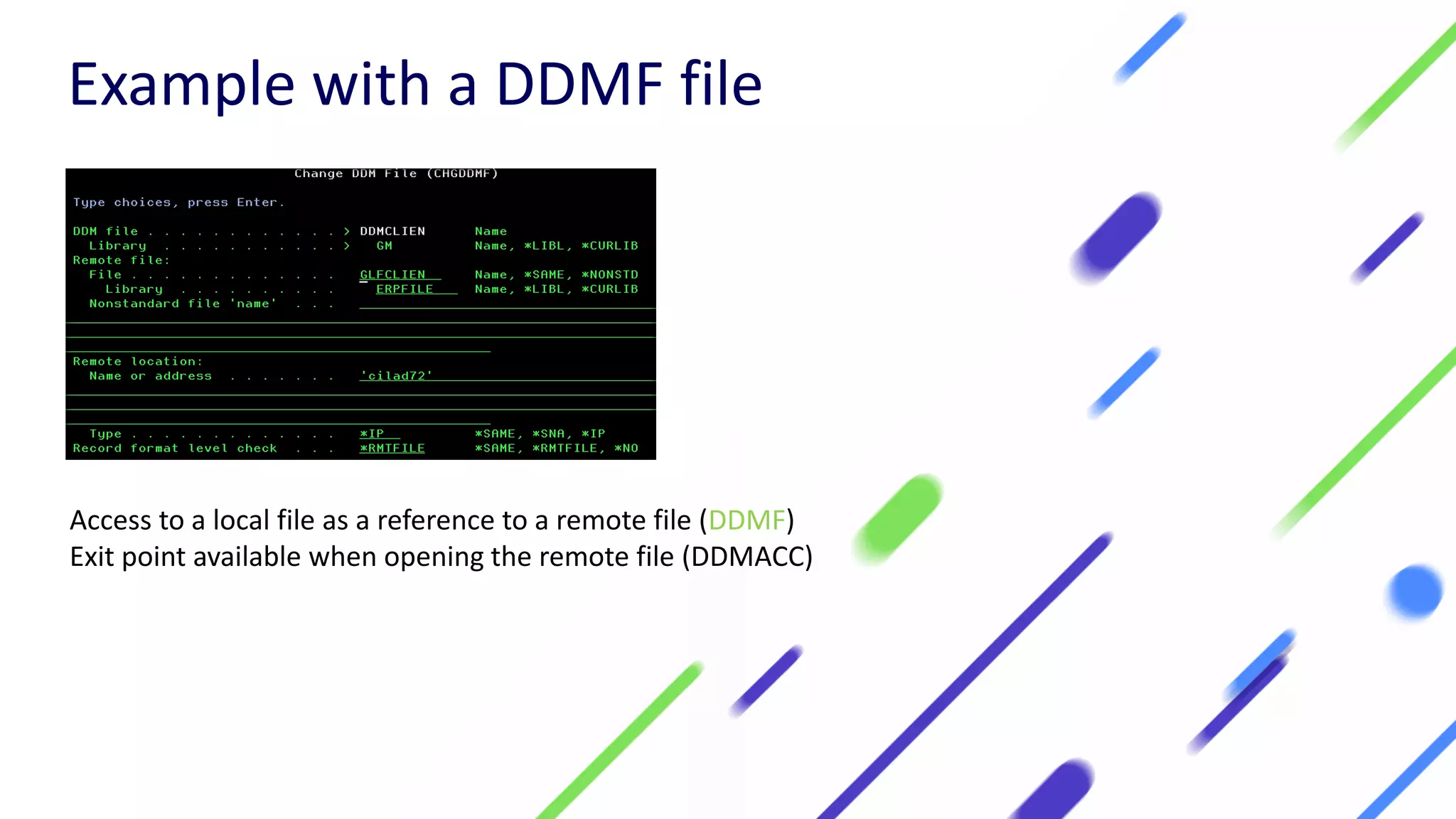
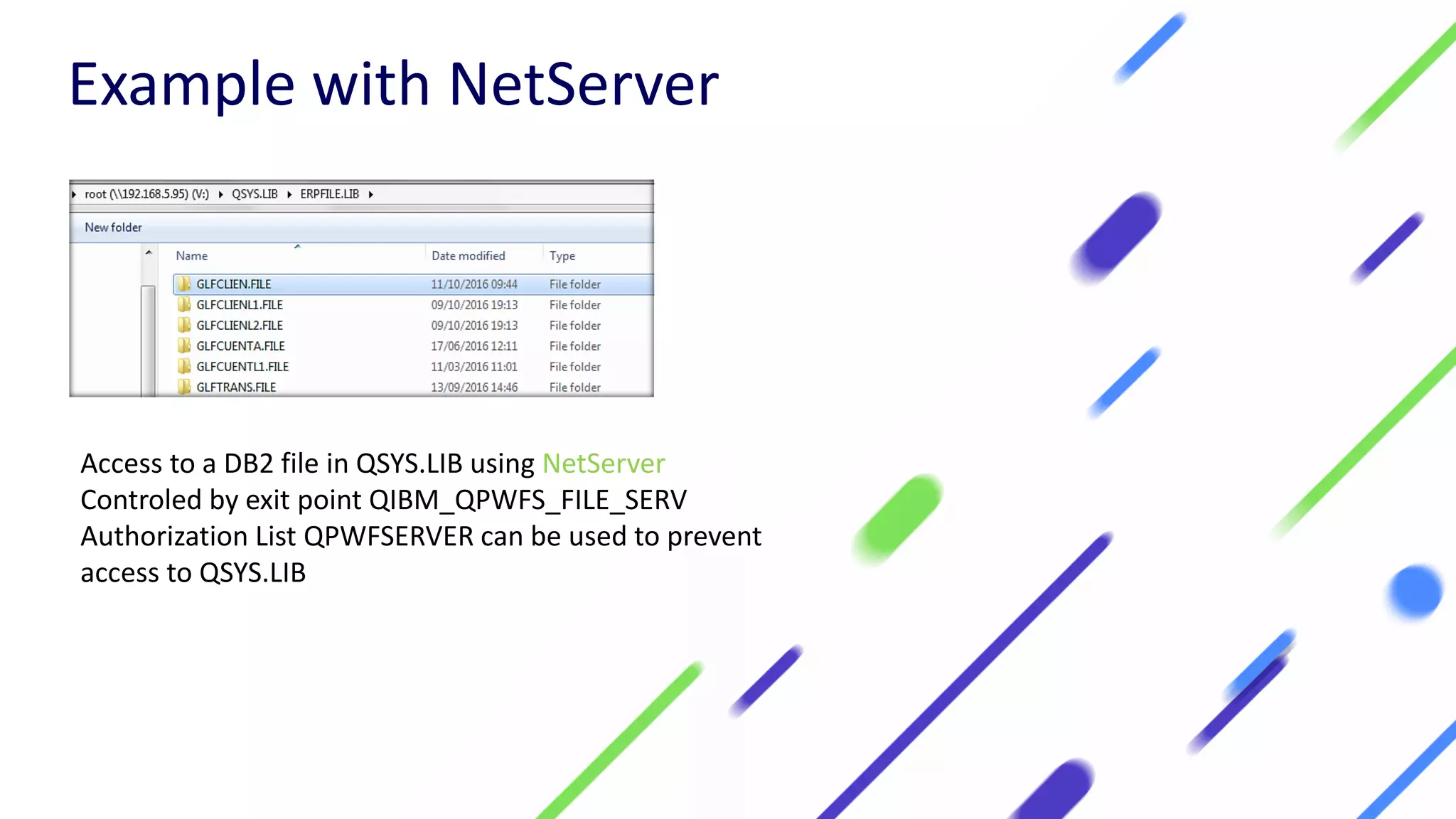
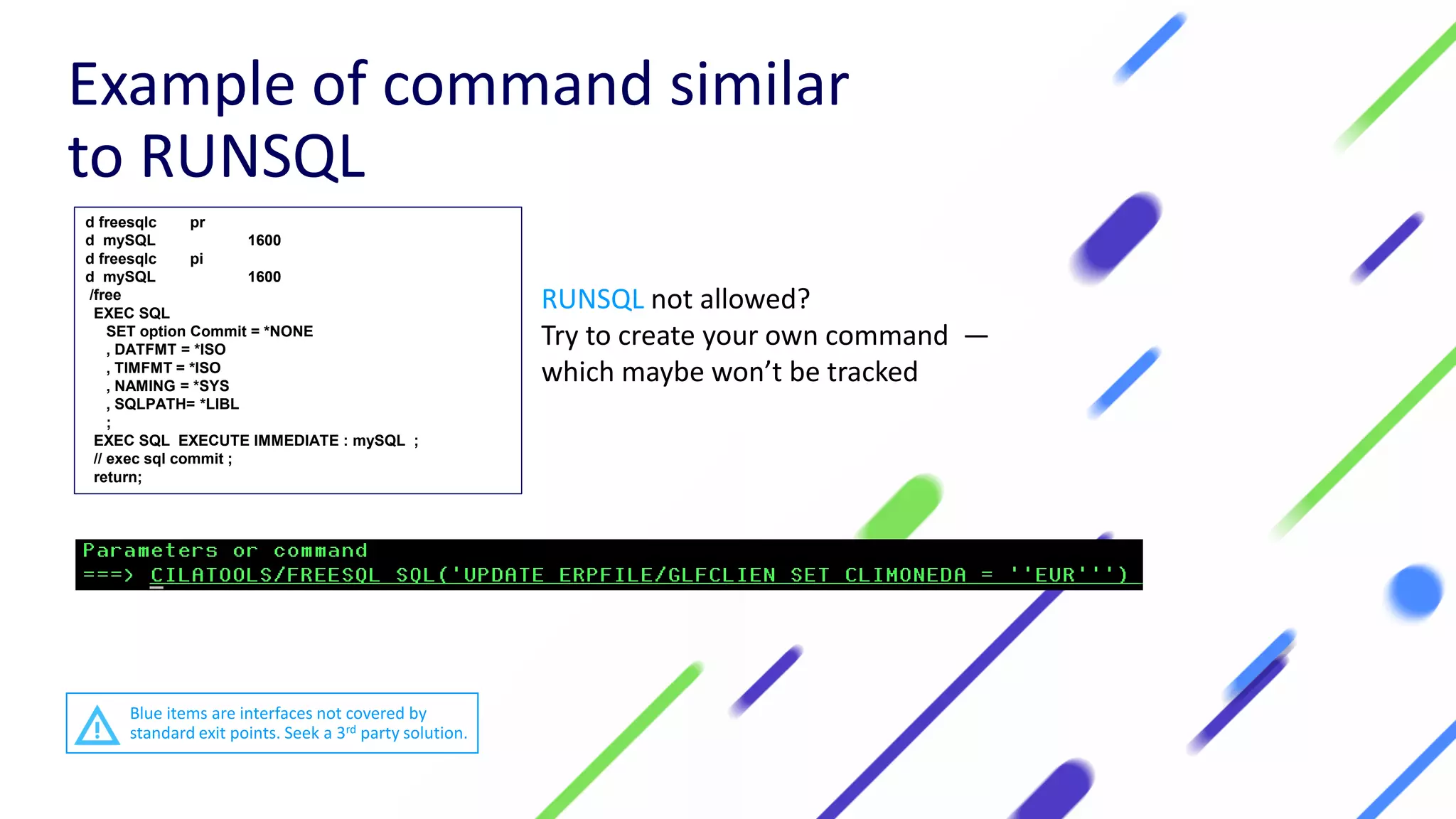
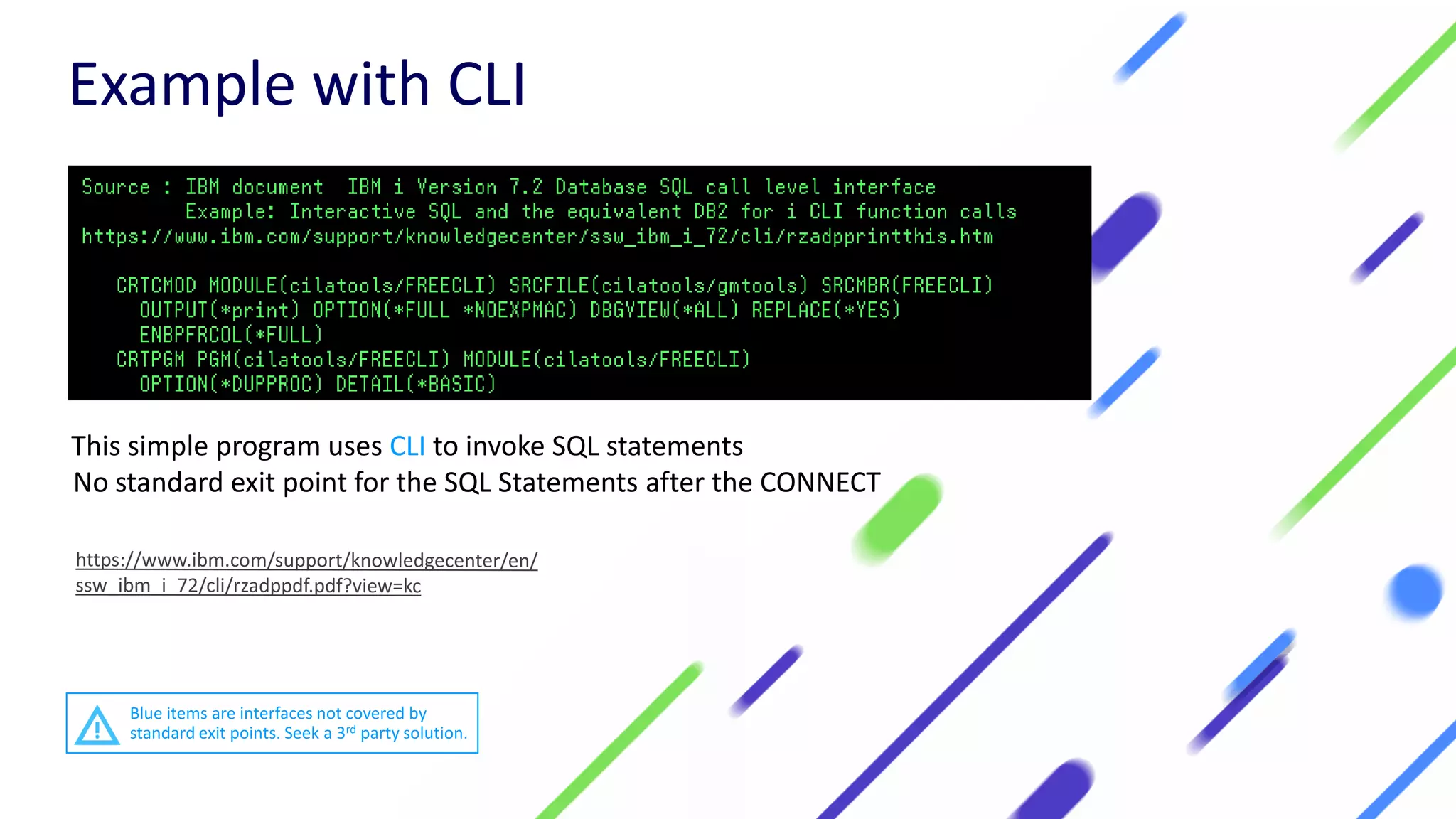
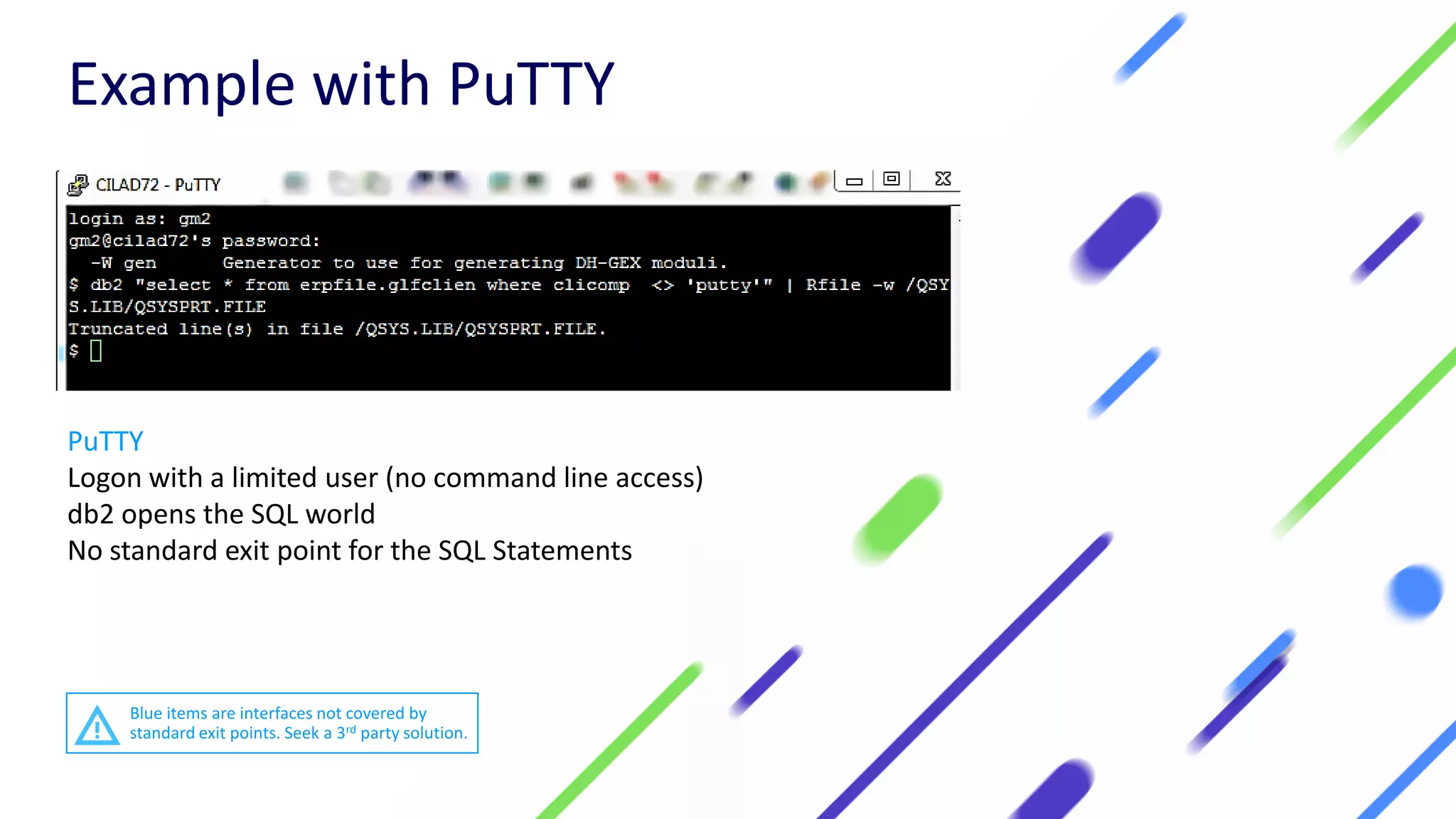
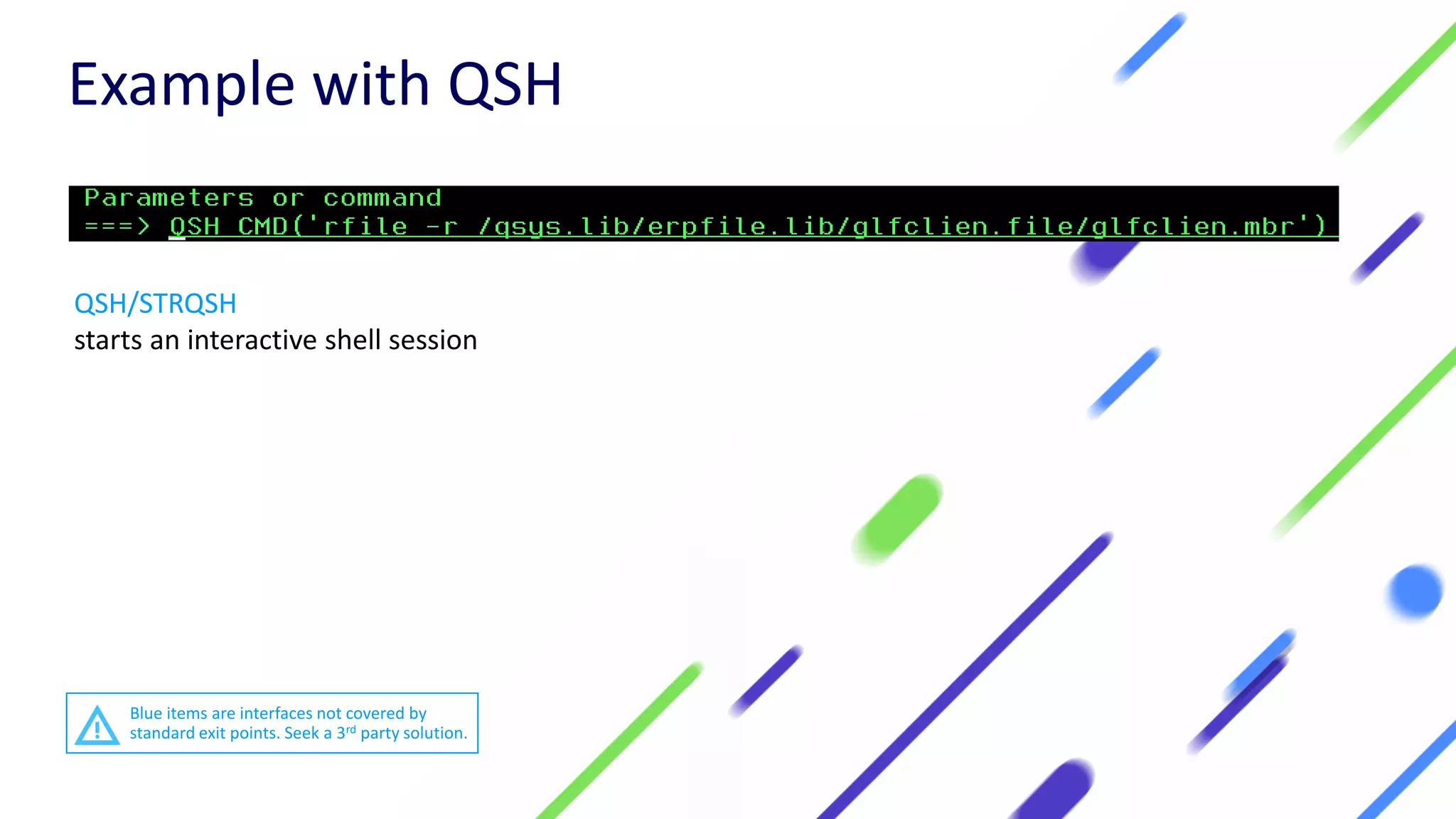
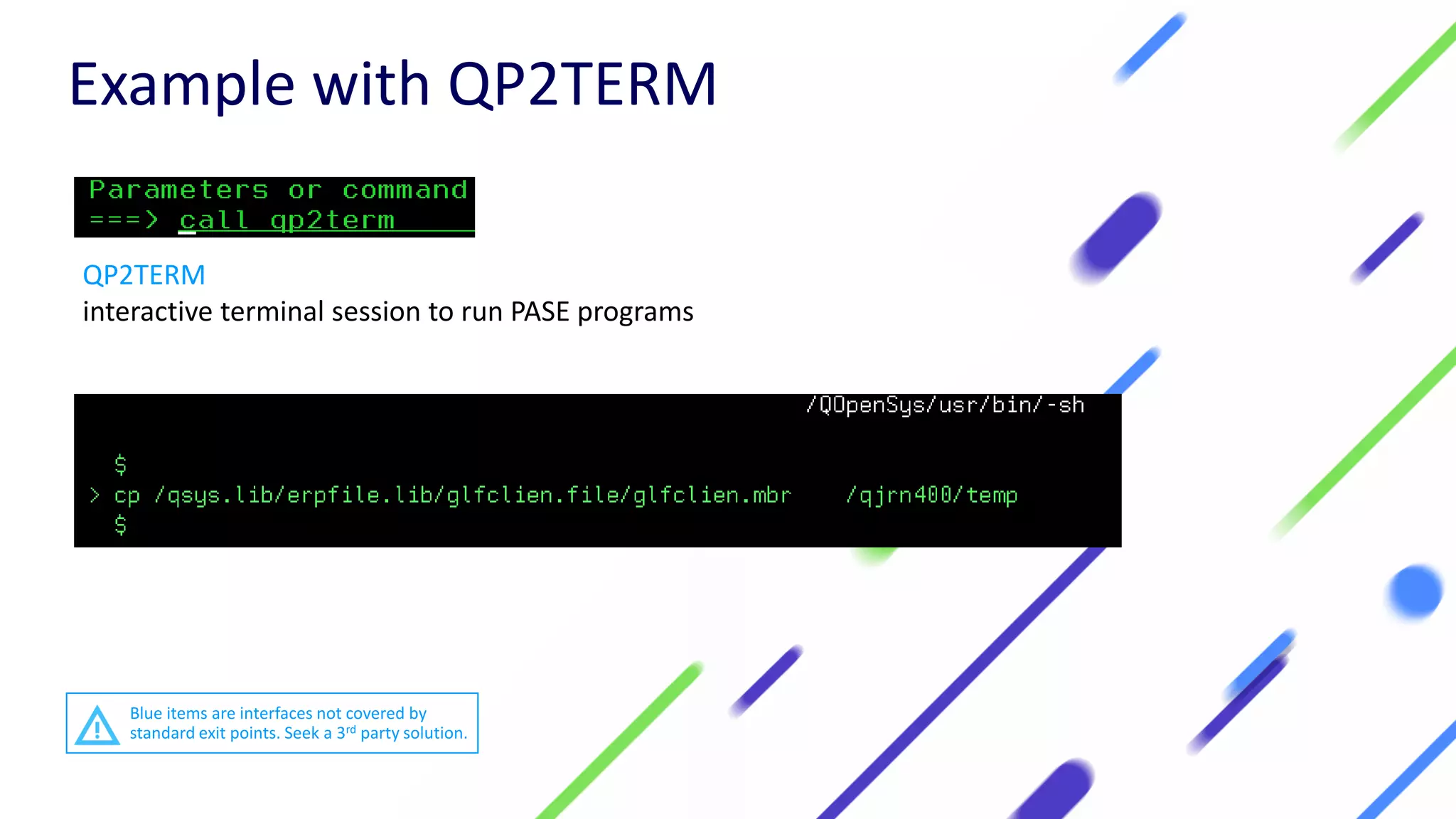
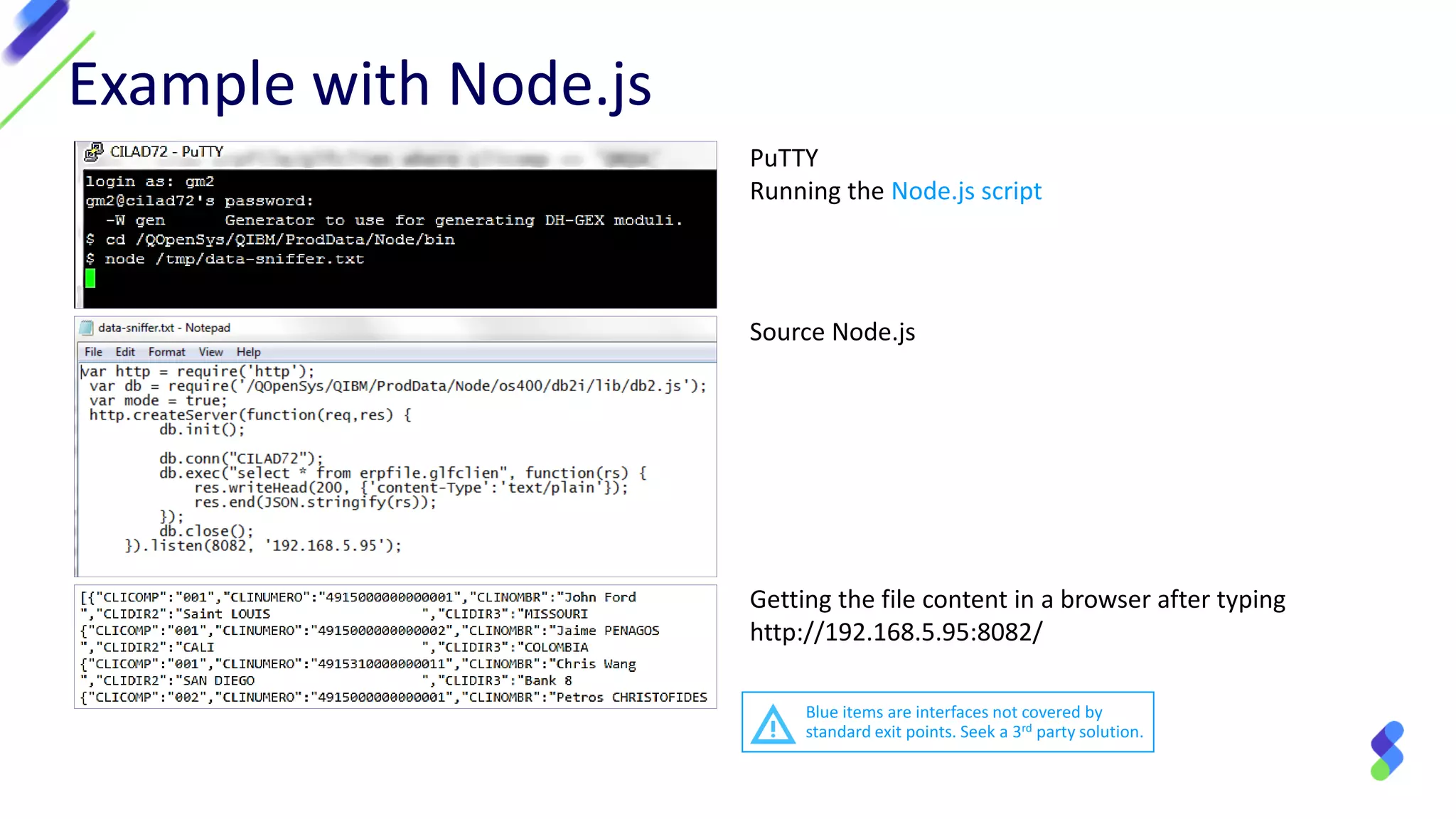
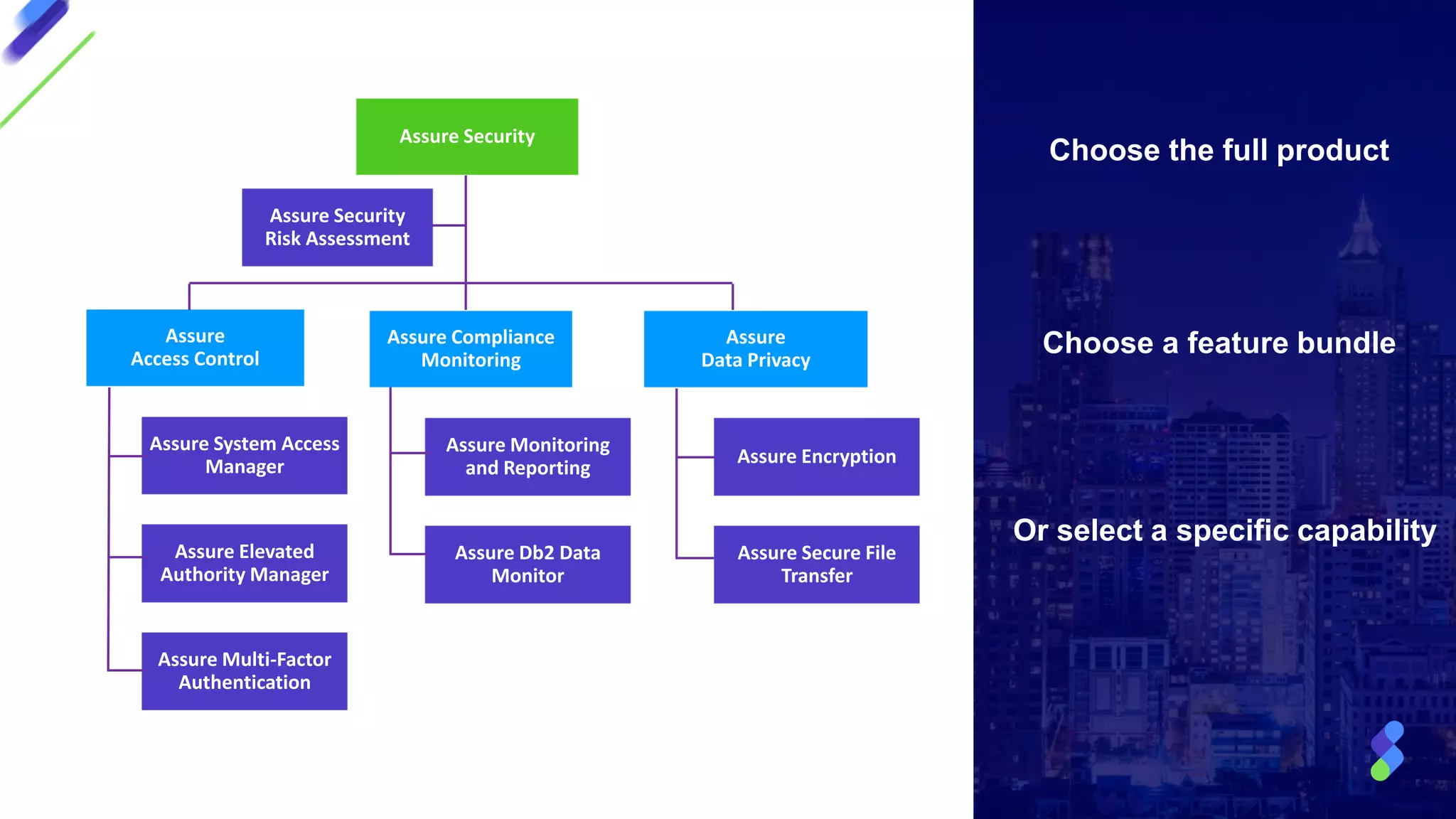
This document discusses expanding control of access to IBM i systems and data. It begins with some logistical information about the webcast. The presentation will discuss myths about IBM i security, exit points and access methods, examples of security issues, and how Syncsort can help with security. The agenda includes discussing the myth that IBM i is secure by nature, reviewing exit points and access methods, providing examples, and explaining how Syncsort can help manage security risks. Overall, the document aims to educate about security risks on IBM i and how third party solutions can help address vulnerabilities from various access methods and improve overall security.