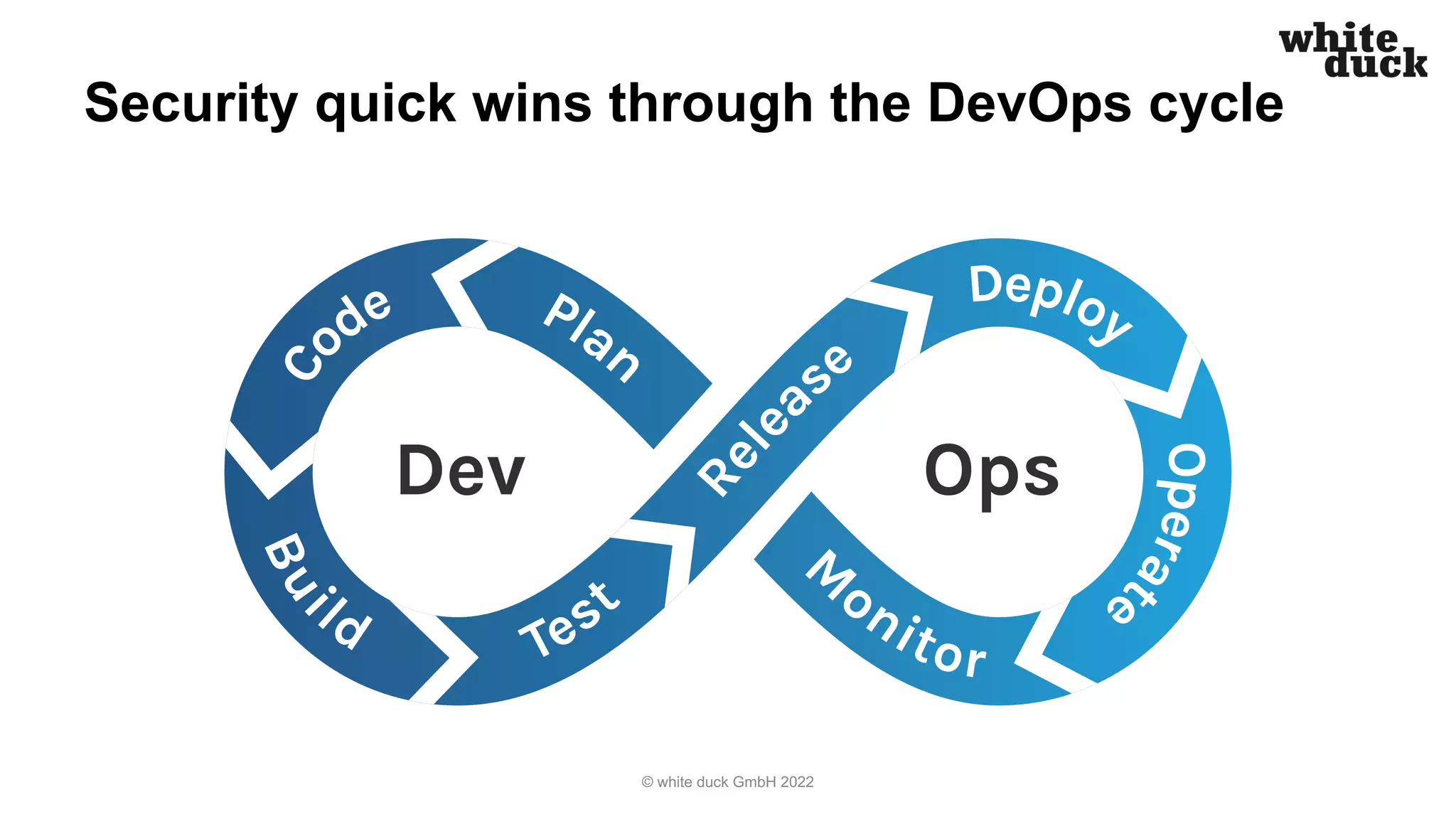
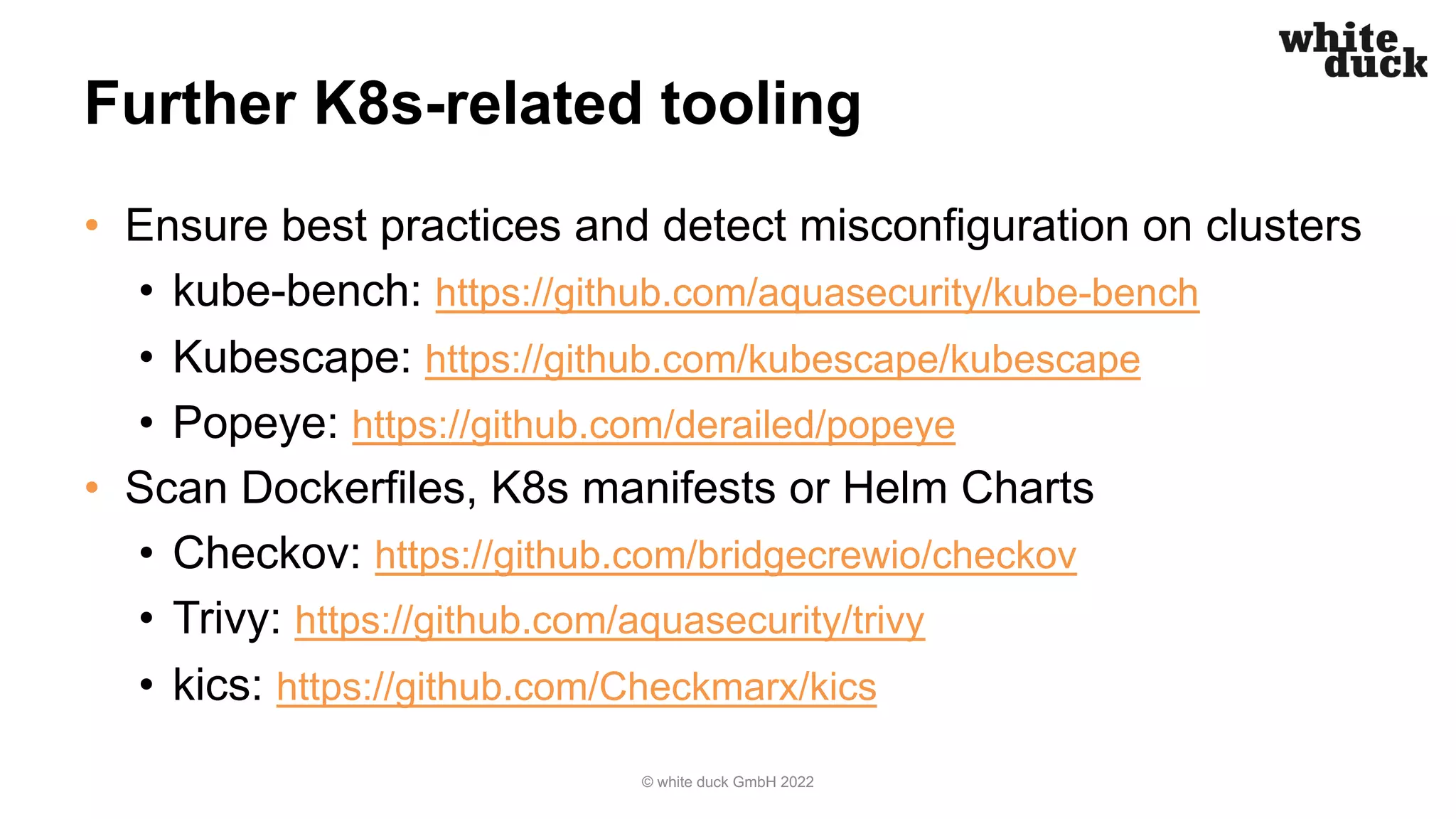
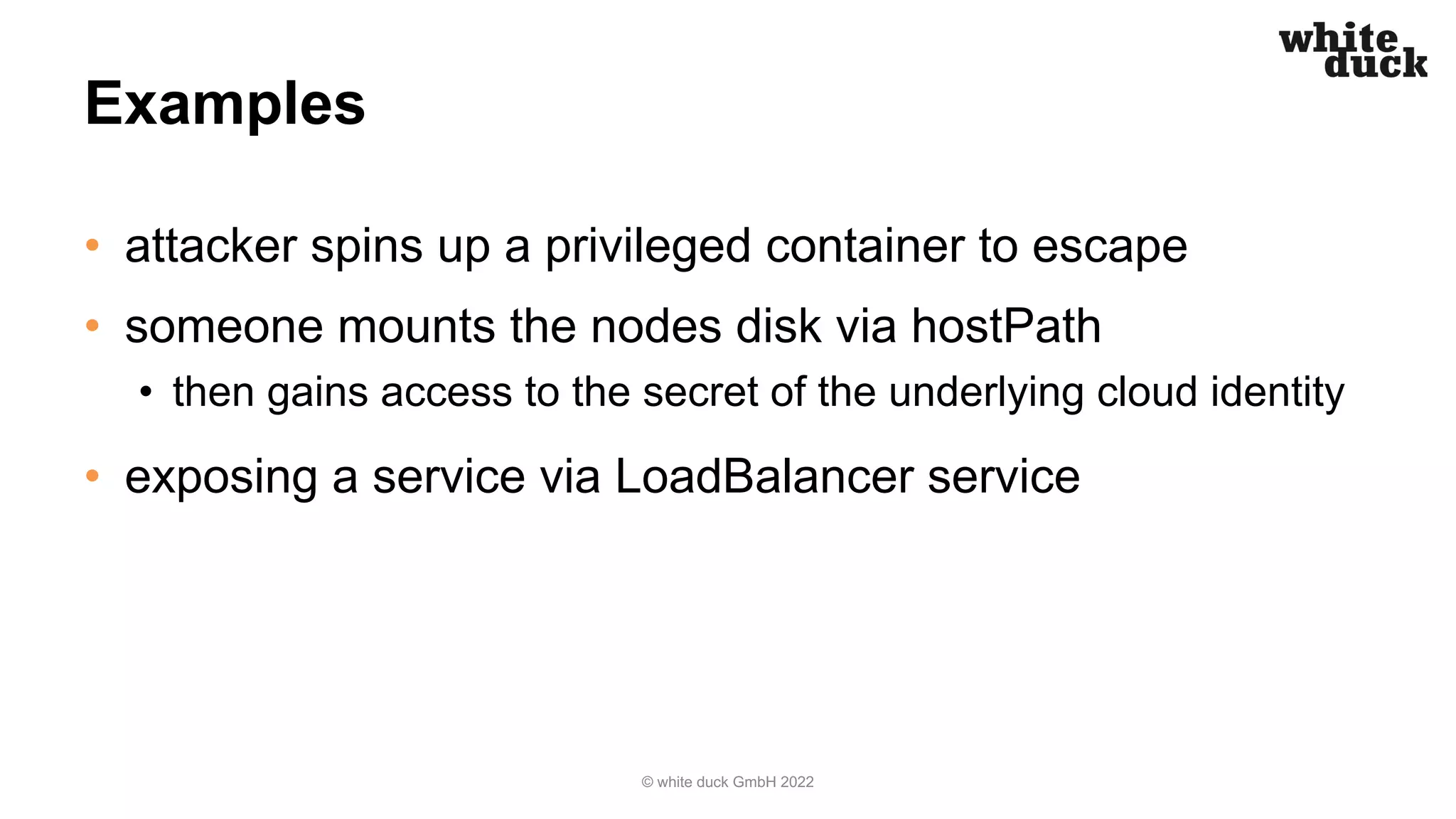
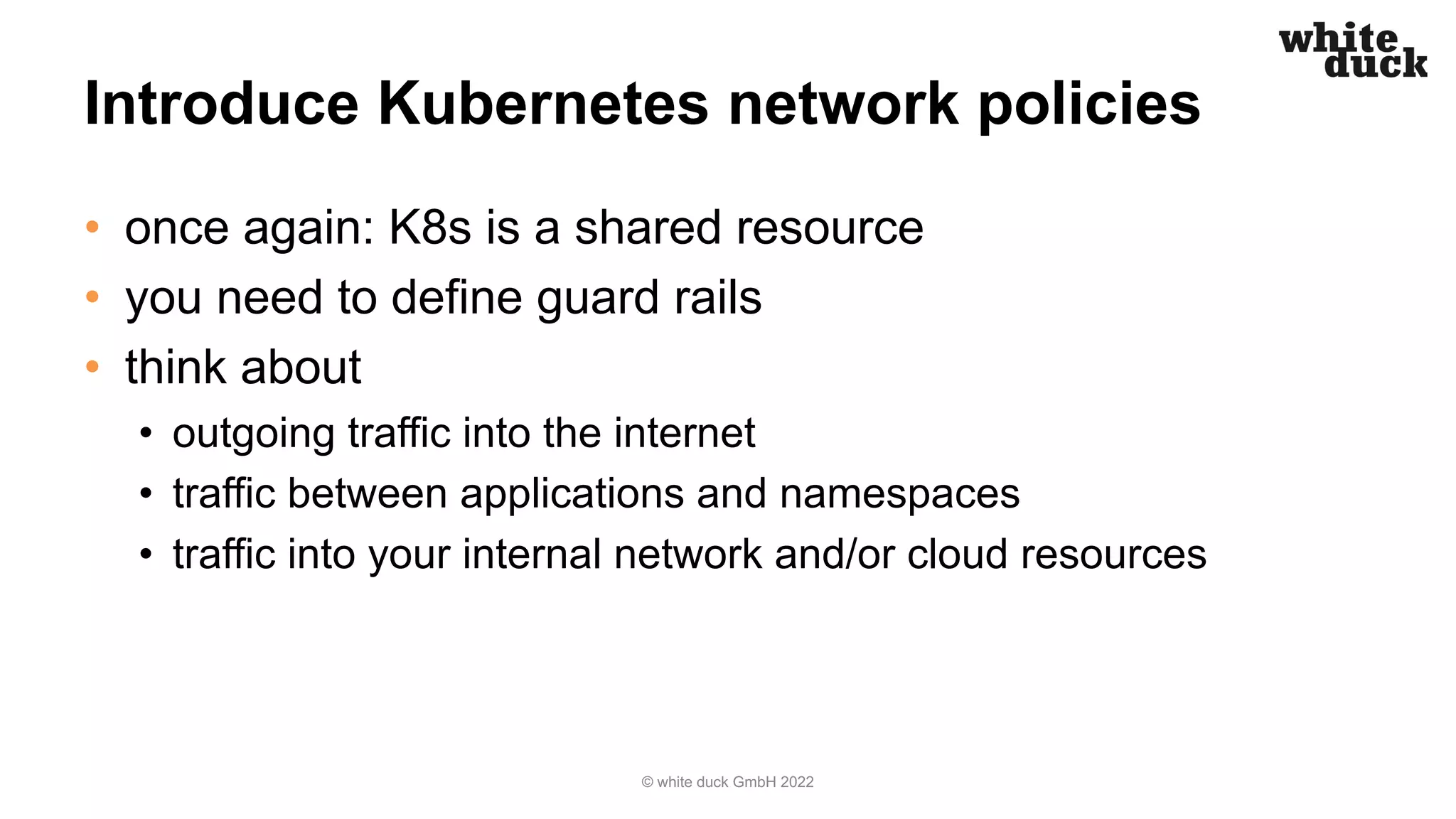
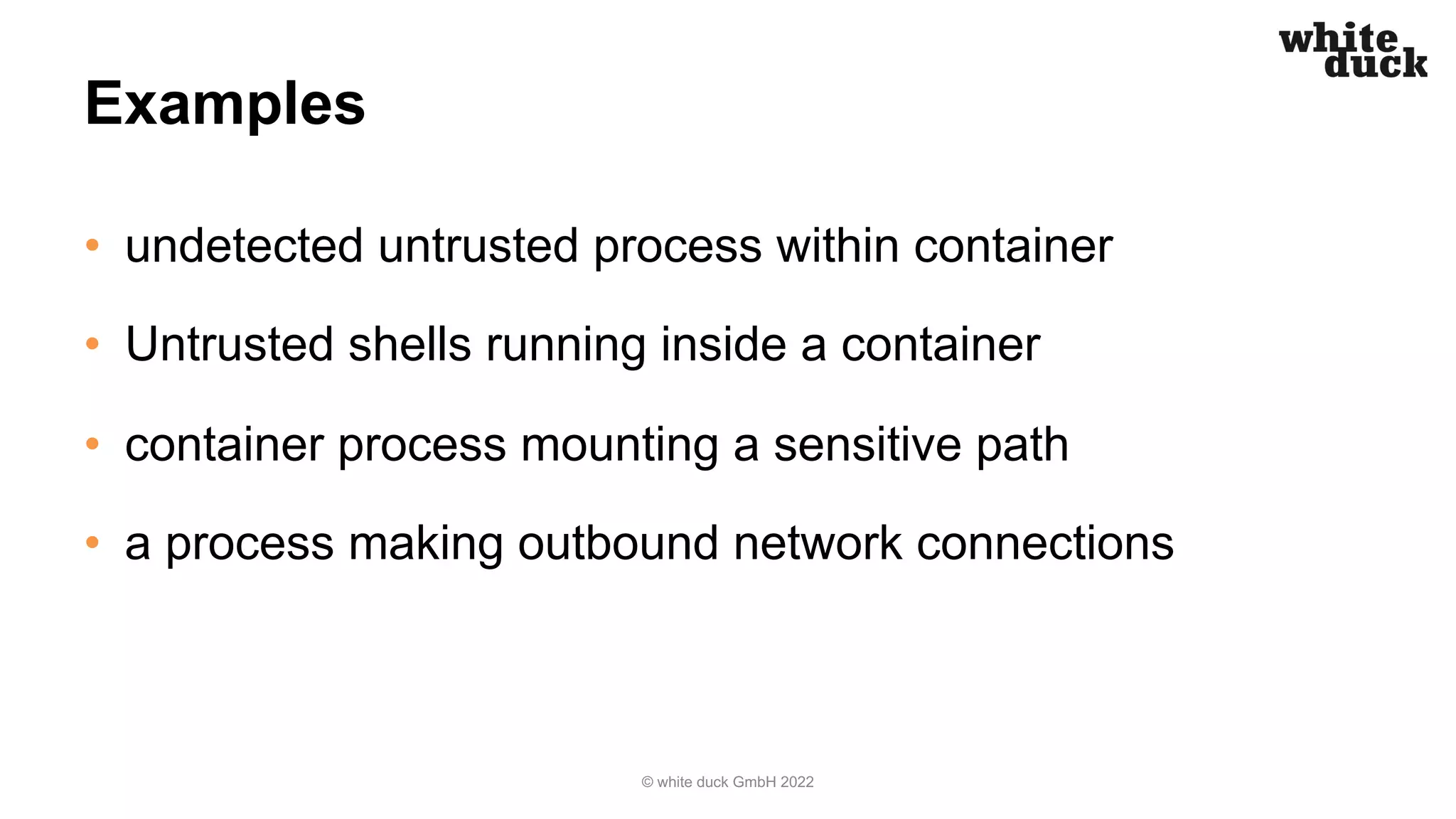
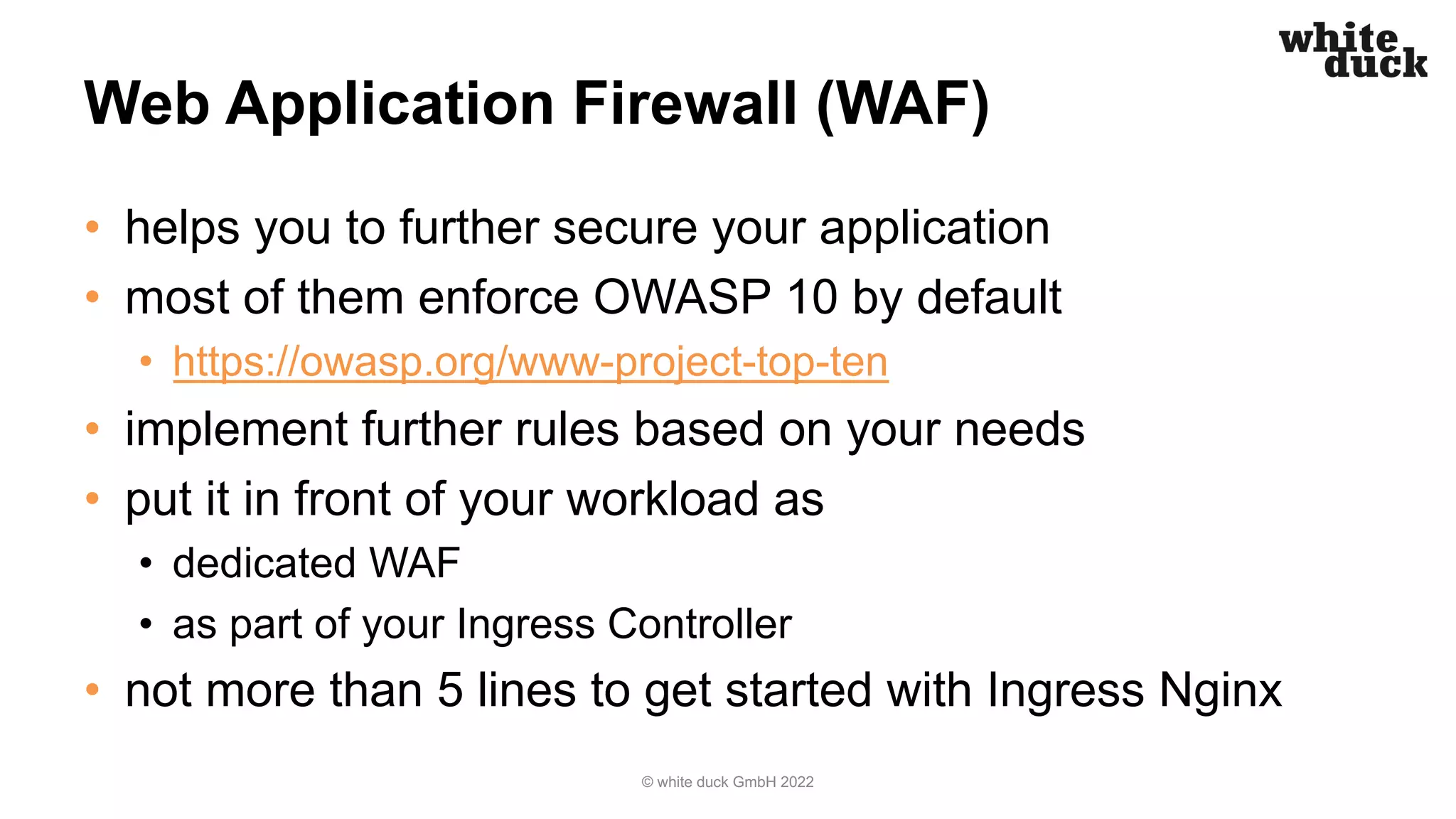
The document outlines strategies for securing Kubernetes clusters against hacking, emphasizing the importance of secure application code, implementing Kubernetes policies, and ensuring container runtime security. It discusses various tools for static application security testing, generating software bills of materials, and vulnerability scanning, as well as effective practices for managing network policies and service accounts. Additional recommendations include utilizing web application firewalls and maintaining security awareness through runtime monitoring tools.