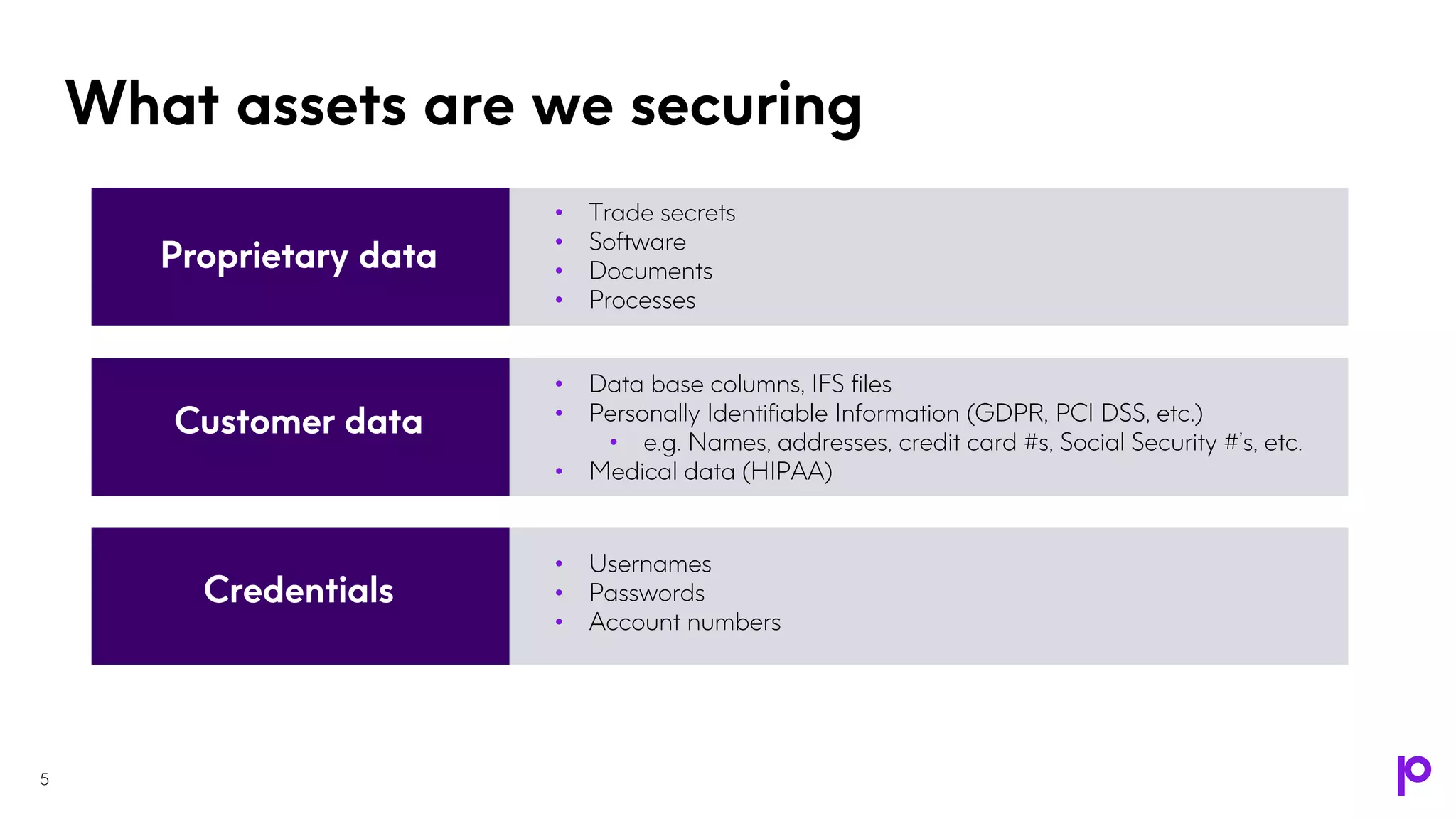
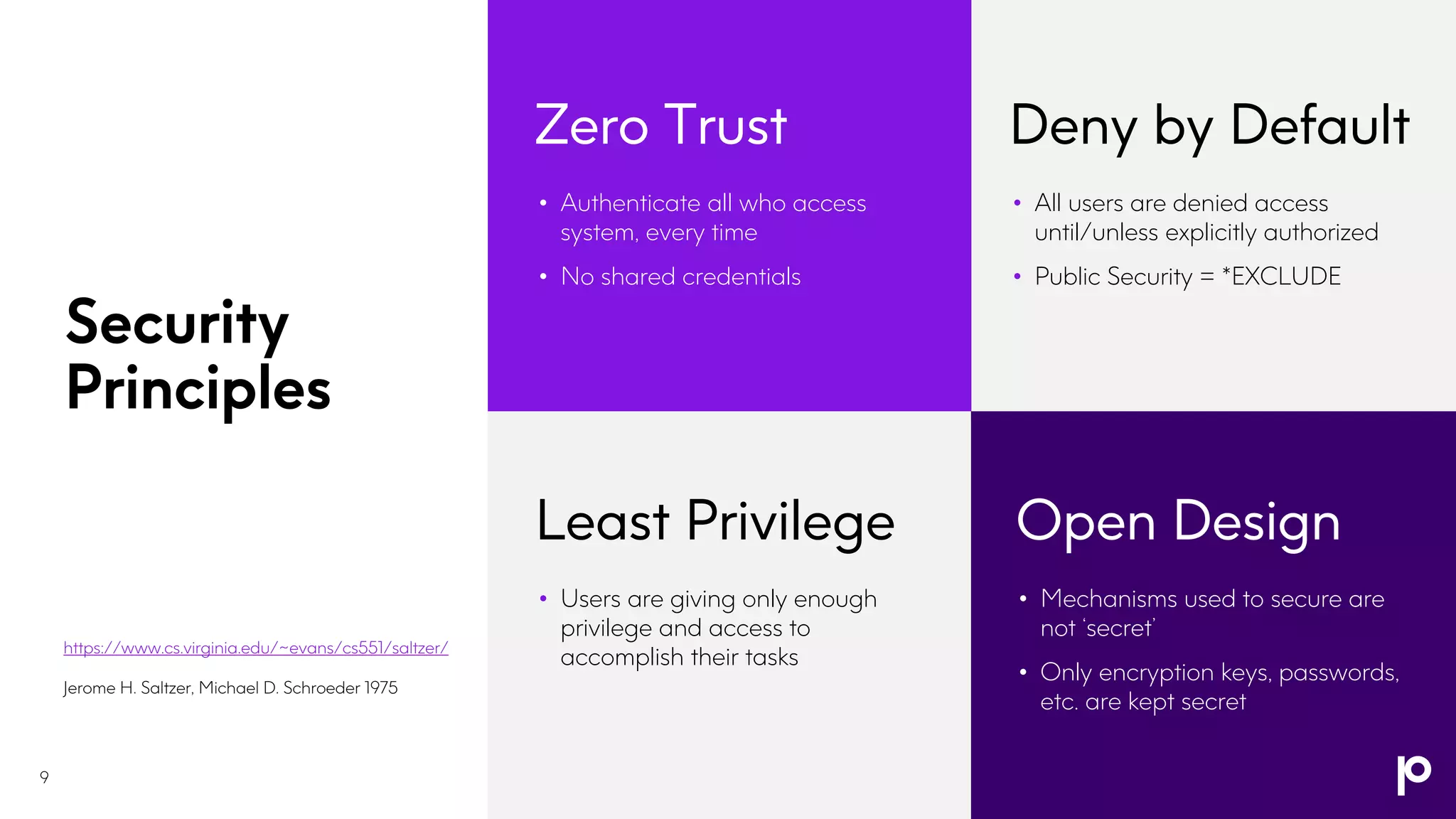
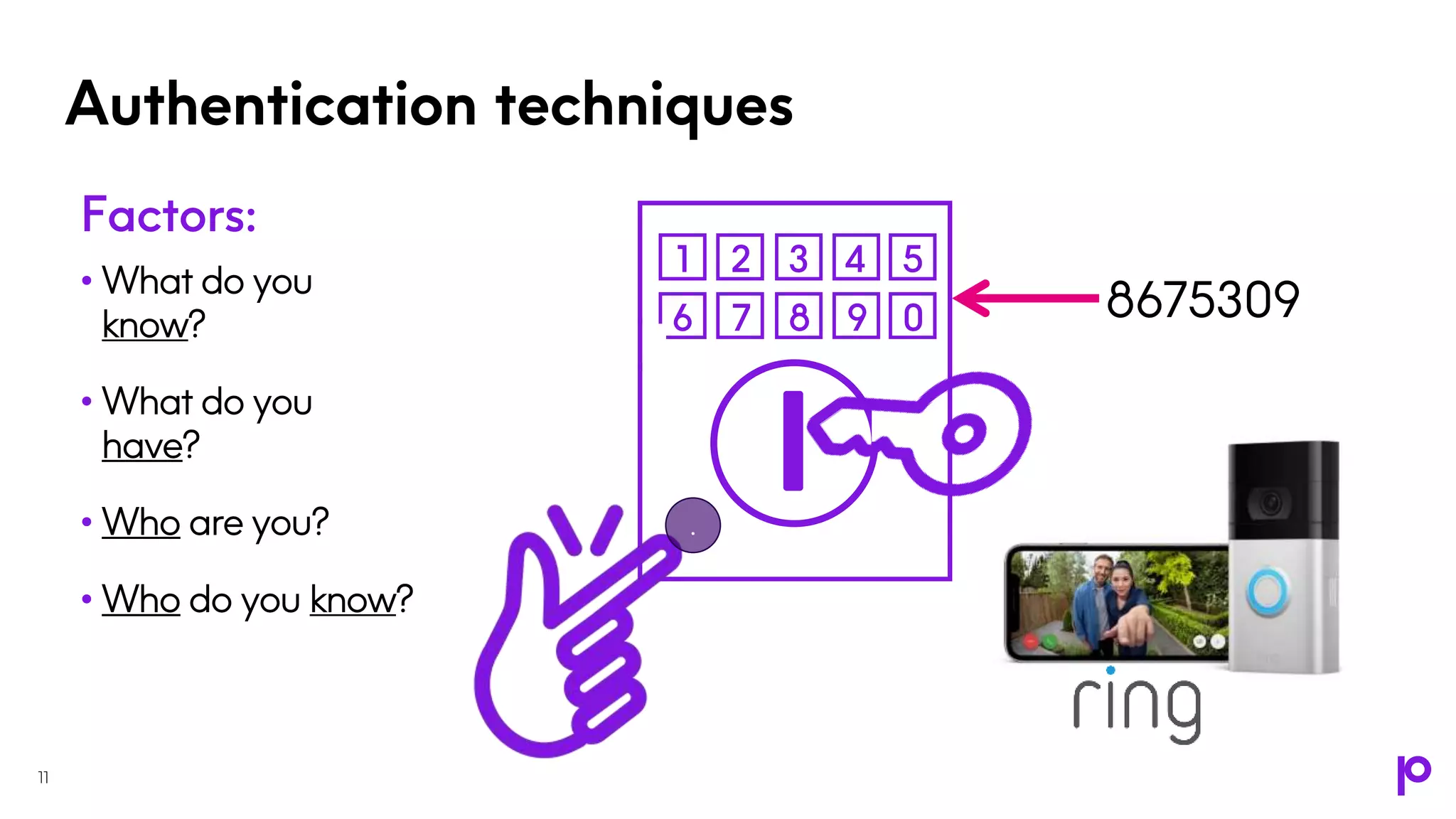
The document outlines an IBM i security strategy that emphasizes securing various assets, actions, and access points using comprehensive security principles and practices. Key topics include authentication, authorization, encryption, tokenization, and the importance of proactive measures like dynamic application security testing and penetration testing. The strategy also discusses the implementation of a multi-layered defense approach to combat increasingly sophisticated security threats and ensure compliance with regulations.