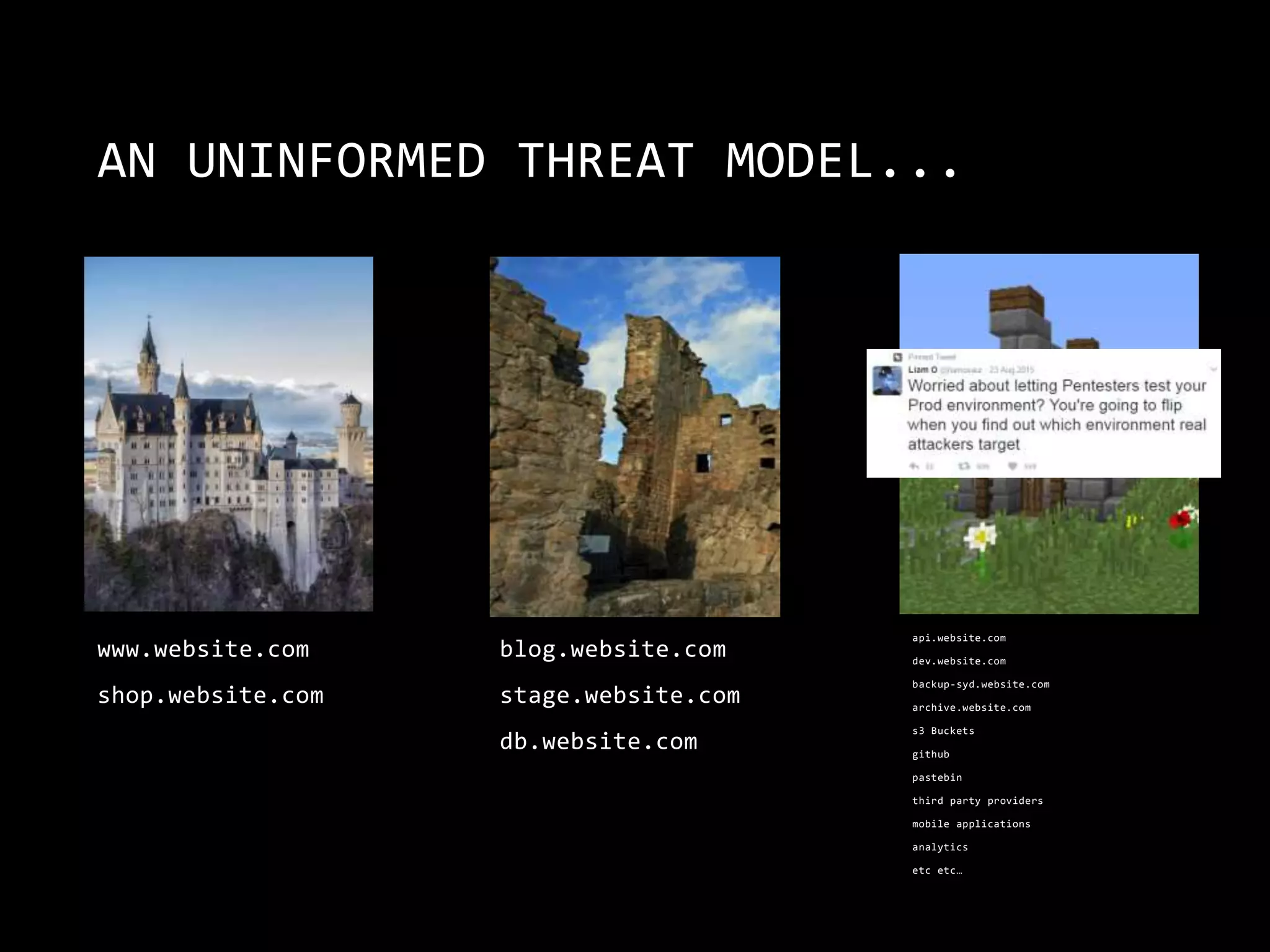
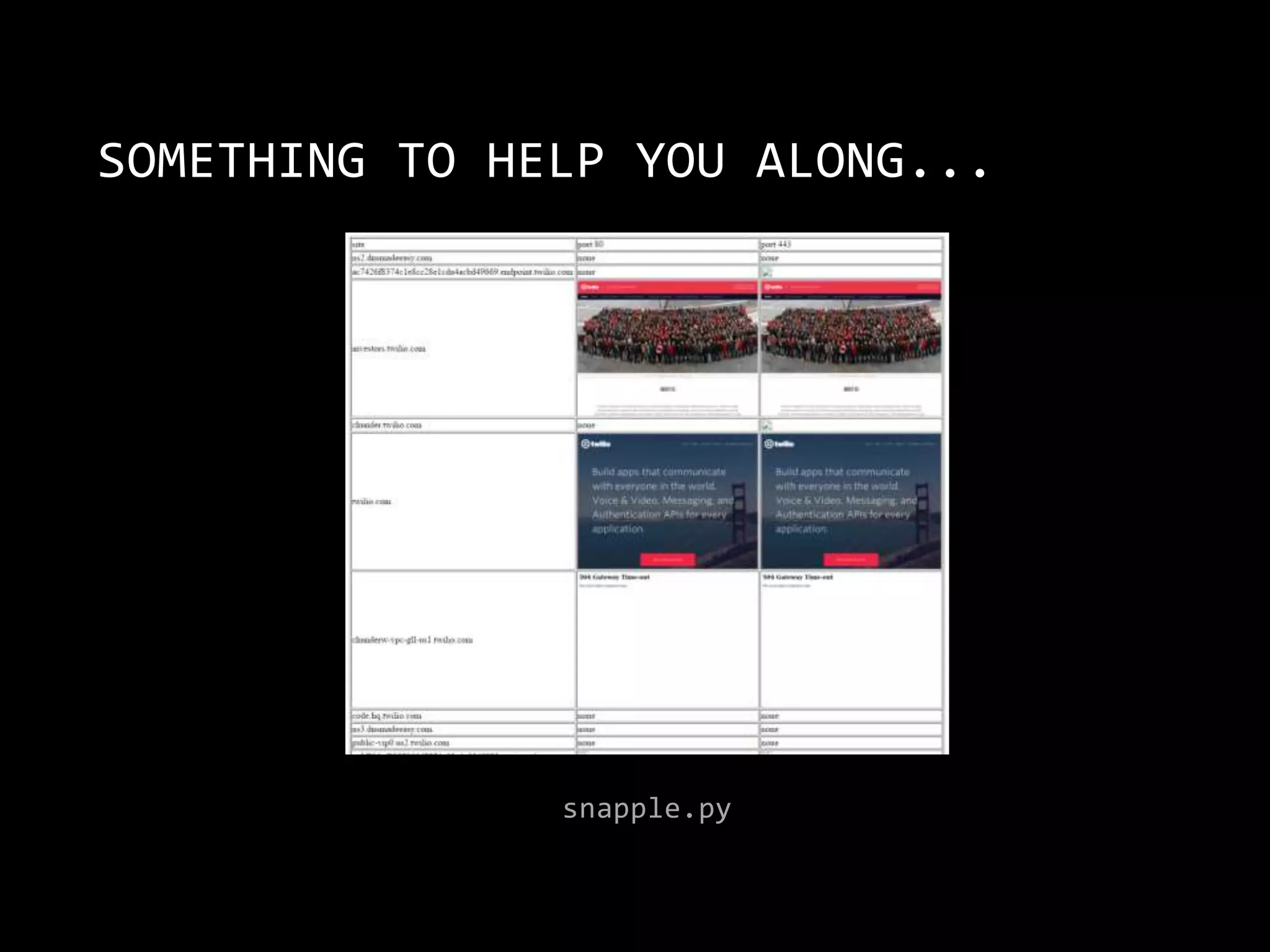
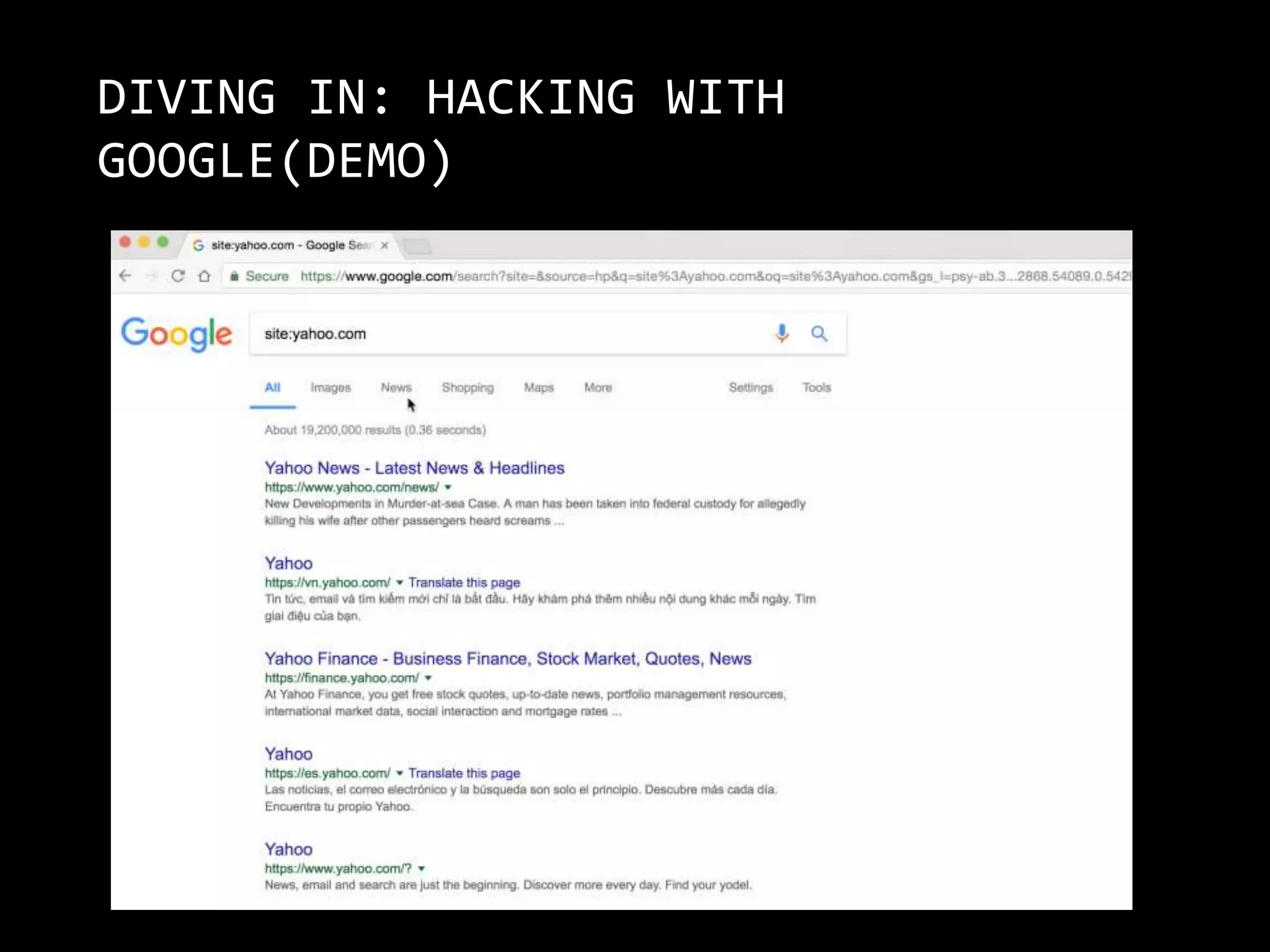
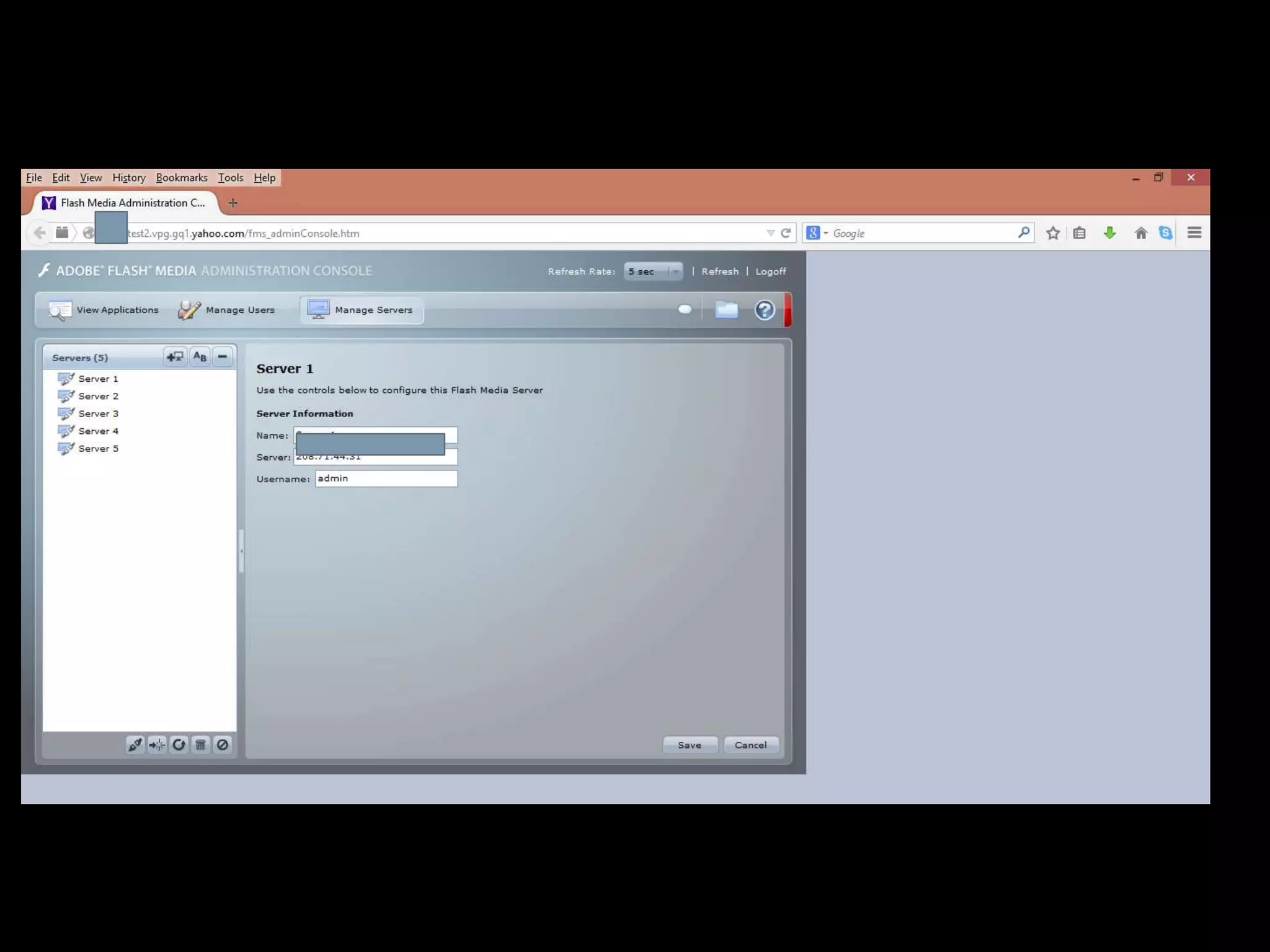
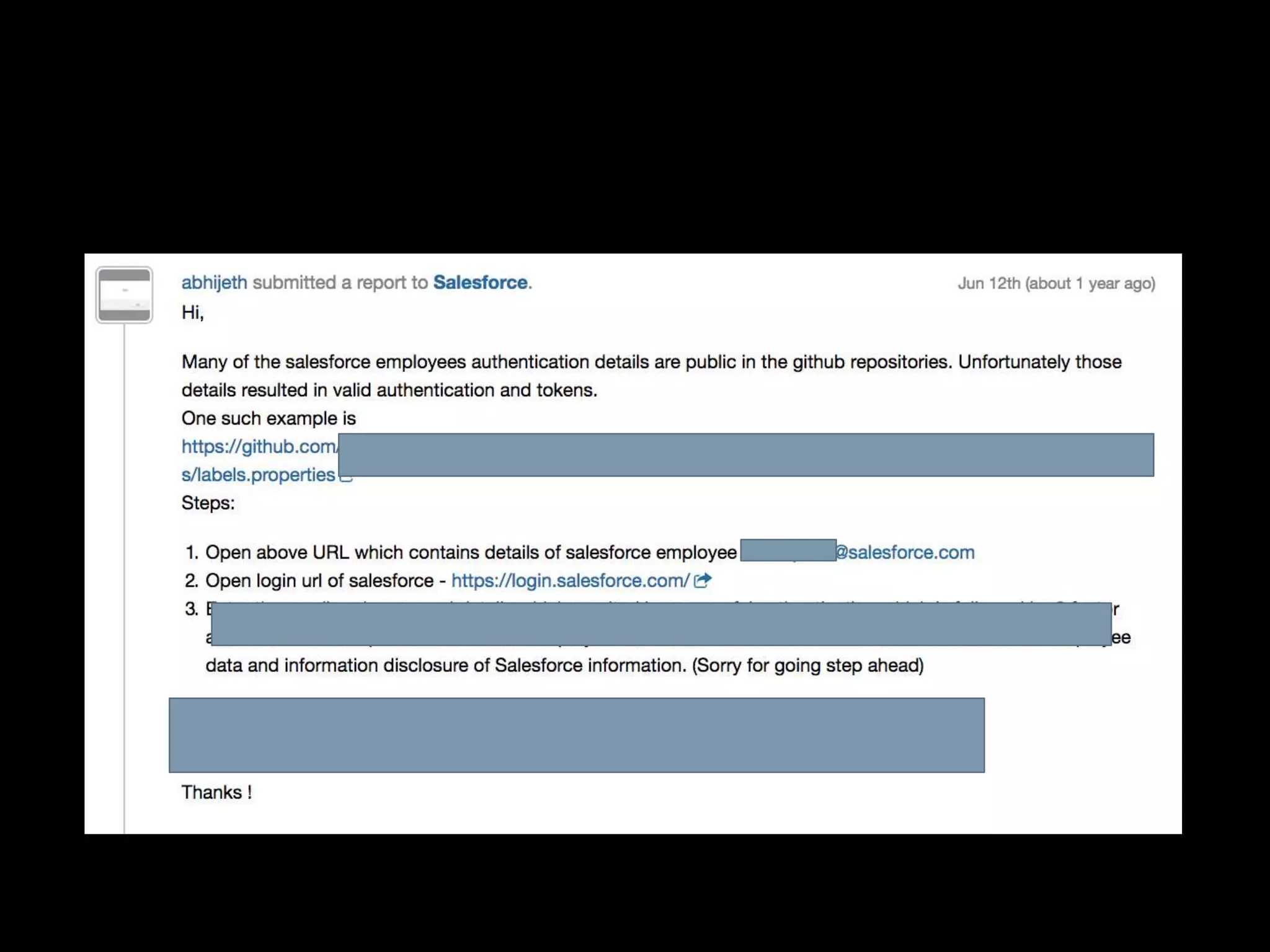
The document is a presentation by Abhijeth Dugginapeddi discussing his experiences with bug bounties and cybersecurity. He shares insights on web security, penetration testing, and tools for discovering vulnerabilities, along with a few personal anecdotes and acknowledgments to fellow researchers. The presentation includes tips on various aspects of hacking and emphasizes the importance of community contributions to cybersecurity.