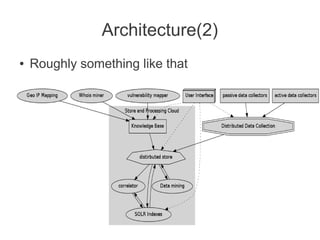
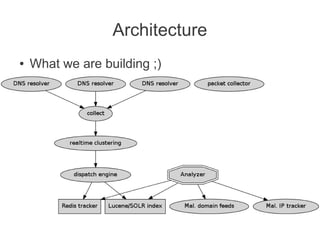
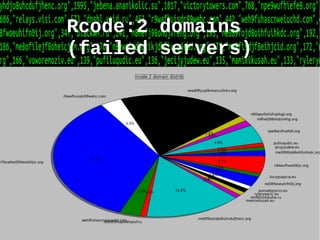
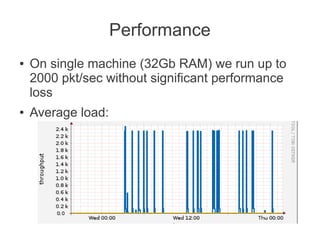
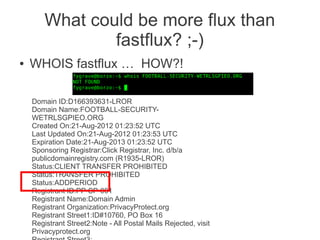
This document discusses detecting malicious network infrastructure through analyzing DNS traffic patterns. Specific techniques discussed include analyzing DNS query patterns for domain generation algorithm (DGA) domains to identify botnets. The document outlines a system built to perform passive DNS analysis to cluster similarly behaving domains and map command and control (C&C) infrastructure through techniques like WHOIS lookups and identifying domains with shared IP addresses or autonomous system numbers. Examples are provided of analyzing DNS query data step-by-step to identify known botnets like Carberp and Palevo. Automated detection and mapping of C&C infrastructure is discussed as well as potential uses of the collected data like generating blacklists or taking over botnets.














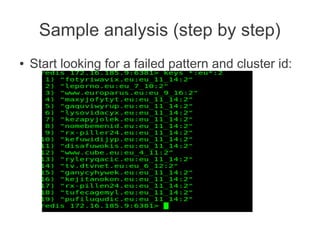
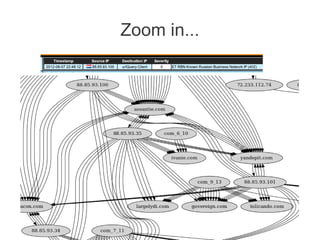
![Sample analysis (two)
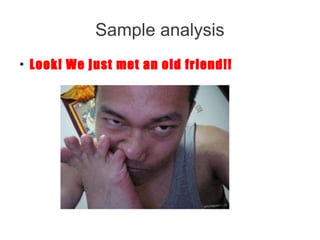
● Get the cluster ID: (eu_11_14)
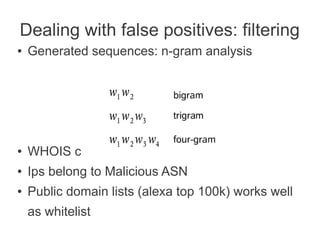
Clustering is based on domain similarity. Currently used characteristics:
- f(zone, pattern (length, depth))
- additional characteristics (building up): natural language domain vs. generated string
(occurrence of two-character sequences - n-grams)
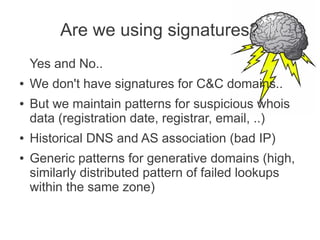
- domain registration parameters (obtained via WHOIS [ problematic! ] )
- cross-reference with existing malicious IP and AS reputation database (incrementally
built by us)](https://image.slidesharecdn.com/hitbkl2012-130220235015-phpapp01/85/Hitbkl-2012-30-320.jpg)
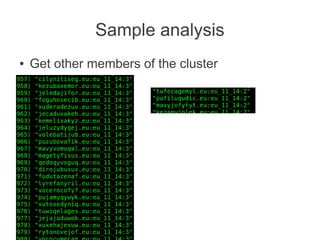
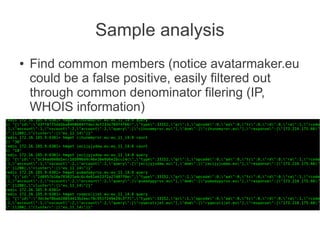
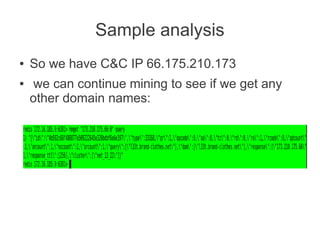





![In short, it is all about quick ways of finding idiots
having no clue of what they are doing with
wordpress, oscommerce, openx, [put yer fave]
And forcing them to update before they get owned
;)
And hmm.. doing it country-wide](https://image.slidesharecdn.com/hitbkl2012-130220235015-phpapp01/85/Hitbkl-2012-46-320.jpg)