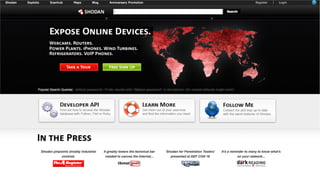
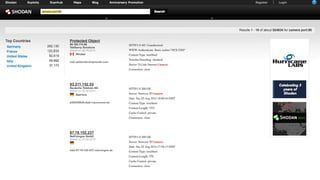
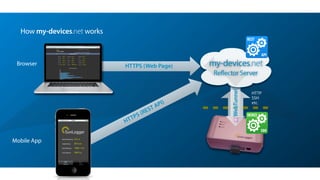
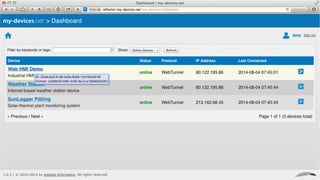
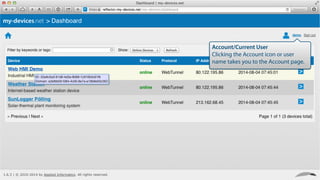
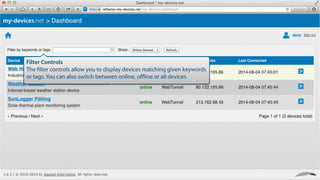
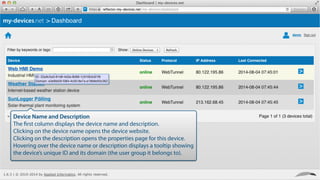
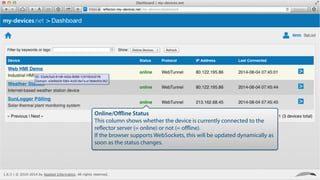
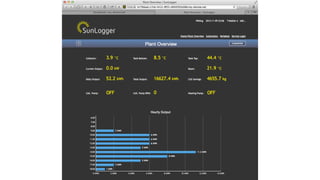
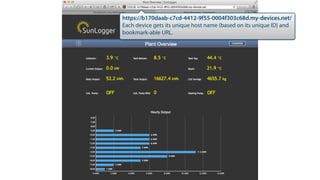
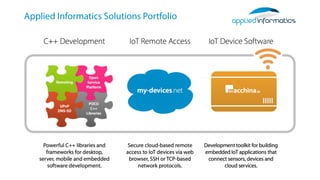
My-devices.net provides secure cloud-enabled remote access to IoT devices via various protocols such as SSH and web browsers. The solution allows users to manage and monitor devices easily without the complexities of traditional methods like VPNs or dynamic DNS, ensuring device security and accessibility. It is suitable for diverse applications including smart metering, industrial equipment maintenance, and remote access for IoT gateways.