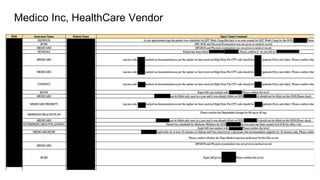
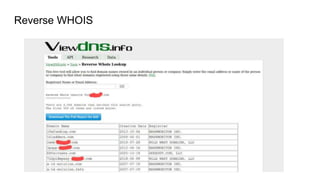
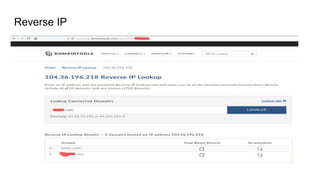
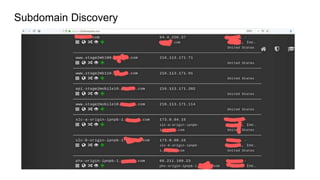
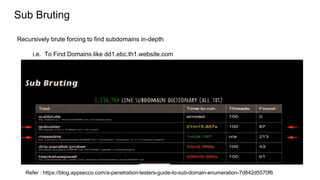
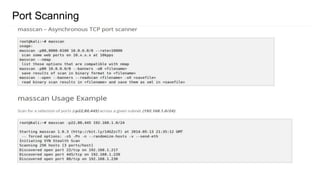
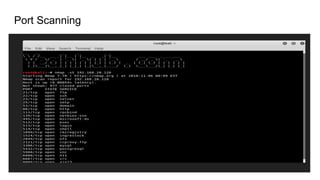
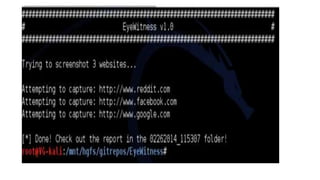
The document outlines various reconnaissance techniques and tools used in penetration testing and bug bounty hunting, such as subdomain discovery, port scanning, and content discovery. It emphasizes the importance of using custom methodologies and includes references to several tools and resources for effective reconnaissance. Key suggestions involve leveraging Google dorking, Wayback Machine, and various brute-forcing tools to uncover hidden information and vulnerabilities.







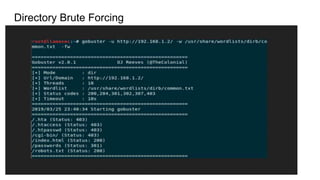
![Tools for Directory Brute Forcing and Content Discovery
Gobuster
BurpSuite Content Discovery
DirBuster - discovering hidden directories
Wfuzz - Discovering hidden files
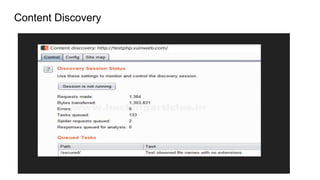
[ NOTE : To do Content Discovery, and brutforcing one requires and good wordlists which is
available in SECLISTS / RAFT / DIGGER WORDLISTS ]](https://image.slidesharecdn.com/recon-191019122510/85/Recon-in-Pentesting-21-320.jpg)





