Recon is an important first step of penetration testing and red teaming to gather publicly available information about a target. The document discusses recon and recon-lit, an updated version of the subdomain discovery tool Sublist3r. It outlines the stages of a recon including setting a target, enumerating subdomains, technologies, directories, endpoints, parameters, and open ports. Tools mentioned for each stage include Recon-lit, Amass, Crt.sh, Dirb, Dirsearch, Linkfinder, Parameth, Nmap, Masscan, and Nikto. The status updates provided an example recon against demo.paypal.com, discovering over 2,300 subdomains and obtaining source code, credentials, and other
![RECON
By
Yash Goti
V1.0 [Basic]
recon is <3](https://image.slidesharecdn.com/recon-200705112652/75/Tool-presentation-Recon-Lit-1-2048.jpg)


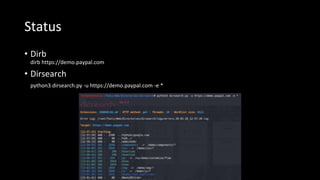
![Stage of recon [Web]
• First set your target
• Enumerate subdomains
• Enumerate Technologies
• Enumerate Directories
• Finding Endpoints
• Finding Hidden Parameters
• Find Open Ports
• Start Testing](https://image.slidesharecdn.com/recon-200705112652/85/Tool-presentation-Recon-Lit-6-320.jpg)
![Status
• We have target [*.paypal.com]](https://image.slidesharecdn.com/recon-200705112652/85/Tool-presentation-Recon-Lit-7-320.jpg)

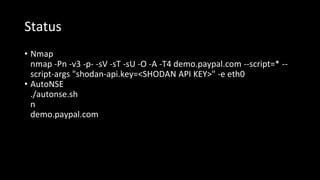
![Status
• Subdomains [from recon-lit] : 2326
python3 reconlit.py -d demo.paypal.com
• Target : demo.paypal.com](https://image.slidesharecdn.com/recon-200705112652/85/Tool-presentation-Recon-Lit-10-320.jpg)