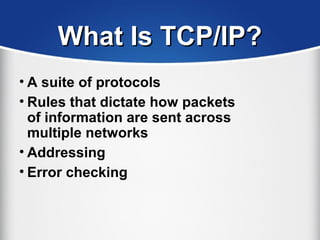
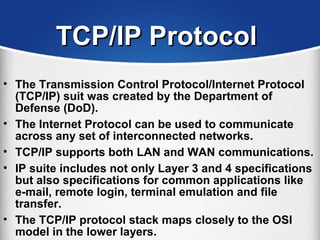
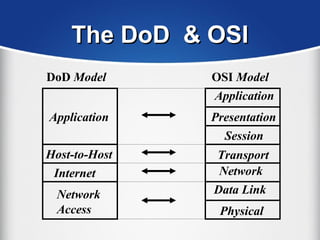
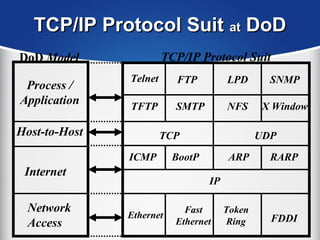
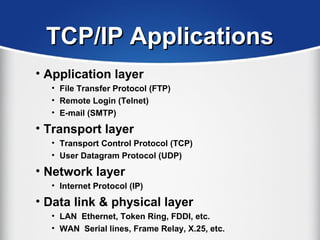
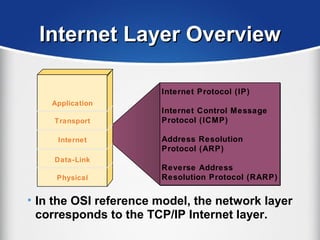
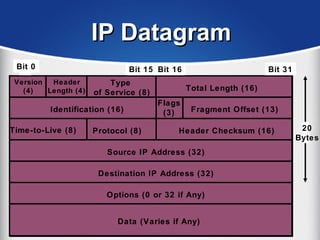
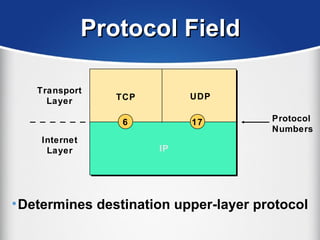
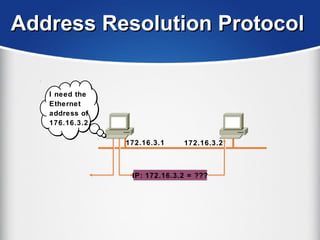
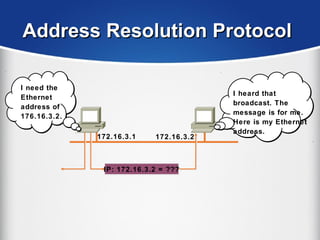
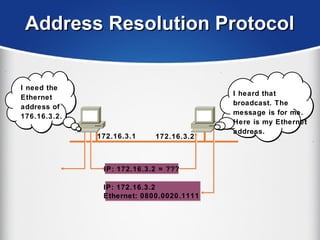
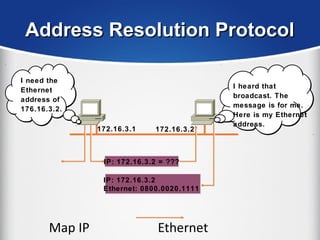
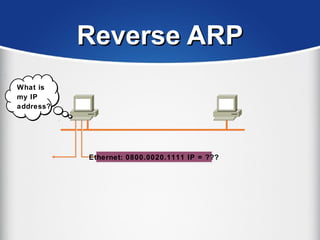
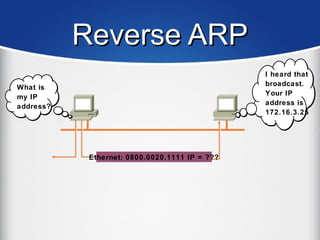
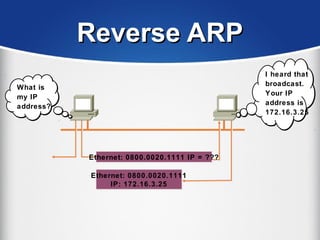
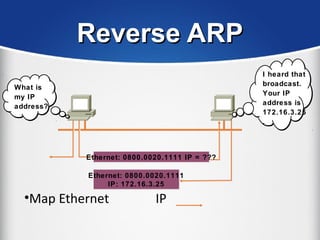
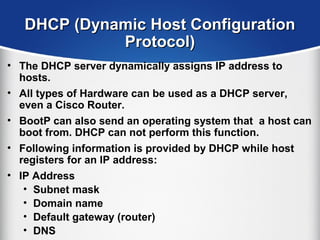
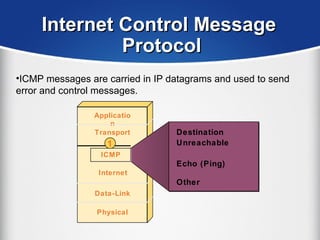
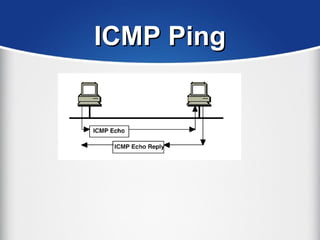
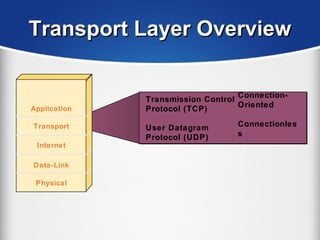
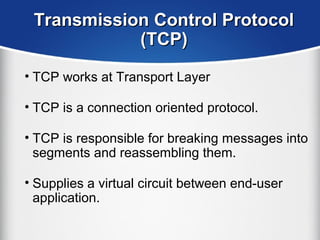
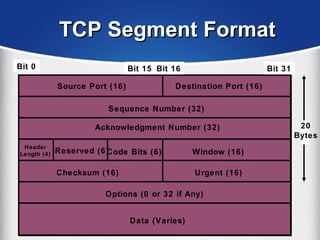
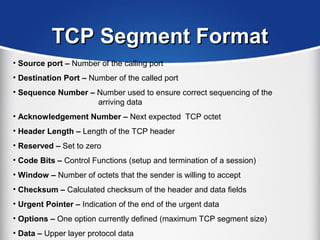
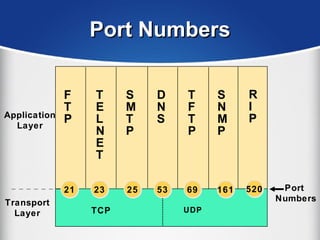
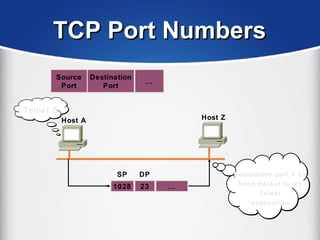
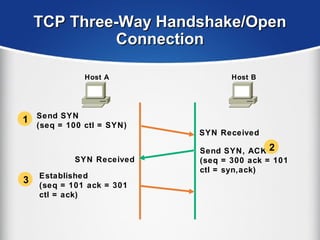
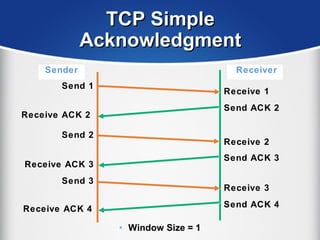
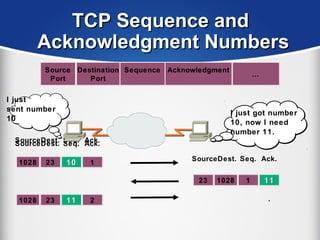
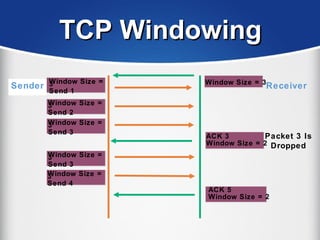
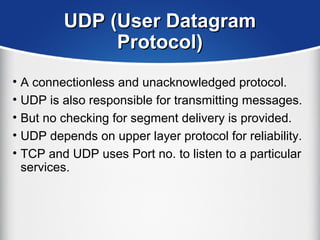
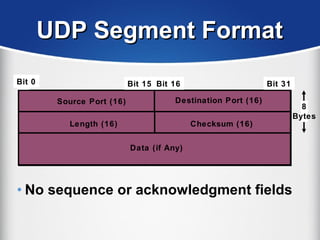
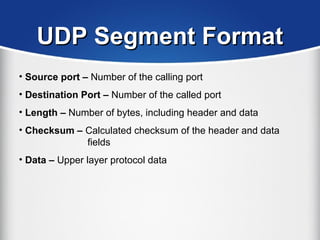
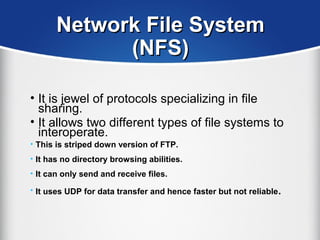
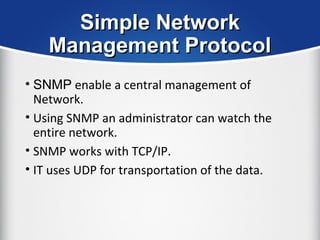
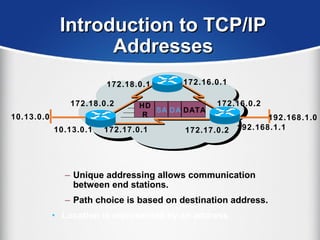
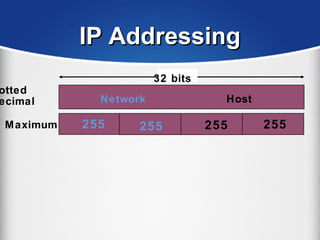
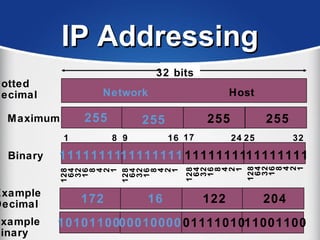
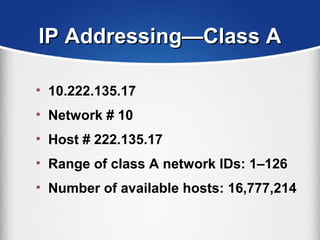
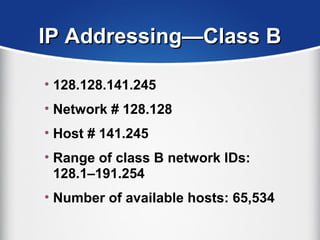
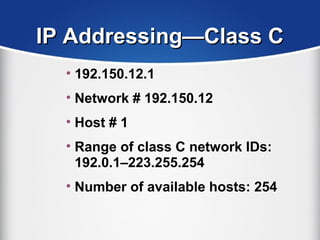
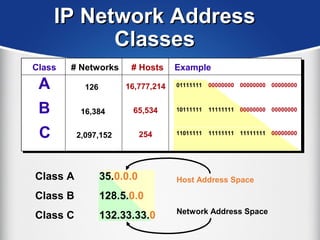
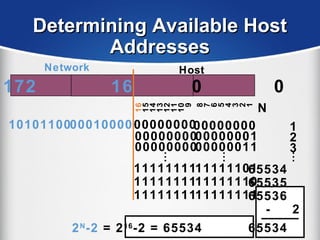
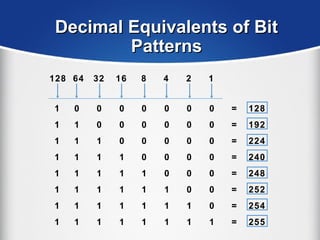
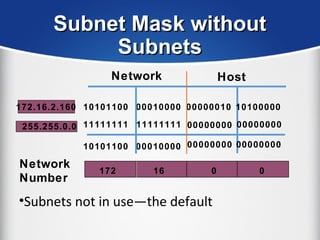
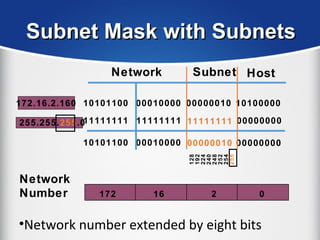
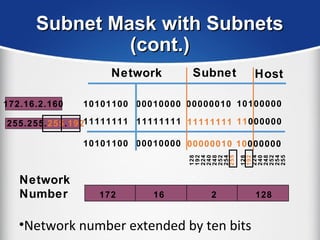
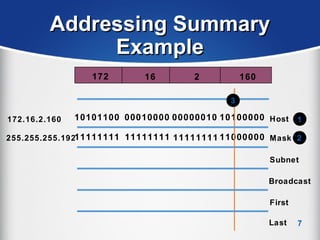
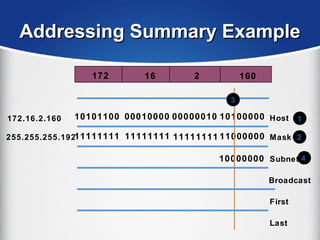
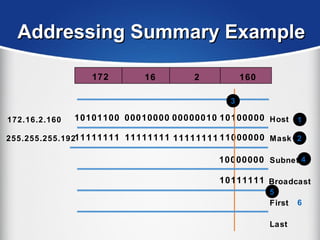
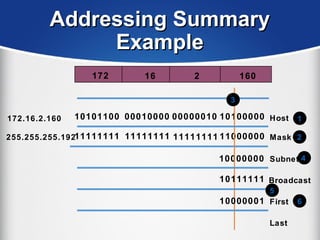
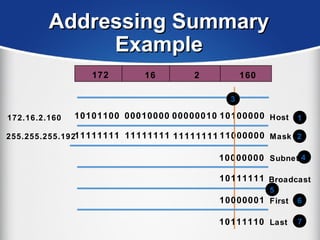
The document provides a comprehensive overview of the TCP/IP protocol suite, detailing its structure, including protocols like TCP, UDP, and IP, as well as their functionalities and the layers they operate within. Key components such as ARP, RARP, DHCP, and several applications like FTP and Telnet are also explained, alongside addressing concepts in IP networking. Additionally, the document covers the significance of IP address classes and management protocols like SNMP and DNS.