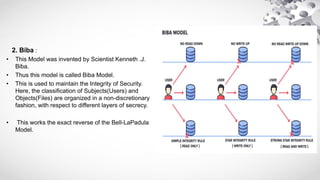
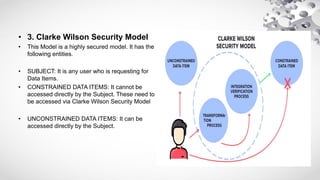
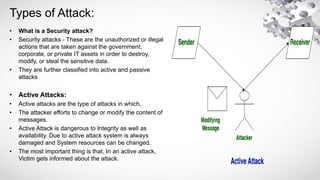
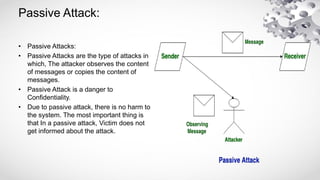
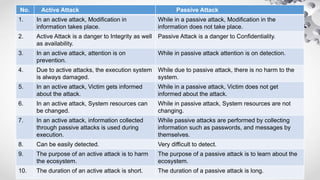
The document provides an extensive overview of information security, emphasizing its purpose of protecting computer assets through principles like confidentiality, integrity, and availability (CIA). It defines threats and vulnerabilities in cybersecurity, describes various security architecture models, and explains types of attacks, including active and passive attacks. Additionally, it discusses malicious codes, their impacts, and the role of intrusion detection systems in monitoring network security.