A More Reilable LAN by MSR Redundant Ring - Redundant Technology 2018
•
0 likes•187 views
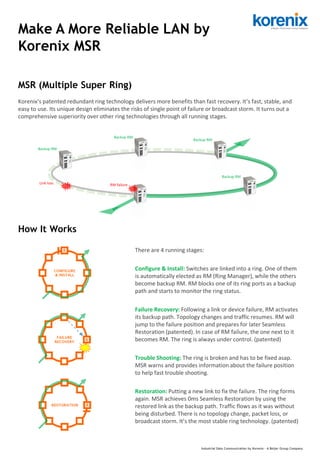
1) MSR (Multiple Super Ring) is Korenix's patented redundant ring technology that makes local area networks (LANs) more reliable. It automatically elects one switch as the Ring Manager (RM) while the others become backup RMs. 2) In the event of a link or device failure, the RM activates its backup path to allow traffic to resume while preparing for seamless restoration. If the RM fails, the next switch becomes the new RM to maintain ring control. 3) MSR provides fast failure recovery within 5ms to minimize packet loss, eliminates single points of failure by having backup RMs, and achieves seamless restoration within 0ms without disrupting traffic flow or causing topology
Report
Share
Report
Share
Download to read offline
Recommended
Principales kpi utilizados para medir una red cellular

Este documento describe los principales KPI (indicadores clave de rendimiento) utilizados para medir una red celular. La accesibilidad es un KPI que indica el porcentaje de éxito que tuvo el usuario al realizar una llamada, variando de 0% a 100%. Un valor de 100% significa que todos los intentos del usuario tuvieron éxito, mientras que un valor mayor al 99% es considerado muy bueno. Valores bajos de accesibilidad, como 60%, son inaceptables y requieren trabajo para mejorar este valor.
AT&T View on LTE to 5G Network Migration 

AT&T proposes a three step approach to evolving 5G architecture from early deployment to more mature phases:
1) Early 5G deployment using Phase 1 Option 3 architecture.
2) Phase 1 evolution to Option 7 architecture while still supporting Option 3, through software upgrades.
3) Phase 2 evolution to Option 2/4 architecture while still supporting Options 3 and 7, with specifications that allow different architectures to coexist.
Inter vlan-routing FundamentoDeRedes

Una VLAN permite crear múltiples subredes lógicas en una red conmutada segmentando los dispositivos según proyectos, funciones o departamentos. Esto proporciona seguridad al aislar el tráfico entre VLANs, reduce costos al no necesitar actualizar la infraestructura física y mejora el rendimiento al dividir los dominios de broadcast.
volte ims network architecture

I have described VoLTE IMS Architecture in simplified way . Are you also finding 3GPP Specs complicated & Complex for VoLTE IMS . It covers Role played by individual Networks Elements as mentioned below :-
# VoLTE SIP Handset : SIP Support , UAC , UAS , User Agent , SIP-UA
# Underlying LTE Network : MME , SGW , PGW , PCRF , HSS , Dedicated Bearer , QCI , Default Bearer
# IMS Core : SIP Servers , P-CSCF , I-CSCF , S-CSCF , TAS , MMTEL , BGw , MRF , ATCF , ATGW , IBCF , MGCF , IM-MGW , TrGW
# Voice Core or PSTN Network for Break-in or Break-out Calls
Gsm Global System For Mobile Comm[1]. Really Nice![Gsm Global System For Mobile Comm[1]. Really Nice](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Gsm Global System For Mobile Comm[1]. Really Nice](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document provides an introduction to cellular technology and the Global System for Mobile Communication (GSM). [1] GSM was established in 1982 to create a common European mobile telephone standard and has become a globally accepted standard. [2] GSM networks use a combination of Time Division Multiple Access (TDMA) and Frequency Division Multiple Access (FDMA) and include mobile stations, base stations, switching centers, databases, and interfaces that allow connection to other networks. [3] GSM supports various services including telephony, data transmission, and messaging and provides features such as security, mobility, and roaming.
AMQP

This document provides an introduction and overview of message queueing and the Advanced Message Queueing Protocol (AMQP). It discusses why messaging is useful, how message queues work, and the main features of message queueing including decoupling applications and asynchronous communication. It then describes AMQP specifically, including why it was developed, how it defines a network protocol and message model, and some key AMQP concepts like exchanges, bindings, queues, and message routing.
Cs fallback feature

This document discusses LTE CS Fallback features which allow LTE networks to reuse CS infrastructure to provide voice and other circuit switched services. CS Fallback enables LTE terminals to redirect to 2G/3G networks when initiating CS services like voice calls. The key aspects covered include the CS Fallback network architecture using the SGs interface, the combined attach procedure used for location updates, advantages/disadvantages of different CS Fallback mechanisms, and signaling flows for CS Fallback and paging.
Transportation Lanes in SAP TM and SAP APO - PDF - V2.0 - Paresh Bhagwatkar 

***Comments Appreciated***
This presentation gives an overview of transportation lanes in SAP TM and SAP TPVS (the functionality is very similar in those products).
It talks about the concept of the transportation lanes, the levels at which data exists, and the granularity of transportation lanes along with guidelines on deciding the granularity.
Also, it goes into different carrier selection strategies and how priority and cost interact.
This presentation does not go into the priorities for broadcast tendering (which is functionality in SAP TM 8.0 and onwards). That will come in update version 3.0.
Recommended
Principales kpi utilizados para medir una red cellular

Este documento describe los principales KPI (indicadores clave de rendimiento) utilizados para medir una red celular. La accesibilidad es un KPI que indica el porcentaje de éxito que tuvo el usuario al realizar una llamada, variando de 0% a 100%. Un valor de 100% significa que todos los intentos del usuario tuvieron éxito, mientras que un valor mayor al 99% es considerado muy bueno. Valores bajos de accesibilidad, como 60%, son inaceptables y requieren trabajo para mejorar este valor.
AT&T View on LTE to 5G Network Migration 

AT&T proposes a three step approach to evolving 5G architecture from early deployment to more mature phases:
1) Early 5G deployment using Phase 1 Option 3 architecture.
2) Phase 1 evolution to Option 7 architecture while still supporting Option 3, through software upgrades.
3) Phase 2 evolution to Option 2/4 architecture while still supporting Options 3 and 7, with specifications that allow different architectures to coexist.
Inter vlan-routing FundamentoDeRedes

Una VLAN permite crear múltiples subredes lógicas en una red conmutada segmentando los dispositivos según proyectos, funciones o departamentos. Esto proporciona seguridad al aislar el tráfico entre VLANs, reduce costos al no necesitar actualizar la infraestructura física y mejora el rendimiento al dividir los dominios de broadcast.
volte ims network architecture

I have described VoLTE IMS Architecture in simplified way . Are you also finding 3GPP Specs complicated & Complex for VoLTE IMS . It covers Role played by individual Networks Elements as mentioned below :-
# VoLTE SIP Handset : SIP Support , UAC , UAS , User Agent , SIP-UA
# Underlying LTE Network : MME , SGW , PGW , PCRF , HSS , Dedicated Bearer , QCI , Default Bearer
# IMS Core : SIP Servers , P-CSCF , I-CSCF , S-CSCF , TAS , MMTEL , BGw , MRF , ATCF , ATGW , IBCF , MGCF , IM-MGW , TrGW
# Voice Core or PSTN Network for Break-in or Break-out Calls
Gsm Global System For Mobile Comm[1]. Really Nice![Gsm Global System For Mobile Comm[1]. Really Nice](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Gsm Global System For Mobile Comm[1]. Really Nice](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The document provides an introduction to cellular technology and the Global System for Mobile Communication (GSM). [1] GSM was established in 1982 to create a common European mobile telephone standard and has become a globally accepted standard. [2] GSM networks use a combination of Time Division Multiple Access (TDMA) and Frequency Division Multiple Access (FDMA) and include mobile stations, base stations, switching centers, databases, and interfaces that allow connection to other networks. [3] GSM supports various services including telephony, data transmission, and messaging and provides features such as security, mobility, and roaming.
AMQP

This document provides an introduction and overview of message queueing and the Advanced Message Queueing Protocol (AMQP). It discusses why messaging is useful, how message queues work, and the main features of message queueing including decoupling applications and asynchronous communication. It then describes AMQP specifically, including why it was developed, how it defines a network protocol and message model, and some key AMQP concepts like exchanges, bindings, queues, and message routing.
Cs fallback feature

This document discusses LTE CS Fallback features which allow LTE networks to reuse CS infrastructure to provide voice and other circuit switched services. CS Fallback enables LTE terminals to redirect to 2G/3G networks when initiating CS services like voice calls. The key aspects covered include the CS Fallback network architecture using the SGs interface, the combined attach procedure used for location updates, advantages/disadvantages of different CS Fallback mechanisms, and signaling flows for CS Fallback and paging.
Transportation Lanes in SAP TM and SAP APO - PDF - V2.0 - Paresh Bhagwatkar 

***Comments Appreciated***
This presentation gives an overview of transportation lanes in SAP TM and SAP TPVS (the functionality is very similar in those products).
It talks about the concept of the transportation lanes, the levels at which data exists, and the granularity of transportation lanes along with guidelines on deciding the granularity.
Also, it goes into different carrier selection strategies and how priority and cost interact.
This presentation does not go into the priorities for broadcast tendering (which is functionality in SAP TM 8.0 and onwards). That will come in update version 3.0.
Ensuring Network Reliabilty And Quality For IP Surveillance 2012

Korenix patented MSR redundancy technology provides more reliable network redundancy for IP surveillance systems compared to other protocols like RSTP. MSR guarantees failure recovery within 5ms, has no packet loss or topology changes during restoration, and can scale to support 250 switches in a single ring. It ensures the highest quality and most reliable video transmission for IP surveillance networks.
What is LoRaNET?

LoRaNET protocol is a LoRa networking protocol, there are various LoRa protocols on the market now, LoRaWAN, CLAA, LinkWAN all have their own advantages. For LoRa applications, stability and reliability is the key, and this article will take you through the LoRaNET protocol in detail.
What is the LoRaNET?
LoRaNET is a LoRa networking protocol that supports secondary development, LoRaNet SDK uses an AMetal software platform, it provides some basic components, which provides a good abstraction of most on-chip hardware resources, when using peripherals, you only need to simply configure, call API, no need to pay attention to the underlying hardware operation.
alm.pdf

The document describes an ALM fiber monitoring solution that provides:
- Real-time fiber monitoring to detect failures within seconds and reduce repair times
- Non-intrusive monitoring that is compatible with any data protocol or transmission system
- Insight into fiber infrastructure quality to immediately address abnormalities or security issues
alm.pdf

The document describes an ALM fiber monitoring solution that provides:
- Real-time fiber monitoring to detect failures within seconds and reduce repair times
- Non-intrusive monitoring that is compatible with any data protocol or transmission system
- Insight into fiber infrastructure quality to immediately address abnormalities or security issues
Broadcast Storm - The Root Causes And The Solutions - Whitepaper 2012

This whitepaper discusses broadcast storms in industrial Ethernet networks that use redundant ring topologies. It reveals that broadcast storms occur due to loops in the network topology that are created during events like link restoration or network restarts. This overwhelms the network with broadcast traffic. The whitepaper then presents Korenix's comprehensive solution to prevent broadcast storms which includes technologies that prevent loops from forming, ensure resilience during ring manager failures, and provide protection beyond individual rings.
Maipu 3 g access solution for enterprises

This document discusses Maipu's 3G access solution for enterprises. It outlines the network requirements of various industries including financial services, police, transportation, power, and retailers. It then describes how Maipu's 3G solution provides flexibility, reliability, security, and easy management through features like dual 3G modules, external antennas, SMS management, remote management, and locating/tracking via an E3G management platform. The document also introduces Maipu's MP1800 router series which supports various interfaces and modules. It concludes with an overview of Maipu's customer base utilizing their 3G and E3G solutions across China.
PLNOG 13: Marek Janik: Rings in Ethernet Networks

Marek Janik – TBD
Topic of Presentation: Rings in Ethernet Networks
Language: Polish
Abstract: TBD
ADVA Advanced Link Monitor (ALM)

This document describes an in-service fiber monitoring solution called the ALM that provides real-time fiber integrity monitoring to enable fast failure detection and repair. The ALM solution streamlines fiber network operations by providing non-intrusive, passive demarcation monitoring without additional equipment or power requirements. It integrates with network management systems to help localize fiber issues and ensure higher service availability.
8 wcdma rf optimization&case study-60

This document discusses WCDMA RF optimization processes, policies, and case studies. It describes the three steps of the WCDMA RF optimization process: single station check, base station group optimization, and whole network optimization. It then discusses common RF problems, analysis, and optimization policies for issues like call drops, discontinuity, and access failures. Finally, it presents five case studies of WCDMA network optimization including issues like handover problems, coverage gaps, high site interference, and neighbor cell list configuration errors.
High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure

High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure
LICENSE-FREE, CERTIFIED AROUND THE WORLD
The Trimble TMR1 Enclosed IP67 is a dual ISM band (865-870 and 902-928 MHz) networked transceiver supporting license-free wireless communications around the world. With available throughput up 2.6Mbps, the TMR1 allows you to seamlessly integrate both serial and Ethernet traffic as well as having the throughput available for video. Range as high as 70 miles has been demonstrated in low noise environments. The TMR1 rugged IP67 housing high performance and versatility make it ideal for oil/gas, water and electric utilities, environmental monitoring and agricultural applications.
ADAPTIVE SPEED/MODULATION TECHNOLOGY
The Trimble TMR1 supports both point-to-point and point-to-multipoint network topologies. With most networked radios operating in point-to-multipoint mode, the speed of the access point radio is restricted to the speed and modulation of the weakest link.
DUAL DATA PORTS FOR BOTH SERIAL AND IP COMMUNICATION
The Trimble TMR1 is equipped with two data connectors: one for serial/power and one for Ethernet. This allows you to attach sensors to the TMR1 in the field and to communicate with any TMR1 via Ethernet cables, a LAN/WAN or the Internet. All links can be protected by AES 128- and 256-bit data encryption and VLAN segregation, so only you are allowed to communicate with your network.
RUGGED, WATERPROOF, MADE FOR THE REAL WORLD
The Trimble TMR1 is built to survive in real-world industrial applications, from mines and
construction sites to warehouses and oil rigs. The rugged aluminum housing and connectors are certified to withstand submersion in 1 meter of water and are chemically treated to withstand corrosion.
08. DRIVE TEST Analysis

This document provides information about MobileComm Technologies' drive test process for UMTS networks. It includes documentation on tools used for tuning and optimization, parameters measured, call flows, key performance indicators, examples of coverage and interference issues identified, and tips for network tuning. The document contains 47 slides covering topics like coverage verification using P-CPICH measurements, identifying interference and overshooting issues, analyzing call drops, tuning for voice and data calls, and comparing mechanical vs electrical antenna tilts.
2G Network Optimization

The document discusses optimization of 2G networks. It describes the objectives, flow, and key performance indicators of 2G network optimization. Common problems addressed through optimization include coverage issues, interference, congestion, handover failures, and call drops. Solutions involve adjusting network parameters, antenna configuration, power levels, frequency plans, and adding new sites or equipment as needed. The goal is to ensure quality of service and meet customer demand on the network.
LE-240XTCS LE-280XTS - Ethernet module for the LET-36 chassis

The document describes Ethernet security modules that provide eavesdropping protection and intrusion control features. The modules have 24 10BASE-T ports and can operate in standard or standalone mode. They employ security features like eavesdropping protection to prevent sniffing of network traffic and intrusion control to monitor unauthorized access. The modules can be managed through SNMP-compliant applications.
PROJECT 2016-2017

The document discusses the implementation and maintenance of a BSS (Base Station Subsystem) system for GSM, CDMA, and 3G networks. It provides information on Tata Docomo as a telecom service provider in India and the products and services it offers. The objective of the project is to implement BSS sites and maintain them using a Network Management Center and Operation and Maintenance Center. It then covers basic BSS concepts, the concept of maintenance, a process flow diagram for project rollout, an example of link budget calculations, common maintenance issues and how to address them, limitations, findings, and recommendations.
High Speed Long Range SCADA Radio Modem TMR1 - OEM

LICENSE-FREE, CERTIFIED AROUND THE WORLD
The Trimble TMR1 Board Level is a dual ISM band (865-870 and 902-928 MHz) networked
transceiver supporting license-free wireless communications around the world. With
available throughput up 2.6Mbps, the TMR1 allows you to seamlessly integrate both serial
and Ethernet traffic as well as having the throughput available for video. Range as high
as 70 miles has been demonstrated in low noise environments. The TMR1 Board Level’s
high performance and versatility make it ideal for oil/gas, water and electric utilities,
environmental monitoring and agricultural applications.
ADAPTIVE SPEED/MODULATION TECHNOLOGY
The Trimble TMR1 supports both point-to-point and point-to-multipoint network
topologies. With most networked radios operating in point-to-multipoint mode,
the speed of the access point radio is restricted to the speed and modulation of
the weakest link.
DUAL DATA PORTS FOR BOTH SERIAL AND IP COMMUNICATION
The Trimble TMR1 Board Level is equipped with two RJ45 connectors: one for serial and
one for Ethernet. This allows you to attach sensors to the TMR1 Board Level in the field
and to communicate with any TMR1 Board Level via Ethernet cables, a LAN/WAN or the
Internet. All links can be protected by AES 128- and 256-bit data encryption and VLAN
segregation, so only you can communicate with your network.
Outstanding In Redundancy And Security - Korenix Ethernet Switches Brochure ...

The document discusses Korenix managed Ethernet switches for industrial applications. It provides specifications for various switch models, including the number and type of ports, supported network redundancy and security features, management capabilities, environmental tolerances, and contact information. The switches provide multiple redundancy technologies to minimize downtime, including ring redundancy with 5ms failure recovery and seamless restoration. They also offer security features like VLAN protection, private VLANs, port security, and various access control lists.
MSIP report

LM Ericsson is a leading telecommunications equipment manufacturer, providing mobile systems solutions and end-to-end network solutions to operators. The author completed an internship at Ericsson where they learned about technical and corporate skills while helping to upgrade the software on 2000 network nodes in Bangladesh. They gained experience in fields maintenance and saw first-hand how Ericsson maintains high quality networks for its customers.
III_UNIT.pptx

This document summarizes key concepts about the data link layer. It discusses the services provided to the network layer including unacknowledged connectionless service, acknowledged connectionless service, and acknowledged connection-oriented service. It describes framing, including frame structure with header, payload, and trailer. Error control using Automatic Repeat Request and flow control are explained. Stop-and-wait and sliding window protocols are given as examples of error control and flow control mechanisms.
III_UNIT.pptx

This document summarizes key concepts about the data link layer. It discusses the services provided to the network layer including unacknowledged connectionless service, acknowledged connectionless service, and acknowledged connection-oriented service. It describes framing, including frame structure with header, payload, and trailer. Error control using Automatic Repeat Request and flow control are explained. Frame types can be fixed-sized or variable-sized, using techniques like length field or end delimiter. The advantages of framing are also provided.
6500-M User Manual

1. The document provides instructions for setting up a Mako network appliance. It describes connecting the appliance to an Ethernet switch, internet connection via DSL or cable, and installing firmware.
2. Setting up a cellular connection requires inserting a SIM card into the appliance and configuring the connection settings through the Central Management System interface.
3. Troubleshooting guidance is provided for checking firmware installation status and testing internet connections. The Makoscope diagnostic tool accessible through the CMS can also check connection status.
Make The Impossible Possible - Industrial PoE Brochure 2014

This document provides specifications for the JetCon 1702 PoE switch, including:
- It has two RJ-45 ports that provide data and PoE power using either Alternative A or B wiring.
- It supports both IEEE 802.3af and 802.3at PoE standards, providing up to 15W or 30W of power per port respectively.
- Additional features include overcurrent, overvoltage, and overtemperature protection for the PoE ports.
Transformation From Today To Tomorrow - Market and Product Strategy 2018

This document outlines a strategy for transforming industrial communication networks from today to the future. It analyzes current solutions and identifies trends impacting networks, including cloud connectivity, network security, and cloud networking. The transformation roadmap involves three phases over the next 5 years: 1) focusing on cloud/security, 2) convergence and scalability, and 3) network virtualization and agility. The goal is for networks to become more flexible, modular, and integrated through both physical and virtual components using technologies like TSN, 5G, wireless, and NFV.
More Related Content
Similar to A More Reilable LAN by MSR Redundant Ring - Redundant Technology 2018
Ensuring Network Reliabilty And Quality For IP Surveillance 2012

Korenix patented MSR redundancy technology provides more reliable network redundancy for IP surveillance systems compared to other protocols like RSTP. MSR guarantees failure recovery within 5ms, has no packet loss or topology changes during restoration, and can scale to support 250 switches in a single ring. It ensures the highest quality and most reliable video transmission for IP surveillance networks.
What is LoRaNET?

LoRaNET protocol is a LoRa networking protocol, there are various LoRa protocols on the market now, LoRaWAN, CLAA, LinkWAN all have their own advantages. For LoRa applications, stability and reliability is the key, and this article will take you through the LoRaNET protocol in detail.
What is the LoRaNET?
LoRaNET is a LoRa networking protocol that supports secondary development, LoRaNet SDK uses an AMetal software platform, it provides some basic components, which provides a good abstraction of most on-chip hardware resources, when using peripherals, you only need to simply configure, call API, no need to pay attention to the underlying hardware operation.
alm.pdf

The document describes an ALM fiber monitoring solution that provides:
- Real-time fiber monitoring to detect failures within seconds and reduce repair times
- Non-intrusive monitoring that is compatible with any data protocol or transmission system
- Insight into fiber infrastructure quality to immediately address abnormalities or security issues
alm.pdf

The document describes an ALM fiber monitoring solution that provides:
- Real-time fiber monitoring to detect failures within seconds and reduce repair times
- Non-intrusive monitoring that is compatible with any data protocol or transmission system
- Insight into fiber infrastructure quality to immediately address abnormalities or security issues
Broadcast Storm - The Root Causes And The Solutions - Whitepaper 2012

This whitepaper discusses broadcast storms in industrial Ethernet networks that use redundant ring topologies. It reveals that broadcast storms occur due to loops in the network topology that are created during events like link restoration or network restarts. This overwhelms the network with broadcast traffic. The whitepaper then presents Korenix's comprehensive solution to prevent broadcast storms which includes technologies that prevent loops from forming, ensure resilience during ring manager failures, and provide protection beyond individual rings.
Maipu 3 g access solution for enterprises

This document discusses Maipu's 3G access solution for enterprises. It outlines the network requirements of various industries including financial services, police, transportation, power, and retailers. It then describes how Maipu's 3G solution provides flexibility, reliability, security, and easy management through features like dual 3G modules, external antennas, SMS management, remote management, and locating/tracking via an E3G management platform. The document also introduces Maipu's MP1800 router series which supports various interfaces and modules. It concludes with an overview of Maipu's customer base utilizing their 3G and E3G solutions across China.
PLNOG 13: Marek Janik: Rings in Ethernet Networks

Marek Janik – TBD
Topic of Presentation: Rings in Ethernet Networks
Language: Polish
Abstract: TBD
ADVA Advanced Link Monitor (ALM)

This document describes an in-service fiber monitoring solution called the ALM that provides real-time fiber integrity monitoring to enable fast failure detection and repair. The ALM solution streamlines fiber network operations by providing non-intrusive, passive demarcation monitoring without additional equipment or power requirements. It integrates with network management systems to help localize fiber issues and ensure higher service availability.
8 wcdma rf optimization&case study-60

This document discusses WCDMA RF optimization processes, policies, and case studies. It describes the three steps of the WCDMA RF optimization process: single station check, base station group optimization, and whole network optimization. It then discusses common RF problems, analysis, and optimization policies for issues like call drops, discontinuity, and access failures. Finally, it presents five case studies of WCDMA network optimization including issues like handover problems, coverage gaps, high site interference, and neighbor cell list configuration errors.
High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure

High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure
LICENSE-FREE, CERTIFIED AROUND THE WORLD
The Trimble TMR1 Enclosed IP67 is a dual ISM band (865-870 and 902-928 MHz) networked transceiver supporting license-free wireless communications around the world. With available throughput up 2.6Mbps, the TMR1 allows you to seamlessly integrate both serial and Ethernet traffic as well as having the throughput available for video. Range as high as 70 miles has been demonstrated in low noise environments. The TMR1 rugged IP67 housing high performance and versatility make it ideal for oil/gas, water and electric utilities, environmental monitoring and agricultural applications.
ADAPTIVE SPEED/MODULATION TECHNOLOGY
The Trimble TMR1 supports both point-to-point and point-to-multipoint network topologies. With most networked radios operating in point-to-multipoint mode, the speed of the access point radio is restricted to the speed and modulation of the weakest link.
DUAL DATA PORTS FOR BOTH SERIAL AND IP COMMUNICATION
The Trimble TMR1 is equipped with two data connectors: one for serial/power and one for Ethernet. This allows you to attach sensors to the TMR1 in the field and to communicate with any TMR1 via Ethernet cables, a LAN/WAN or the Internet. All links can be protected by AES 128- and 256-bit data encryption and VLAN segregation, so only you are allowed to communicate with your network.
RUGGED, WATERPROOF, MADE FOR THE REAL WORLD
The Trimble TMR1 is built to survive in real-world industrial applications, from mines and
construction sites to warehouses and oil rigs. The rugged aluminum housing and connectors are certified to withstand submersion in 1 meter of water and are chemically treated to withstand corrosion.
08. DRIVE TEST Analysis

This document provides information about MobileComm Technologies' drive test process for UMTS networks. It includes documentation on tools used for tuning and optimization, parameters measured, call flows, key performance indicators, examples of coverage and interference issues identified, and tips for network tuning. The document contains 47 slides covering topics like coverage verification using P-CPICH measurements, identifying interference and overshooting issues, analyzing call drops, tuning for voice and data calls, and comparing mechanical vs electrical antenna tilts.
2G Network Optimization

The document discusses optimization of 2G networks. It describes the objectives, flow, and key performance indicators of 2G network optimization. Common problems addressed through optimization include coverage issues, interference, congestion, handover failures, and call drops. Solutions involve adjusting network parameters, antenna configuration, power levels, frequency plans, and adding new sites or equipment as needed. The goal is to ensure quality of service and meet customer demand on the network.
LE-240XTCS LE-280XTS - Ethernet module for the LET-36 chassis

The document describes Ethernet security modules that provide eavesdropping protection and intrusion control features. The modules have 24 10BASE-T ports and can operate in standard or standalone mode. They employ security features like eavesdropping protection to prevent sniffing of network traffic and intrusion control to monitor unauthorized access. The modules can be managed through SNMP-compliant applications.
PROJECT 2016-2017

The document discusses the implementation and maintenance of a BSS (Base Station Subsystem) system for GSM, CDMA, and 3G networks. It provides information on Tata Docomo as a telecom service provider in India and the products and services it offers. The objective of the project is to implement BSS sites and maintain them using a Network Management Center and Operation and Maintenance Center. It then covers basic BSS concepts, the concept of maintenance, a process flow diagram for project rollout, an example of link budget calculations, common maintenance issues and how to address them, limitations, findings, and recommendations.
High Speed Long Range SCADA Radio Modem TMR1 - OEM

LICENSE-FREE, CERTIFIED AROUND THE WORLD
The Trimble TMR1 Board Level is a dual ISM band (865-870 and 902-928 MHz) networked
transceiver supporting license-free wireless communications around the world. With
available throughput up 2.6Mbps, the TMR1 allows you to seamlessly integrate both serial
and Ethernet traffic as well as having the throughput available for video. Range as high
as 70 miles has been demonstrated in low noise environments. The TMR1 Board Level’s
high performance and versatility make it ideal for oil/gas, water and electric utilities,
environmental monitoring and agricultural applications.
ADAPTIVE SPEED/MODULATION TECHNOLOGY
The Trimble TMR1 supports both point-to-point and point-to-multipoint network
topologies. With most networked radios operating in point-to-multipoint mode,
the speed of the access point radio is restricted to the speed and modulation of
the weakest link.
DUAL DATA PORTS FOR BOTH SERIAL AND IP COMMUNICATION
The Trimble TMR1 Board Level is equipped with two RJ45 connectors: one for serial and
one for Ethernet. This allows you to attach sensors to the TMR1 Board Level in the field
and to communicate with any TMR1 Board Level via Ethernet cables, a LAN/WAN or the
Internet. All links can be protected by AES 128- and 256-bit data encryption and VLAN
segregation, so only you can communicate with your network.
Outstanding In Redundancy And Security - Korenix Ethernet Switches Brochure ...

The document discusses Korenix managed Ethernet switches for industrial applications. It provides specifications for various switch models, including the number and type of ports, supported network redundancy and security features, management capabilities, environmental tolerances, and contact information. The switches provide multiple redundancy technologies to minimize downtime, including ring redundancy with 5ms failure recovery and seamless restoration. They also offer security features like VLAN protection, private VLANs, port security, and various access control lists.
MSIP report

LM Ericsson is a leading telecommunications equipment manufacturer, providing mobile systems solutions and end-to-end network solutions to operators. The author completed an internship at Ericsson where they learned about technical and corporate skills while helping to upgrade the software on 2000 network nodes in Bangladesh. They gained experience in fields maintenance and saw first-hand how Ericsson maintains high quality networks for its customers.
III_UNIT.pptx

This document summarizes key concepts about the data link layer. It discusses the services provided to the network layer including unacknowledged connectionless service, acknowledged connectionless service, and acknowledged connection-oriented service. It describes framing, including frame structure with header, payload, and trailer. Error control using Automatic Repeat Request and flow control are explained. Stop-and-wait and sliding window protocols are given as examples of error control and flow control mechanisms.
III_UNIT.pptx

This document summarizes key concepts about the data link layer. It discusses the services provided to the network layer including unacknowledged connectionless service, acknowledged connectionless service, and acknowledged connection-oriented service. It describes framing, including frame structure with header, payload, and trailer. Error control using Automatic Repeat Request and flow control are explained. Frame types can be fixed-sized or variable-sized, using techniques like length field or end delimiter. The advantages of framing are also provided.
6500-M User Manual

1. The document provides instructions for setting up a Mako network appliance. It describes connecting the appliance to an Ethernet switch, internet connection via DSL or cable, and installing firmware.
2. Setting up a cellular connection requires inserting a SIM card into the appliance and configuring the connection settings through the Central Management System interface.
3. Troubleshooting guidance is provided for checking firmware installation status and testing internet connections. The Makoscope diagnostic tool accessible through the CMS can also check connection status.
Similar to A More Reilable LAN by MSR Redundant Ring - Redundant Technology 2018 (20)
Ensuring Network Reliabilty And Quality For IP Surveillance 2012

Ensuring Network Reliabilty And Quality For IP Surveillance 2012
Broadcast Storm - The Root Causes And The Solutions - Whitepaper 2012

Broadcast Storm - The Root Causes And The Solutions - Whitepaper 2012
High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure

High Speed Long Range Wireless SCADA Radio Modem TMR1 - IP67 Enclosure
LE-240XTCS LE-280XTS - Ethernet module for the LET-36 chassis

LE-240XTCS LE-280XTS - Ethernet module for the LET-36 chassis
High Speed Long Range SCADA Radio Modem TMR1 - OEM

High Speed Long Range SCADA Radio Modem TMR1 - OEM
Outstanding In Redundancy And Security - Korenix Ethernet Switches Brochure ...

Outstanding In Redundancy And Security - Korenix Ethernet Switches Brochure ...
More from Jiunn-Jer Sun
Make The Impossible Possible - Industrial PoE Brochure 2014

This document provides specifications for the JetCon 1702 PoE switch, including:
- It has two RJ-45 ports that provide data and PoE power using either Alternative A or B wiring.
- It supports both IEEE 802.3af and 802.3at PoE standards, providing up to 15W or 30W of power per port respectively.
- Additional features include overcurrent, overvoltage, and overtemperature protection for the PoE ports.
Transformation From Today To Tomorrow - Market and Product Strategy 2018

This document outlines a strategy for transforming industrial communication networks from today to the future. It analyzes current solutions and identifies trends impacting networks, including cloud connectivity, network security, and cloud networking. The transformation roadmap involves three phases over the next 5 years: 1) focusing on cloud/security, 2) convergence and scalability, and 3) network virtualization and agility. The goal is for networks to become more flexible, modular, and integrated through both physical and virtual components using technologies like TSN, 5G, wireless, and NFV.
Market Trend And Korenix IIoT Vision - 2018

This document discusses Korenix's vision for becoming an IIoT player by leveraging trends in cloud connectivity, cybersecurity, and the gap between IT and OT networks. It outlines Korenix's opportunities in advanced security features, edge devices, and cloud solutions. The document proposes a roadmap over 3 years to build out Korenix's next generation product family, refine security capabilities, achieve key certifications, develop cloud connectivity and networking solutions, and market Korenix as a total IIoT solution provider through new product pilots and ongoing development.
Industrial Wireless for Transportation - Korenix Wireless Solution 2016

Industrial Wireless Solution For Transportation
- Korenix provides wireless solutions for various transportation applications including railway, heavy vehicles, and vehicles using their JetWave product families.
- The solutions offer full IP communication, low power consumption, ruggedized devices, high performance, and different classes of passenger WiFi services.
- Example devices include the JetWave 3000 series for rail and heavy vehicles and JetWave 2000 series for vehicles, offering features like WiFi, cellular connectivity, switching, routing and traffic shaping.
Secure Reliable Quality Networking Solutions for Railway 2019

This document discusses Korenix's industrial data communication solutions for railways. It provides an overview of Korenix as a company, their product lines, and experience with various railway projects. Specific examples are given of passenger WiFi projects in the UK and Australia where Korenix's industrial switches and access points provided reliable connectivity. Features are described like Power over Ethernet reliability, link reliability through redundant rings, and network separation capabilities. The document promotes Korenix's ability to provide full-range networking solutions and customize solutions for railway projects.
Effective Network Security Against Cyber Threats - Network Segmentation Techn...

Primary ports can access all other ports, community ports can communicate within their group and with primary ports, and isolated ports can only communicate with their primary port. Korenix's private VLAN technology separates devices within a VLAN group to achieve higher security than traditional VLANs. It establishes three types of VLANs - primary, community, and isolated - to finely separate devices and limit traffic paths according to device behavior. Configuring a private VLAN involves creating the VLAN, assigning secondaries to primaries, and assigning ports, providing easier management than traditional VLAN tables.
Power Distribution Feeder Automation - Application Story 2012

Feeder automation systems in Taiwan monitor and control power distribution networks. Korenix's fiber Ethernet switches and redundant ring technology were used to implement the fiber network connecting feeder terminal units along the distribution system. This enabled failure detection, identification, recovery, and reporting to minimize error handling time and ensure continuous network service when failures occurred on the fiber links.
Enhancing Network Quality for Video Transmission 2012

This document discusses the benefits of using multicast over unicast and broadcast for video transmission in IP surveillance networks. It explains that multicast allows an IP camera to transmit video to multiple clients simultaneously without overloading bandwidth or the camera itself. The document emphasizes that IGMP is needed to integrate multicast efficiently and that Korenix switches support optimized IGMP snooping and querying to provide high-quality, scalable video transmission across surveillance networks.
Beijer Korenix Connected - Beijer Sales Kit 2019

This document discusses various networking products from Korenix, including unmanaged switches, managed switches, media converters, wireless access points, and cellular routers. It provides information on selecting the appropriate product for different customer needs and applications, such as single machine networks, extensible machine networks, and building automation systems. It also highlights features of Korenix products like network redundancy, security, and real-time monitoring capabilities.
Defend Your DHCP Infrastructure Against Cyber Attacks - Network Security Feat...

This document discusses defending a DHCP infrastructure against cyber attacks. It describes how DHCP works to assign IP addresses via a client-server model. It then outlines common attacks like DHCP spoofing and starvation. It recommends deploying DHCP Snooping on switches to validate DHCP messages and filter invalid ones to prevent attacks and ensure correct network configuration.
Build A Solid Foundation For Industrial Network Security - Cybersecurity Webi...

Agenda
- The unknown truth of cyber threats
- The myths of network security
- Attack and defense analysis
- IEC 62443 standard and how it impacts on you
- IT vs. OT security and the golden rule of defense
- A foundation where technology meets humanity
Essential Protection for The Fundamental of IP Networking - Cybersecurity Tra...

Agenda
• Why IP address and MAC address
• How packets are delivered through the network
• The address resolution mechanism (ARP) and how it works
• Vulnerabilities and cyberattacks to ARP
• Defense by network security Dynamic ARP Inspection
• Korenix products with advanced cybersecurity features
Protect Your DHCP Infrastructure from Cyber Attacks - Cybersecurity Training ...

Agenda
• IEC 62443 IACS standard
• Scope and why
• DHCP protocol and how it works
• DHCP’s Vulnerabilities
• Types of Cyber Attacks to DHCP
• Defense by network security DHCP Snooping
• Korenix products with advanced security features
A Big Picture of IEC 62443 - Cybersecurity Webinar (2) 2020

• Why An Industrial Cybersecurity Standard
• What Is IEC 62443 About
• How It Impacts On You - The Security Lifecycle
• IEC 62443 Certificates
• Reference: Some Ongoing Projects
• Summary
Protect The Fundamental of IP Networking - Network Security Features 2019

The document discusses how IP addresses are resolved to MAC addresses through the Address Resolution Protocol (ARP) and how ARP spoofing attacks threaten industrial network security. It describes how ARP works and how attackers can spoof ARP responses to redirect network traffic. The document advocates for using Dynamic ARP Inspection on industrial Ethernet switches to validate IP-MAC bindings and prevent ARP spoofing attacks from occurring. Securing ARP is important for protecting the basic operations of industrial IP networking.
Levels Up Your Redundant Network By ERPS - Redundant Technology 2019

ERPS (Ethernet Ring Protection Switching) is an open standard for network redundancy in industrial applications. It utilizes ring topologies to provide fast recovery from link failures within 50ms while also allowing flexibility through coupling multiple independent rings. Version 2 of ERPS improves on version 1 by enabling various non-ring topologies without compromising recovery time and eliminating potential packet loss during network restoration. Korenix supports both ERPS versions as well as proprietary and other standards-based redundant solutions to meet different industrial networking needs.
Making Your Heavy Chores Easy - Industrial PoE Handbook 2008

1. Reliability is critical, so PoE devices must withstand harsh conditions like vibration and temperature extremes. Single points of failure could cause major issues.
2. Industrial systems may require diverse output voltages that fall outside the standard PoE range, requiring additional equipment.
3. Some industrial devices have ultra power demands beyond what standard PoE can provide, or maximum power limitations could be an issue with supporting multiple high-power devices.
Get Inspired By Beijer's Wireless Solution - Wireless Brochure 2016

This document provides information on various wireless networking products from Beijer Electronics, including WiFi access points and routers. It lists the key features and specifications of different models, such as the number of radios, supported frequency bands, maximum data rates, outdoor protection ratings, and antenna options. Application scenarios for each product are also described, such as creating wireless backbones, point-to-point links, and networks for mobile or industrial environments.
Flying You From Wired To Wireless - Product Brochure 2013

This document provides information on various networking products from Korenix for industrial applications. It includes switches, wireless access points, media converters, and a network management system. The products highlighted have features like robust housing, long distance connectivity, fiber support, Power over Ethernet, and reliability in harsh environments.
More from Jiunn-Jer Sun (20)
Make The Impossible Possible - Industrial PoE Brochure 2014

Make The Impossible Possible - Industrial PoE Brochure 2014
Transformation From Today To Tomorrow - Market and Product Strategy 2018

Transformation From Today To Tomorrow - Market and Product Strategy 2018
Industrial Wireless for Transportation - Korenix Wireless Solution 2016

Industrial Wireless for Transportation - Korenix Wireless Solution 2016
Secure Reliable Quality Networking Solutions for Railway 2019

Secure Reliable Quality Networking Solutions for Railway 2019
Effective Network Security Against Cyber Threats - Network Segmentation Techn...

Effective Network Security Against Cyber Threats - Network Segmentation Techn...
Power Distribution Feeder Automation - Application Story 2012

Power Distribution Feeder Automation - Application Story 2012
Enhancing Network Quality for Video Transmission 2012

Enhancing Network Quality for Video Transmission 2012
Defend Your DHCP Infrastructure Against Cyber Attacks - Network Security Feat...

Defend Your DHCP Infrastructure Against Cyber Attacks - Network Security Feat...
Build A Solid Foundation For Industrial Network Security - Cybersecurity Webi...

Build A Solid Foundation For Industrial Network Security - Cybersecurity Webi...
Essential Protection for The Fundamental of IP Networking - Cybersecurity Tra...

Essential Protection for The Fundamental of IP Networking - Cybersecurity Tra...
Protect Your DHCP Infrastructure from Cyber Attacks - Cybersecurity Training ...

Protect Your DHCP Infrastructure from Cyber Attacks - Cybersecurity Training ...
A Big Picture of IEC 62443 - Cybersecurity Webinar (2) 2020

A Big Picture of IEC 62443 - Cybersecurity Webinar (2) 2020
Protect The Fundamental of IP Networking - Network Security Features 2019

Protect The Fundamental of IP Networking - Network Security Features 2019
Levels Up Your Redundant Network By ERPS - Redundant Technology 2019

Levels Up Your Redundant Network By ERPS - Redundant Technology 2019
Wireless AP and Antenna Quick Selection Guide 2013

Wireless AP and Antenna Quick Selection Guide 2013
Making Your Heavy Chores Easy - Industrial PoE Handbook 2008

Making Your Heavy Chores Easy - Industrial PoE Handbook 2008
Get Inspired By Beijer's Wireless Solution - Wireless Brochure 2016

Get Inspired By Beijer's Wireless Solution - Wireless Brochure 2016
Flying You From Wired To Wireless - Product Brochure 2013

Flying You From Wired To Wireless - Product Brochure 2013
Recently uploaded
Presentation of the OECD Artificial Intelligence Review of Germany

Consult the full report at https://www.oecd.org/digital/oecd-artificial-intelligence-review-of-germany-609808d6-en.htm
“I’m still / I’m still / Chaining from the Block”

“An Outlook of the Ongoing and Future Relationship between Blockchain Technologies and Process-aware Information Systems.” Invited talk at the joint workshop on Blockchain for Information Systems (BC4IS) and Blockchain for Trusted Data Sharing (B4TDS), co-located with with the 36th International Conference on Advanced Information Systems Engineering (CAiSE), 3 June 2024, Limassol, Cyprus.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
UiPath Test Automation using UiPath Test Suite series, part 6

Welcome to UiPath Test Automation using UiPath Test Suite series part 6. In this session, we will cover Test Automation with generative AI and Open AI.
UiPath Test Automation with generative AI and Open AI webinar offers an in-depth exploration of leveraging cutting-edge technologies for test automation within the UiPath platform. Attendees will delve into the integration of generative AI, a test automation solution, with Open AI advanced natural language processing capabilities.
Throughout the session, participants will discover how this synergy empowers testers to automate repetitive tasks, enhance testing accuracy, and expedite the software testing life cycle. Topics covered include the seamless integration process, practical use cases, and the benefits of harnessing AI-driven automation for UiPath testing initiatives. By attending this webinar, testers, and automation professionals can gain valuable insights into harnessing the power of AI to optimize their test automation workflows within the UiPath ecosystem, ultimately driving efficiency and quality in software development processes.
What will you get from this session?
1. Insights into integrating generative AI.
2. Understanding how this integration enhances test automation within the UiPath platform
3. Practical demonstrations
4. Exploration of real-world use cases illustrating the benefits of AI-driven test automation for UiPath
Topics covered:
What is generative AI
Test Automation with generative AI and Open AI.
UiPath integration with generative AI
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...Edge AI and Vision Alliance
For the full video of this presentation, please visit: https://www.edge-ai-vision.com/2024/06/building-and-scaling-ai-applications-with-the-nx-ai-manager-a-presentation-from-network-optix/
Robin van Emden, Senior Director of Data Science at Network Optix, presents the “Building and Scaling AI Applications with the Nx AI Manager,” tutorial at the May 2024 Embedded Vision Summit.
In this presentation, van Emden covers the basics of scaling edge AI solutions using the Nx tool kit. He emphasizes the process of developing AI models and deploying them globally. He also showcases the conversion of AI models and the creation of effective edge AI pipelines, with a focus on pre-processing, model conversion, selecting the appropriate inference engine for the target hardware and post-processing.
van Emden shows how Nx can simplify the developer’s life and facilitate a rapid transition from concept to production-ready applications.He provides valuable insights into developing scalable and efficient edge AI solutions, with a strong focus on practical implementation.Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
20240607 QFM018 Elixir Reading List May 2024

Everything I found interesting about the Elixir programming ecosystem in May 2024
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

Leonard Jayamohan, Partner & Generative AI Lead, Deloitte
This keynote will reveal how Deloitte leverages Neo4j’s graph power for groundbreaking digital twin solutions, achieving a staggering 100x performance boost. Discover the essential role knowledge graphs play in successful generative AI implementations. Plus, get an exclusive look at an innovative Neo4j + Generative AI solution Deloitte is developing in-house.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
Recently uploaded (20)
Presentation of the OECD Artificial Intelligence Review of Germany

Presentation of the OECD Artificial Intelligence Review of Germany
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
UiPath Test Automation using UiPath Test Suite series, part 6

UiPath Test Automation using UiPath Test Suite series, part 6
“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...

“Building and Scaling AI Applications with the Nx AI Manager,” a Presentation...
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...

GraphSummit Singapore | The Future of Agility: Supercharging Digital Transfor...
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
A More Reilable LAN by MSR Redundant Ring - Redundant Technology 2018
- 1. MSR (Multiple Super Ring) Make A More Reliable LAN by Korenix MSR Industrial Data Communication by Korenix – A Beijer Group Company Link loss RM failure Backup RM Backup RM Backup RM Backup RM How It Works There are 4 running stages: Configure & Install: Switches are linked into a ring. One of them is automatically elected as RM (Ring Manager), while the others become backup RM. RM blocks one of its ring ports as a backup path and starts to monitor the ring status. Failure Recovery: Following a link or device failure, RM activates its backup path. Topology changes and traffic resumes. RM will jump to the failure position and prepares for later Seamless Restoration (patented). In case of RM failure, the one next to it becomes RM. The ring is always under control. (patented) Trouble Shooting: The ring is broken and has to be fixed asap. MSR warns and provides information about the failure position to help fast trouble shooting. Restoration: Putting a new link to fix the failure. The ring forms again. MSR achieves 0ms Seamless Restoration by using the restored link as the backup path. Traffic flows as it was without being disturbed. There is no topology change, packet loss, or broadcast storm. It’s the most stable ring technology. (patented) Korenix’s patented redundant ring technology delivers more benefits than fast recovery. It’s fast, stable, and easy to use. Its unique design eliminates the risks of single point of failure or broadcast storm. It turns out a comprehensive superiority over other ring technologies through all running stages.
- 2. Configuration made easy Superior In All Running Stages It’s designed to be used without the need of IT knowledge. RM and backup path are elected automatically. Step 1 Create a new ring with an ID Step 2 Choose ring ports Step 3 Enable (Done!) MSR Other proprietary rings * CONFIGURE & INSTALL • Simple • Assign ring ports and enable • RM and backup path auto selected • Mistake indication • Manually • Not support FAILURE RECOVERY • Fast • 5ms recovery minimizes packet loss • RM Redundancy – no critical point • Network resumes immediately • 20ms or more • Single point of failure • Wait until RESTORATION TROUBLE SHOOTING • Clear • LED failure positioning • Warning notification • Live topology map • No LED positioning RESTORATION • Seamless • 0ms Seamless Restoration • No topology change – stable • No packet loss – no error • No broadcast storm – risk free • 20ms or more • Topology change • Packet loss or risk of broadcast storm Healthy Link Loss Configure Error ? * In most cases Ring Status LED indicator helps field engineers to identify failure cause and position. Industrial Data Communication by Korenix – A Beijer Group Company
- 3. More Than One Ring MultiRing connects multiple rings in the simplest way. Each ring operates independently. TrunkRing multiples the bandwidth and the redundancy by aggregating multiple ring links. Rapid Dual Homing connects to a 3rd party network by multiple nodes or redundant links. Super Chain extends a ring network by a chain. The chain has its own redundant protection. • How many nodes can be in a ring? Up to 250 switches in a ring without compromise in recovery time. • What speed and media? It doesn’t matter. A ring can be composed by 100Mbps or gigabit, by copper or fiber mixed. • Why can’t I find RM indicator? The RM of most ring technologies is fixed and is a critical point. It’s very important to know RM position for the reason of single point of failure. Thanks to the patent of RM Redundancy, MSR solves this issue and uses RS (Ring Status) indicator instead for more benefits. • How to monitor the ring status? You can monitor ring status by LED indicator, web, CLI, SNMP, Korenix network management software, Modbus TCP, and can be informed by email, SNMP trap, relay alarm for warning events. • Why broadcast storm occurs to a ring and how to solve it? A ring without a blocking path is a loop, which let go broadcast packet runs in the circle endlessly and overwhelms the network in a blink. It is highly risky during restoration, reboot from blackout, or RM failure. MSR’s Seamless Restoration prevents loop, RM Redundancy recovers RM failure, which in turn eliminates the possibility of broadcast storm. FAQ Industrial Data Communication by Korenix – A Beijer Group Company
