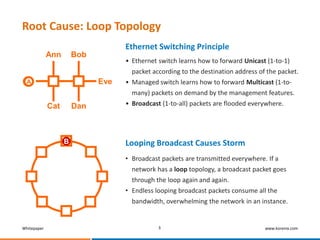
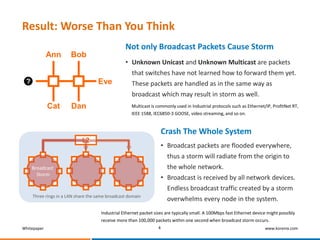
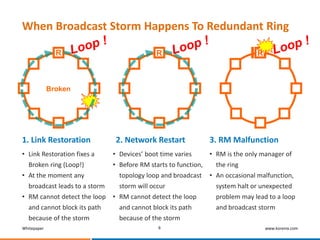
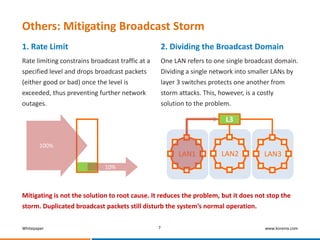
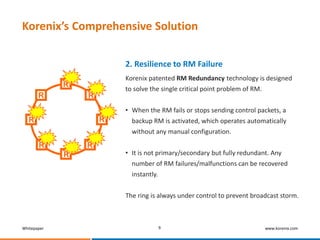
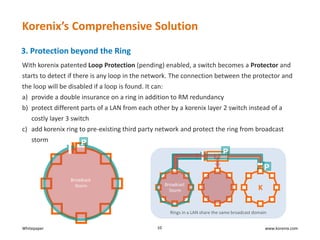
This whitepaper discusses broadcast storms in industrial Ethernet networks that use redundant ring topologies. It reveals that broadcast storms occur due to loops in the network topology that are created during events like link restoration or network restarts. This overwhelms the network with broadcast traffic. The whitepaper then presents Korenix's comprehensive solution to prevent broadcast storms which includes technologies that prevent loops from forming, ensure resilience during ring manager failures, and provide protection beyond individual rings.