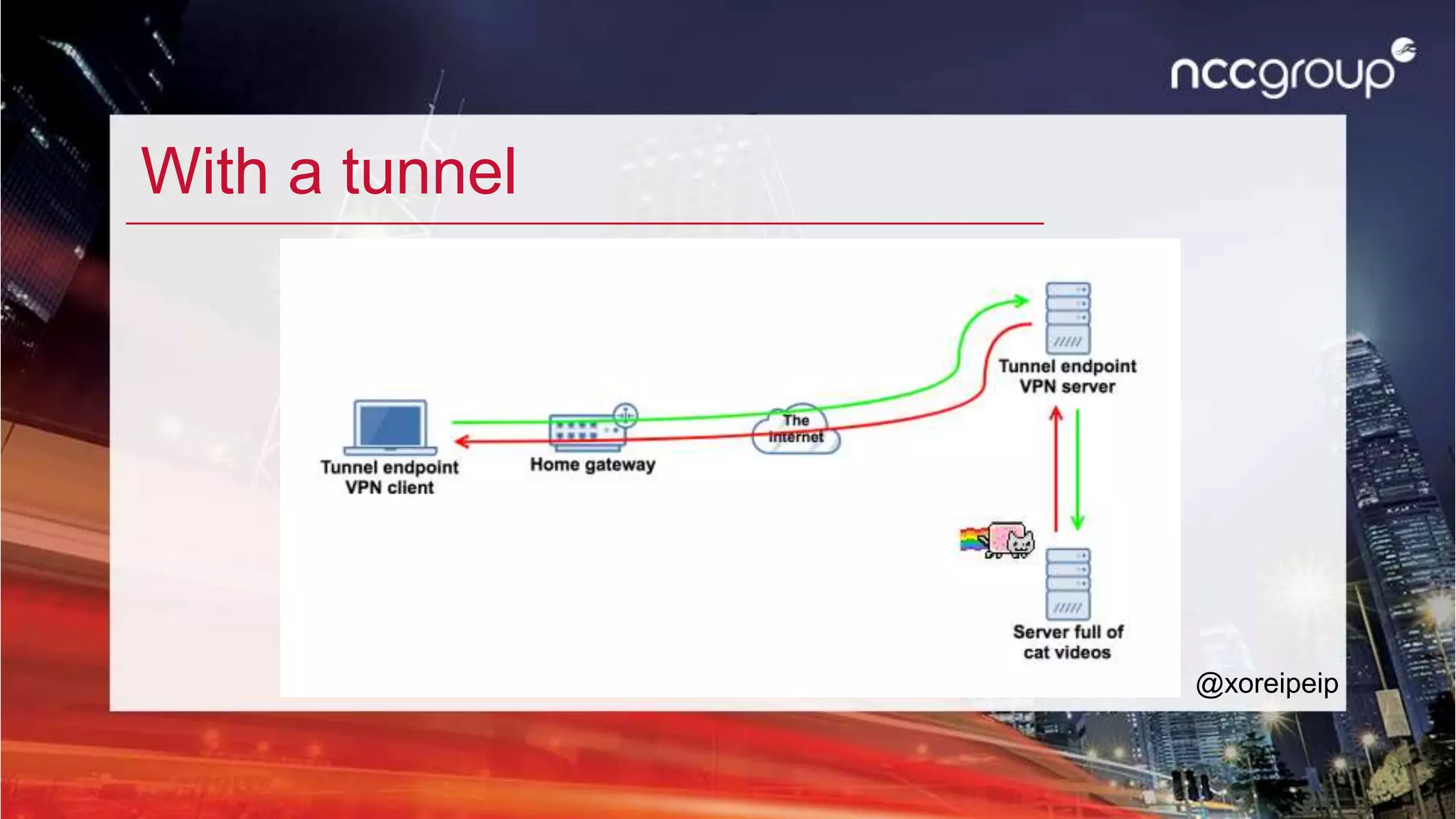
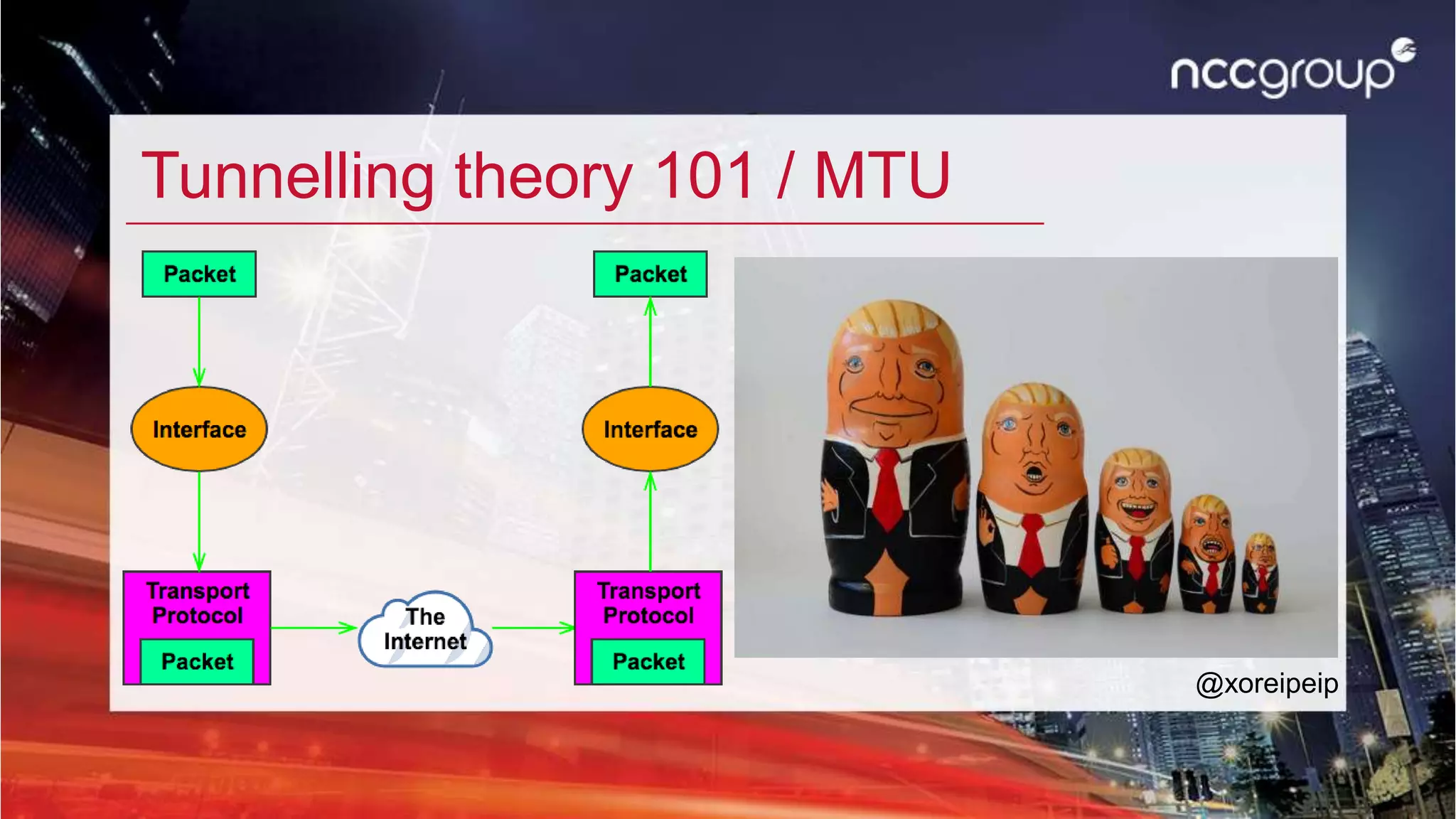
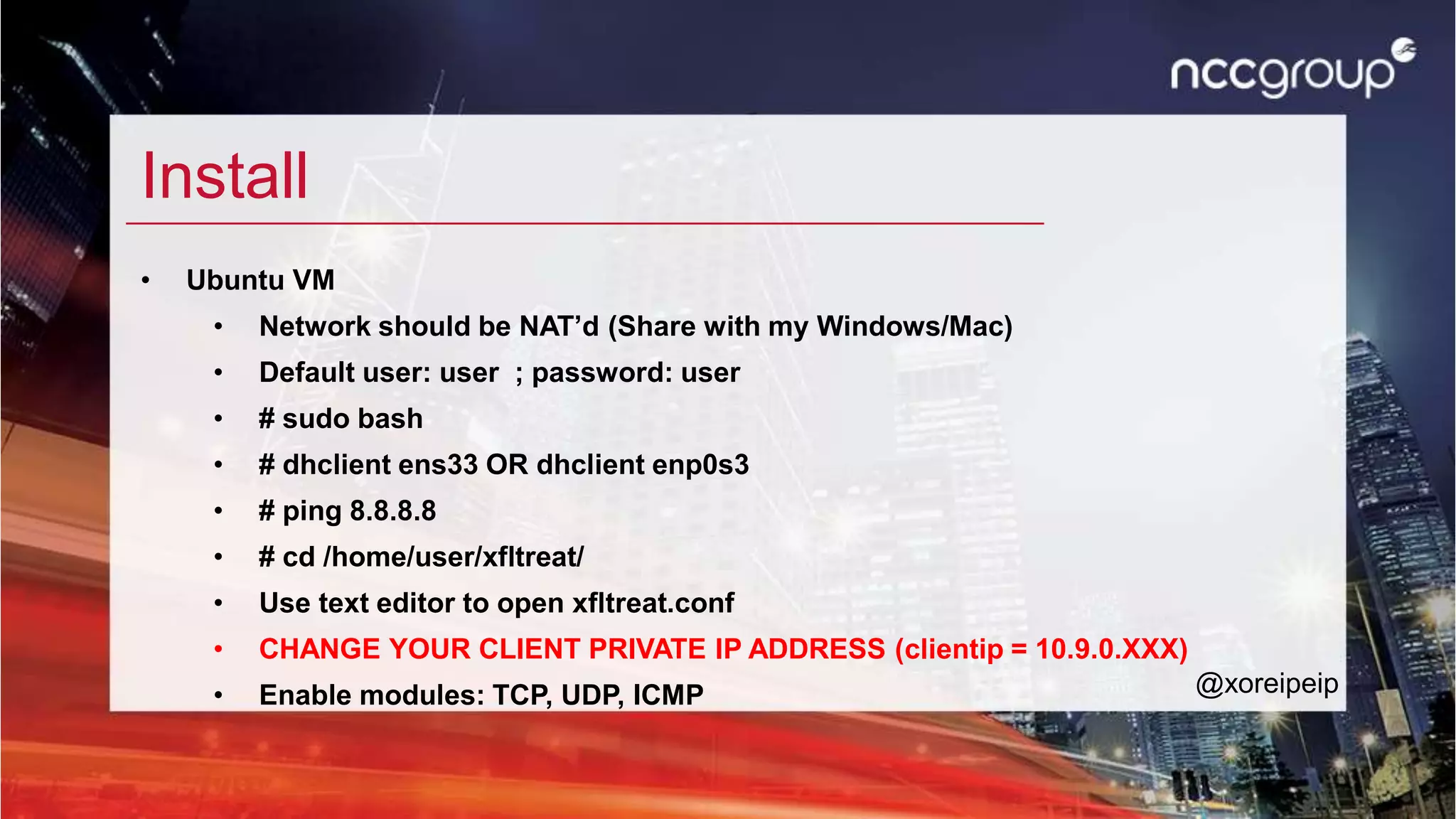
This document summarizes a presentation about escaping locked down networks. It discusses using tools like XFLTReaT to bypass network restrictions by tunneling traffic through unfiltered protocols. Specific techniques covered include changing the MAC address, using alternative gateways, exploiting misconfigured proxies or firewalls, and setting up tunnels through protocols like SSH, ICMP, or RDP. The presentation also demonstrates how to install and use XFLTReaT on Linux and Windows systems to test what protocols are unfiltered on a network.


















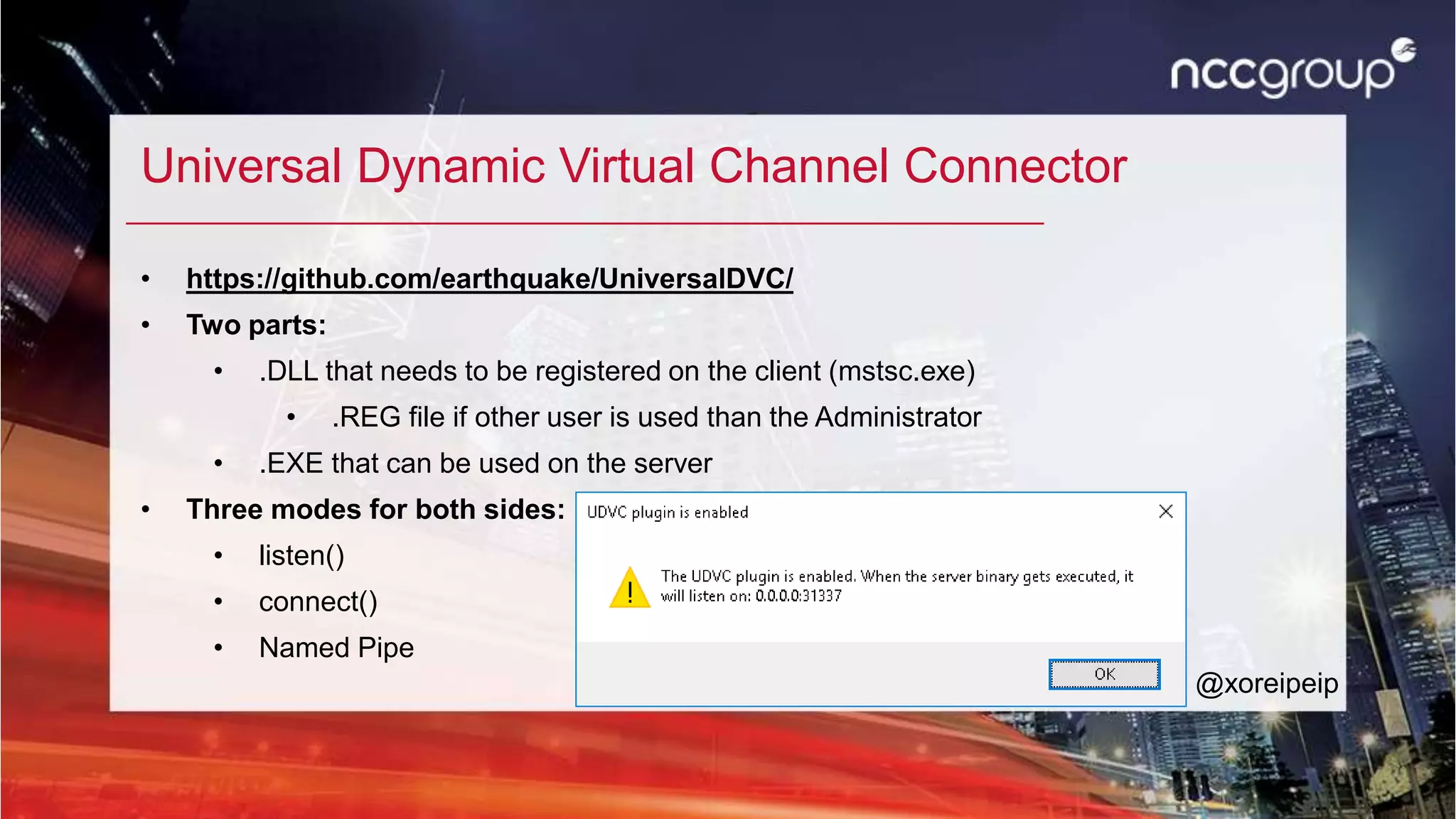





![Install
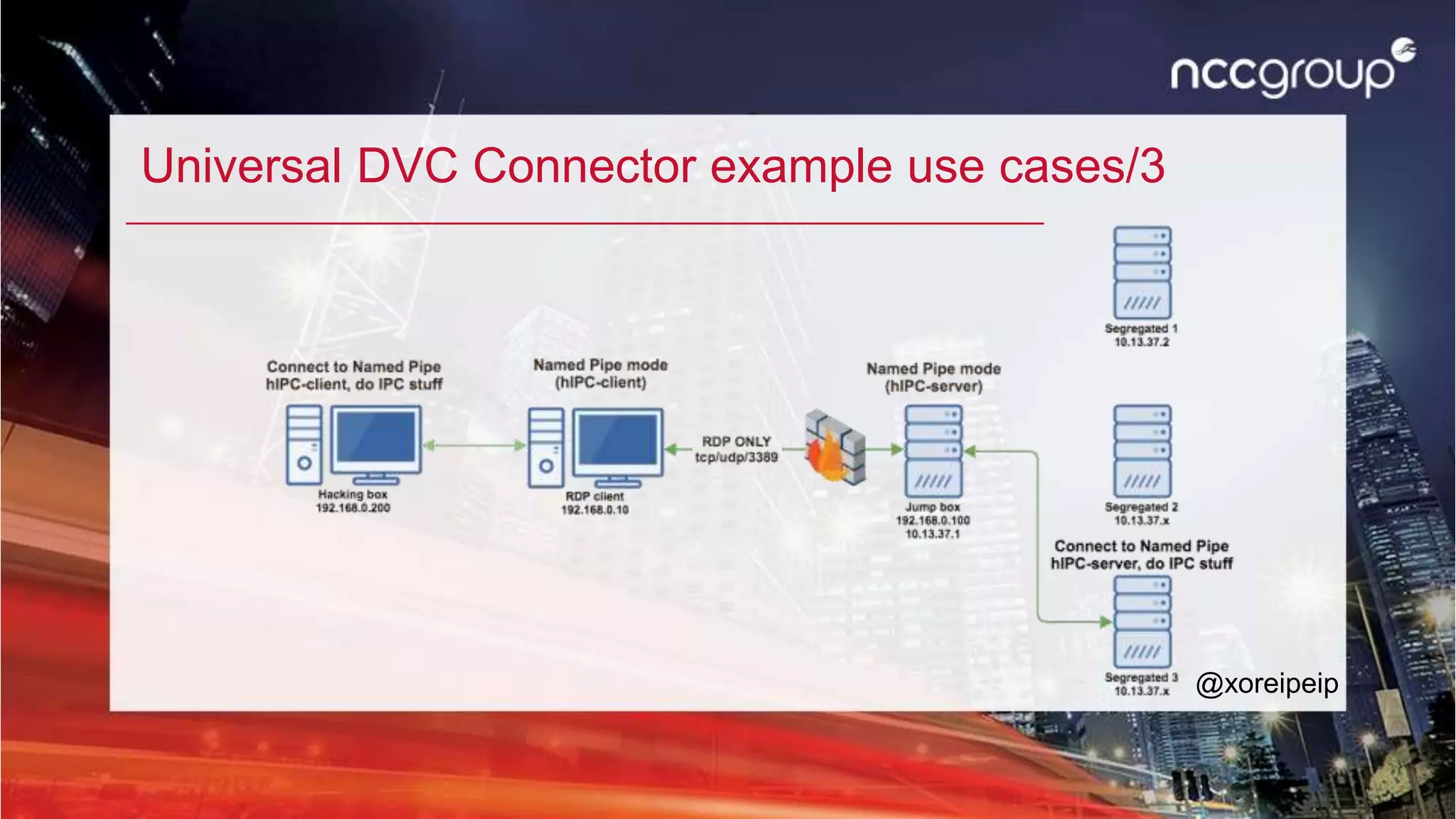
• Windows
• Are you using Vista SP1 or newer?
• Are you using 32bit or 64bit Windows?
• Install vc_redist.x86 / x64.exe
• Unzip the right zip file
• Open a cmd/powershell with Administrator rights
• regsvr32.exe /u UDVC-Plugin[x86 | x64].dll
@xoreipeip](https://image.slidesharecdn.com/hackersuli-workshop-xflws-180826095451/75/Hogy-jussunk-ki-lezart-halozatokbol-29-2048.jpg)
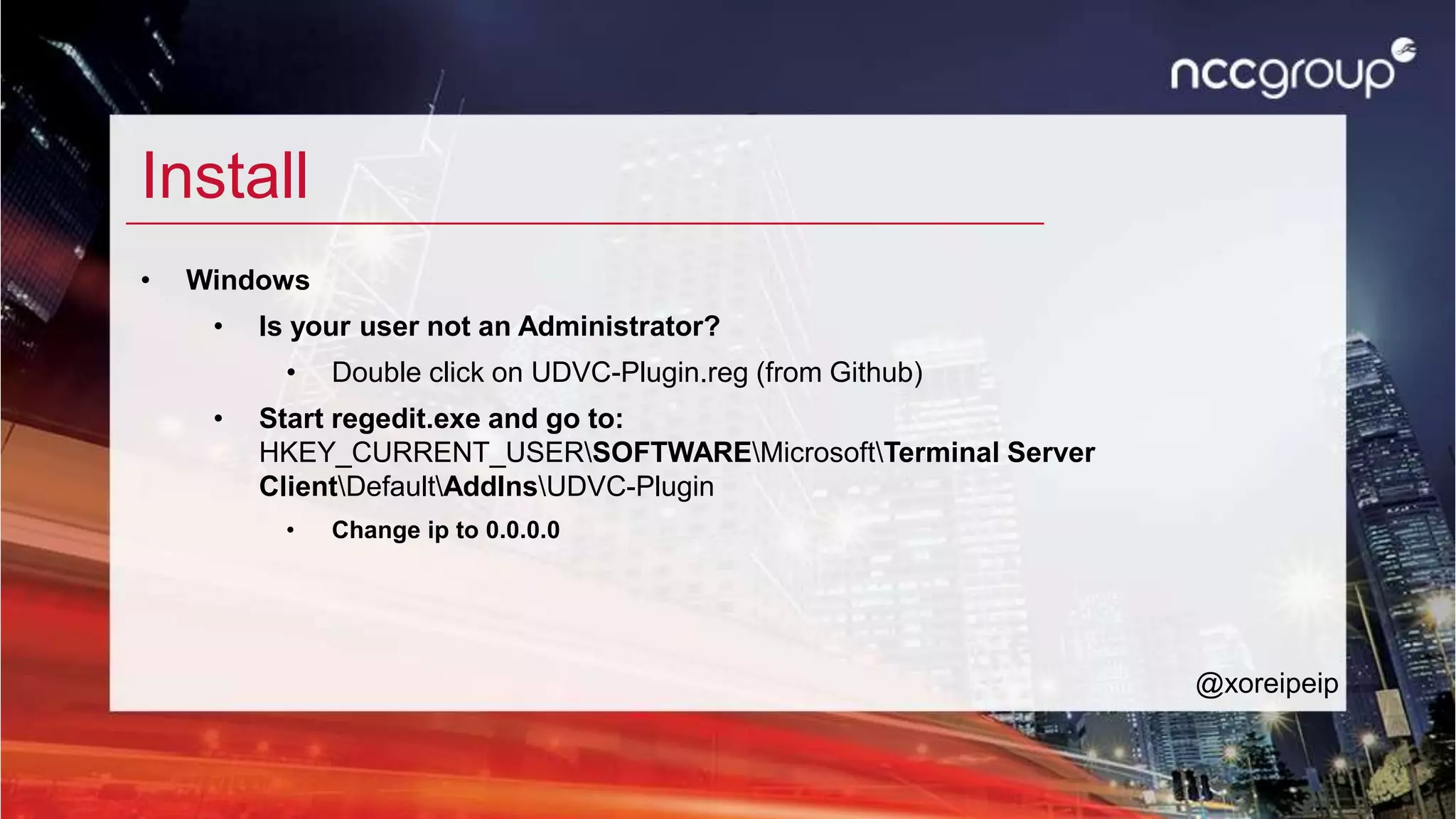
![Config UDVC + connect RDP
• enabled -> 1
• mode -> 0
• ip -> 0.0.0.0
• port -> 31337
• Start mstsc.exe (Remote Desktop Client)
• Connect: 18.184.9.137
• User: xfl[your number]
• Password: HekkerSuli18
@xoreipeip](https://image.slidesharecdn.com/hackersuli-workshop-xflws-180826095451/75/Hogy-jussunk-ki-lezart-halozatokbol-31-2048.jpg)






