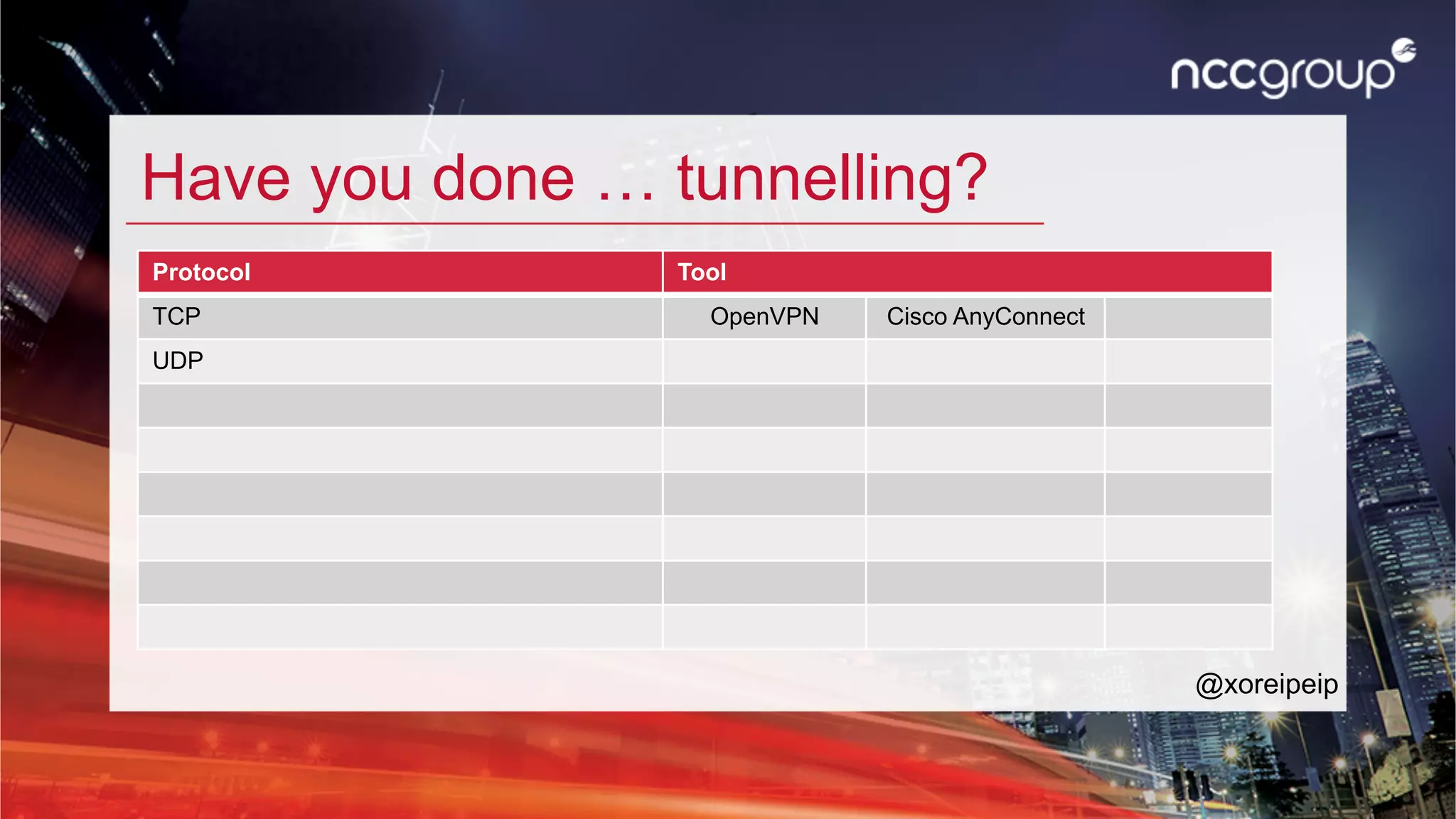
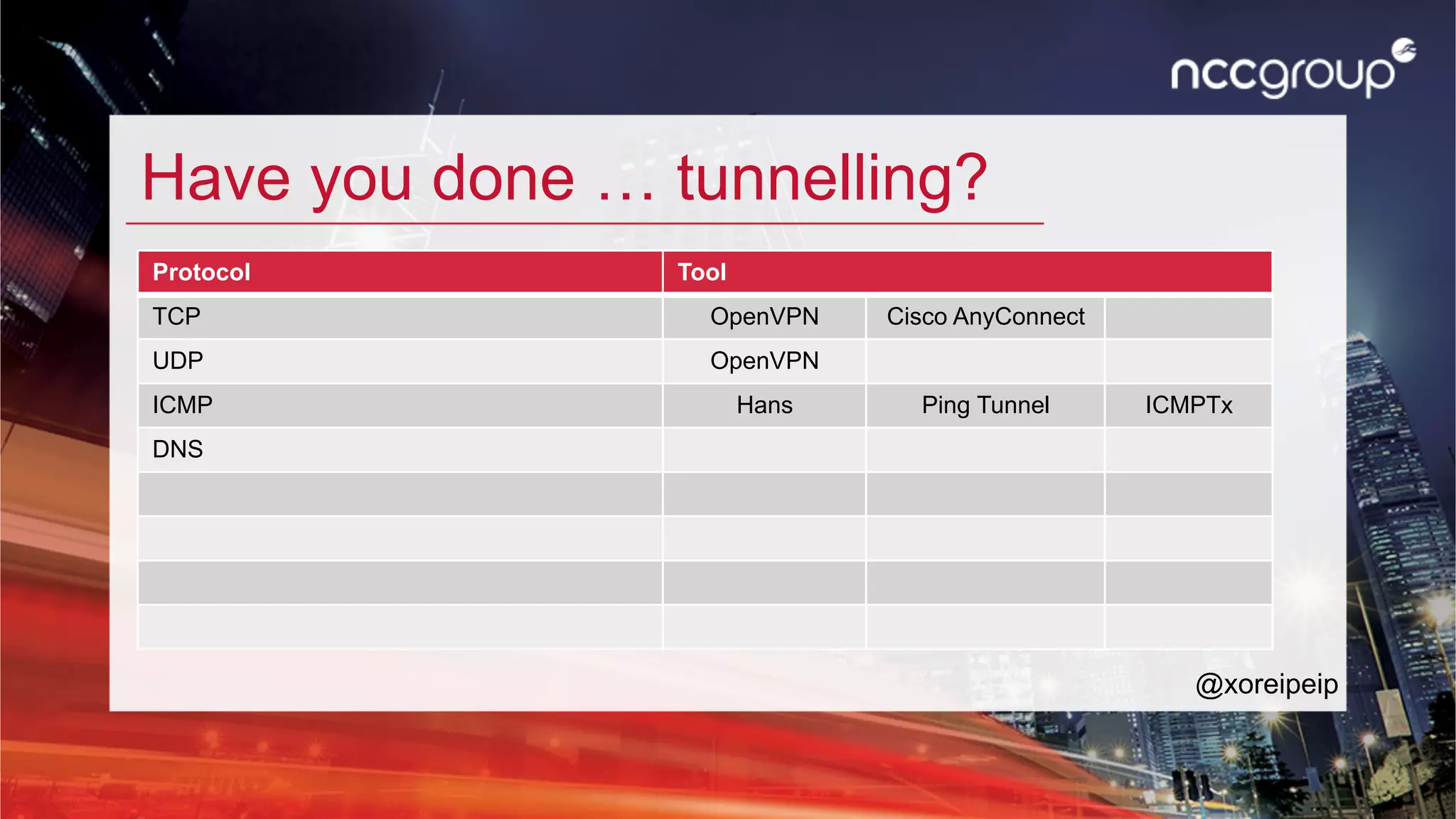
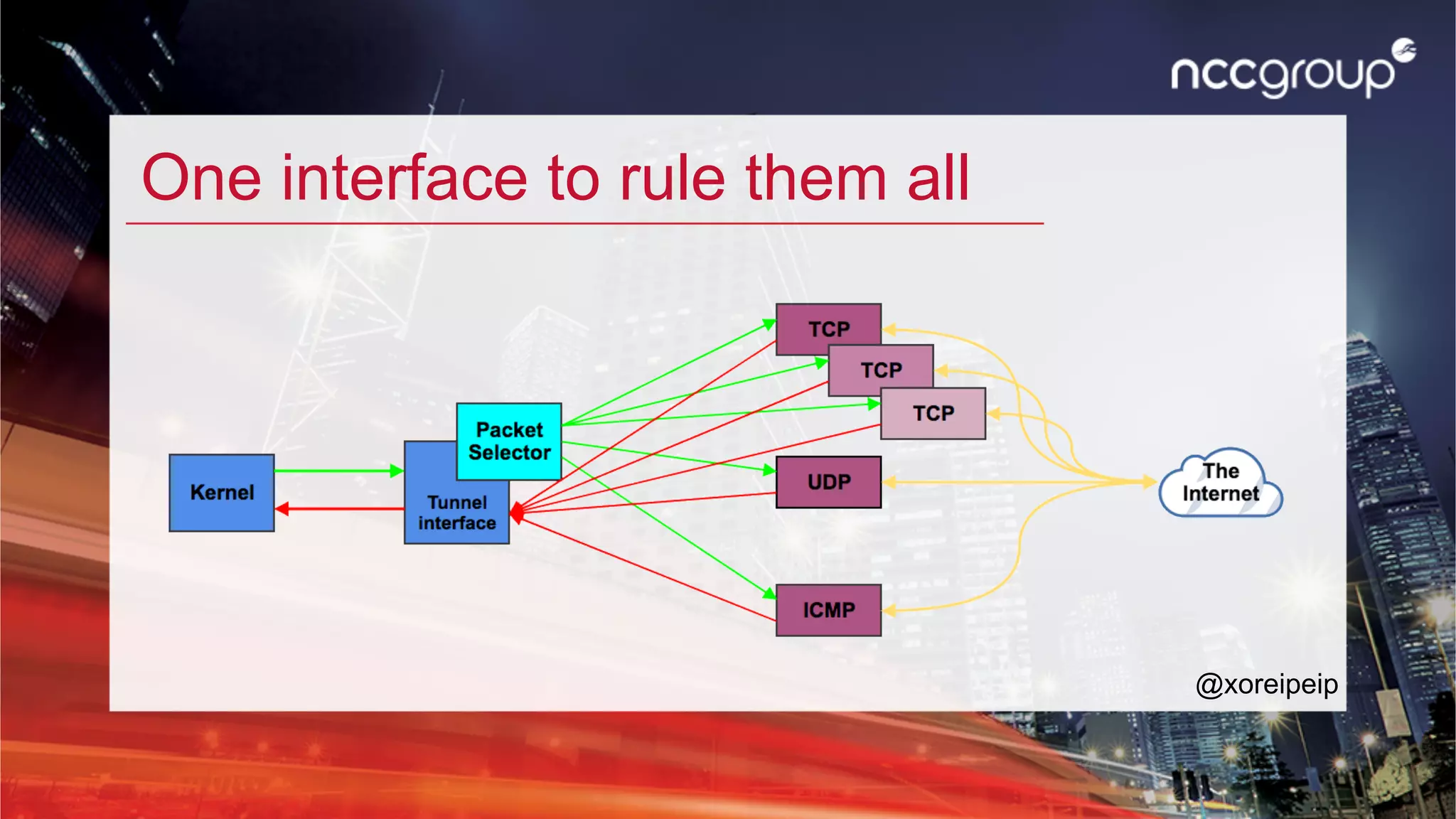
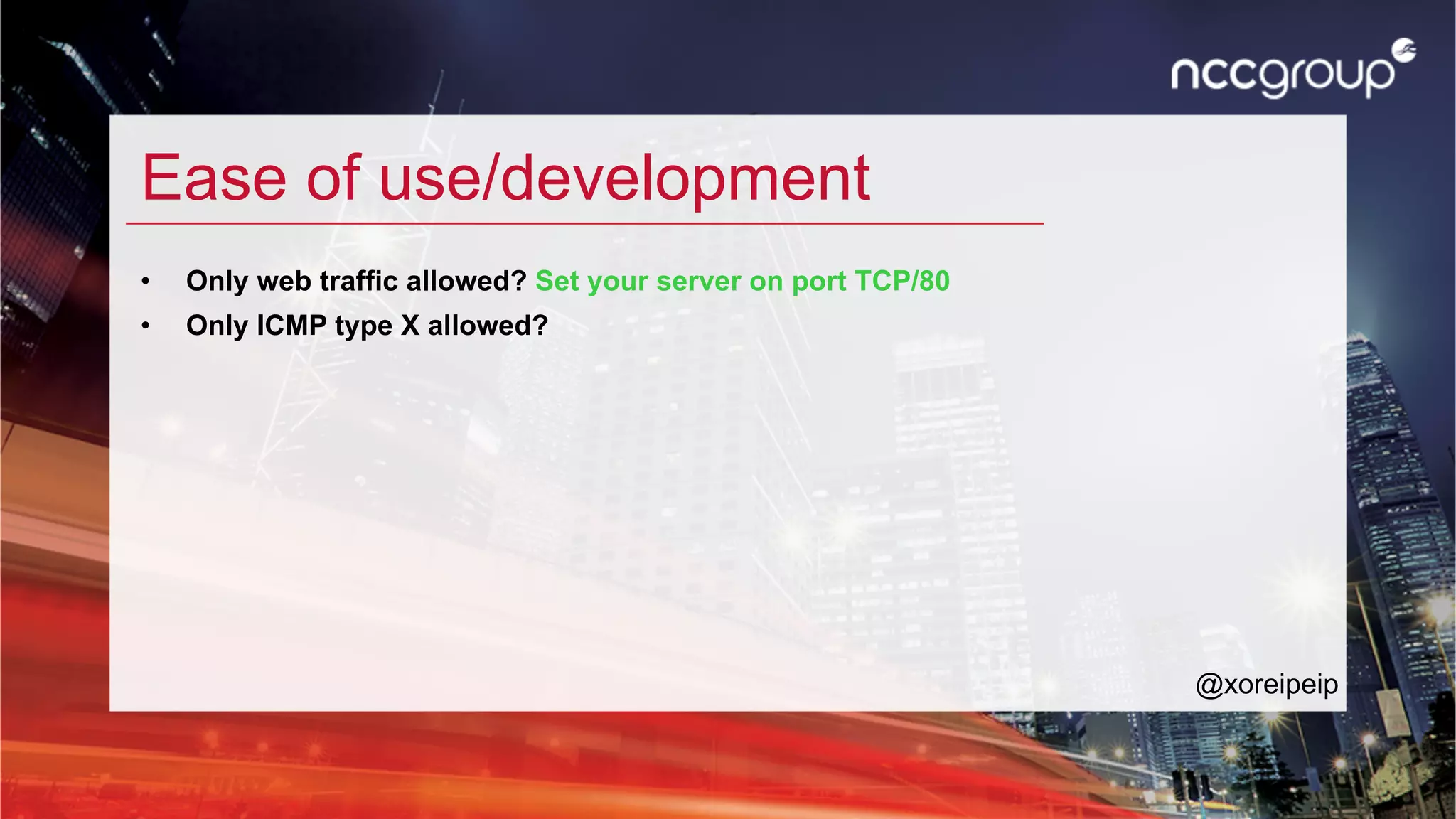
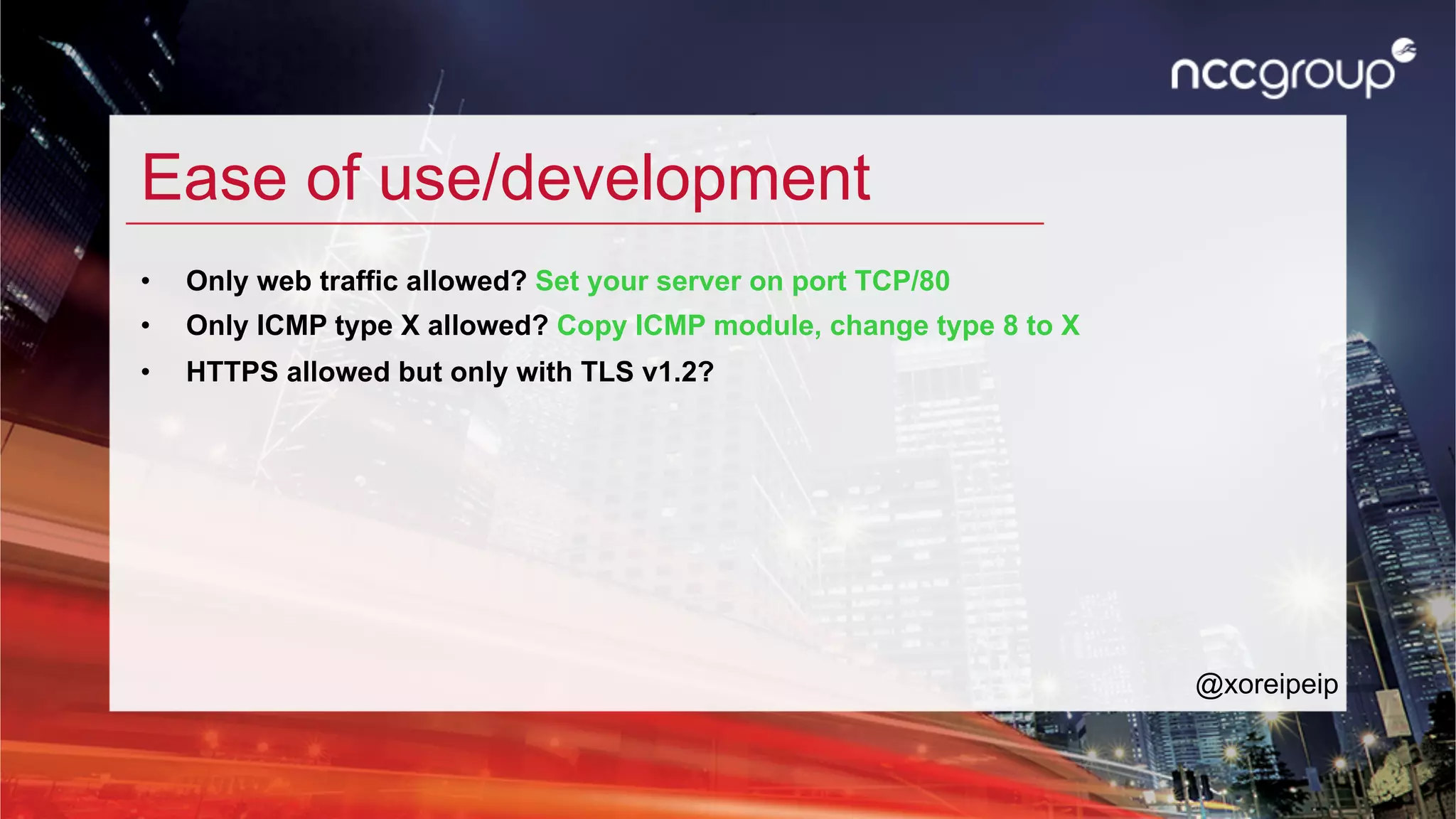
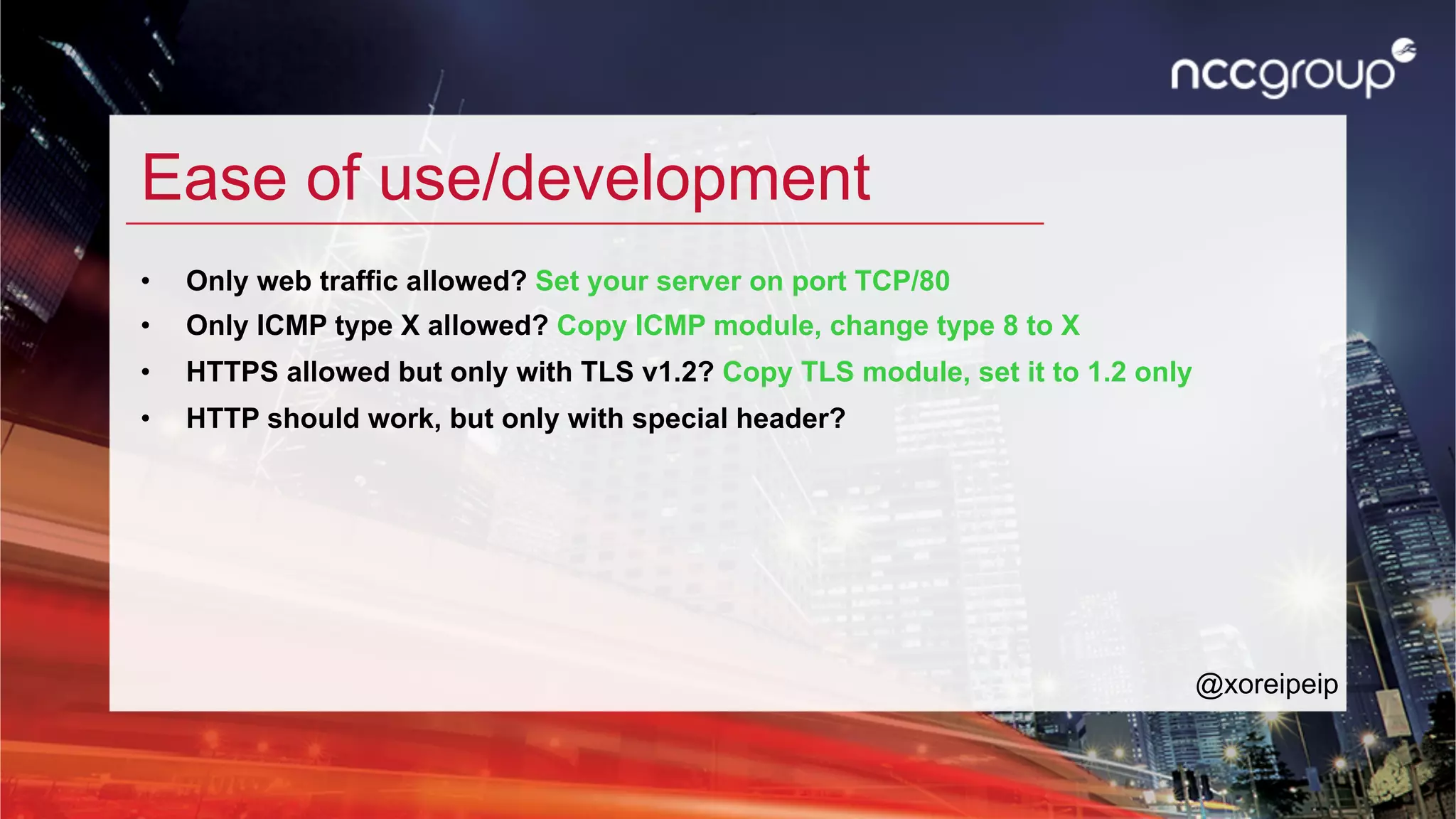
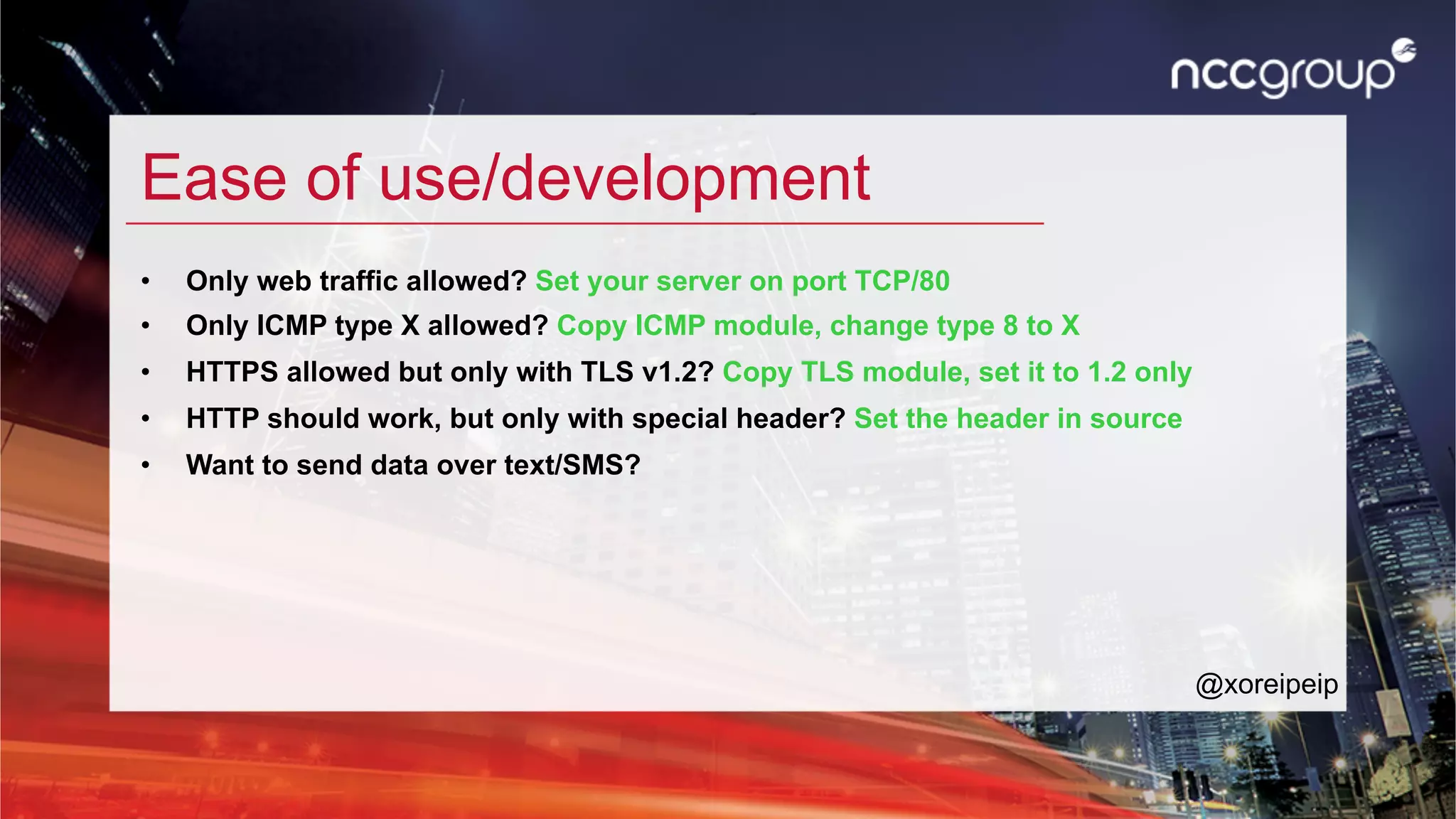
The document discusses 'xfltreat', an open-source tunnelling framework created by Balazs Bucsay, aimed at simplifying the tunnelling process with a modular and user-friendly design. It addresses the need for confidentiality in various online activities while providing examples of its application and configuration. The document also outlines potential security measures for companies to enhance their networks against tunnelling threats.