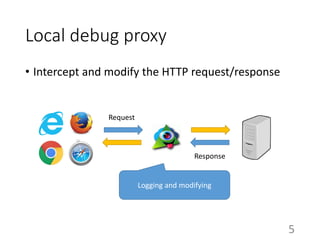
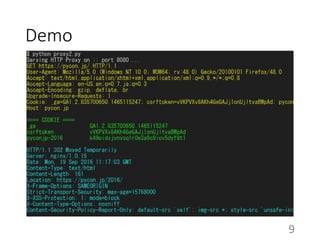
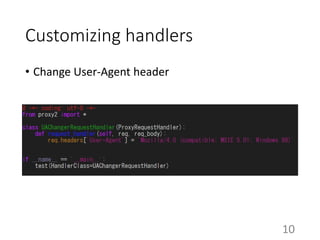
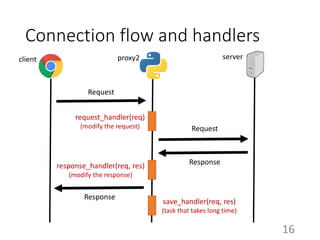
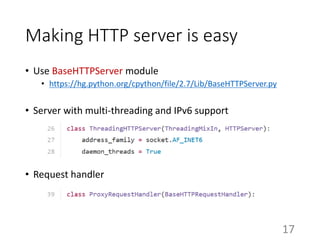
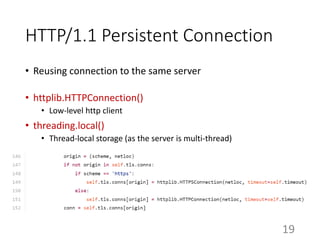
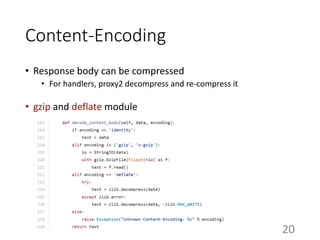
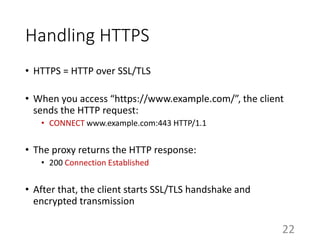
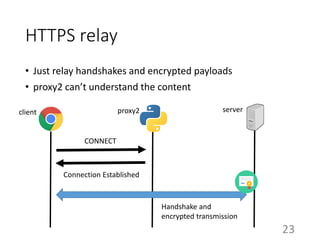
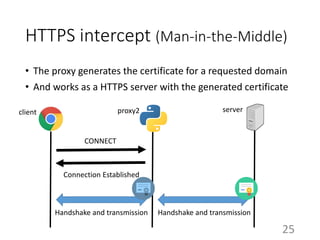
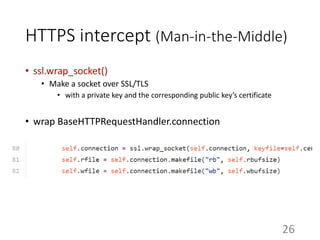
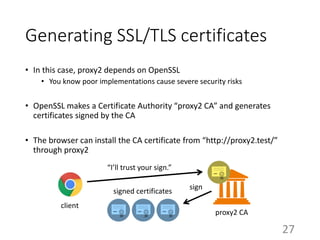
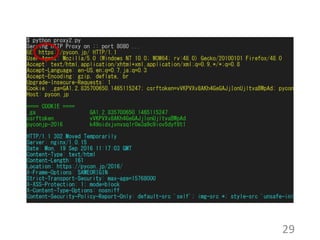
This document summarizes the design and implementation of proxy2, an HTTP proxy library written in Python. Proxy2 aims to be a simple yet fully customizable proxy. It uses standard Python modules and implements request, response, and save handlers that can be overridden by users to modify requests, responses, or perform long tasks. The document covers challenges like HTTP persistent connections, content encoding, and hop-by-hop headers that proxy2 addresses. It also explains how proxy2 supports HTTPS relay and interception using SSL/TLS.