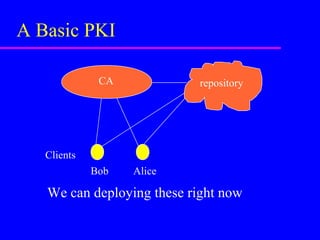
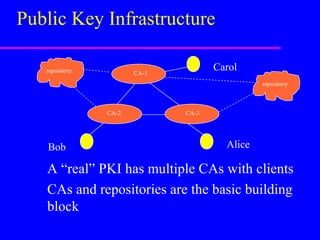
This document provides an overview of public key infrastructure (PKI). It discusses how PKI uses public key cryptography and digital certificates to securely distribute public keys. A PKI relies on certificate authorities (CAs) to issue and revoke certificates binding public keys to their owners. It also discusses the roles of CAs, registration authorities, repositories, and clients in a PKI. The document outlines how standards bodies are working to develop PKI standards and the need for testing interoperability between PKI components. It notes that while PKI can support some applications today, a global public key infrastructure is not yet achievable and full interoperability has not been established.









![Transaction Formats and
Protocols
Three major specifications
– Certificate Request Message Format, or CRMF
(RFC 2511)
– Certificate Management Protocol, or CMP
(RFC 2510) [references 2511]
– Certificate Management Messages over CMS,
or CMC (I-D) [references 2511]
Is there room for CMP and CMC?](https://image.slidesharecdn.com/polk-140303204910-phpapp02/85/PKI-by-Tim-Polk-12-320.jpg)




















