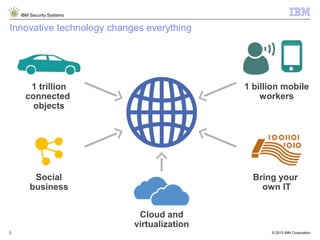
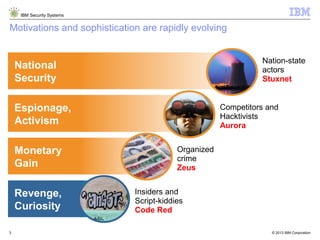
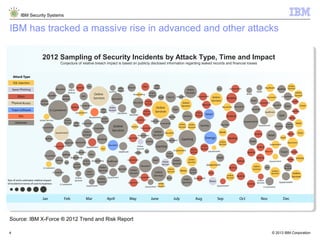
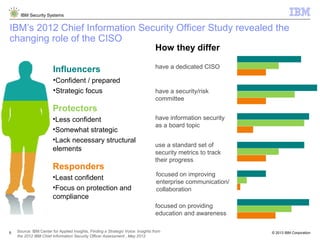
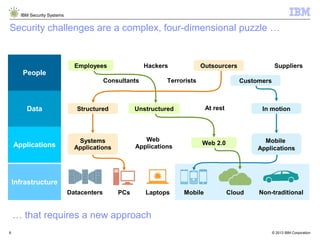
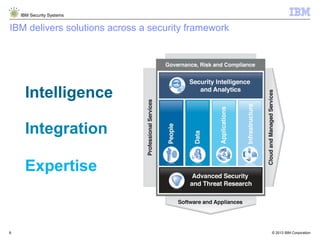
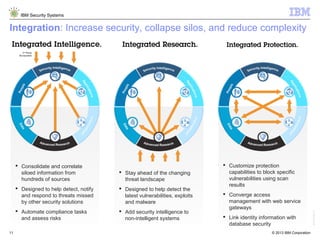
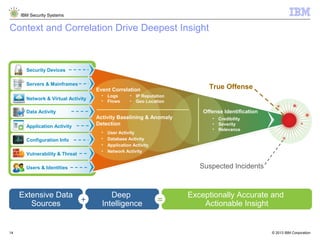
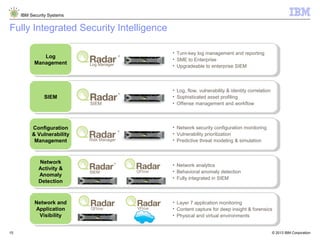
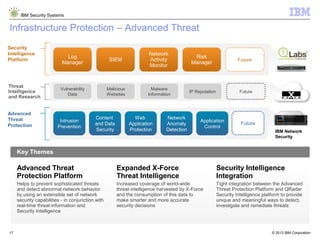
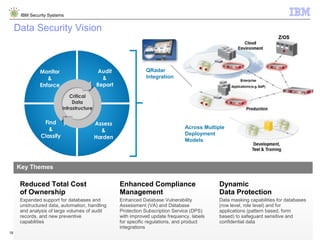
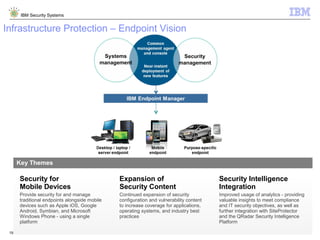
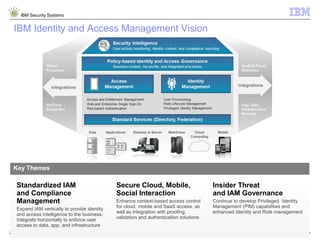
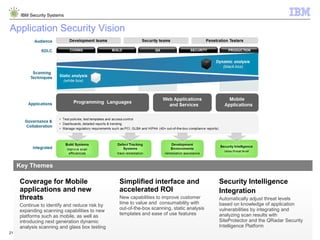
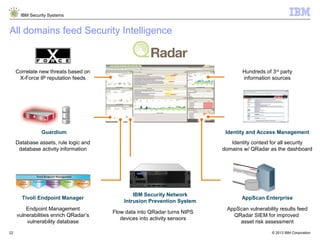
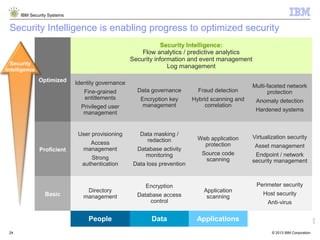
The document outlines IBM's approach to security in the rapidly evolving technological landscape, emphasizing the rise in sophisticated cyber threats and the need for advanced security strategies. It discusses IBM's comprehensive security solutions, including intelligence, integration, and expertise to address diverse security challenges across various domains. The document also highlights key themes such as mobile security, compliance management, and the importance of collaboration in threat detection and management.