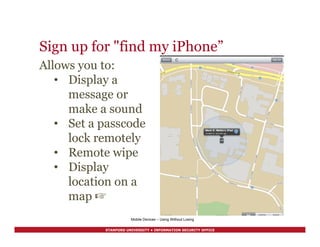
Mark K. Mellis of Stanford University's Information Security Office gave a briefing on securing mobile devices. He discussed risks of loss, theft, or spying of mobile devices and tips for using passcodes, updating software, backups, and encryption. If a device is lost or stolen, he recommends immediately changing network passwords and potentially wiping the device remotely if it is enrolled in Stanford's Mobile Device Management program.


















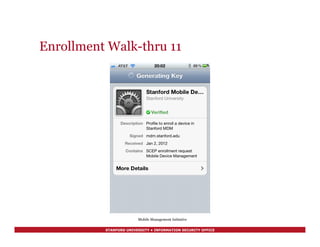
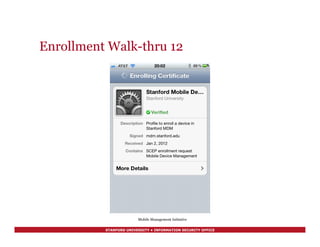
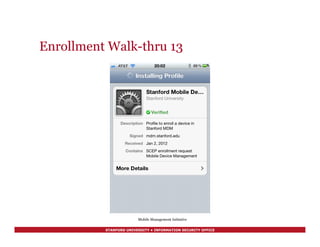
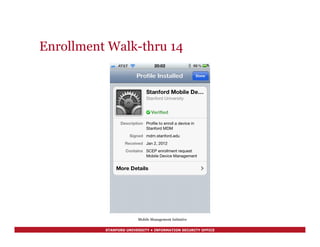










![STANFORD UNIVERSITY • INFORMATION SECURITY OFFICE
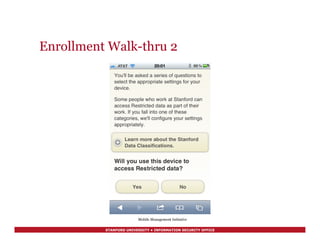
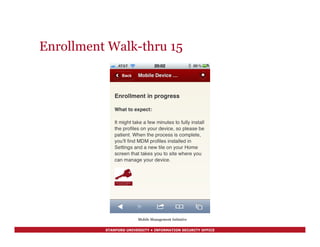
Support Management Interface 2
$ remctl mdm1 mdm show-device fde2f92601f64fb48fb7847cf9599f58ec85ff8c
Device 1 of 1:
DB id: 3158
UDID: fde2f92601f64fb48fb7847cf9599f58ec85ff8c
Device Name: Mark K. Mellis's iPhone
User Name: mkmellis
Model: iPhone 4S
Last Check-in: 2012-01-02 20:03:09
OS Version: iOS 5.0.1 (9A405)
Cert Expires: 2013-01-01 20:02:18
WiFi Mac Address: 3c:d0:f8:4e:df:16
[continued]
Mobile Management Initiative](https://image.slidesharecdn.com/mobiledevicesecuritytechbriefing20120330-140725180937-phpapp01/85/Mobile-Devices-Using-Without-Losing-Mark-K-Mellis-Associate-Information-Security-Officer-47-320.jpg)
![STANFORD UNIVERSITY • INFORMATION SECURITY OFFICE
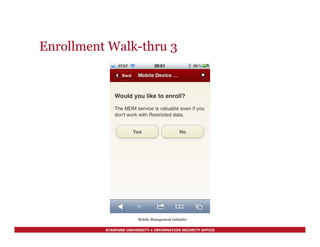
Support Management Interface 3
[continued]
Phone Number: +16504756859
Cellular Technology: GSM
Cellular NetworkId: 01 300400 333769 5
Sim Carrier: AT&T
Last Carrier:
Serial Number: C39GPJ9QDT9V
Carrier Settings Version: 11.0
Modem Firmware Version: 1.0.13
Capacity (GB): 13.58082199096700
Last Updated: 2012-01-02 20:02:42
Profiles Installed:
MDM Regular [v20110815-9]
ActiveSync [v20110815-13]
Cisco VPN [v20110815-15]
$
Mobile Management Initiative](https://image.slidesharecdn.com/mobiledevicesecuritytechbriefing20120330-140725180937-phpapp01/85/Mobile-Devices-Using-Without-Losing-Mark-K-Mellis-Associate-Information-Security-Officer-48-320.jpg)
![STANFORD UNIVERSITY • INFORMATION SECURITY OFFICE
Support Management Interface 3
$ remctl mdm1 mdm show-apps fde2f92601f64fb48fb7847cf9599f58ec85ff8c
Applications Installed:
AirPort(100.14)
BayAreaNews(1.02)
BodyMedia(2413)
Calc 16C(1.1.0)
[…]
Yelp(5.5.1)
Z-Subsonic(2.8)
$
Mobile Management Initiative](https://image.slidesharecdn.com/mobiledevicesecuritytechbriefing20120330-140725180937-phpapp01/85/Mobile-Devices-Using-Without-Losing-Mark-K-Mellis-Associate-Information-Security-Officer-49-320.jpg)