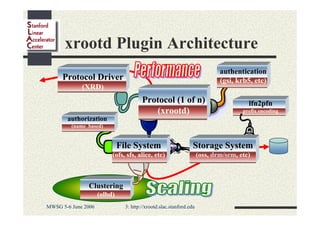
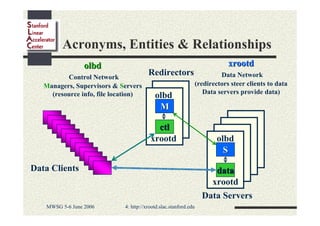
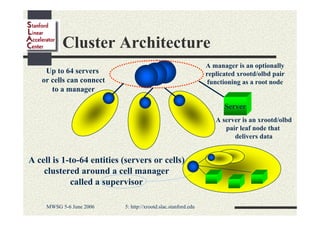
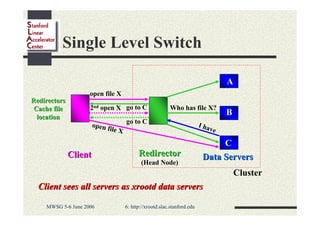
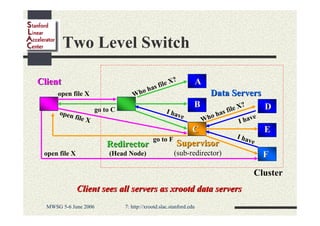
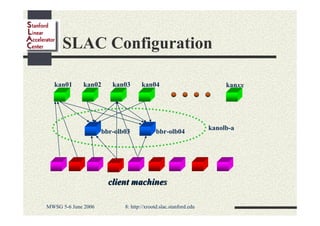
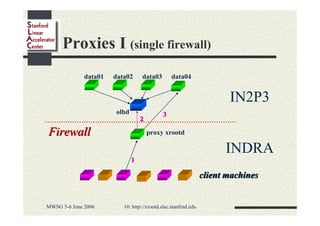
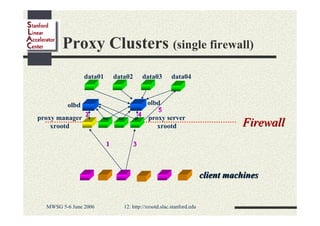
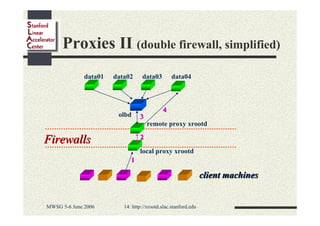
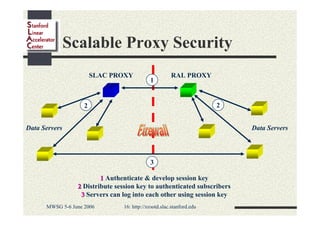
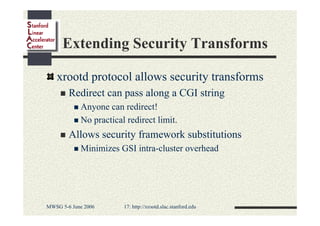
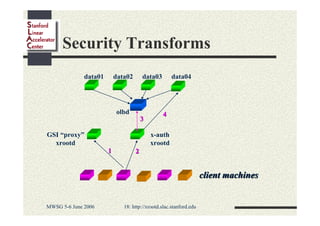
Andrew Hanushevsky gave a presentation on using xrootd proxies to provide scalable and secure remote access to data. Proxies allow clients outside a firewall to access data servers behind the firewall. Proxy clusters provide load balancing and redundancy. Authentication between proxies and servers can be handled through a security transformation that establishes a shared session key. This simplifies key management in large clustered systems and allows access across multiple firewalls. xrootd was designed with security in mind through features like support for security transforms and easy administration of clustered proxies.