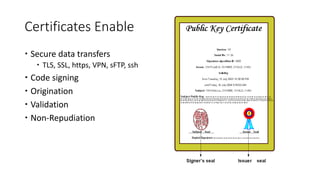
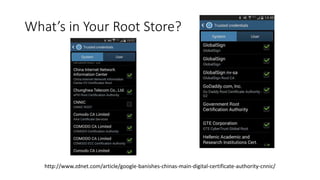
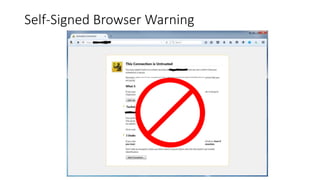
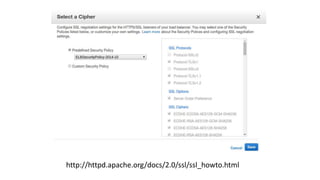
This document discusses public key infrastructure (PKI) and digital certificates. It covers how certificates enable authentication, confidentiality, integrity and non-repudiation. It also discusses certificate authorities, self-signed certificates, common uses of certificates including TLS and code signing, and risks associated with certificates like compromised certificate authorities and vulnerable algorithms. The document provides recommendations around treating certificates as assets, establishing policies, being aware of issues for embedded systems, and monitoring for malware that targets certificates.