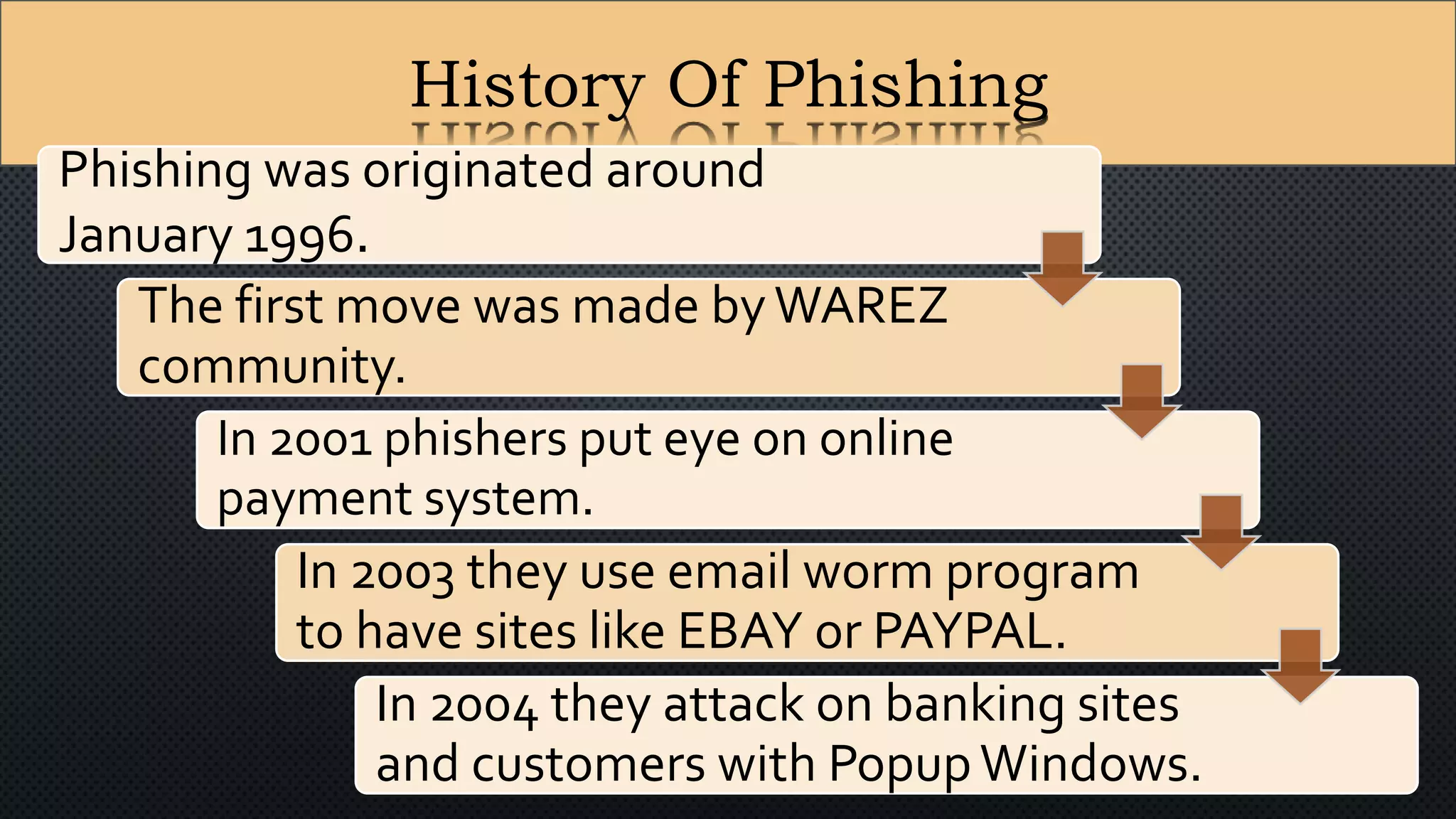
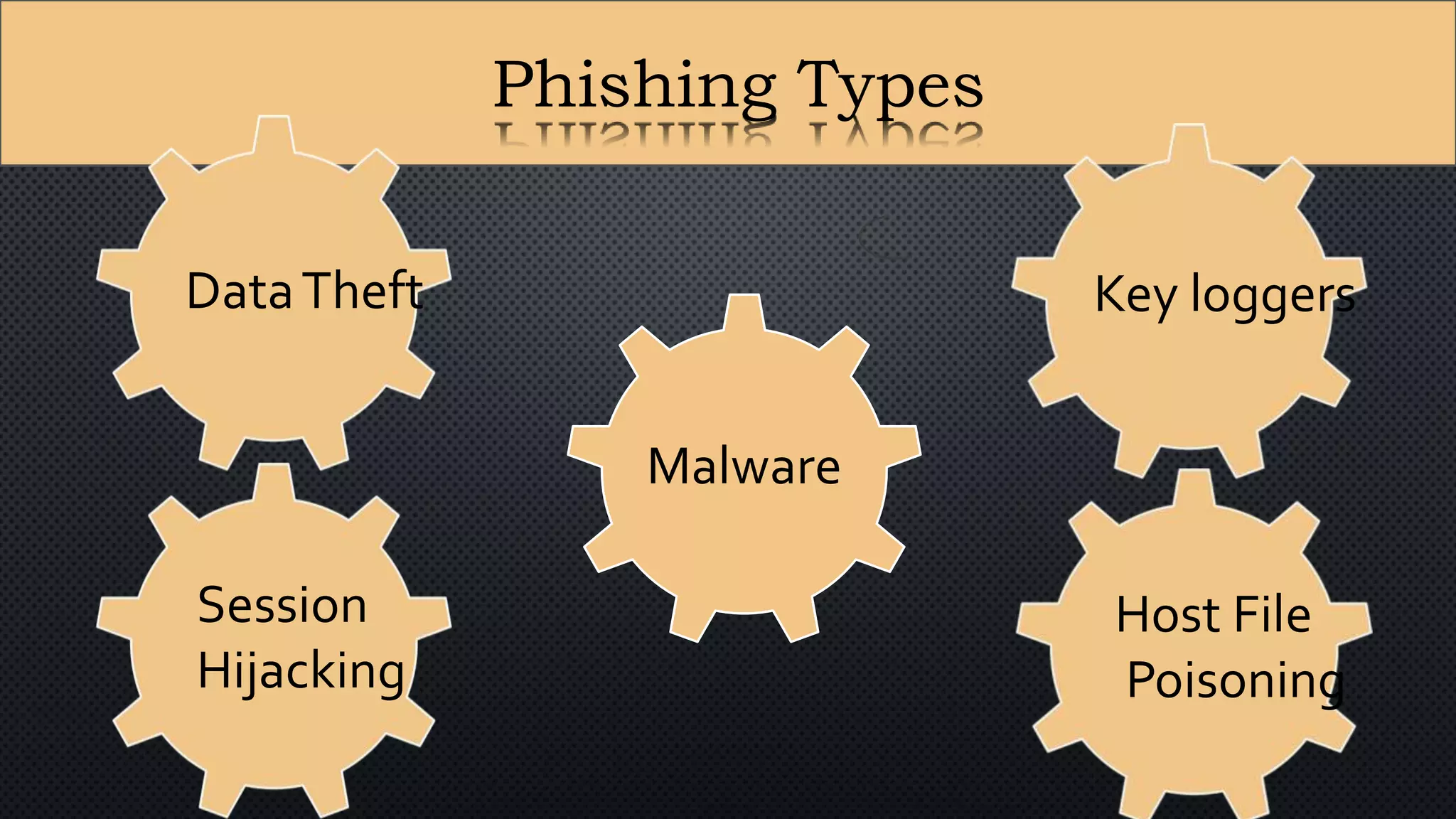
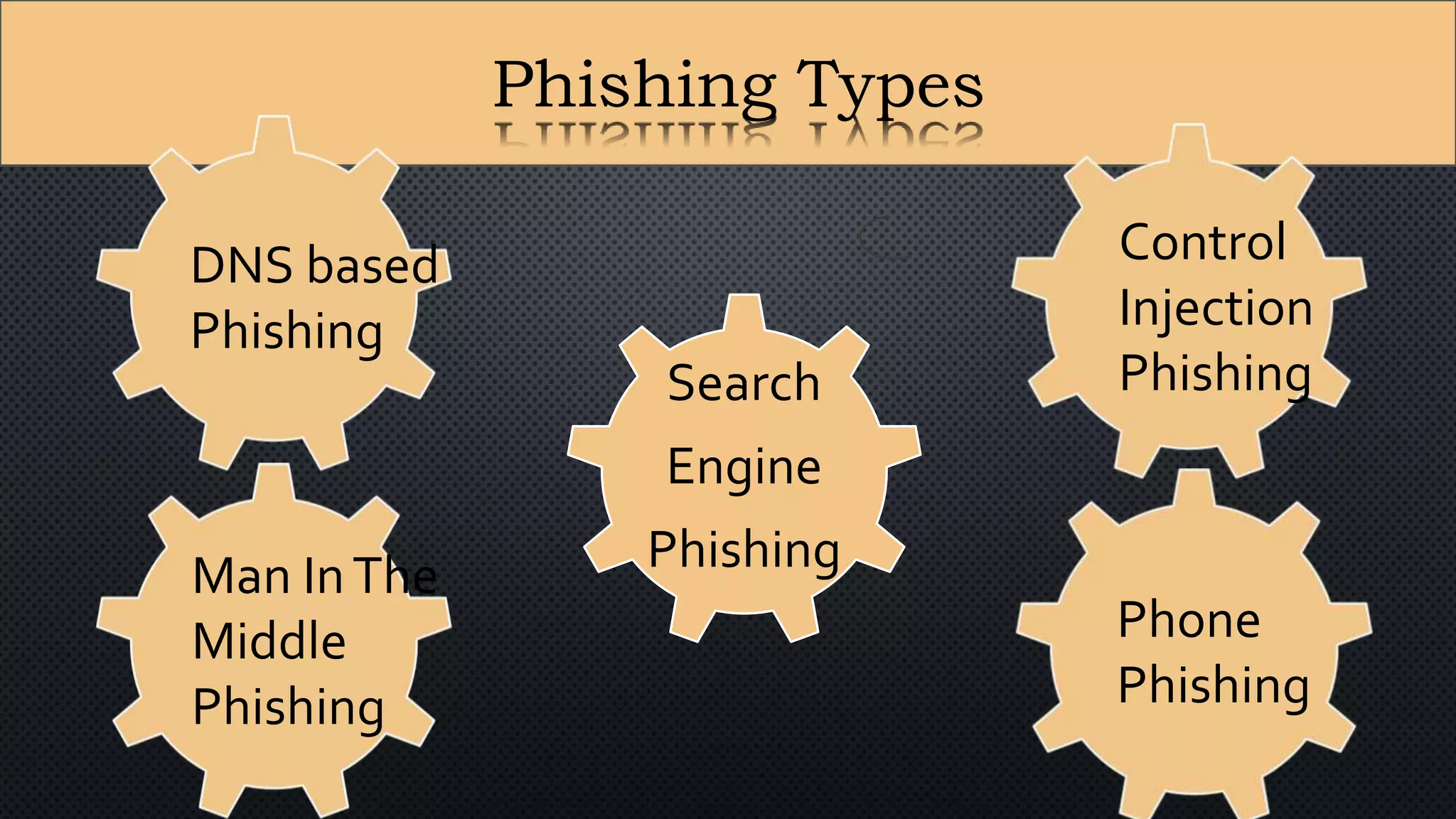
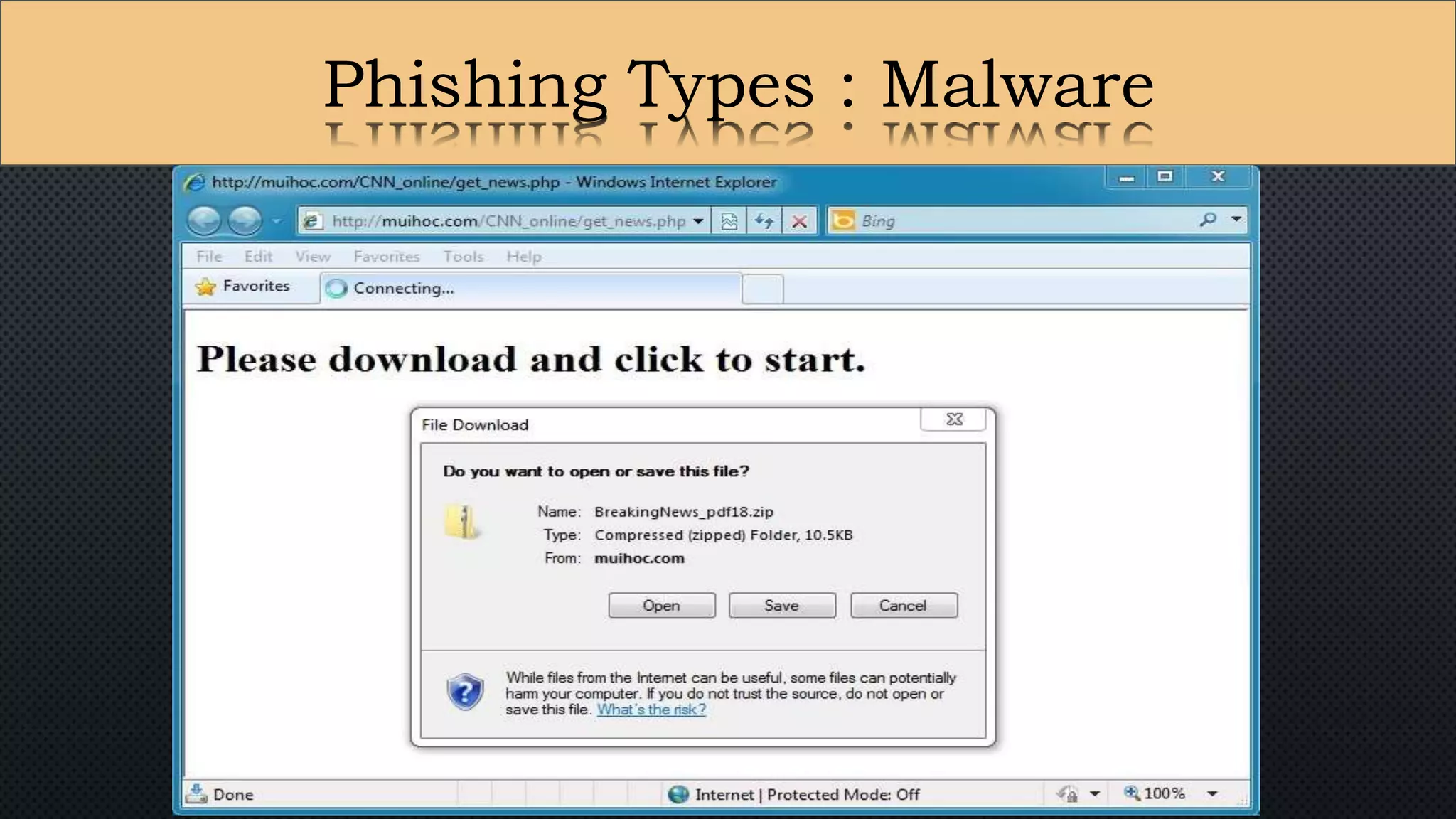
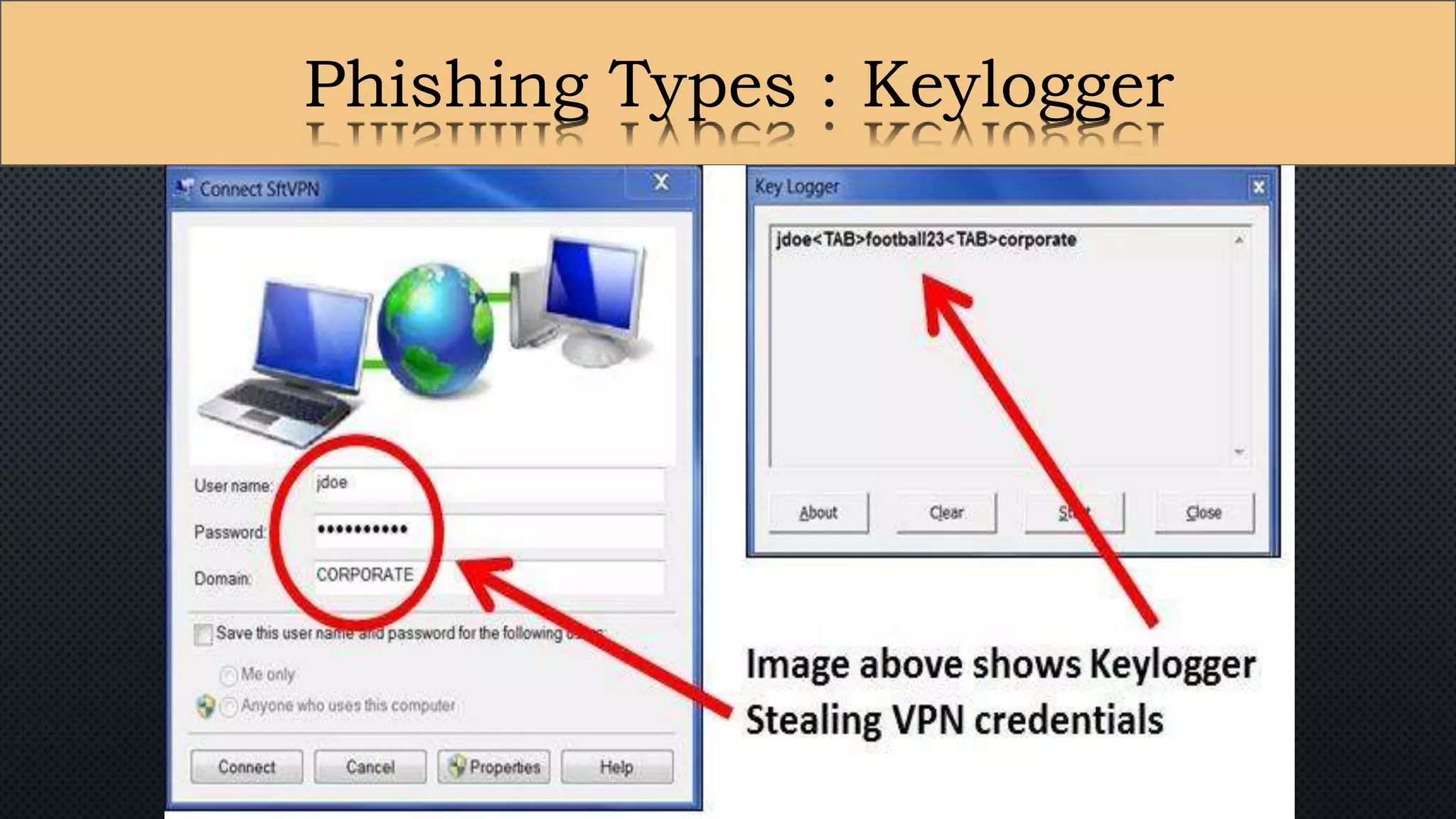
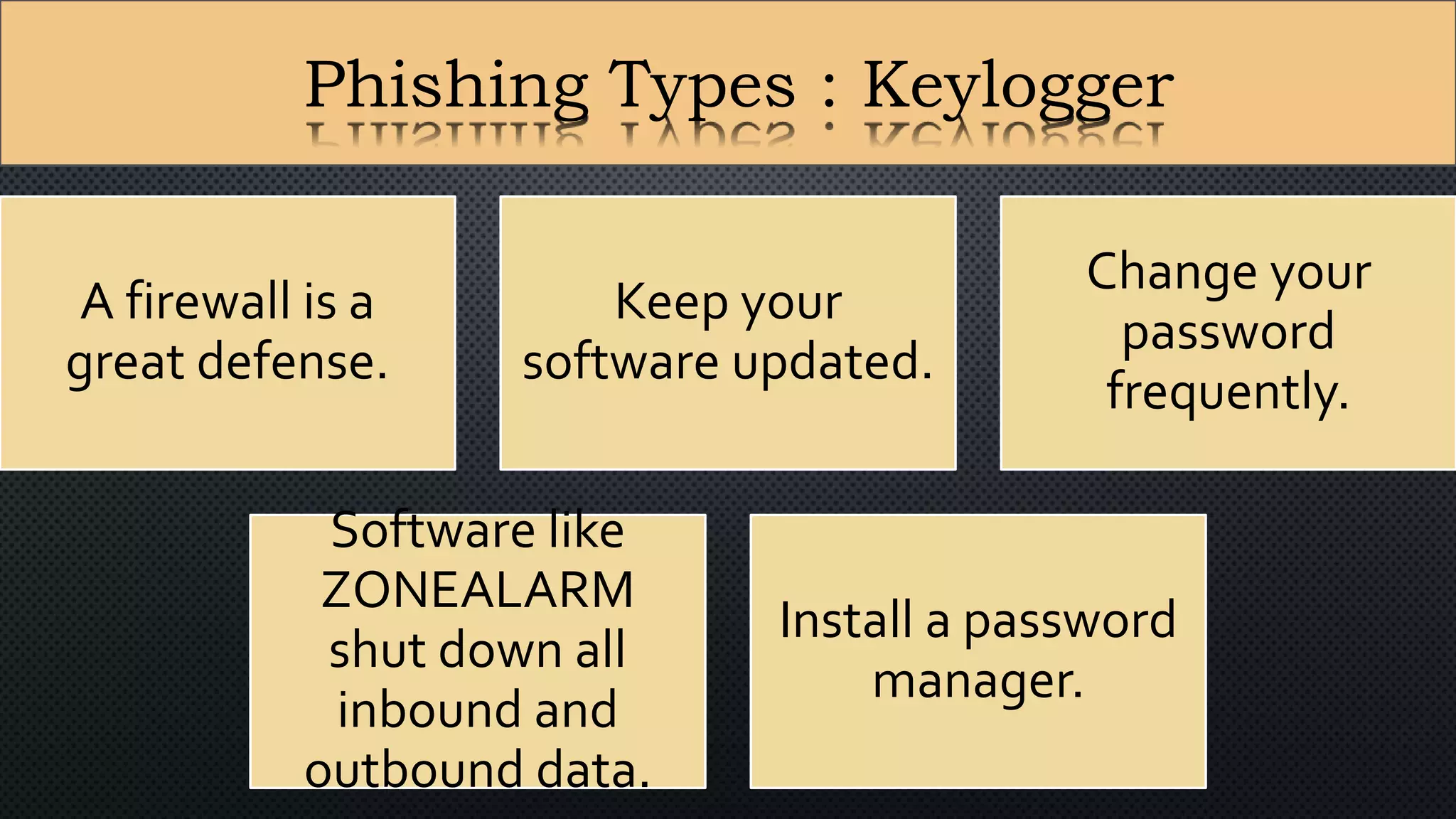
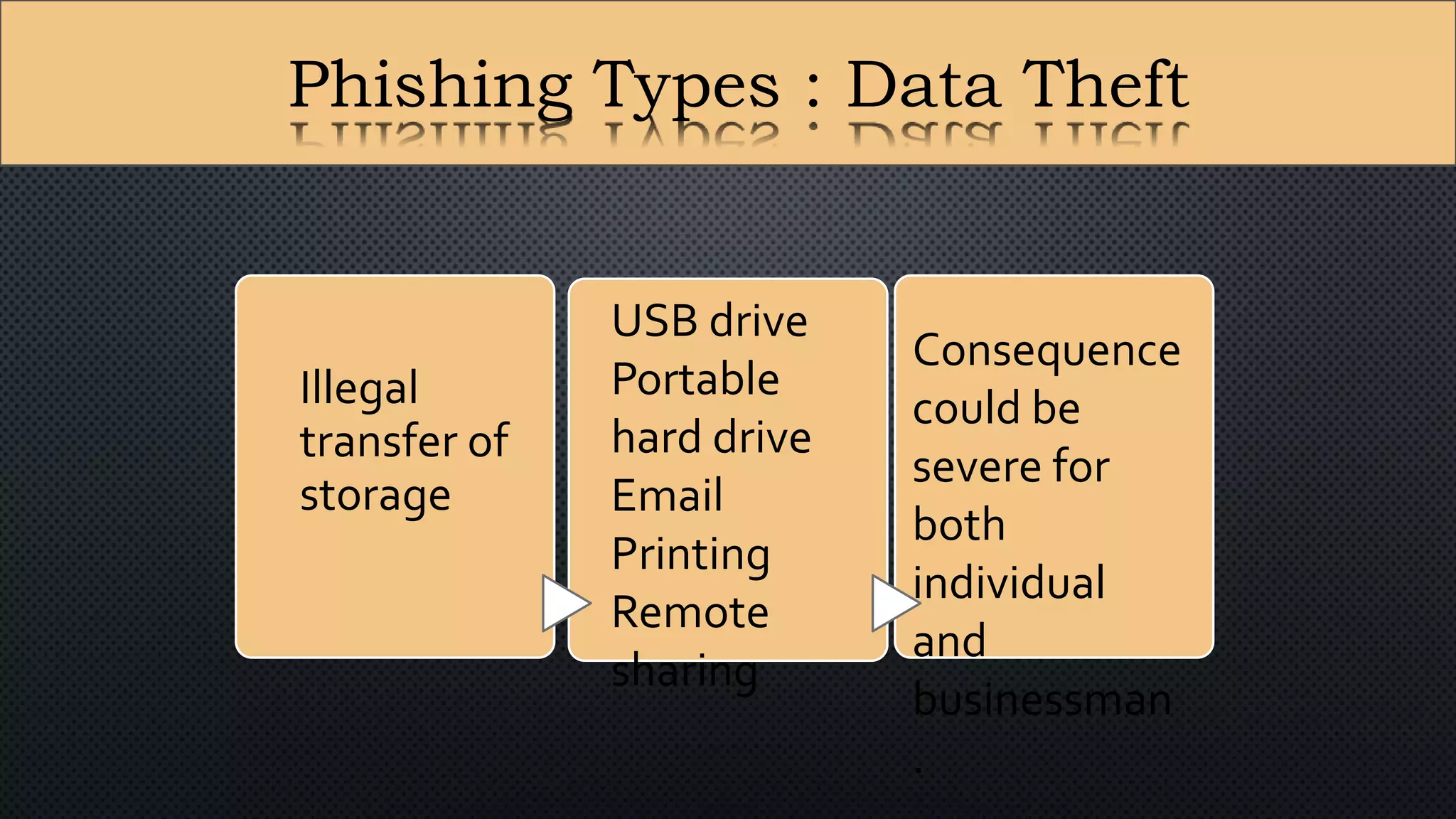
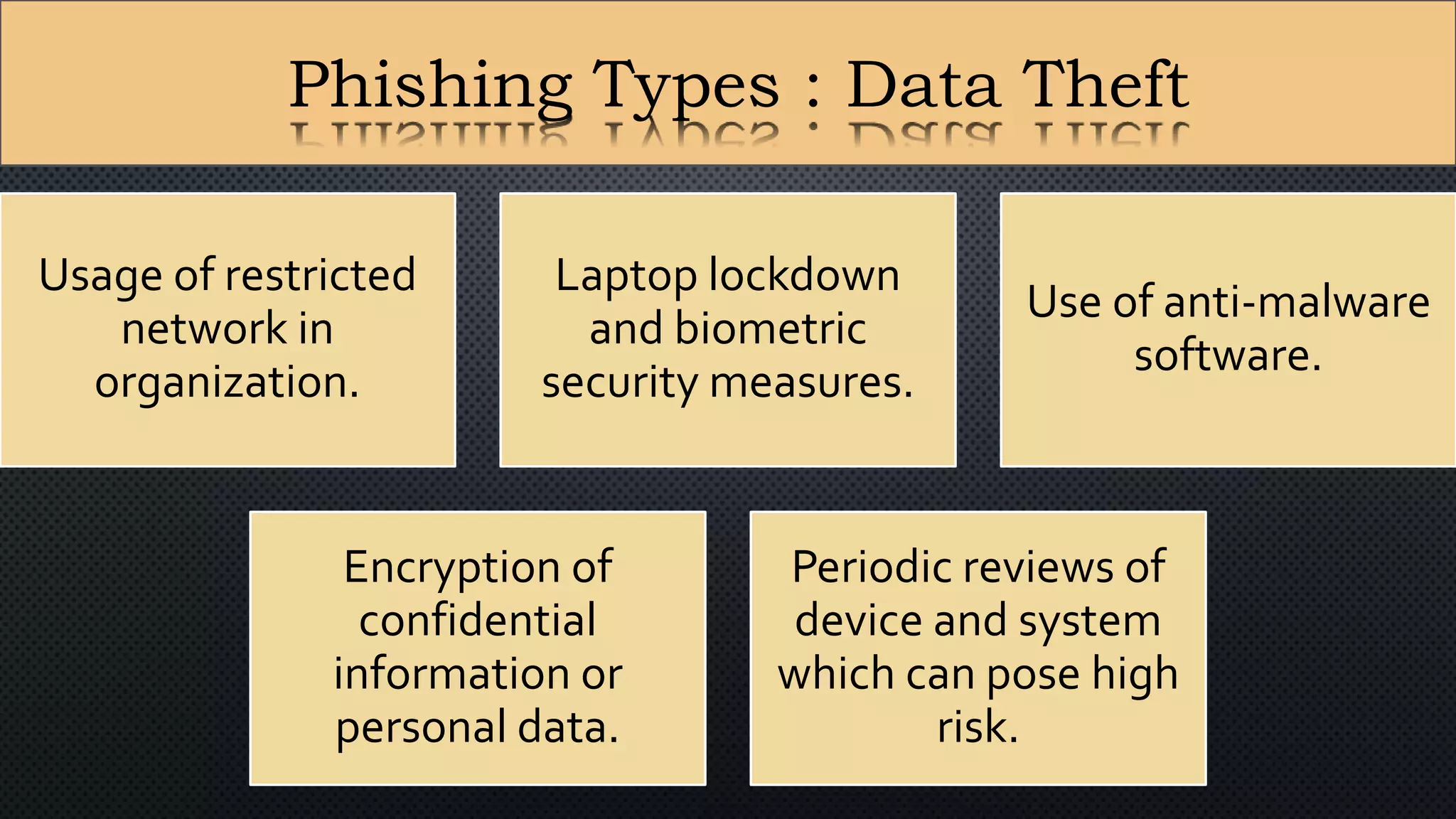
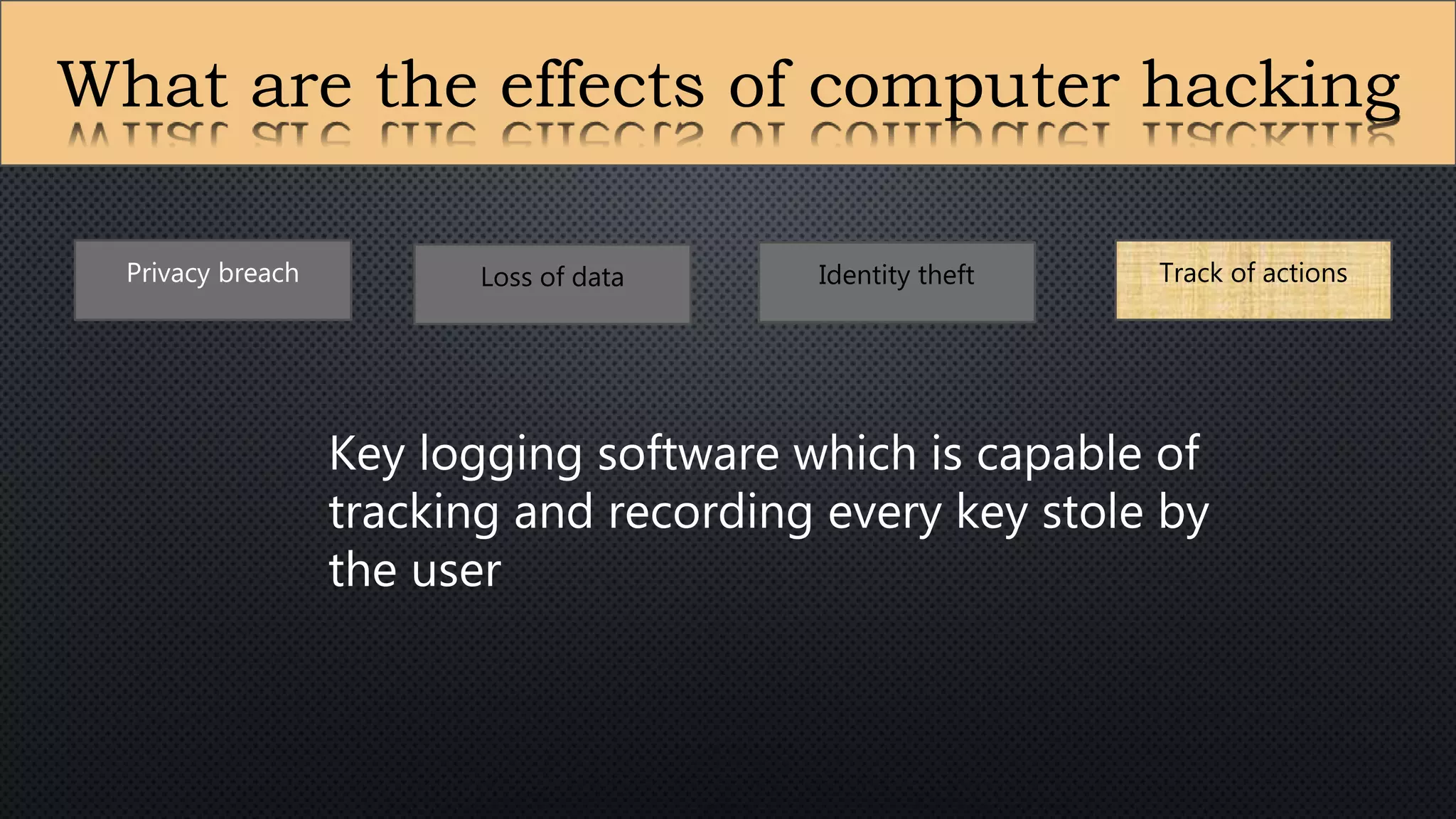
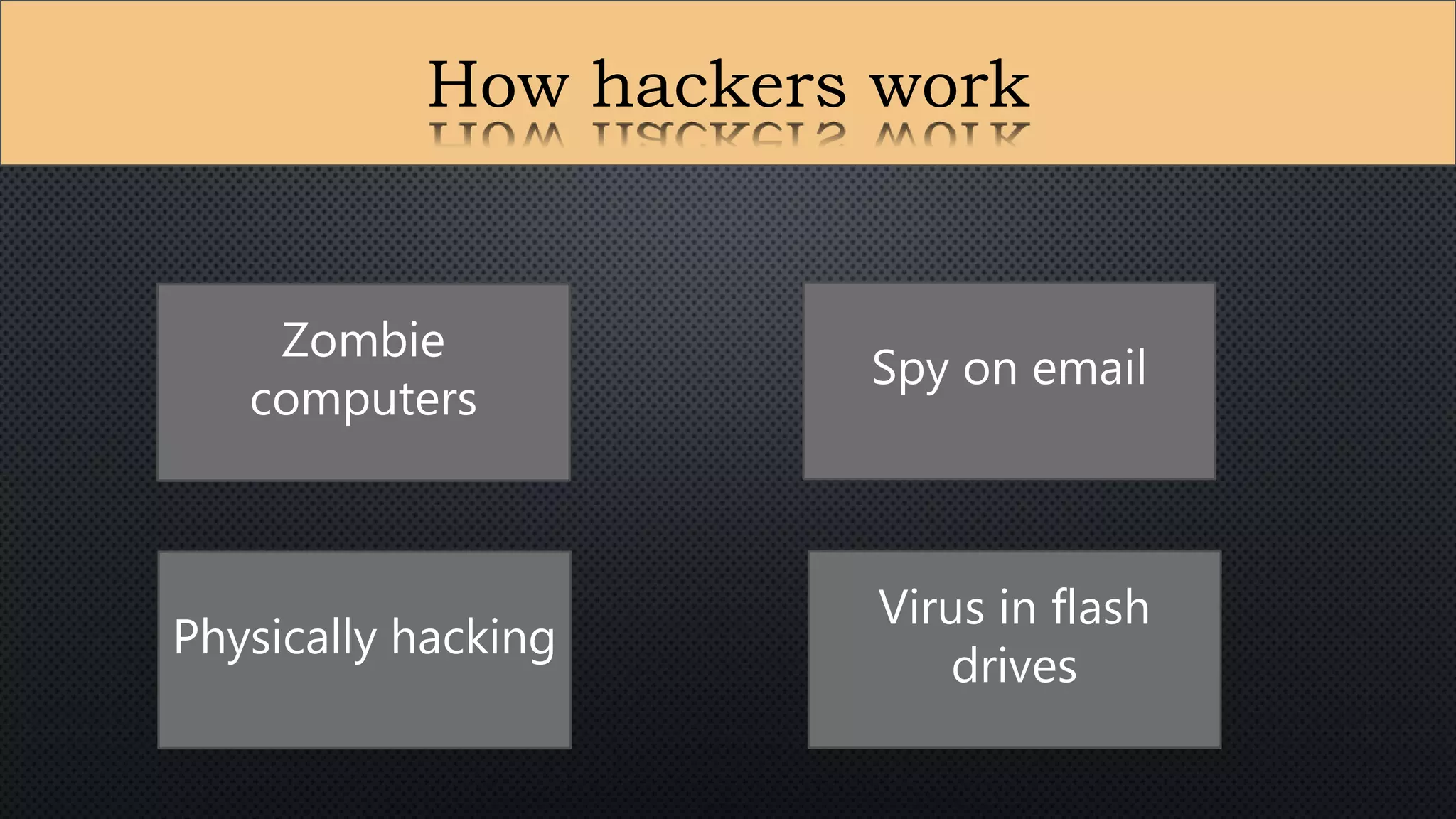
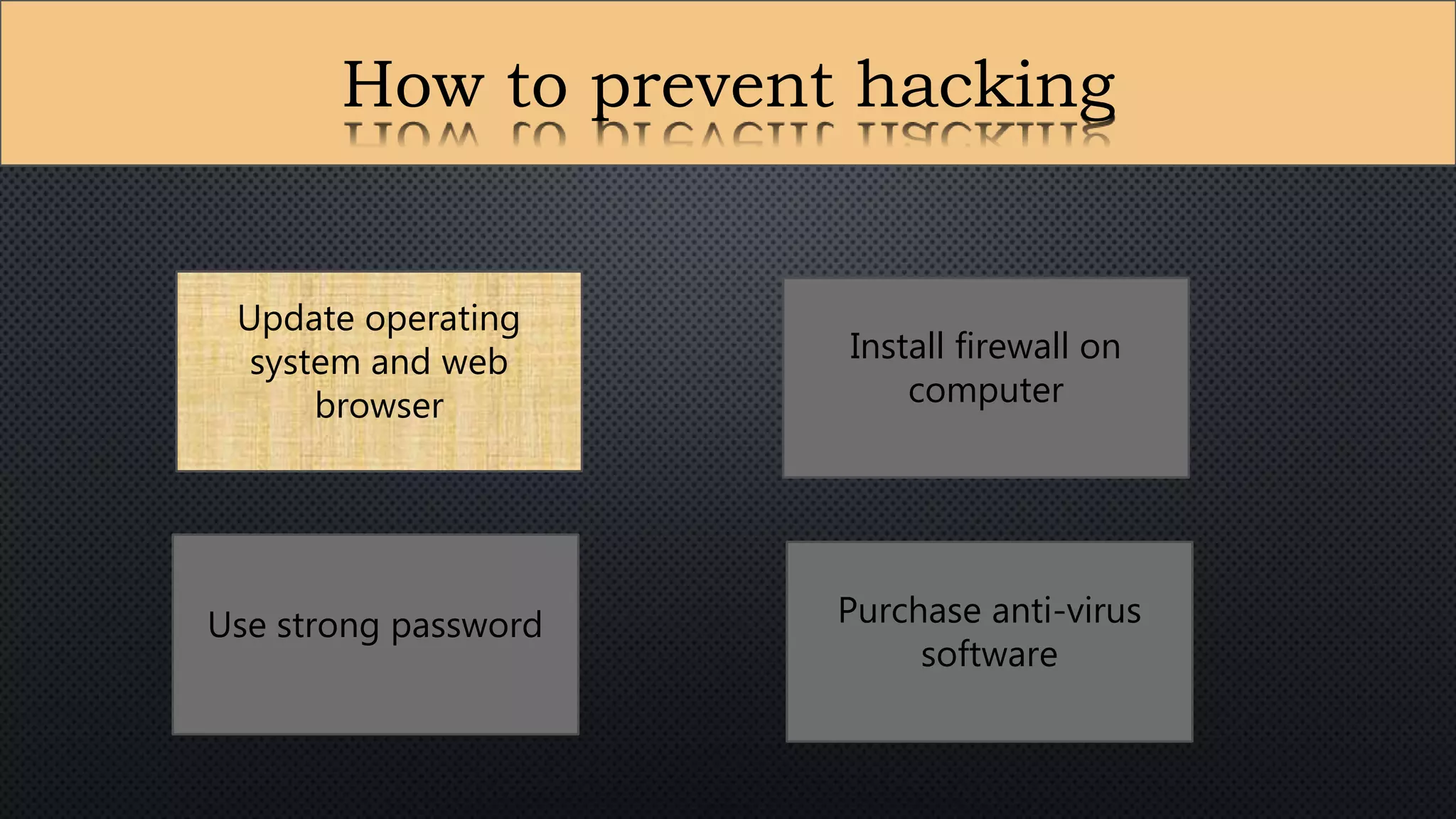
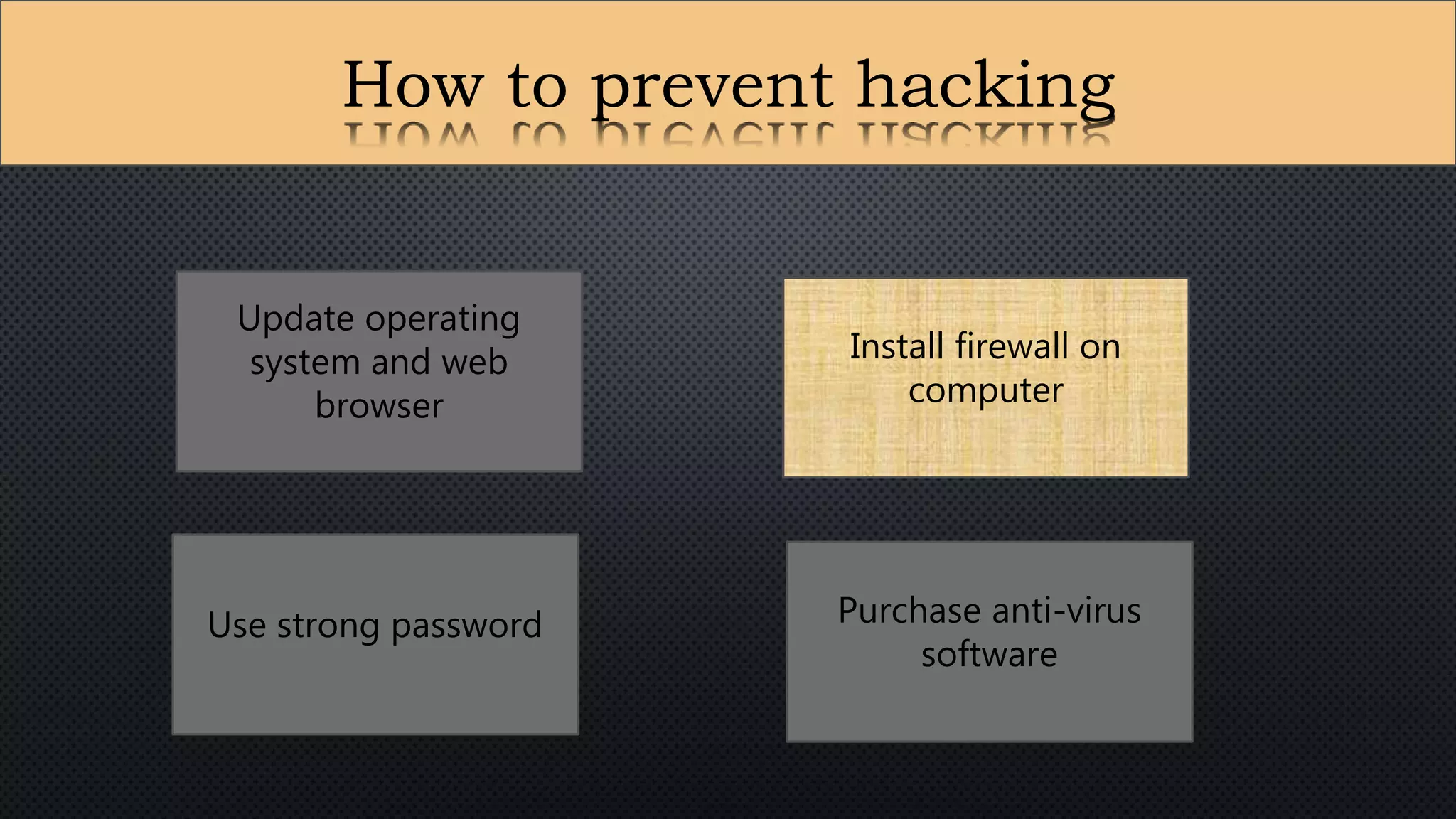
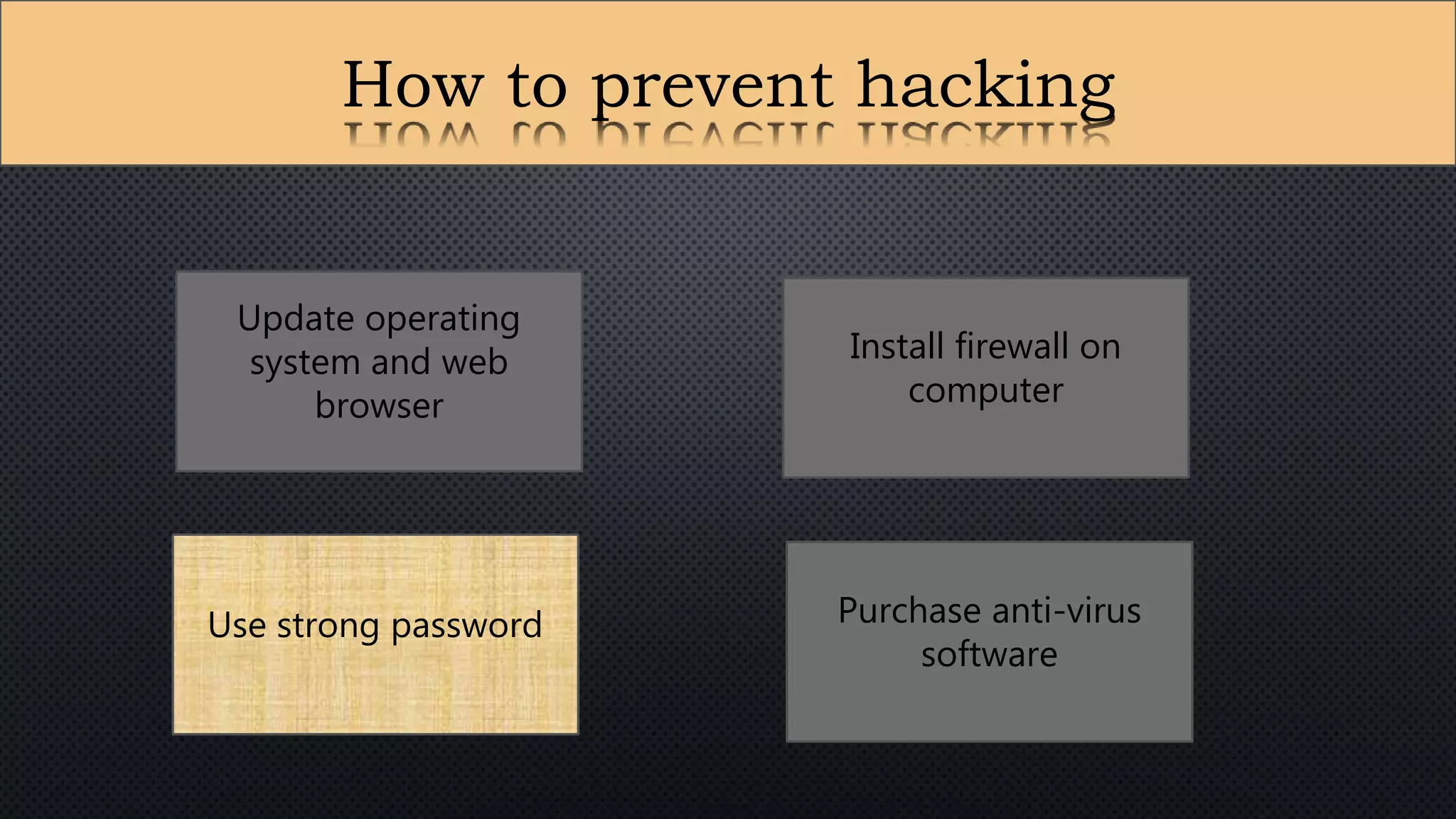
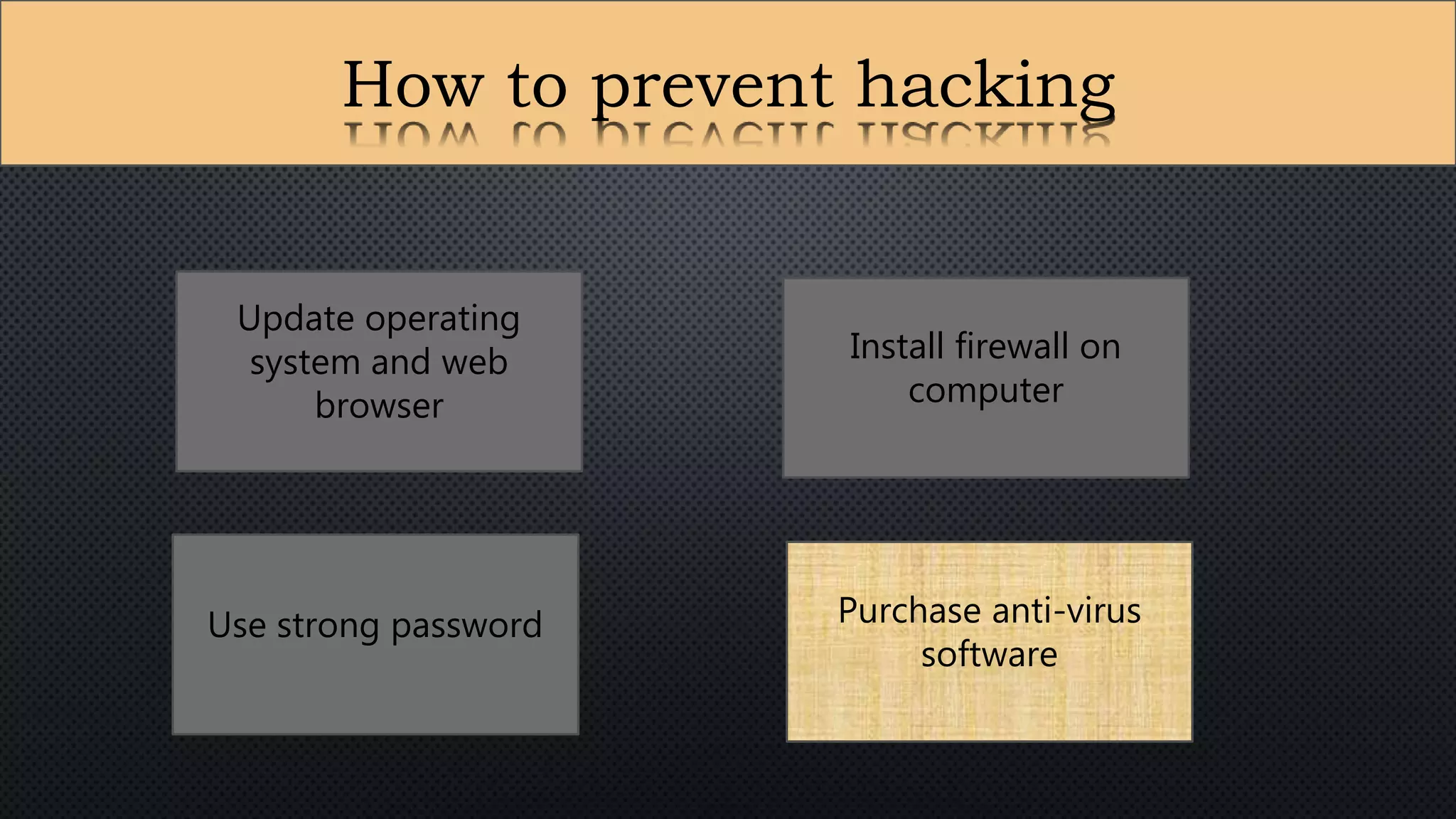
The document presents a group presentation on phishing and hacking, detailing the history, types, and effects of these cyber threats. Key points include various phishing methods such as keyloggers, malware, and man-in-the-middle attacks, alongside preventive measures like using antivirus software and implementing strong passwords. It also discusses the distinction between hackers and crackers, highlighting both positive and negative impacts of hacking on data security and privacy.