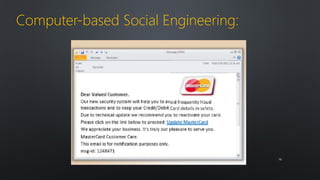
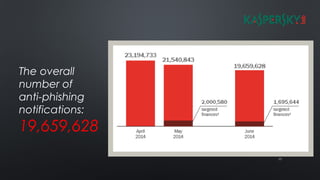
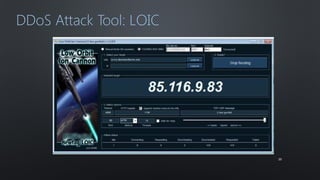
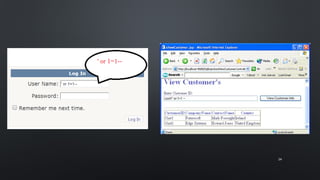
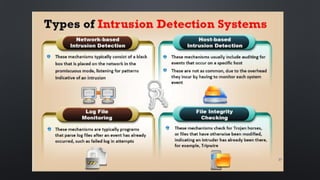
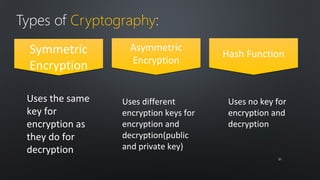
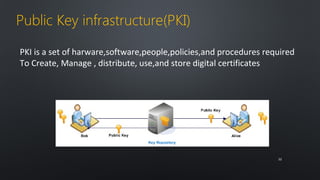
The document discusses various cybersecurity threats facing internet banking, including a significant rise in stolen credit card information, password thefts, and malware infections. It describes common hacking techniques like password cracking, denial of service attacks, botnets, and social engineering. The document also outlines defenses such as intrusion detection systems, firewalls, honeypots, encryption, and a public key infrastructure to help secure systems from cyber attacks.