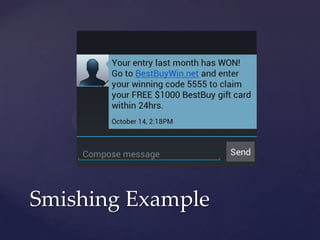
The document provides tips for email security and awareness to protect against common email scams and dangers, emphasizing the importance of strong, unique passwords and recognizing phishing attempts. It outlines various scams including lottery, advanced fee, and money mule scams, and warns against responding to suspicious emails or attachments. Additional resources and practical advice for verifying email legitimacy and securing personal information are also included.