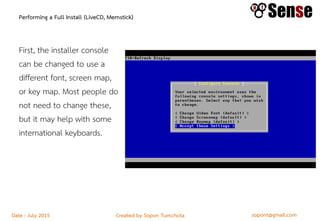
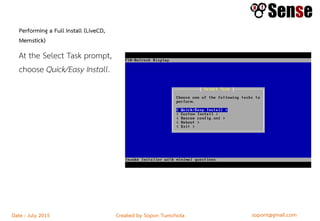
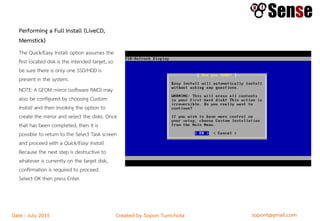
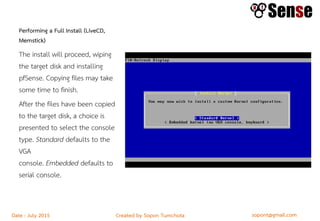
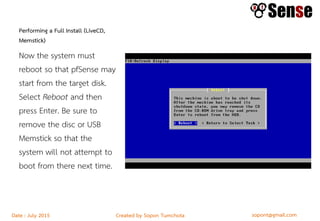
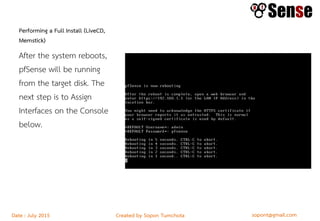
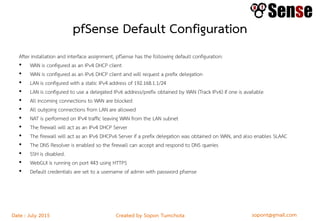
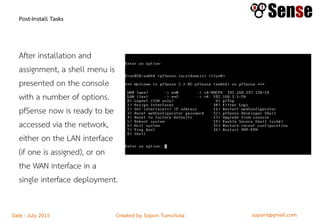
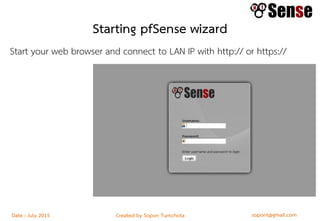
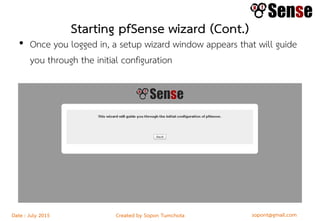
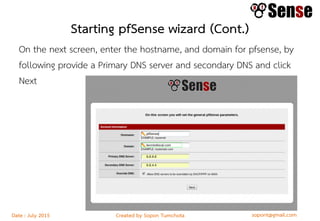
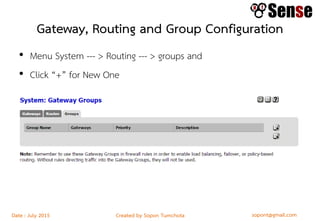
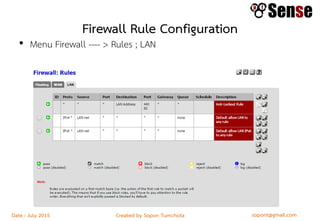
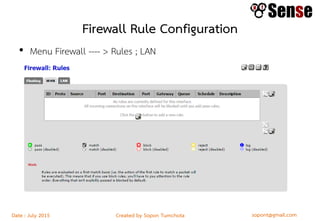
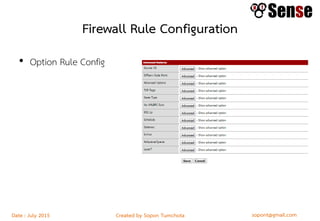
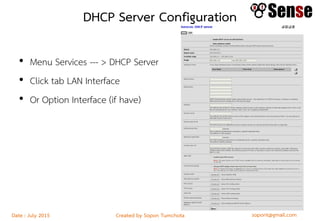
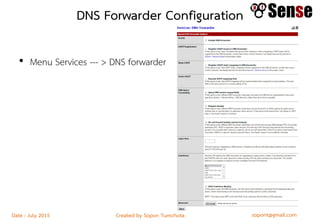
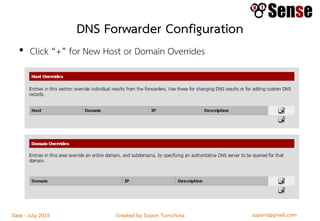
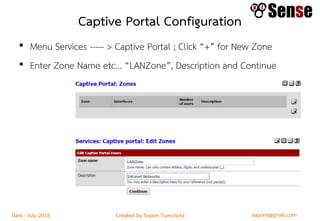
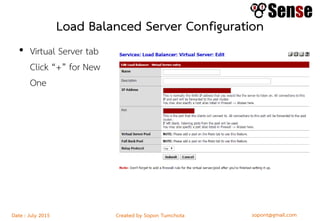
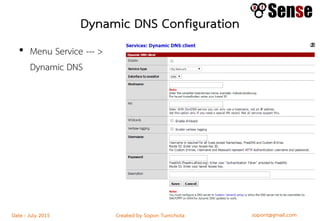
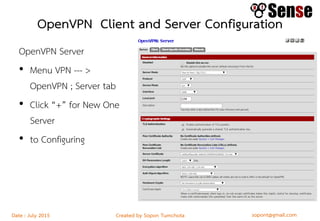
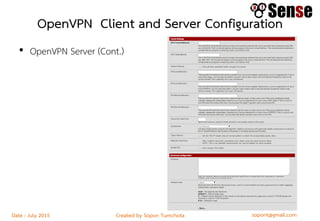
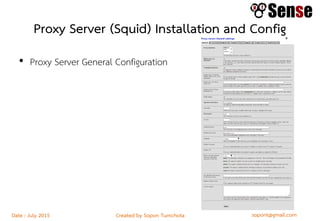
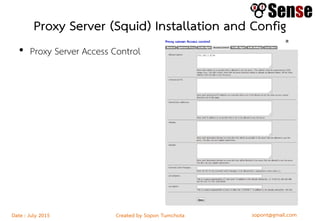
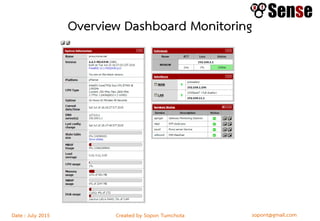
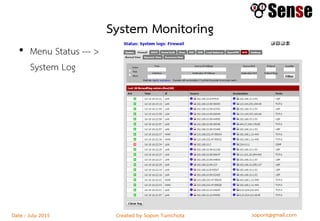
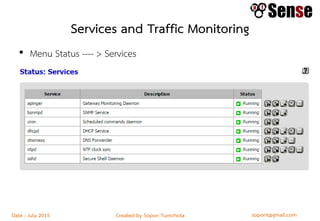
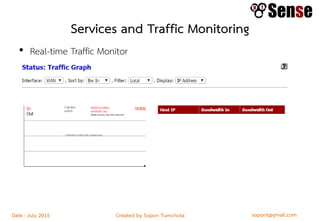
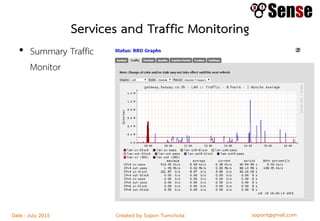
This document provides details about a firewall workshop guide, including:
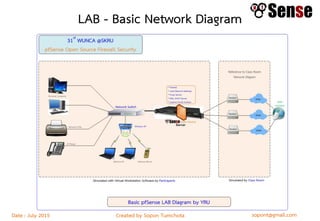
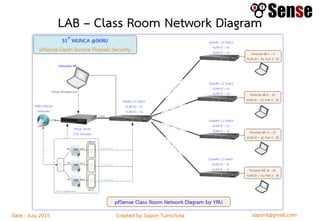
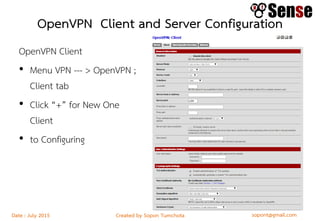
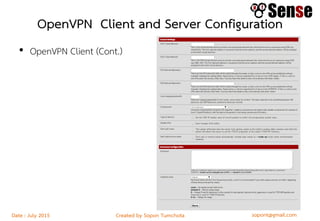
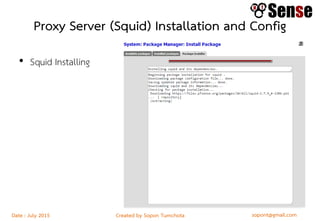
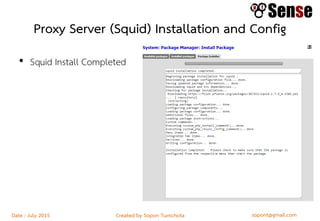
- An overview of topics to be covered such as basic routing and firewalls, pfSense installation and configuration, firewall rule configuration, and network monitoring.
- Requirements for workshop participants including computer hardware specs and recommended software.
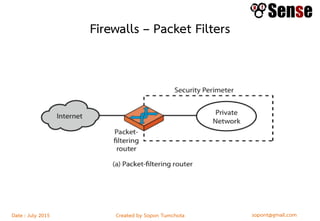
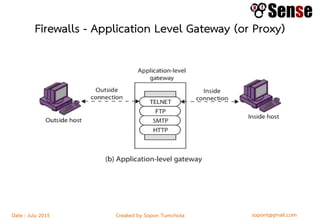
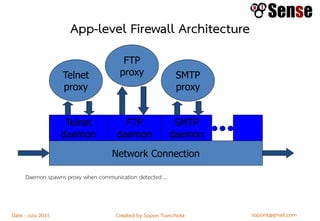
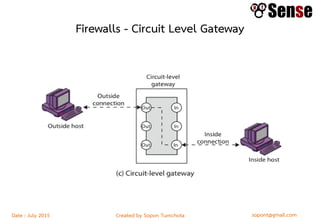
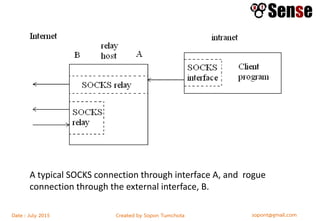
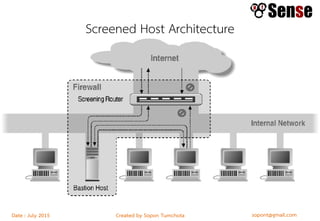
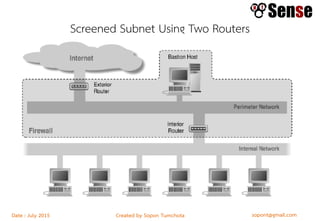
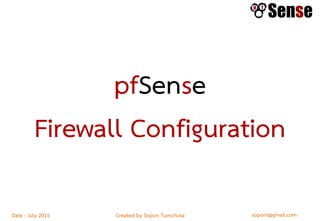
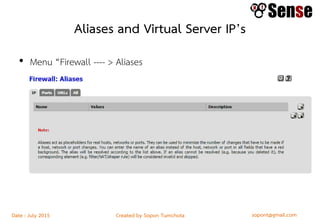
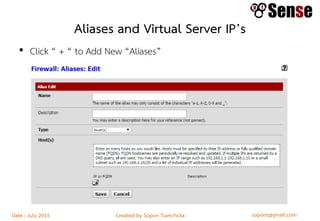
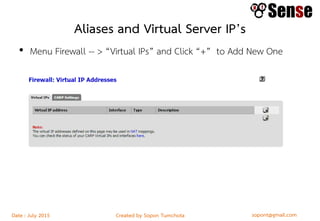
- Sections within the guide on firewall types like packet filters, application proxies, and dynamic packet filters.