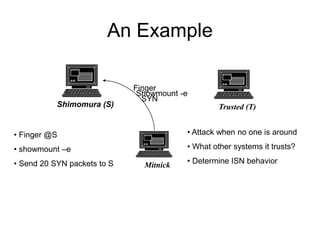
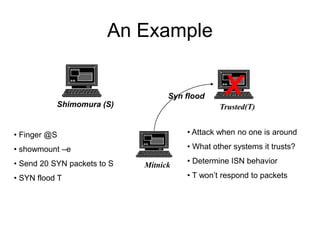
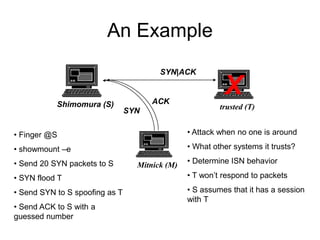
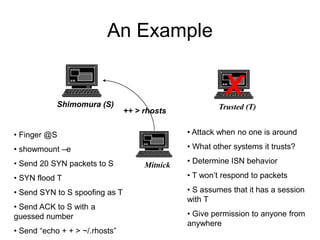
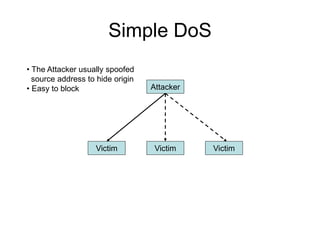
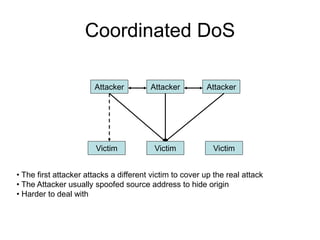
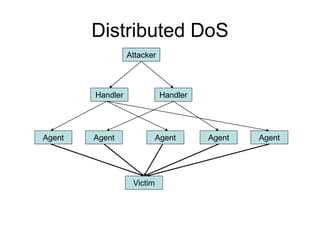
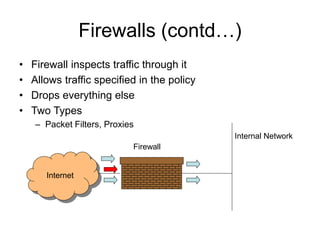
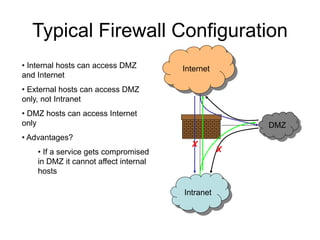
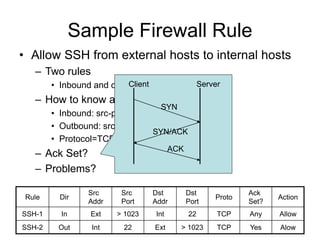
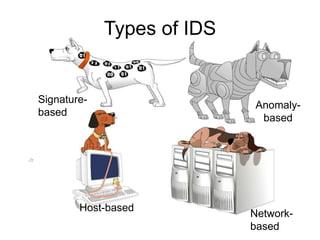
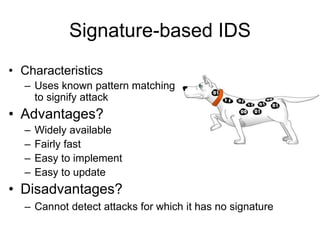
This document discusses network security concepts like vulnerabilities in TCP/IP protocols, denial of service attacks, firewalls, and intrusion detection systems. It outlines common attacks like spoofing, flooding, and session hijacking. It also describes the functions of packet filtering firewalls and proxy firewalls, as well as signature-based and anomaly-based intrusion detection systems that can monitor networks or individual hosts.