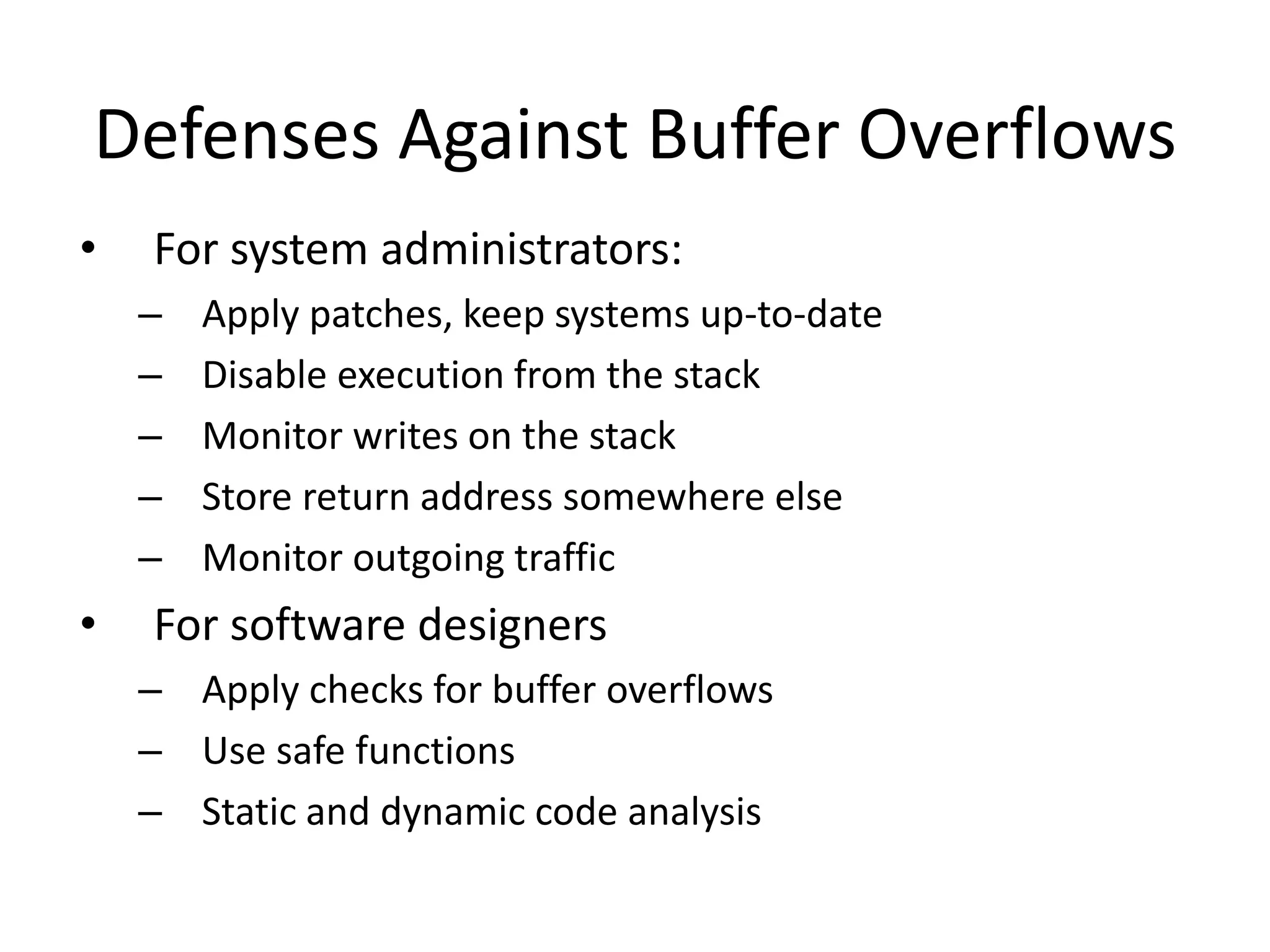
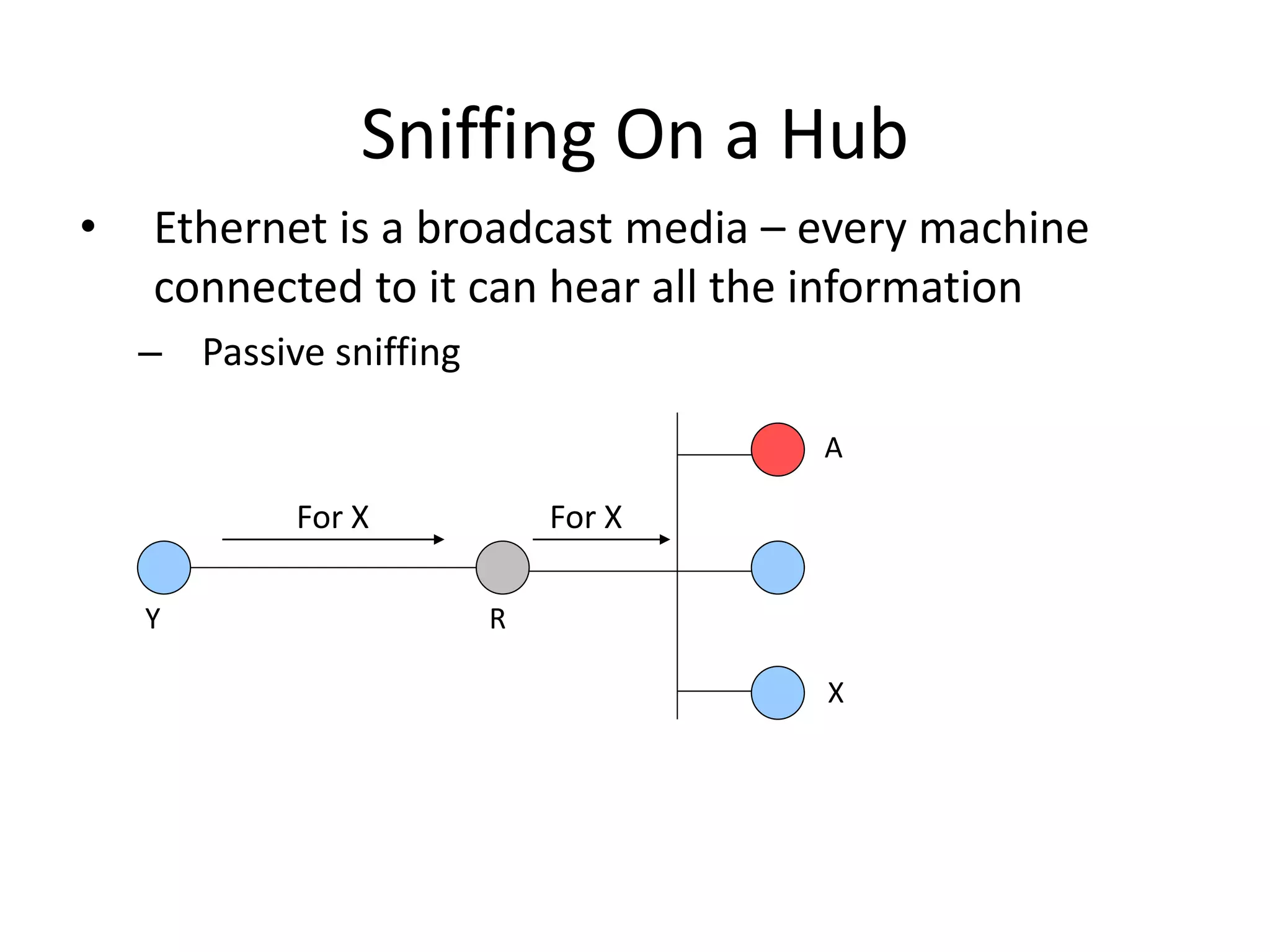
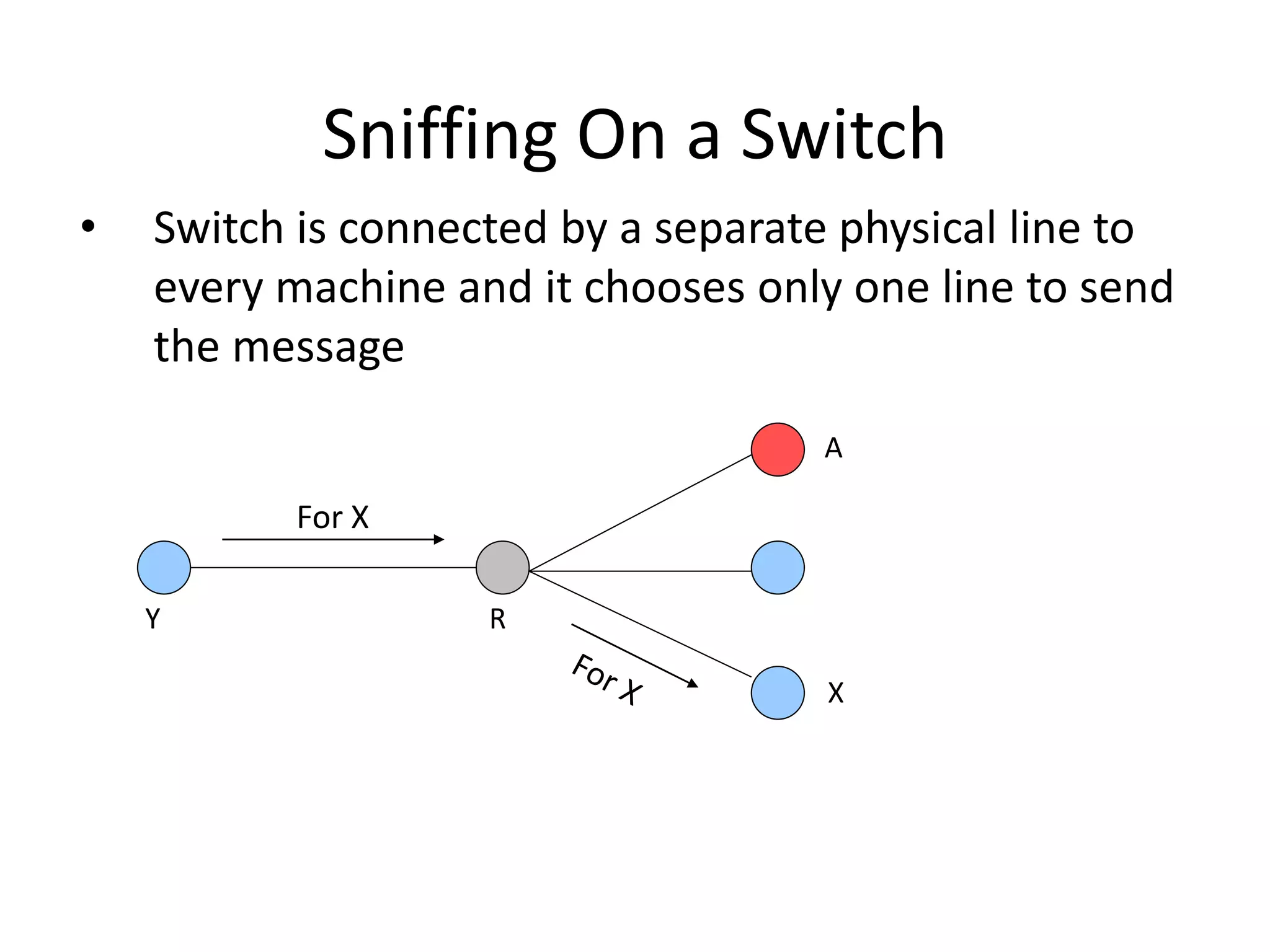
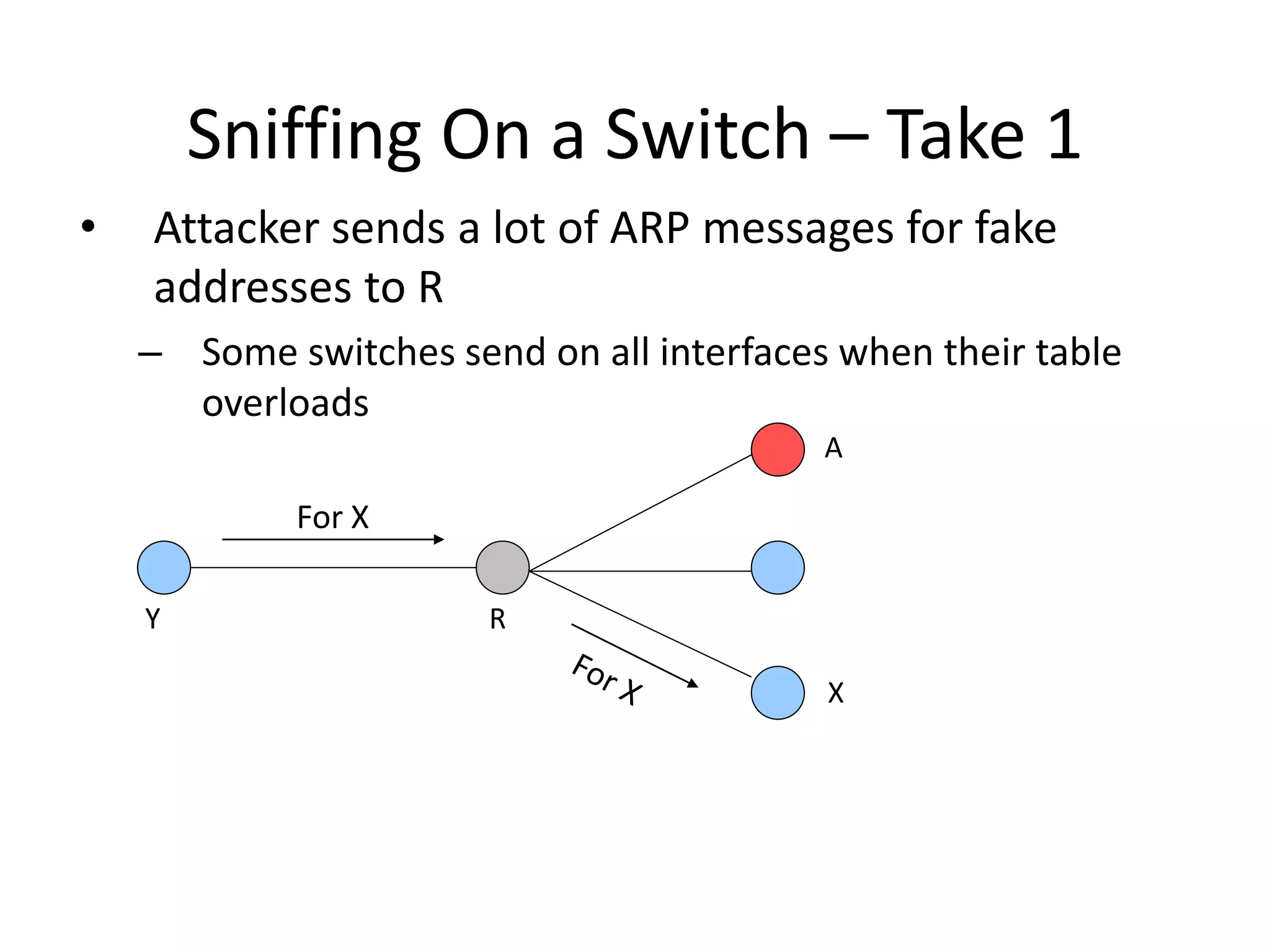
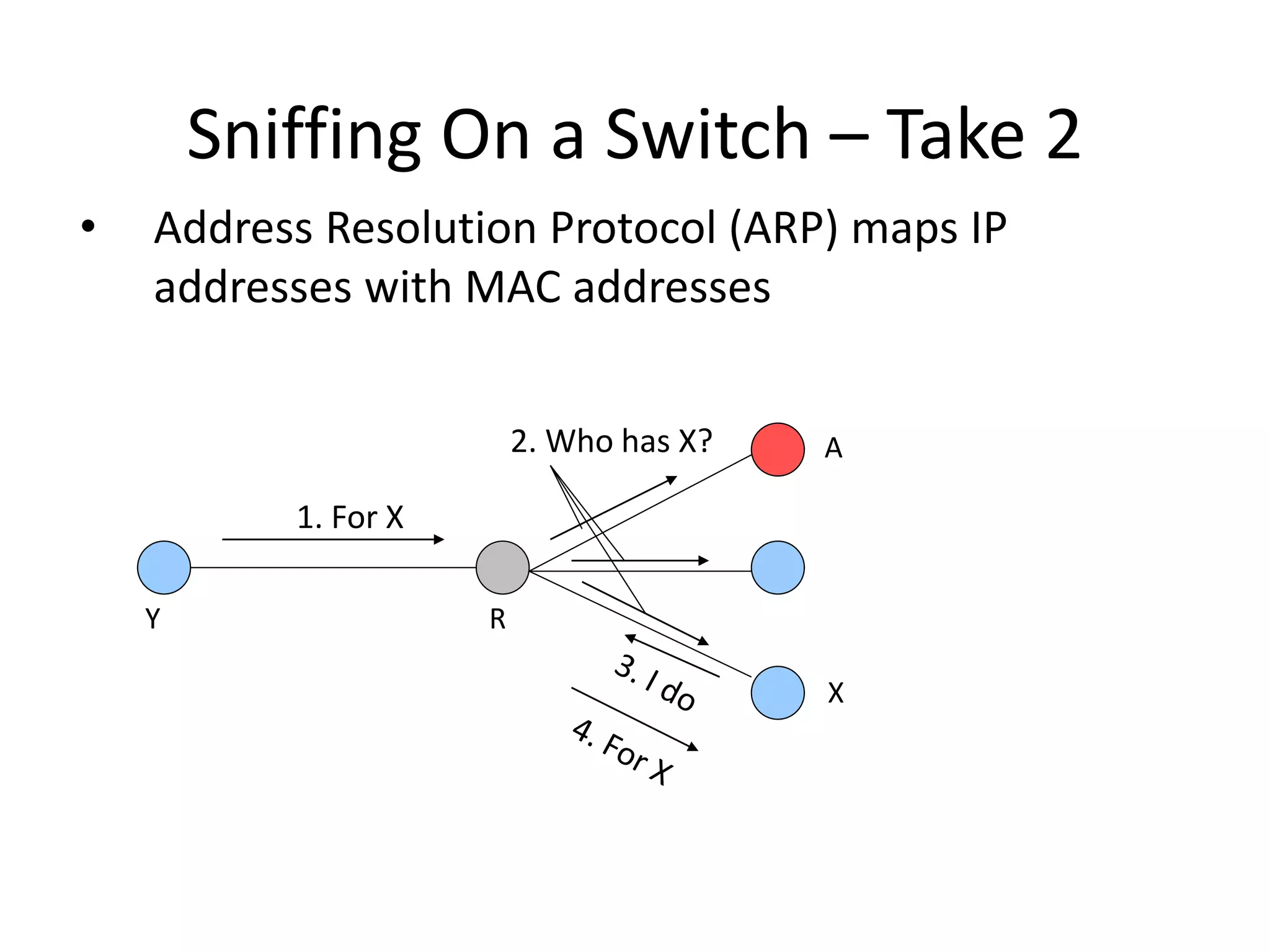
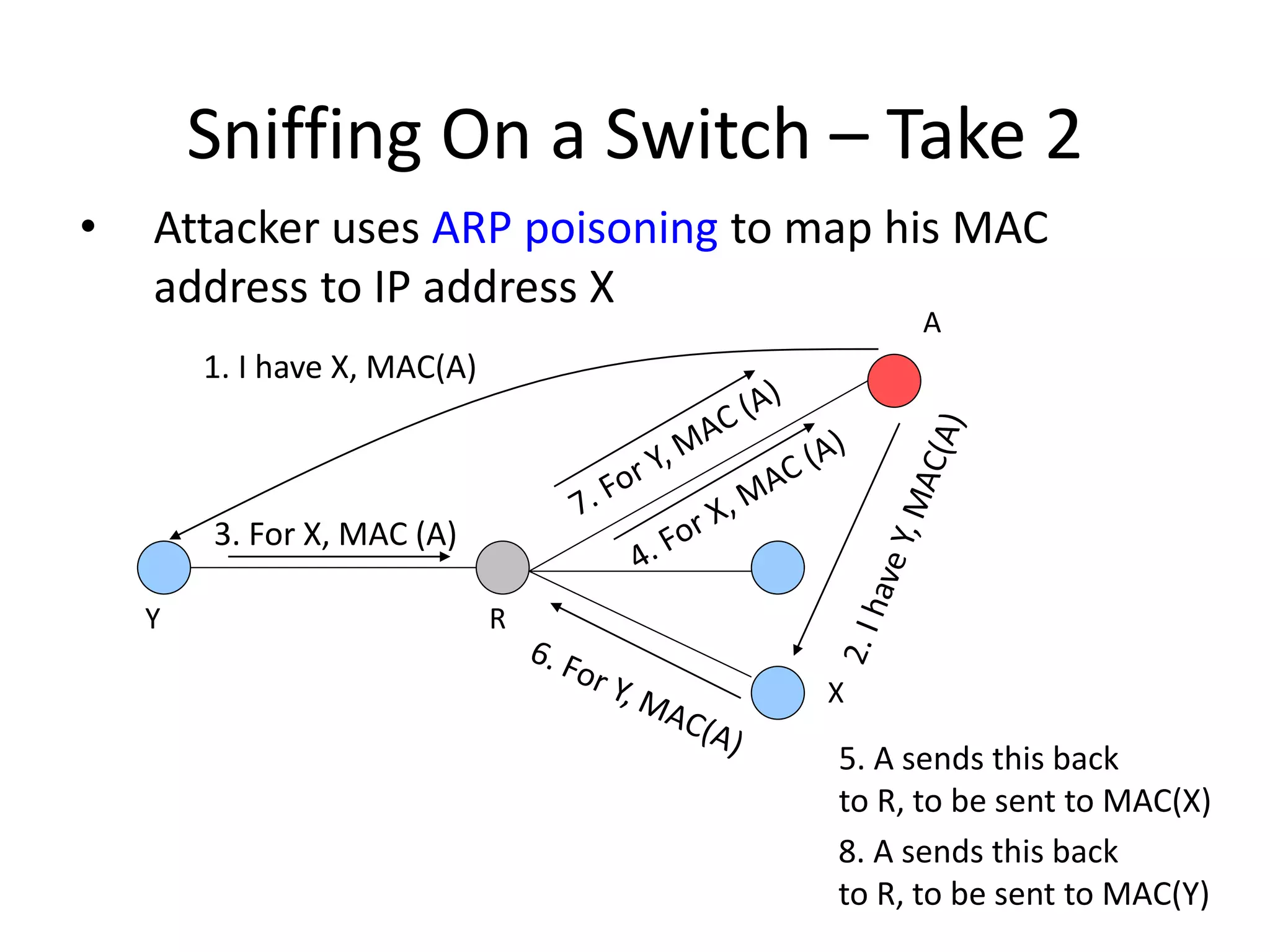
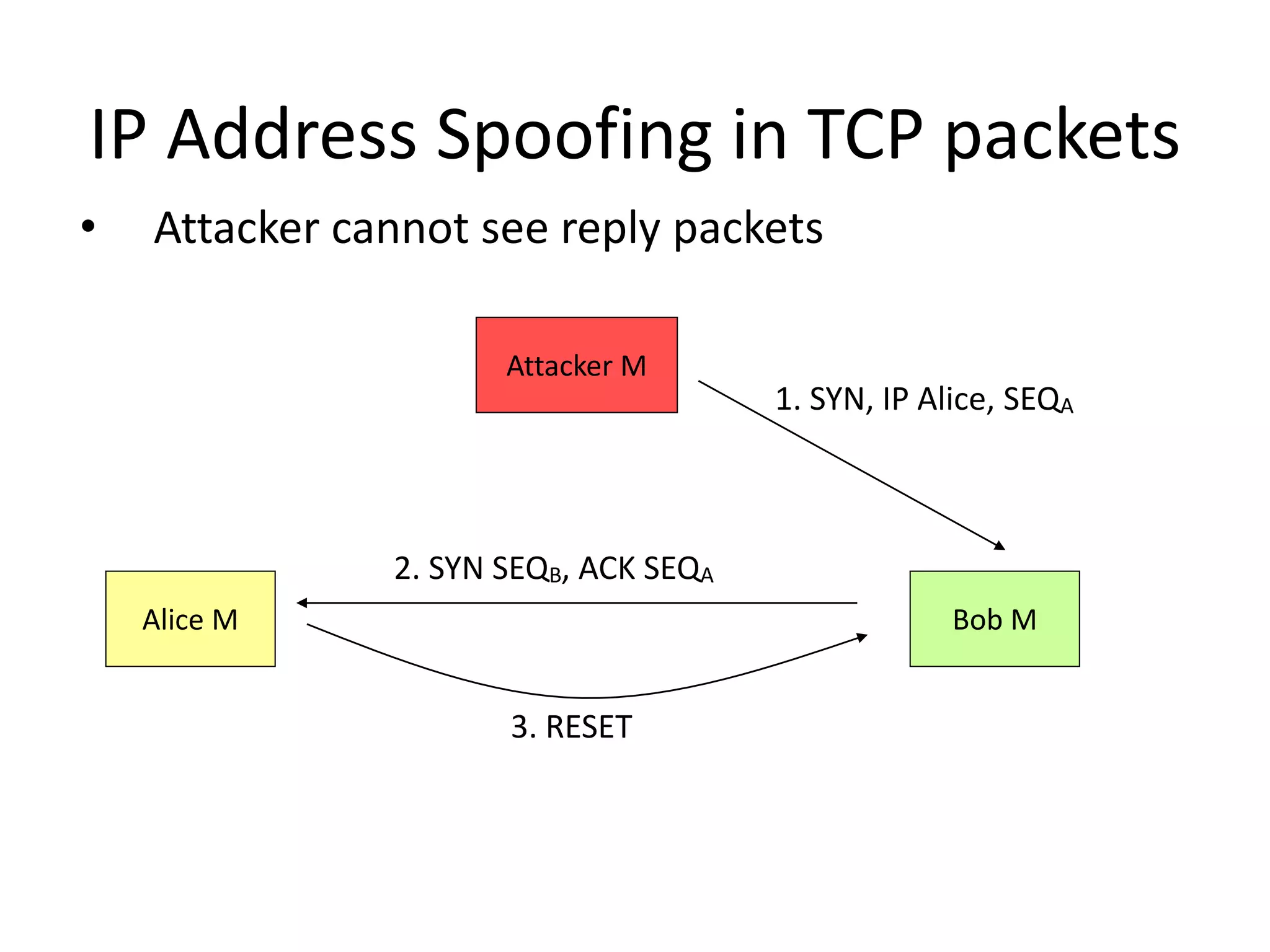
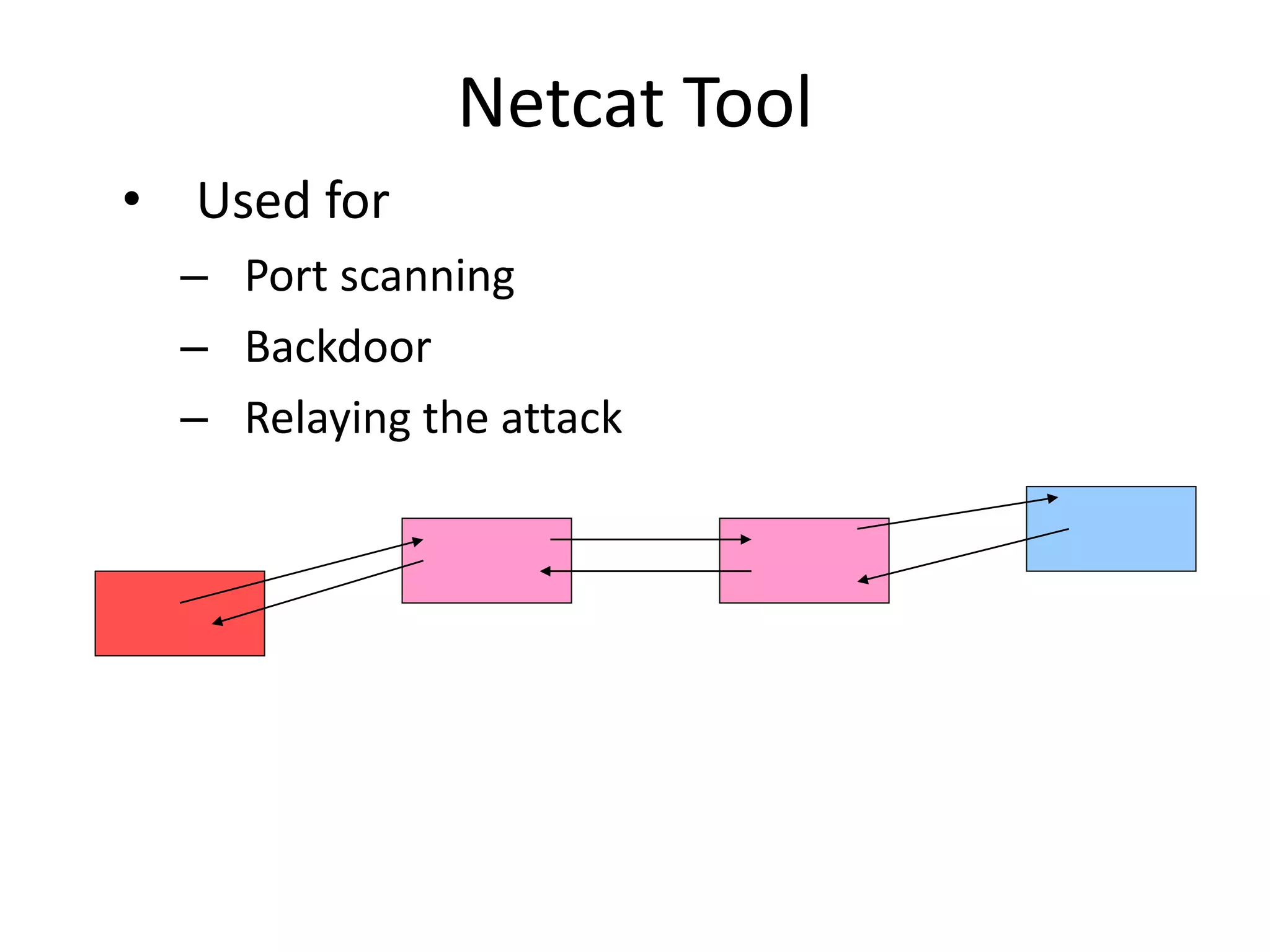
The document discusses various phases of intrusion and techniques used by attackers:
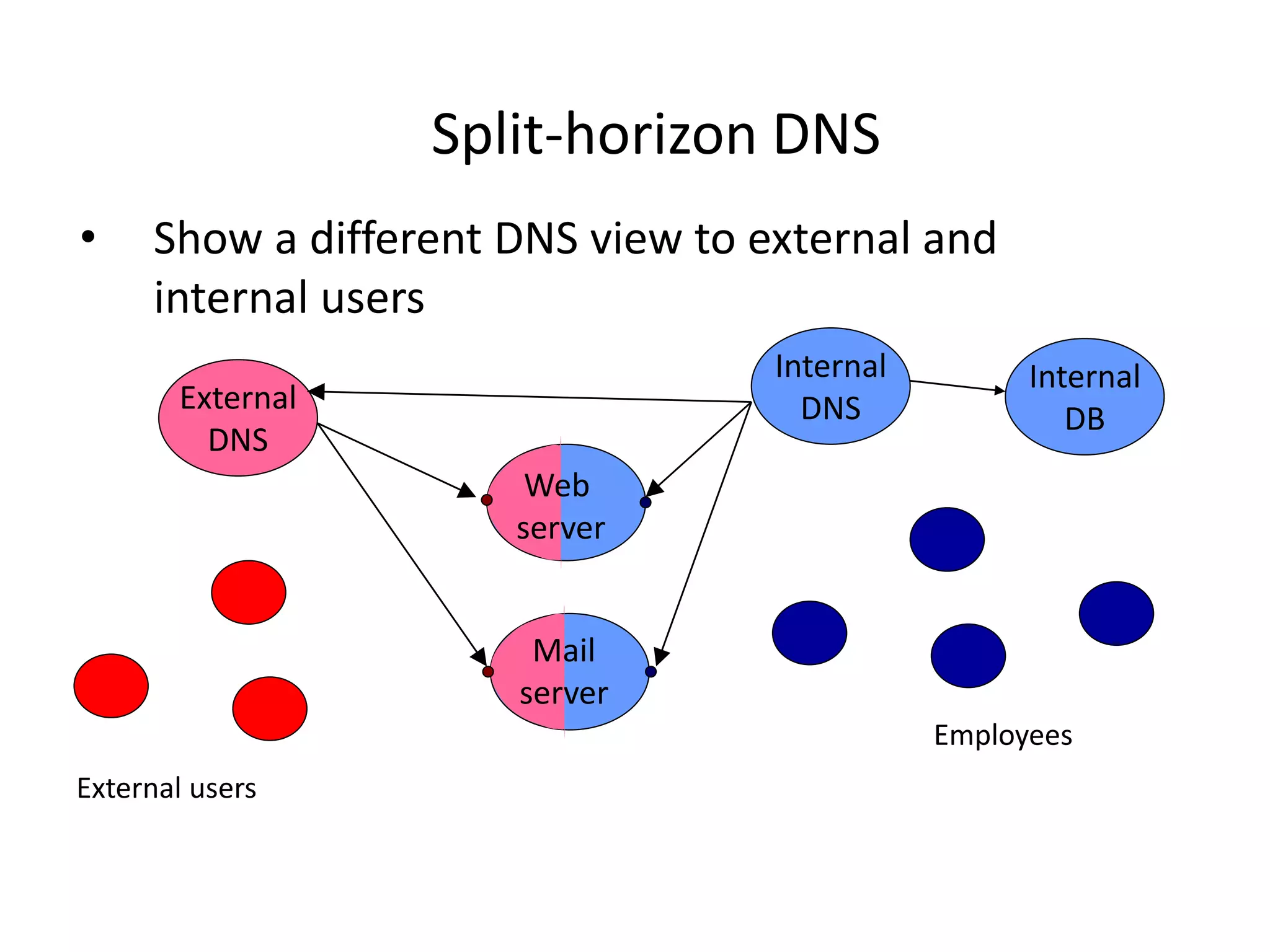
1. Reconnaissance involves gathering information about the target through techniques like searching public databases, domain name records, and social engineering to map the network and discover vulnerabilities.
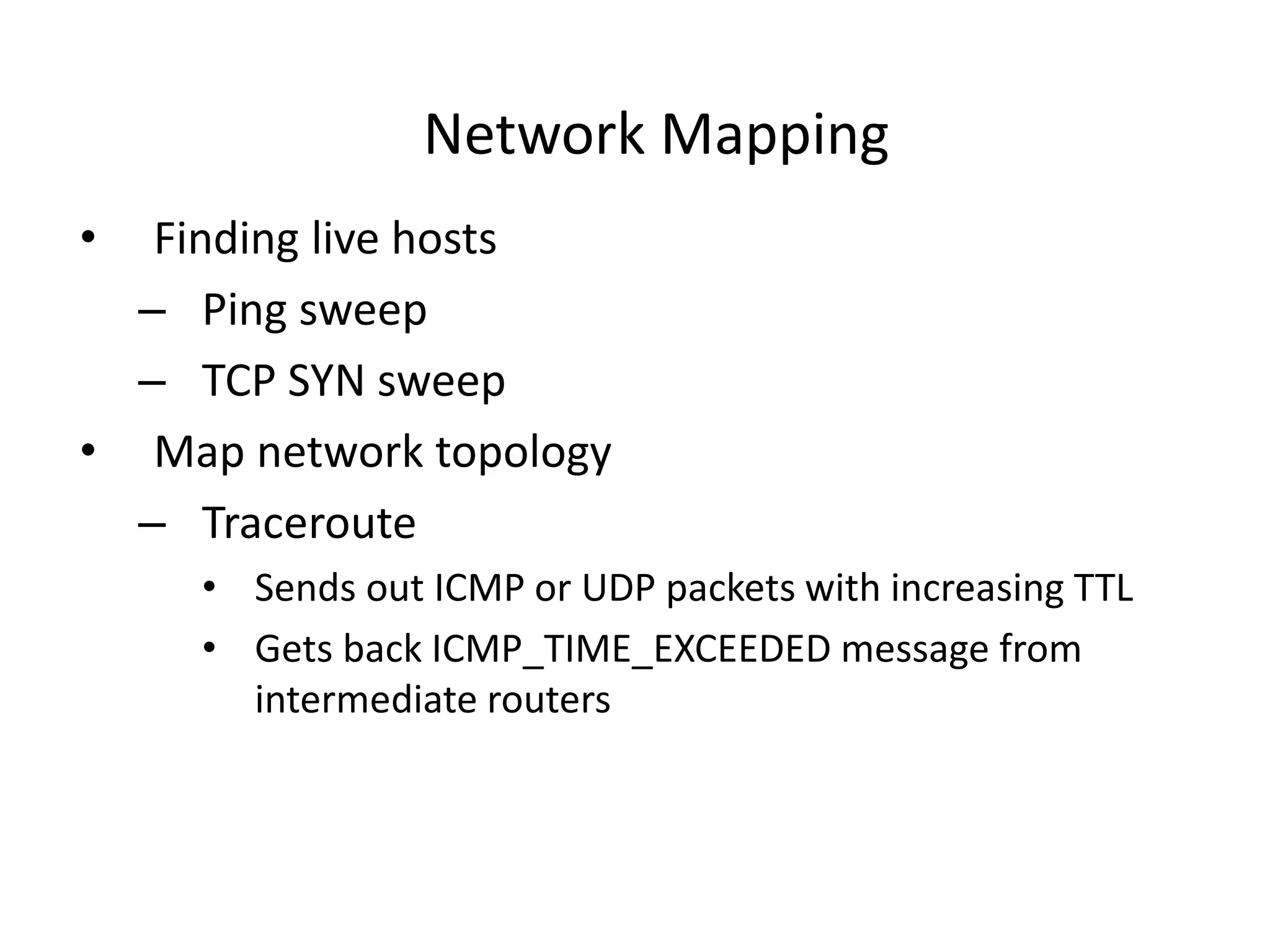
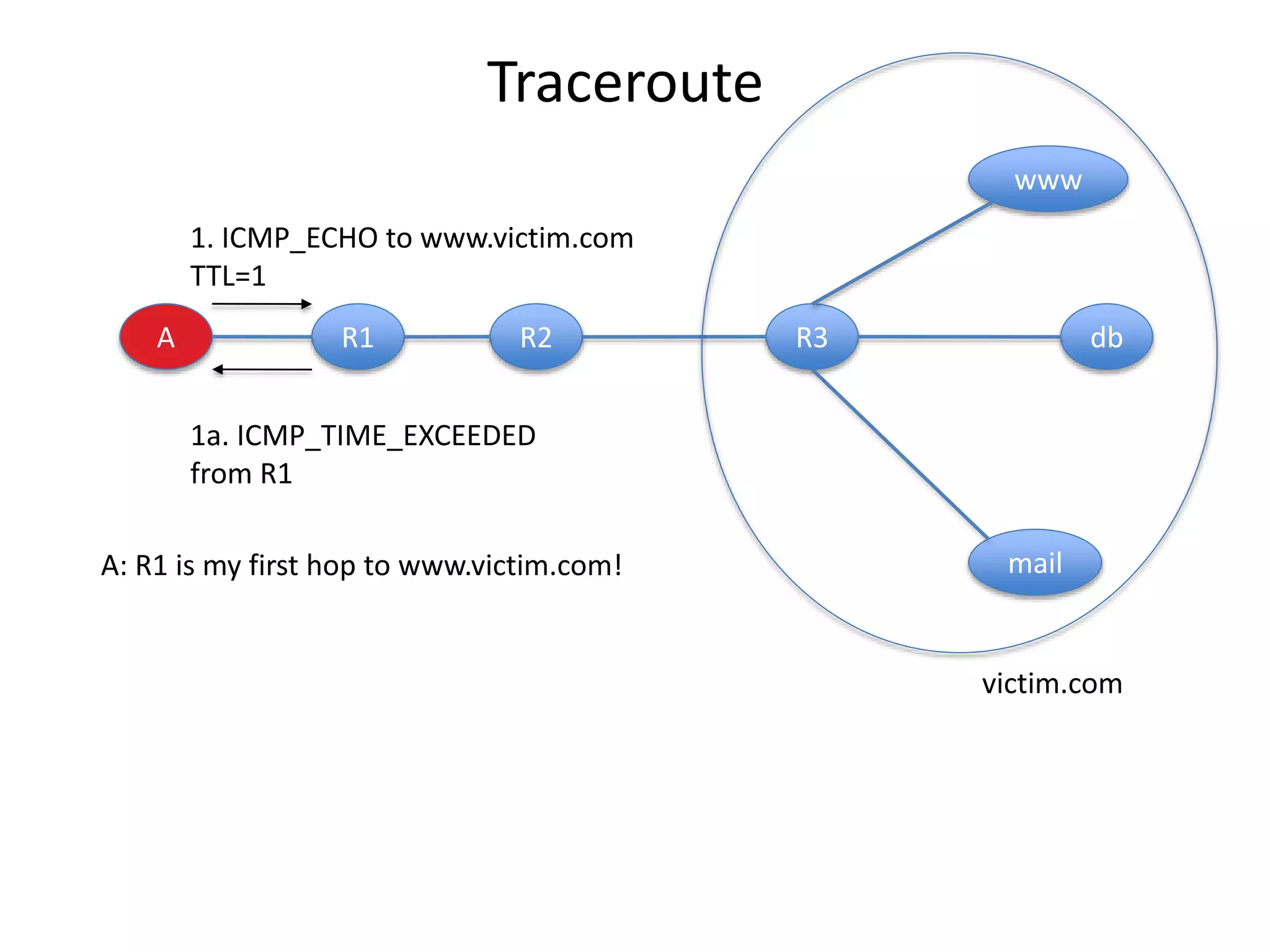
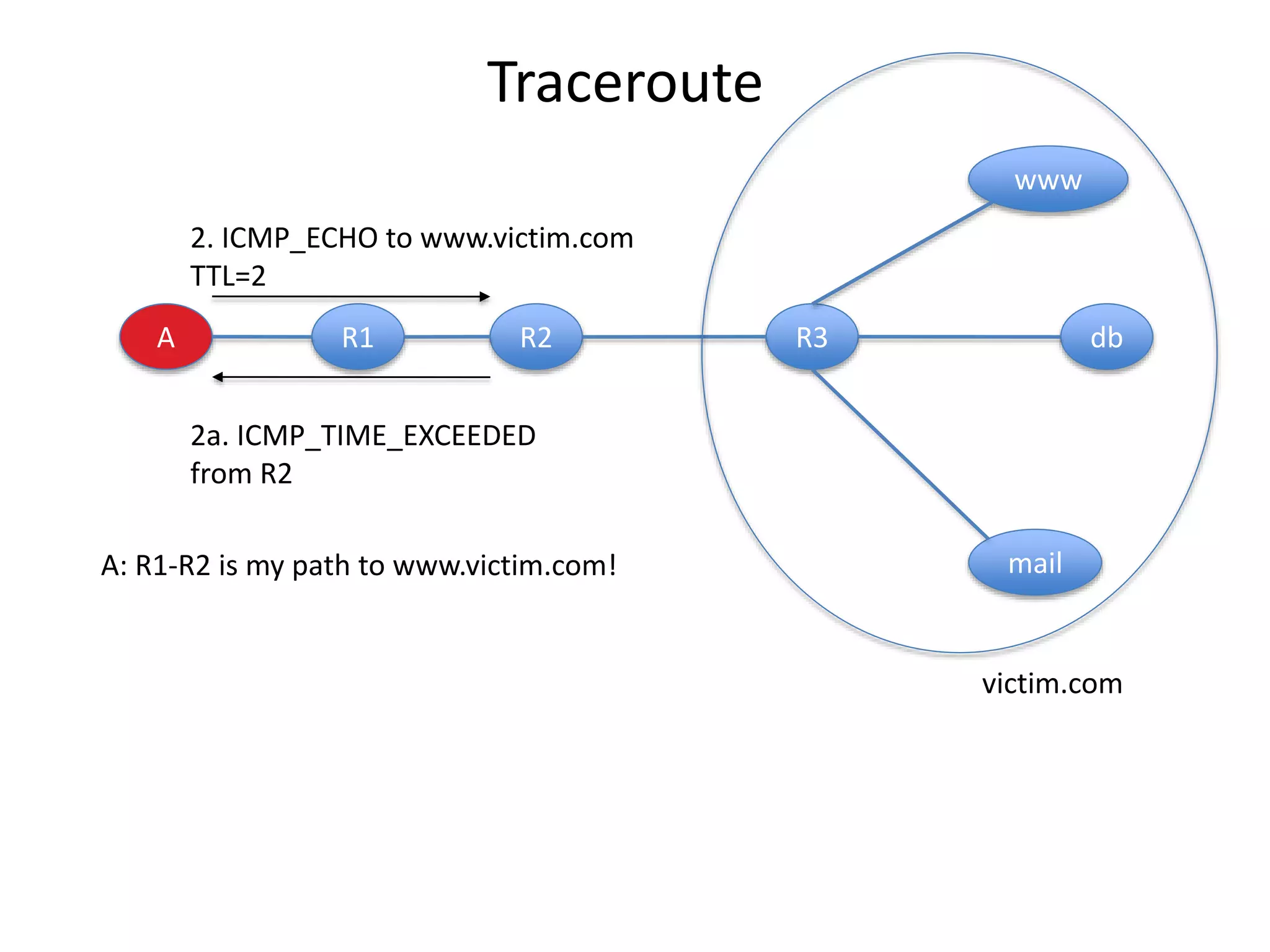
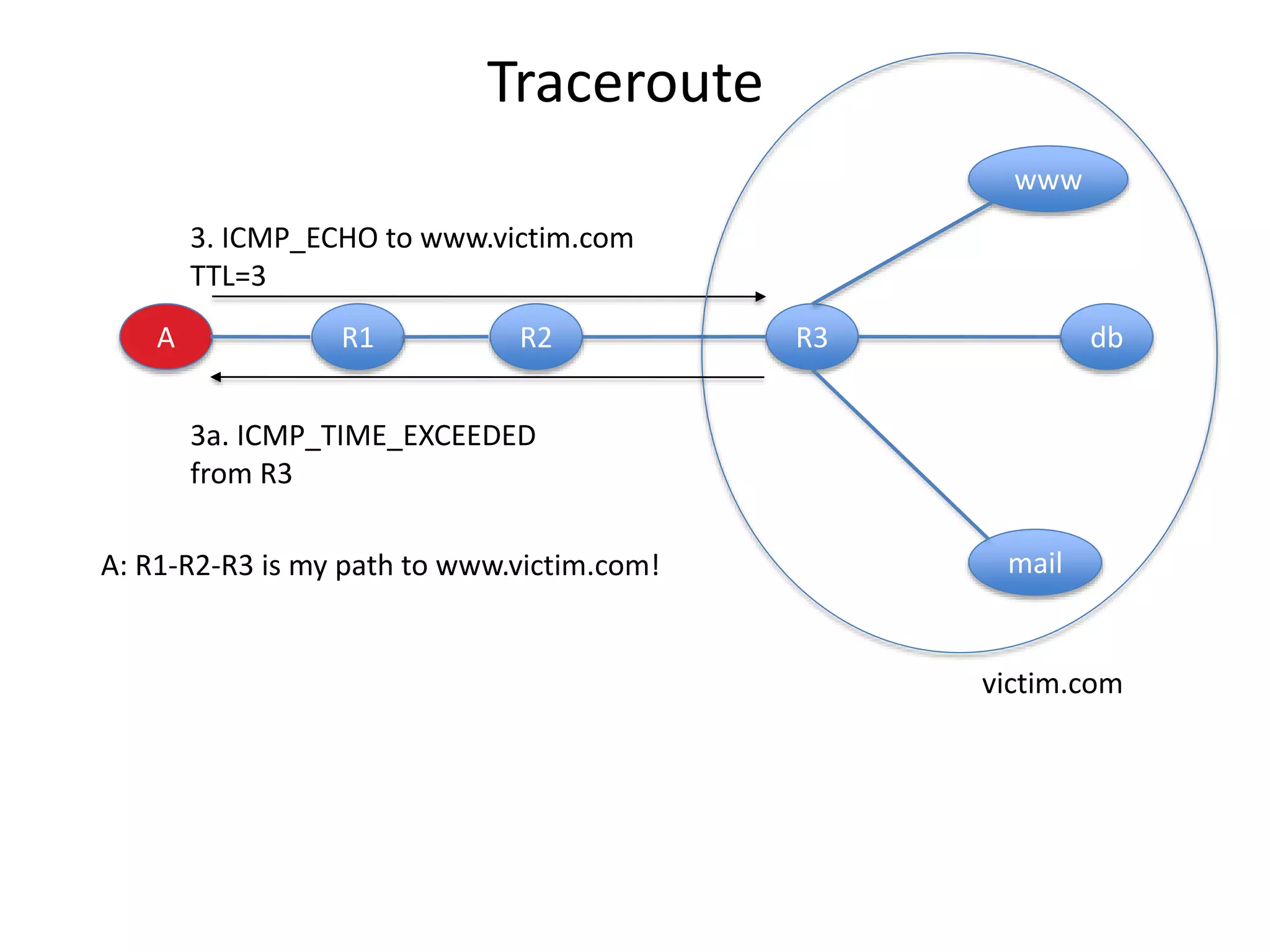
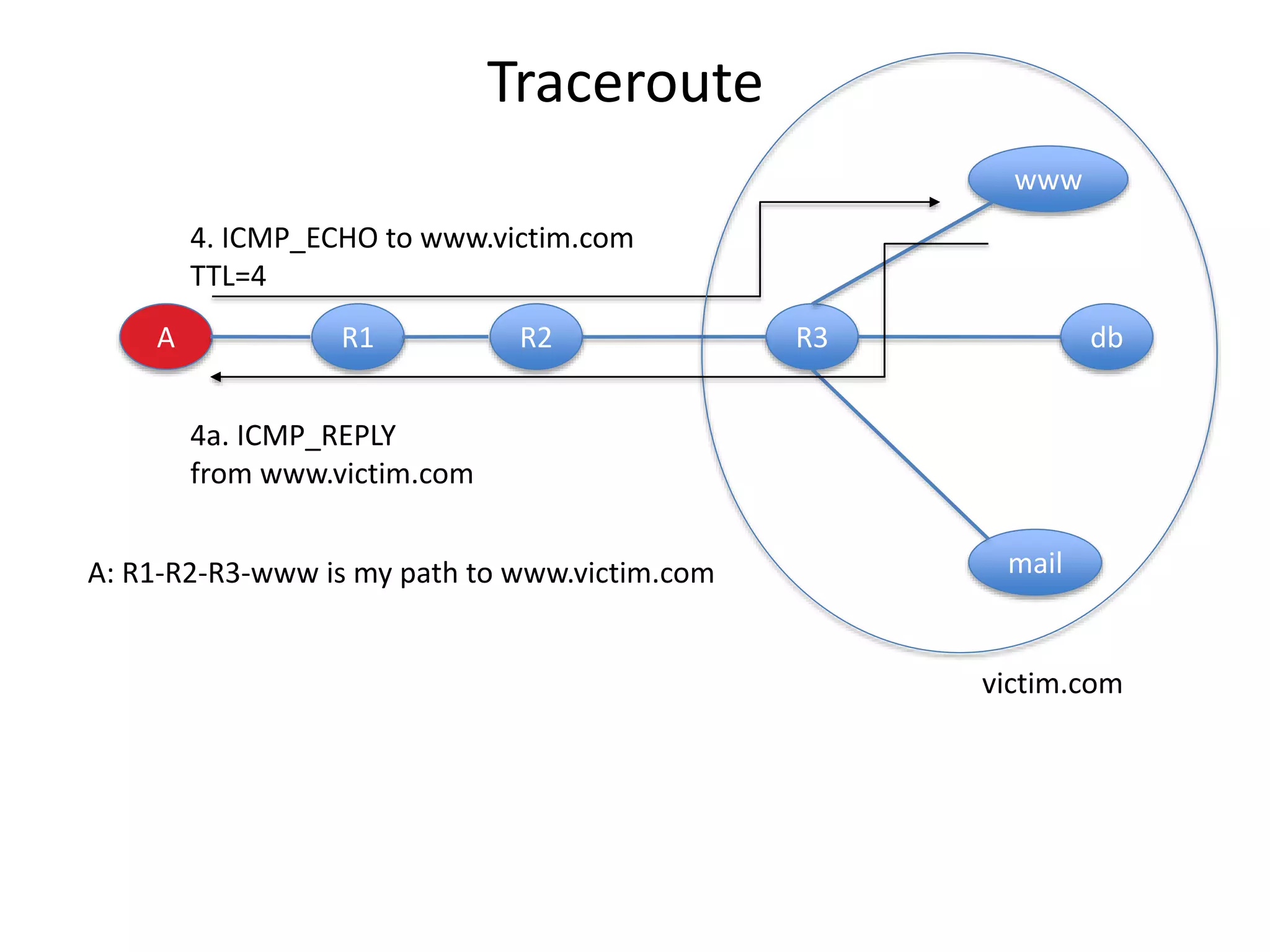
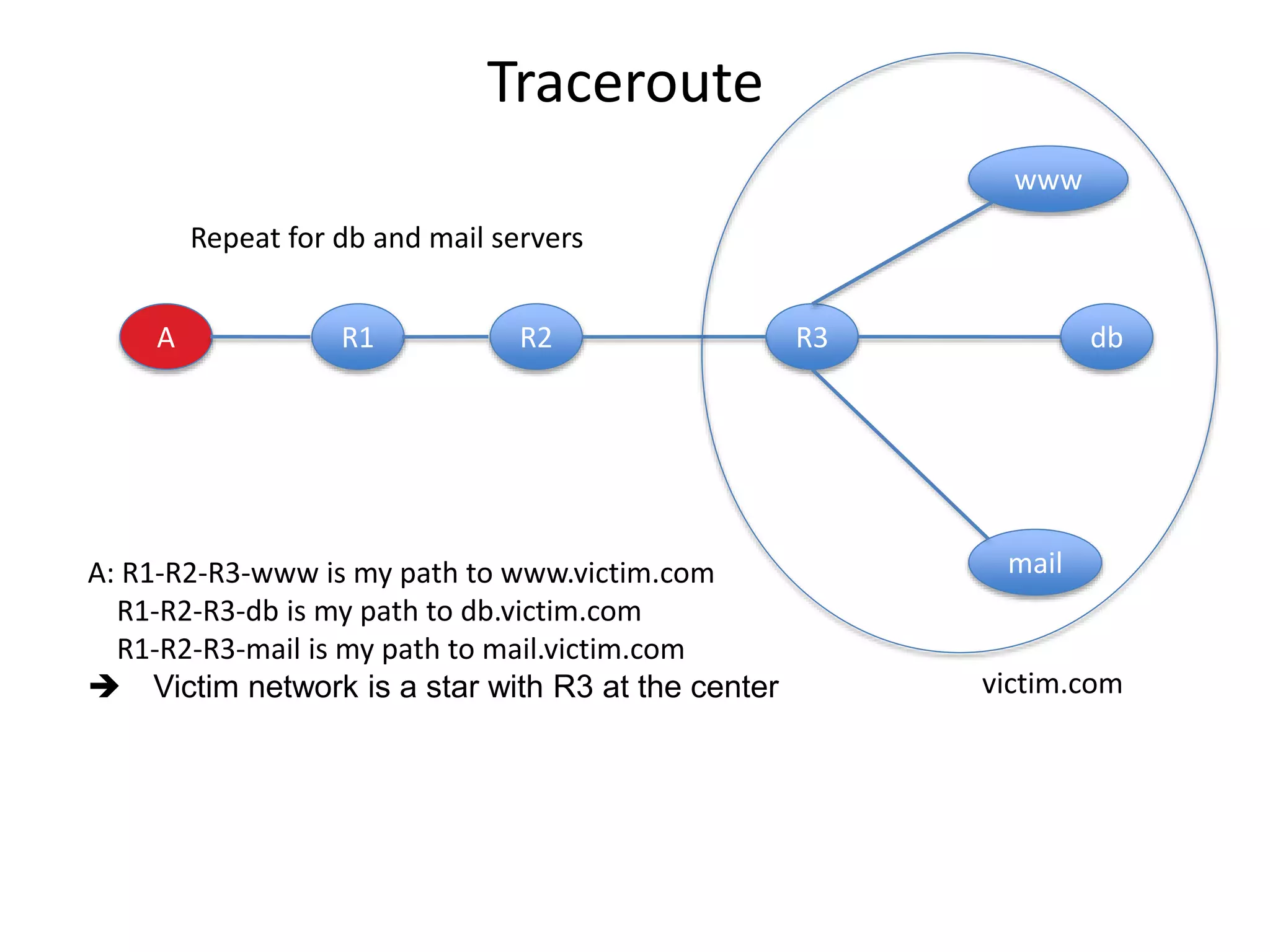
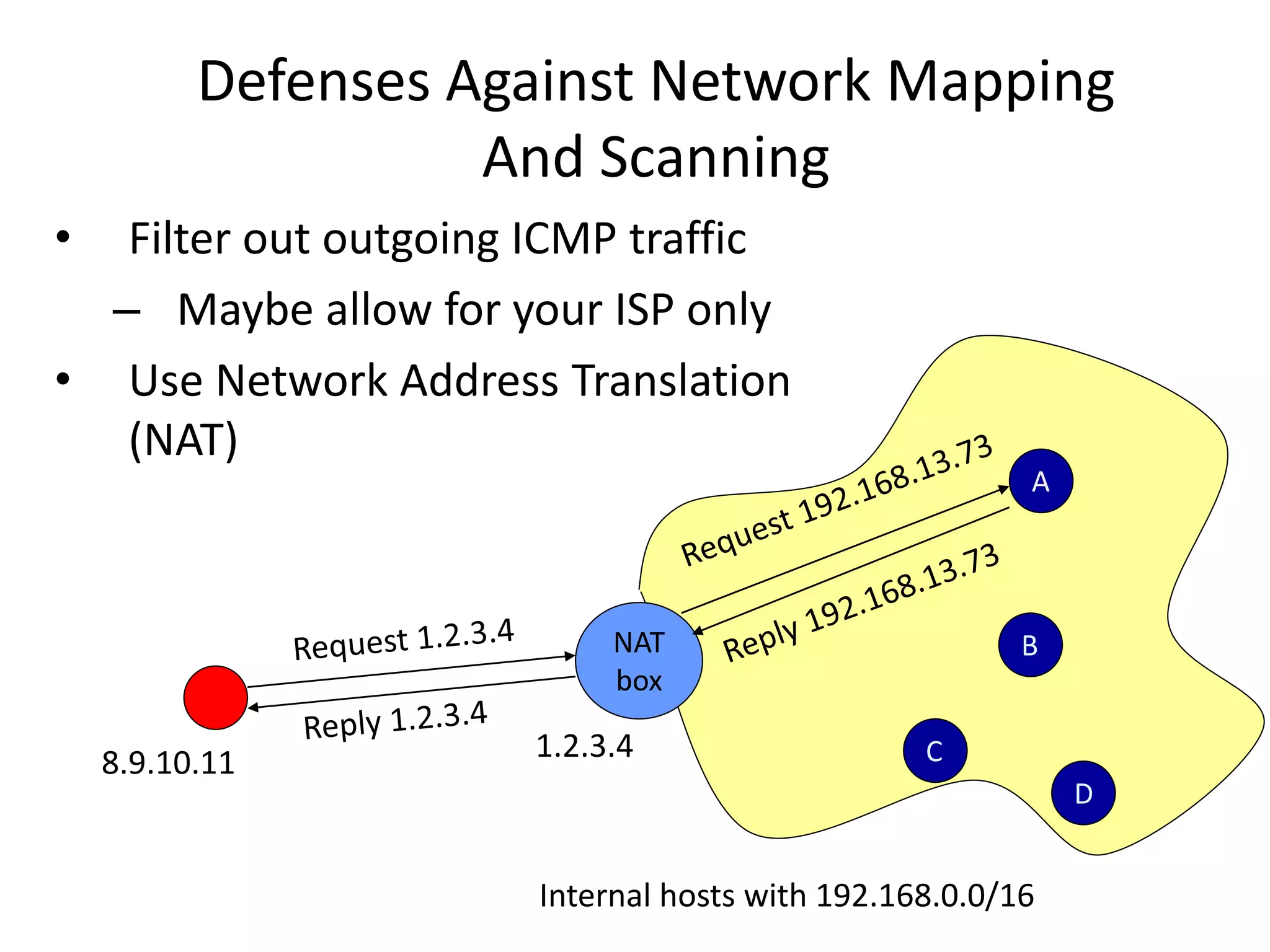
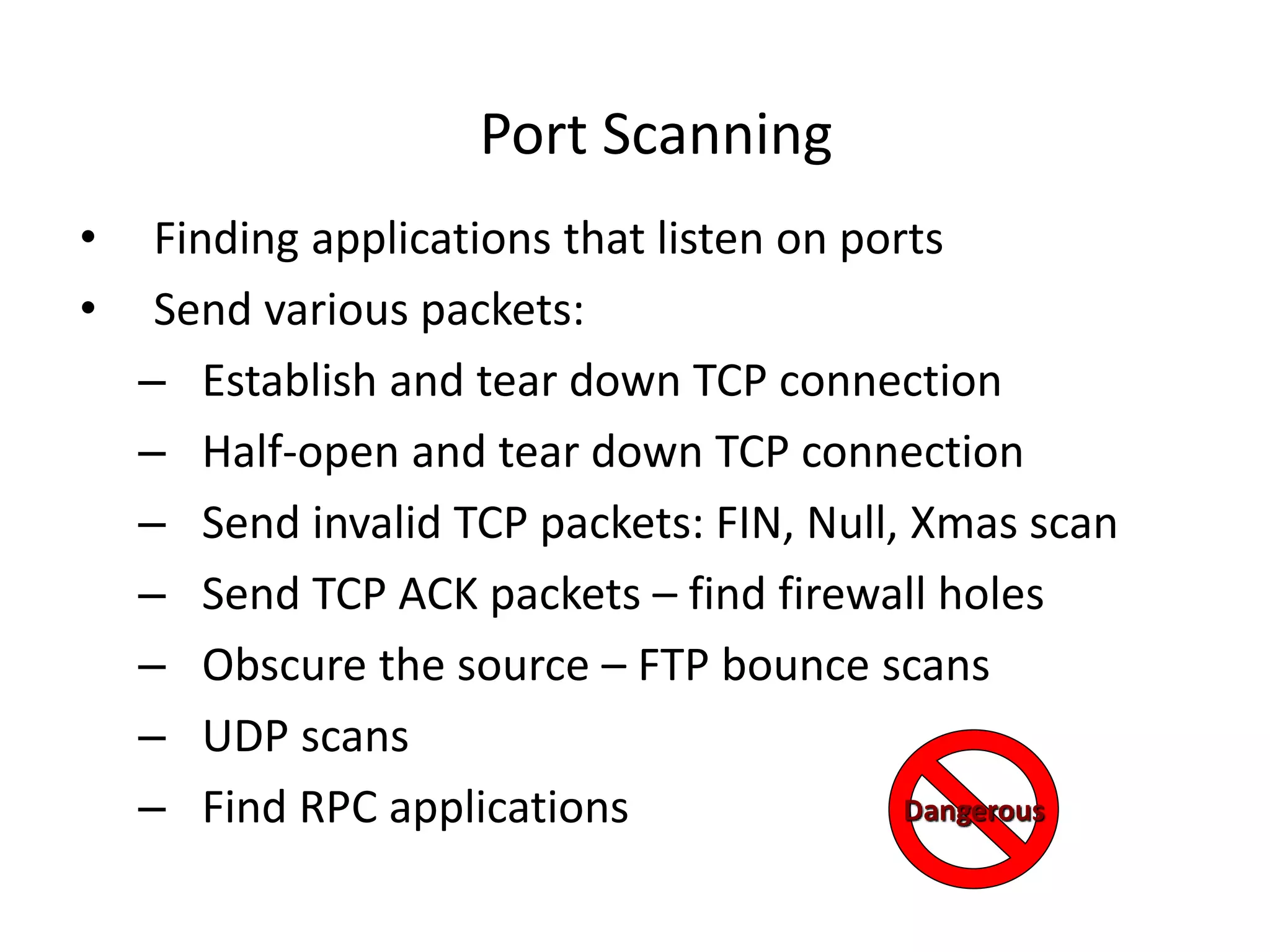
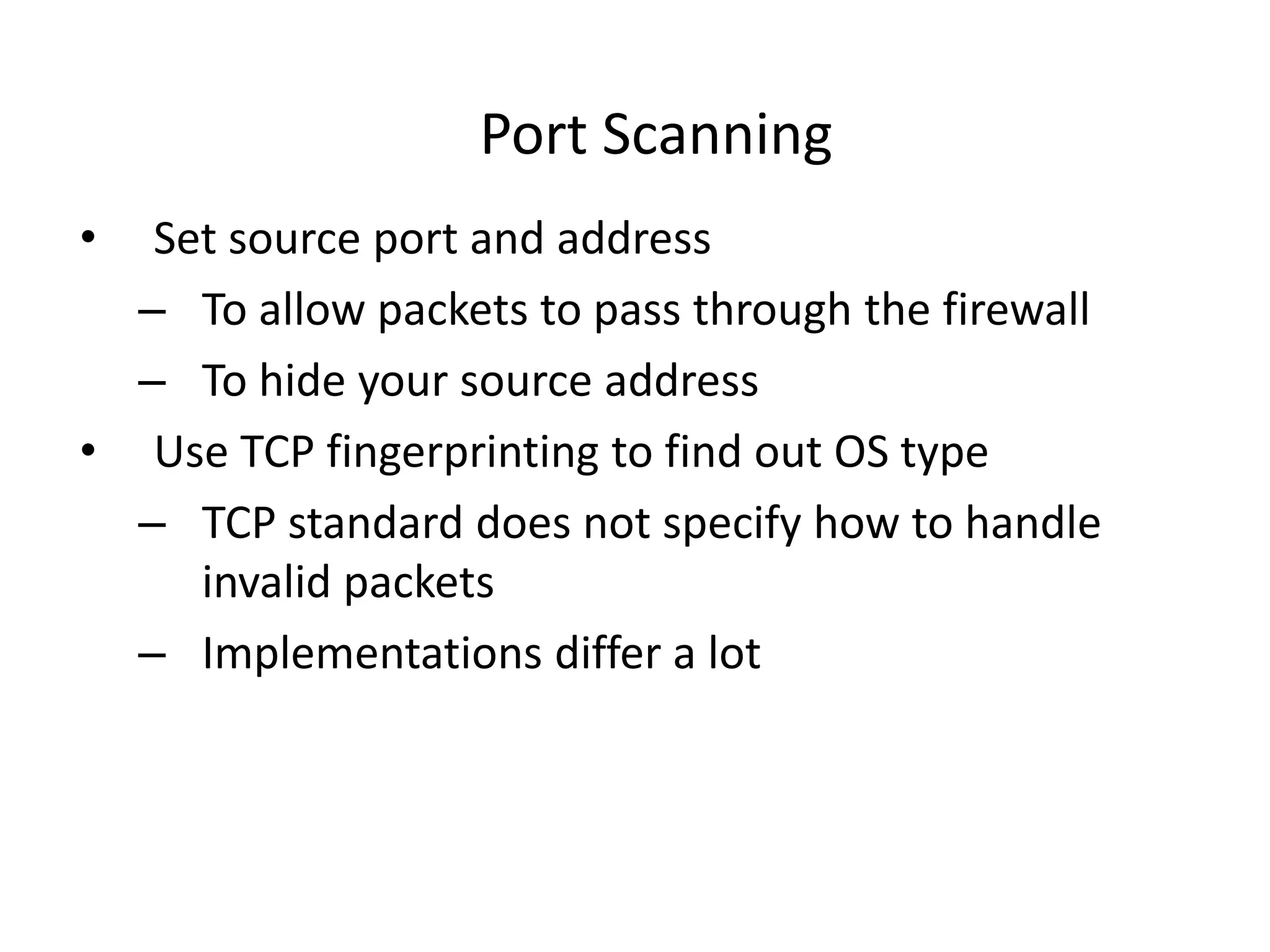
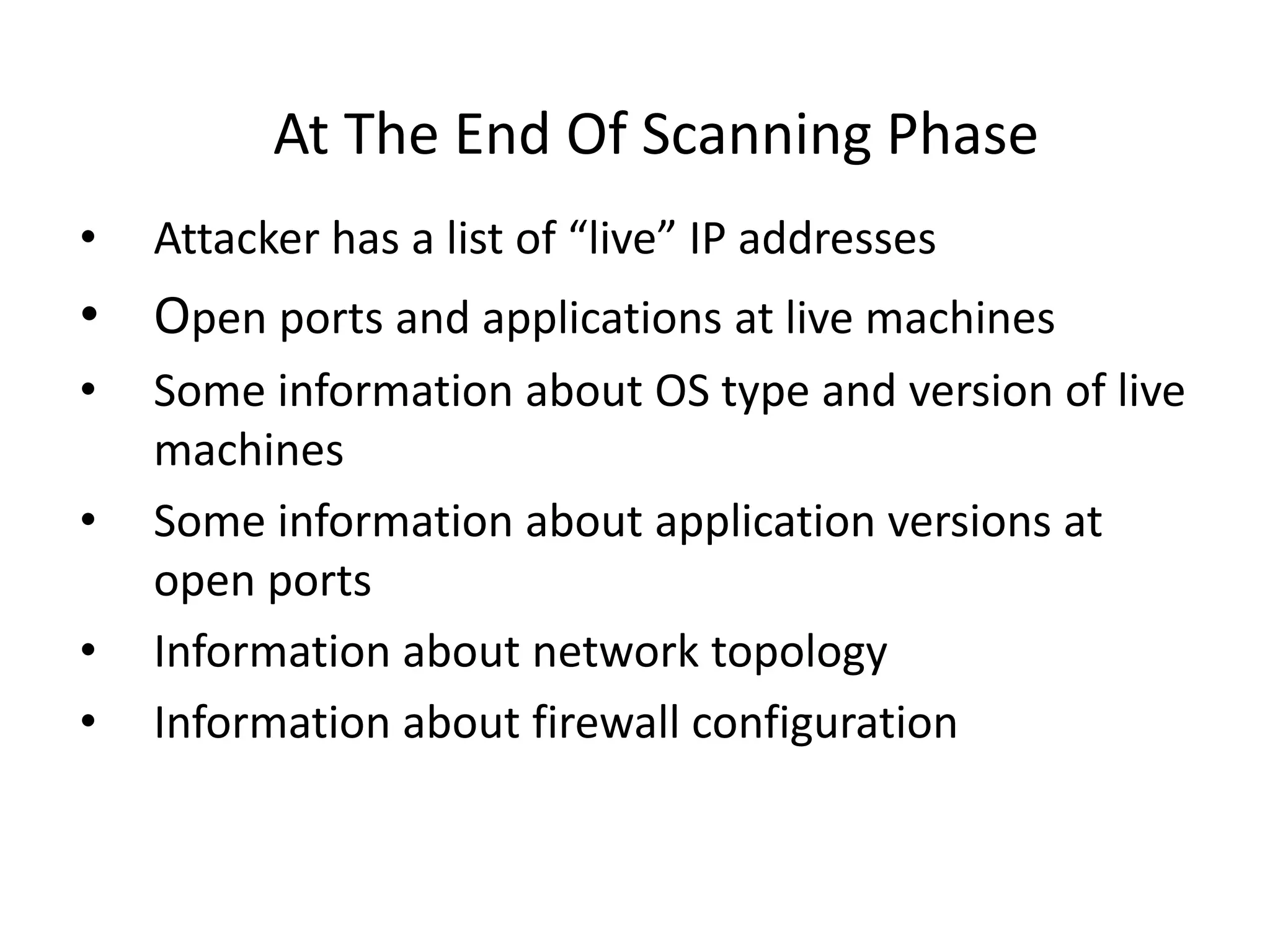
2. Scanning detects live machines, network topology, firewall configurations, applications, and vulnerabilities using tools like ping sweeps, traceroute, port scanning, and vulnerability scanners.
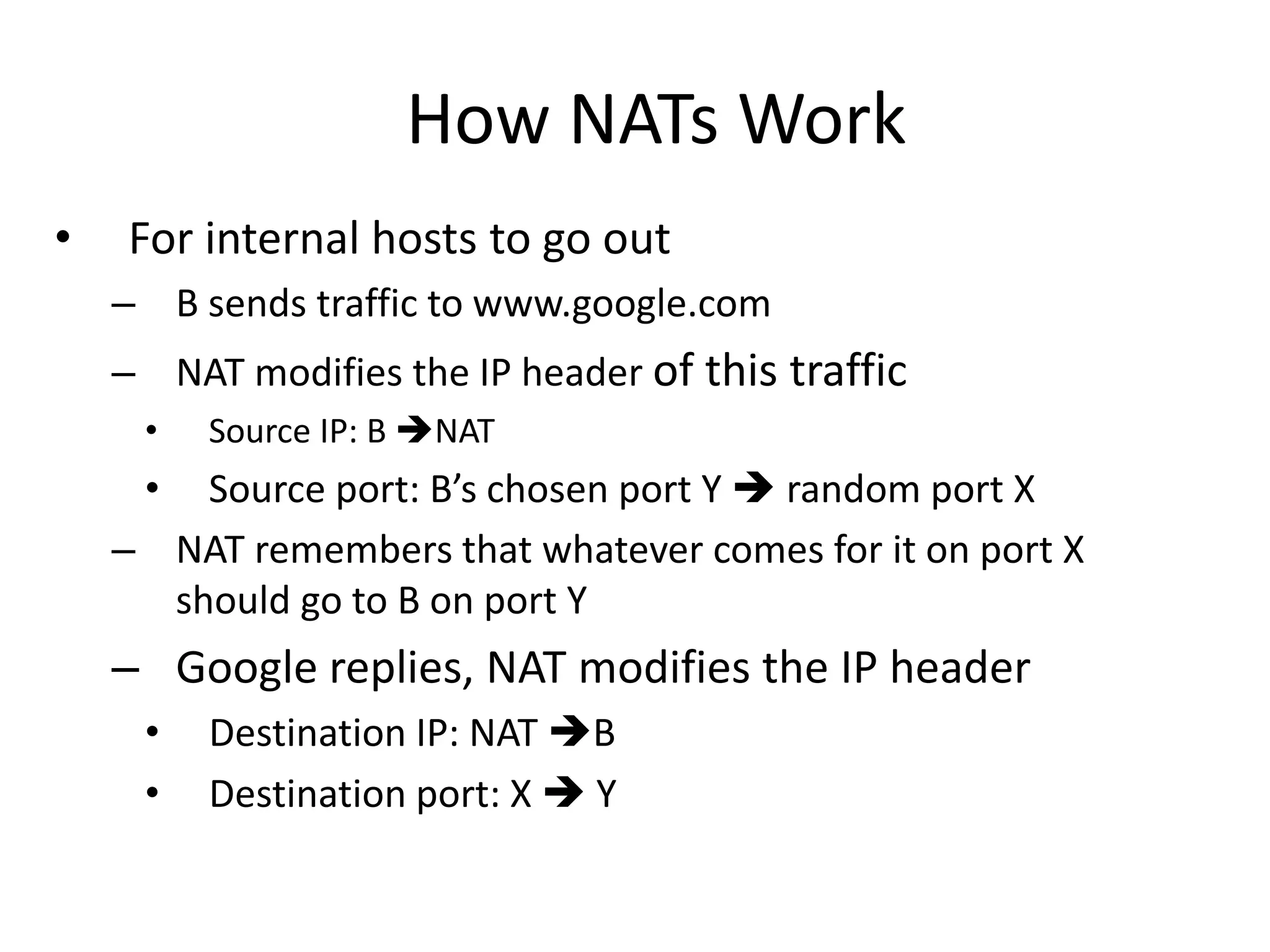
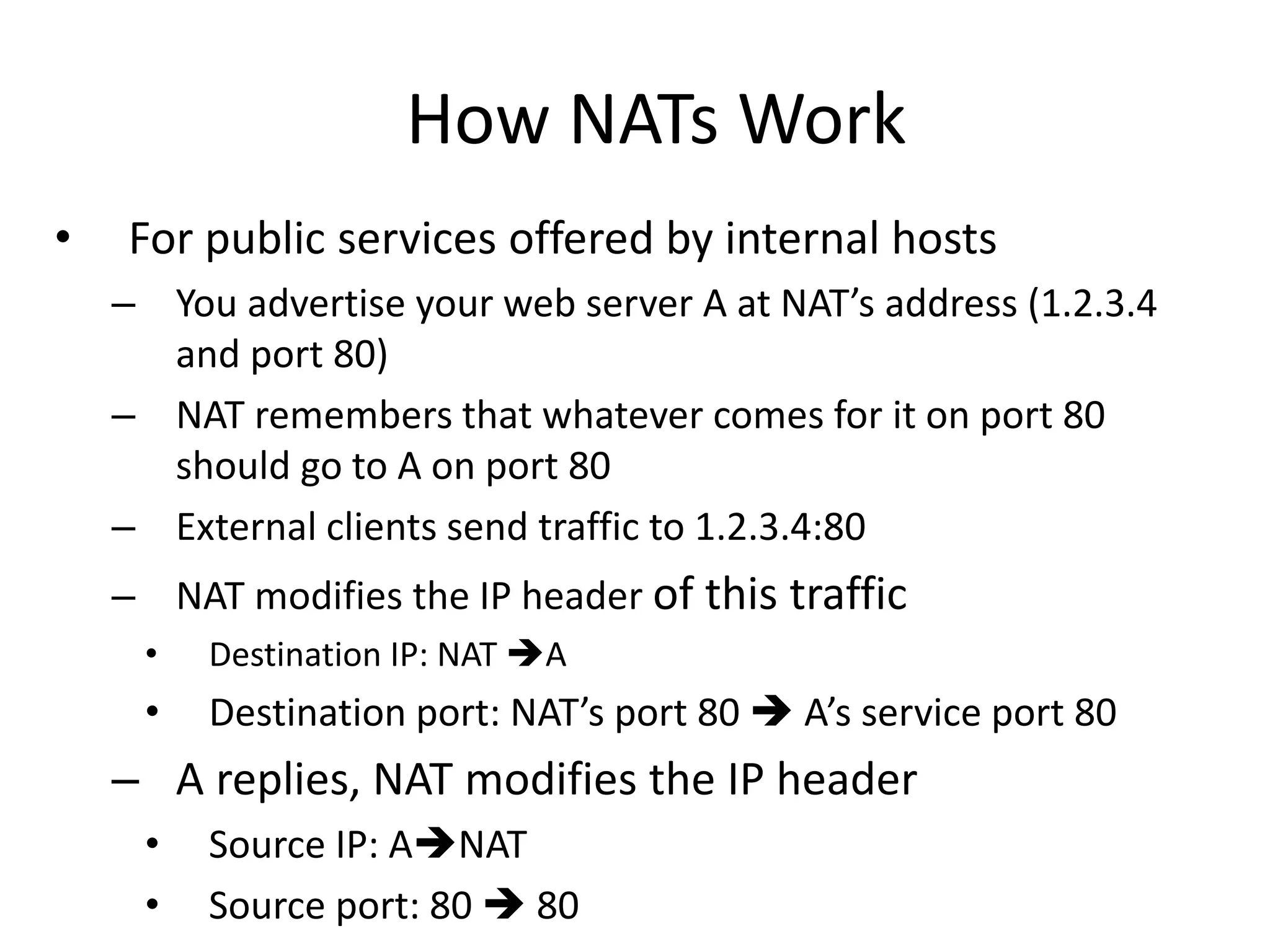
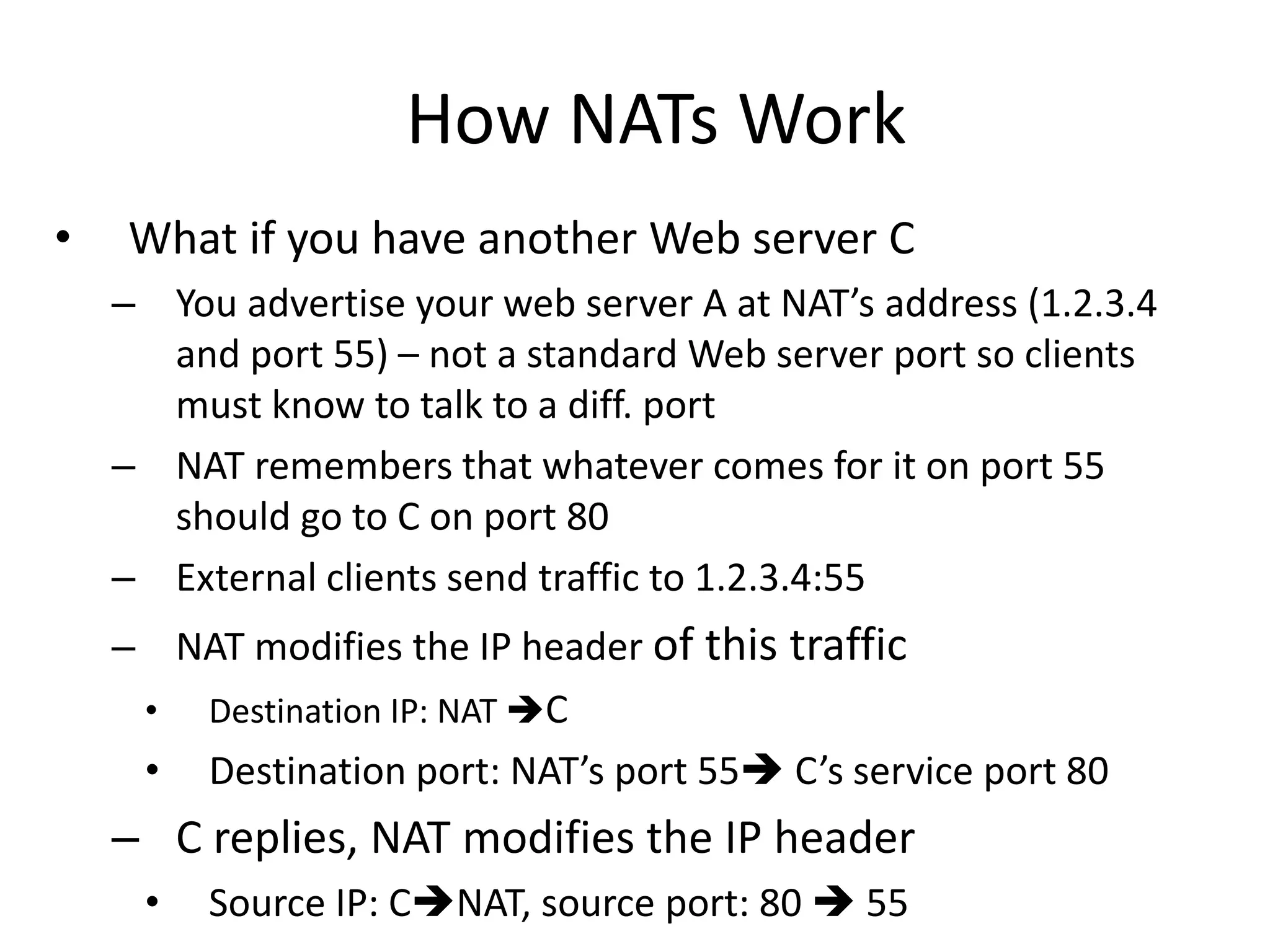
3. Gaining access exploits known vulnerabilities through buffer overflow attacks or by downloading exploits from hacker sites to compromise systems.


















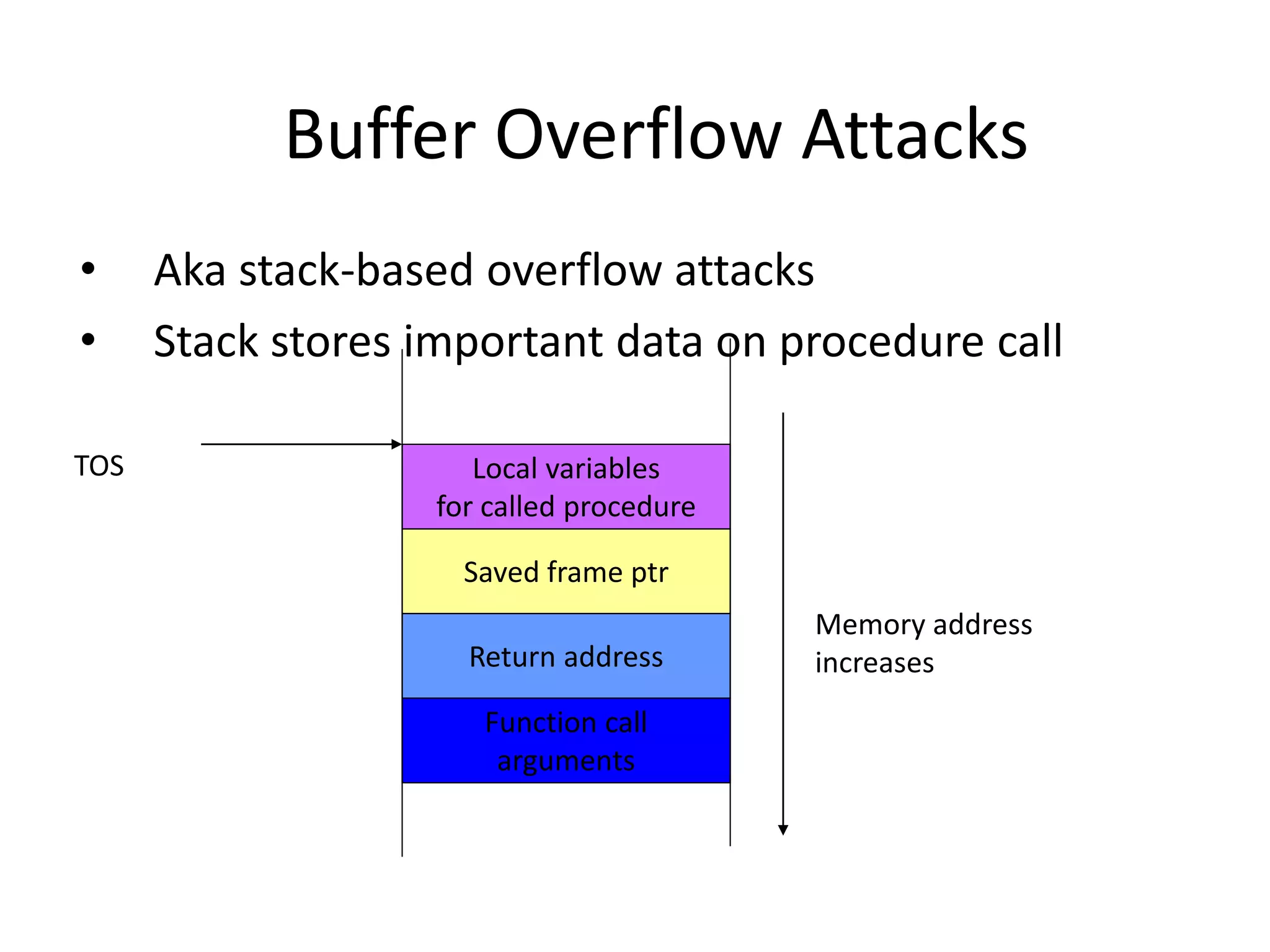
![Buffer Overflow Attacks
• Consider a function
void sample_function(char* s)
{
char buffer[10];
strcpy(buffer, s);
return;
}
• And a main program
void main()
{
int i;
char temp[200];
for(i=0; i<200;i++) temp[i]=‘A’;
sample_function(temp);
return;
}
Argument is larger
than we expected
…](https://image.slidesharecdn.com/lecture5-221027074153-826edbf6/75/lecture5-pptx-40-2048.jpg)
![Buffer Overflow Attacks
• Large input will be stored on the stack,
overwriting system information
Function call
arguments
Return address
Saved frame ptr
s,buffer[10]
TOS
Memory address
increases
Overwritten
by A’s](https://image.slidesharecdn.com/lecture5-221027074153-826edbf6/75/lecture5-pptx-41-2048.jpg)