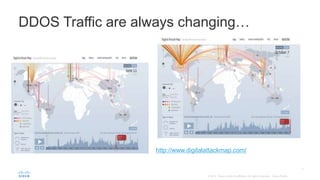
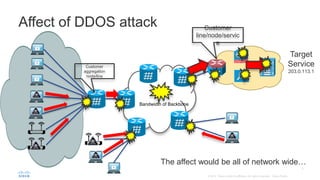
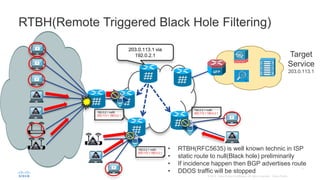
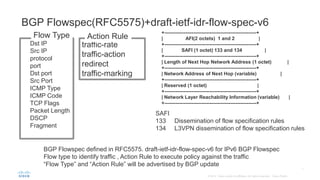
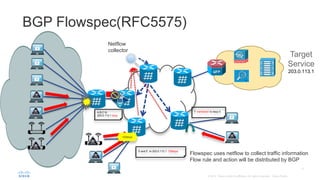
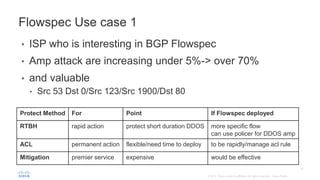
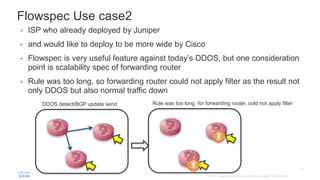
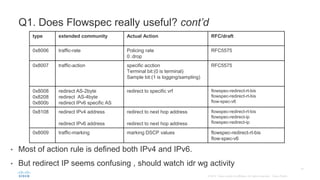
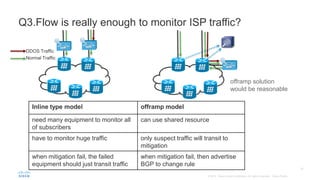
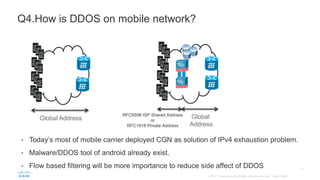
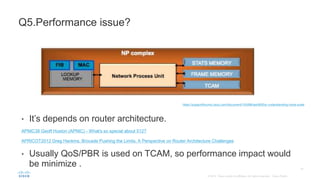
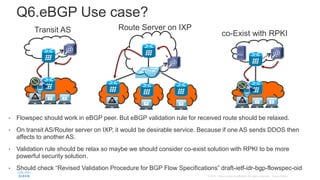
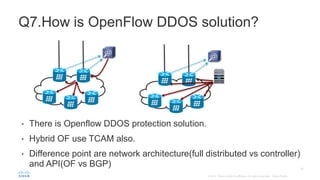
BGP Flowspec is a technique for distributing flow specification rules via BGP. It allows an ISP to dynamically distribute filtering and redirection rules to mitigate DDoS attacks. The document discusses several real-world use cases where BGP Flowspec was deployed to successfully block large DDoS attacks in a targeted manner without affecting legitimate traffic. However, interoperability between vendors and scalability challenges remain open issues requiring further work and testing.