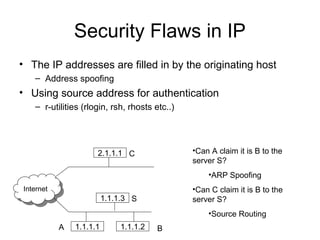
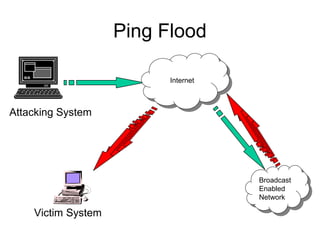
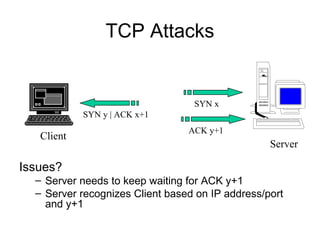
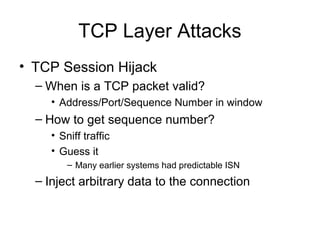
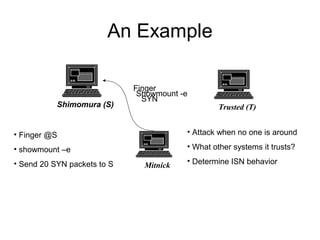
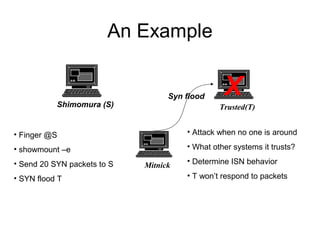
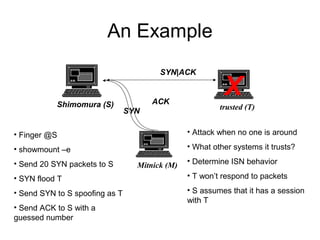
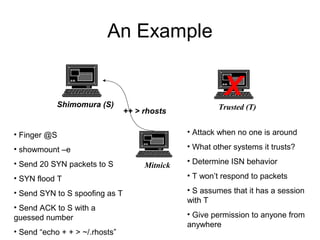
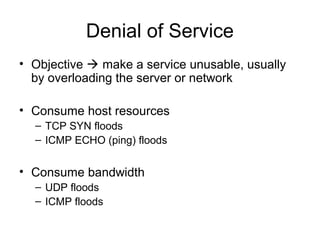
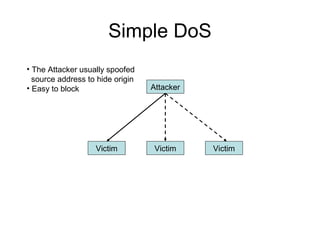
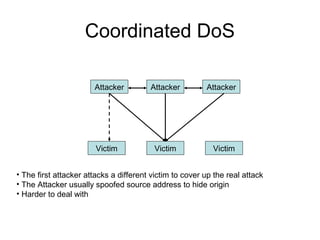
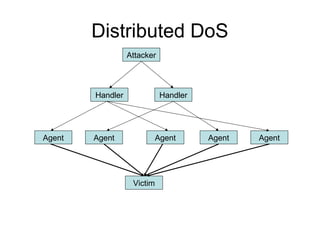
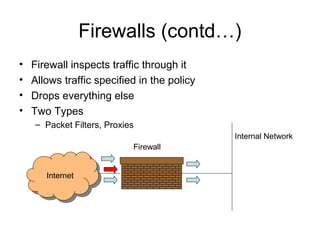
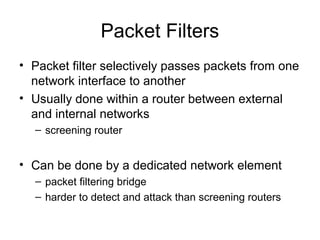
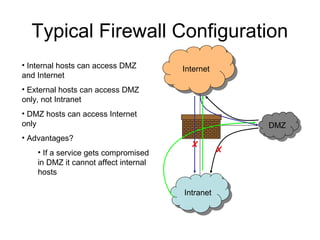
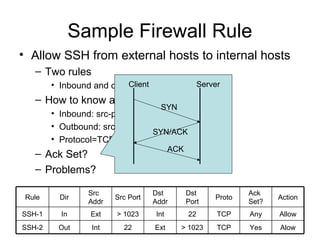
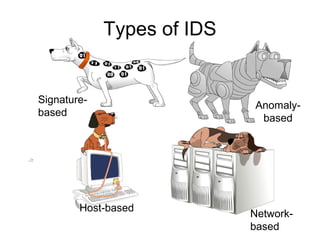
Network security vulnerabilities exist at various layers of the TCP/IP protocol suite. Firewalls and intrusion detection systems help mitigate these issues. Firewalls use packet filtering or proxies to restrict traffic according to security policies. Intrusion detection systems monitor network traffic or host activity for signs of attacks using signature-based or anomaly-based detection methods.