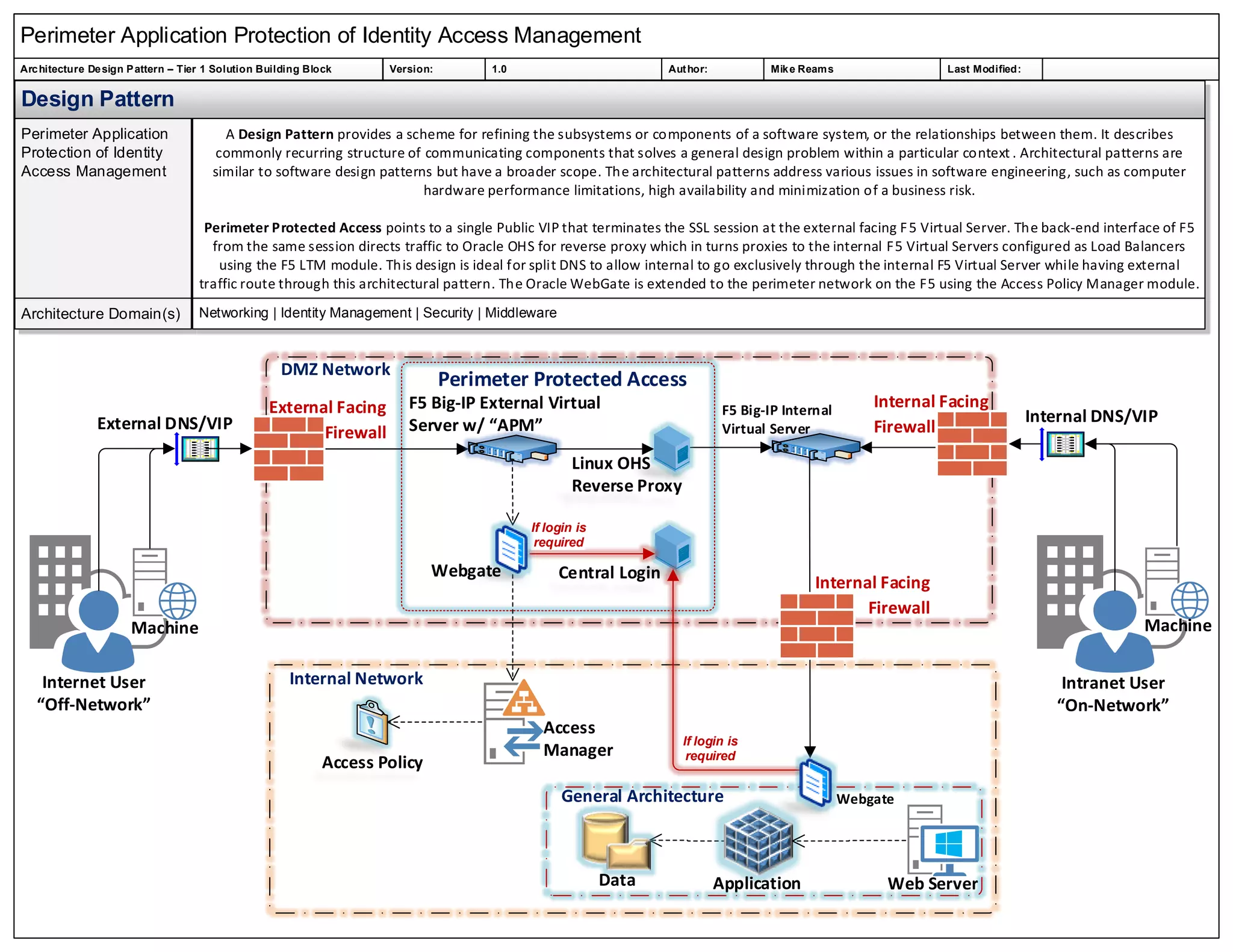
This document outlines the design pattern for perimeter application protection in identity access management architecture, focusing on tier 1 solutions. It describes the structure and components of the architectural pattern, which addresses challenges in software engineering like performance limitations and business risk minimization. The implementation involves SSL termination at F5 virtual servers with traffic directed to Oracle OHS for secure access management.