Mobile user single sign on flow
•
0 likes•280 views
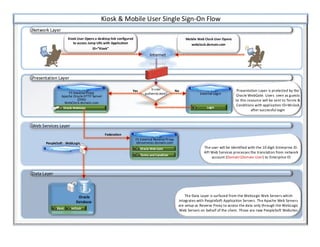
This document summarizes a single sign-on user flow for a kiosk and mobile web clock application. It involves multiple layers including a network layer, presentation layer, web services layer, and data layer. The presentation layer is protected by an Oracle WebGate that will send successfully authenticated users to terms and conditions for the web clock application. The user is identified by their 10-digit enterprise ID after translation from their network account by an API web service. The data is accessed from WebLogic application servers through a reverse proxy on Apache web servers.
Report
Share
Report
Share
Download to read offline
Recommended
Visio Diagram of a user SSO Flow

Demonstrates a user accessing an SSO provider from Portal as an authenticated/authorized user originating from the IdP
Sample Template for Single Sign-On (SSO)

Microsoft Visio Diagram for a user flow in an Identity management user SSO flow to a service provider originating from an Identity Provider
Design Pattern Logical Model

External Access points to a single Public VIP that terminates the TLS session at the external facing F5 Virtual Server. The back-end VLAN interface of F5 from the same session, forwards all TCP traffic to Oracle OHS for reverse proxy. - Which in turns communicates to the internal facing VLAN of the F5 Virtual Servers configured as Load Balancers using the F5 LTM module. The “APM” module uses the Oracle WebGate integration for access management
http://mikereams.com
TeraGrid's GRAM Auditing & Accounting, & its Integration with the LEAD Scienc...

I presented the few slides at the end about the LEAD project and integration with the GRAM auditing support.
A Detailed Guide to Securing React applications with Keycloak - WalkingTree ...

With KeyCloak you can setup multiple identity providers from existing social networks or setup user-defined authentication servers and use it to secure all your React applications with ease. In this blog, We elaborate on how to setup KeyCloak server, configure it with Google as its identity provider and use it to secure a simple React application.
Recommended
Visio Diagram of a user SSO Flow

Demonstrates a user accessing an SSO provider from Portal as an authenticated/authorized user originating from the IdP
Sample Template for Single Sign-On (SSO)

Microsoft Visio Diagram for a user flow in an Identity management user SSO flow to a service provider originating from an Identity Provider
Design Pattern Logical Model

External Access points to a single Public VIP that terminates the TLS session at the external facing F5 Virtual Server. The back-end VLAN interface of F5 from the same session, forwards all TCP traffic to Oracle OHS for reverse proxy. - Which in turns communicates to the internal facing VLAN of the F5 Virtual Servers configured as Load Balancers using the F5 LTM module. The “APM” module uses the Oracle WebGate integration for access management
http://mikereams.com
TeraGrid's GRAM Auditing & Accounting, & its Integration with the LEAD Scienc...

I presented the few slides at the end about the LEAD project and integration with the GRAM auditing support.
A Detailed Guide to Securing React applications with Keycloak - WalkingTree ...

With KeyCloak you can setup multiple identity providers from existing social networks or setup user-defined authentication servers and use it to secure all your React applications with ease. In this blog, We elaborate on how to setup KeyCloak server, configure it with Google as its identity provider and use it to secure a simple React application.
FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)

FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)
Web Services With Delphi, Sep, 2008

Describes the steps necessary to build web services (both server-side and client-side) in Delphi.
Share point 2013 add-in (formerly app) development

An Introduction to SharePoint 2013 Add-in (formerly App) Development
Offline Web with Oracle JET

Everyone is already familiar with the idea of distributed applications that continue to function in the face of intermittent network connectivity, but its only since the release of HTML5 that a solution for discontinuous network connectivity can be extended to web applications.
In this session Florin will demonstrate how Oracle JET can be utilised to build offline web modules that may cache within the browser’s local database when the server is out of reach and how these modules can be integrated with existing APEX or ADF applications.
Secure Code Warrior - Os command injection

OWASP Web App Top 10 - Slidepack on "OS Command Injection" by Secure Code Warrior Limited and licensed under CC BY-ND 4.0
What is an API?

Describe about what is an API, what kind of API web services, API methodologies and also which style that you should choose for your application.
CIS14: OAuth and OpenID Connect in Action

Chuck Mortimore, Salesforcce.com
Setup and walk-through of live demos, demonstrating interop of various providers and showing real enterprise use-cases.
SharePoint 2010 Client Object Model

Discussion on the new features of the Client Object Model (Client OM) in SharePoint 2010.
Presented at SharePoint Saturday Richmond 11/18/2009
Presented at SharePoint Saturday Virginia Beach 1/13/2010
Presented at SharePoint Saturday Boston 2/27/2009
Open Id, O Auth And Webservices

This presentation was given at Web Directions South in 2008. It is a developers guide to building sites using OpenID, OAuth and webservices - no code, but enough to point you in the right direction
Solution Delivery Calendar

Visio diagram of a project delivery timeline of tasks needed to support identity management deployments. It’s a clean way of visually communicating out the deployment strategy and plan. I used Microsoft Visio 2013 using the out-of-the-box templates for Timeline Shapes.
More Related Content
What's hot
FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)

FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)
Web Services With Delphi, Sep, 2008

Describes the steps necessary to build web services (both server-side and client-side) in Delphi.
Share point 2013 add-in (formerly app) development

An Introduction to SharePoint 2013 Add-in (formerly App) Development
Offline Web with Oracle JET

Everyone is already familiar with the idea of distributed applications that continue to function in the face of intermittent network connectivity, but its only since the release of HTML5 that a solution for discontinuous network connectivity can be extended to web applications.
In this session Florin will demonstrate how Oracle JET can be utilised to build offline web modules that may cache within the browser’s local database when the server is out of reach and how these modules can be integrated with existing APEX or ADF applications.
Secure Code Warrior - Os command injection

OWASP Web App Top 10 - Slidepack on "OS Command Injection" by Secure Code Warrior Limited and licensed under CC BY-ND 4.0
What is an API?

Describe about what is an API, what kind of API web services, API methodologies and also which style that you should choose for your application.
CIS14: OAuth and OpenID Connect in Action

Chuck Mortimore, Salesforcce.com
Setup and walk-through of live demos, demonstrating interop of various providers and showing real enterprise use-cases.
SharePoint 2010 Client Object Model

Discussion on the new features of the Client Object Model (Client OM) in SharePoint 2010.
Presented at SharePoint Saturday Richmond 11/18/2009
Presented at SharePoint Saturday Virginia Beach 1/13/2010
Presented at SharePoint Saturday Boston 2/27/2009
Open Id, O Auth And Webservices

This presentation was given at Web Directions South in 2008. It is a developers guide to building sites using OpenID, OAuth and webservices - no code, but enough to point you in the right direction
What's hot (20)
Protecting your APIs with Doorkeeper and OAuth 2.0

Protecting your APIs with Doorkeeper and OAuth 2.0
FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)

FI-WARE OAUTH-XACML-based API Access Control - Overview (Part 1)
Share point 2013 add-in (formerly app) development

Share point 2013 add-in (formerly app) development
Viewers also liked
Solution Delivery Calendar

Visio diagram of a project delivery timeline of tasks needed to support identity management deployments. It’s a clean way of visually communicating out the deployment strategy and plan. I used Microsoft Visio 2013 using the out-of-the-box templates for Timeline Shapes.
Environment Gap Analysis for Applications

Brainstorming diagram in Microsoft Visio 2013 for asking questions in determining environment gaps for applications
Design Pattern for Federated Single Sign-On Access

A Design Pattern provides a scheme for refining the subsystems or components of a software system, or the relationships between them
How Technology has changed the Architecture? (Mobile Apps Only) �

How Technology has changed the Architecture?
(Mobile Apps Only)
�
Visio Diagram Scripting and Server Management flow

Sample Visio Diagram of managing a server and a process to follow
Design Pattern for Oracle Identity Provisioning

Architecture Design pattern for how to manage person data in an Identity ecosystem. Supports a TOGAF framework for establishing Building Blocks.
Reference:
Design Pattern Library http://solventarchitect.com/design-patterns
High-level Architecture viewpoint of a Troux Infrastructure

A Visio Diagram of a High-level Architecture viewpoint of a Troux Infrastructure for 2 companies using a common platform
Perimeter Protected Access Design Pattern

Design pattern called "Perimeter Application Protection of Identity Access Management" describes the general pattern for following securing applications with external access
Software is not a Building - Designing Technical Architecture for Change

In this presentation, we talk about the symptoms that make software hard to change and remedies to cure them. Topics like tension between patterns in modern, rapid development frameworks and the patterns and practices used to keep software malleable are discussed.
Slides by David Fox, Director of Technical Design
Viewers also liked (18)
Design Pattern for Federated Single Sign-On Access

Design Pattern for Federated Single Sign-On Access
How Technology has changed the Architecture? (Mobile Apps Only) �

How Technology has changed the Architecture? (Mobile Apps Only) �
Visio Diagram Scripting and Server Management flow

Visio Diagram Scripting and Server Management flow
High-level Architecture viewpoint of a Troux Infrastructure

High-level Architecture viewpoint of a Troux Infrastructure
Get Started the server side Swift on server less OpenWhisk

Get Started the server side Swift on server less OpenWhisk
hp_reference_architecture_for_mapr_m7_on_hp_proliant_sl45401

hp_reference_architecture_for_mapr_m7_on_hp_proliant_sl45401
Software is not a Building - Designing Technical Architecture for Change

Software is not a Building - Designing Technical Architecture for Change
Similar to Mobile user single sign on flow
Series of Visual Flow Diagrams

Series of Microsoft Visio Diagrams for various workflows such as SSO, scripting, Application architecture, Business Use Case
Introduction to the Client OM in SharePoint 2010

This session was presented by Ben Robb and Eric Shupps at the SharePoint Evolution Conference in London, in April 2010.
SSO With APEX and ADFS the weblogic way

My presentation for the juli 2019 UK OUG Southern Tech Summit
Extending Oracle SSO

With a complete new Identity/Access Management Suite on the Oracle market,
one might forget the good old SSO server, bundled with each and every IAS server.
Although it has some out-of-the-box capabilities like WNA and X509 certificate support,
it can be quite hard to set up an authentication scheme just the way you (or your customers) like it.
Using a case study, this presentation discusses how you can extend Oracle’s Single
Sign On (SSO) server to your needs. It will discuss :
- Integration & authentication with smartcard passports (eID)
- Authentication with digital certificates
- Implementing fallback authentication schemes
- Integration with SSL terminators and reverse proxies
- DIY federated authentication
- writing your own SSO plugin
The solutions presented are part of AXI NV/BV's portfolio.
Intro to web api with dynamics 365

Microsoft Dynamics 365.Intro to web API with Dynamics 365. Web API is a new Web Service end-point available to access data and metadata. Web API provides a platform-agnostic development experience which can be used across a wide variety of programming languages, platforms, and devices.
Oracle World 2002 Leverage Web Services in E-Business Applications

OracleWorld 2002 Session 32781
Leverage Oracle9iAS Web Services In E-Business Applications
20180605 sso with apex and adfs the weblogic way

Explanation on how to implement SAML2 based SSO for Apex with ADFS as an IdentityProvider and leveraging the Weblogic authenticators.
Microsoft Graph API Delegated Permissions

Slidedeck presented during a webinar i held on13th December 2023 about how to consume Microsoft Graph API using user level permissions.
Webinar Recording https://youtu.be/2cSsg5ws1H4
SharePoint Connector – Setup and Configuration

Adobe’s SharePoint Connector exposes content via the standard JCR interface, enabling applications to access content that resides in a proprietary repository in a standardized manner, thus, simplifying access to content. This presentation provides step-by-step guidelines on how to setup and configure a Share Connector with CQ/AEM (5.6.0). Watch the on-demand webinar: http://adobe.ly/1ffzutV.
Oracle APEX Social Login

Presentation on using Social Login based on OAuth 2.0 with Oracle APEX, this includes a demonstration on how to configure Facebook, Google and LinkedIn to be used for authentication with APEX.
This presentation was given as a webinar as part of the Oracle APEX Office Hours series:
https://asktom.oracle.com/pls/apex/f?p=100:551:::NO:551:P551_CLASS_ID:744:
Skype for business mobility

The Skype for Business (Lync) apps are one of the ubiquitous aspect of the product. Mobility is cross platform (Android, IOS and Windows are supported), has specific requirements and (in Skype for Business) adds some specific limits for clients on authentication, security and features. As part of the default server features, mobility is now both easier and more critical to understand. In this session, we will see what has been made available for the mobile users and what will be released. Configurations, requirements and deployment suggestions will be explained for on-premises, Cloud and hybrid deployments
Similar to Mobile user single sign on flow (20)
Oracle World 2002 Leverage Web Services in E-Business Applications

Oracle World 2002 Leverage Web Services in E-Business Applications
Recently uploaded
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Presented by Suzanne Phillips and Alex Marcotte
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

As AI technology is pushing into IT I was wondering myself, as an “infrastructure container kubernetes guy”, how get this fancy AI technology get managed from an infrastructure operational view? Is it possible to apply our lovely cloud native principals as well? What benefit’s both technologies could bring to each other?
Let me take this questions and provide you a short journey through existing deployment models and use cases for AI software. On practical examples, we discuss what cloud/on-premise strategy we may need for applying it to our own infrastructure to get it to work from an enterprise perspective. I want to give an overview about infrastructure requirements and technologies, what could be beneficial or limiting your AI use cases in an enterprise environment. An interactive Demo will give you some insides, what approaches I got already working for real.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
UiPath Test Automation using UiPath Test Suite series, part 3

Welcome to UiPath Test Automation using UiPath Test Suite series part 3. In this session, we will cover desktop automation along with UI automation.
Topics covered:
UI automation Introduction,
UI automation Sample
Desktop automation flow
Pradeep Chinnala, Senior Consultant Automation Developer @WonderBotz and UiPath MVP
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
Knowledge engineering: from people to machines and back

Keynote at the 21st European Semantic Web Conference
Recently uploaded (20)
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024

Kubernetes & AI - Beauty and the Beast !?! @KCD Istanbul 2024
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
UiPath Test Automation using UiPath Test Suite series, part 3

UiPath Test Automation using UiPath Test Suite series, part 3
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
Knowledge engineering: from people to machines and back

Knowledge engineering: from people to machines and back
Mobile user single sign on flow
- 1. Internet Network Layer Presentation Layer Web Services Layer F5-External Reverse Proxy Idmservices.domain.com Oracle Web Gate External Login Login Is user authenticated? Data Layer F5 Reverse Proxy Apache Oracle HTTP Server (OHS) WebClock.domain.com Oracle WebGate Presentation Layer is protected by the Oracle WebGate. Users seen as guests to this resource will be sent to Terms & Conditions with application ID=Wclock after successful login The user will be identified with the 10 digit Enterprise ID. API Web Services processes the translation from network account (DomainDomain User) to Enterprise ID The Data Layer is surfaced from the WebLogic Web Servers which integrates with PeopleSoft Application Servers. The Apache Web Servers are setup as Reverse Proxy to access the data only through the WebLogic Web Servers on behalf of the client. These are new PeopleSoft Websites Oracle Database Kiosk PeopleSoft - WebLogic Mobile Web Clock User Opens webclock.domain.com Kiosk User Opens a desktop link configured to access Jump URL with Application ID=”Kiosk” Terms and Condition mClock Kiosk & Mobile User Single Sign-On Flow Yes No Federation
