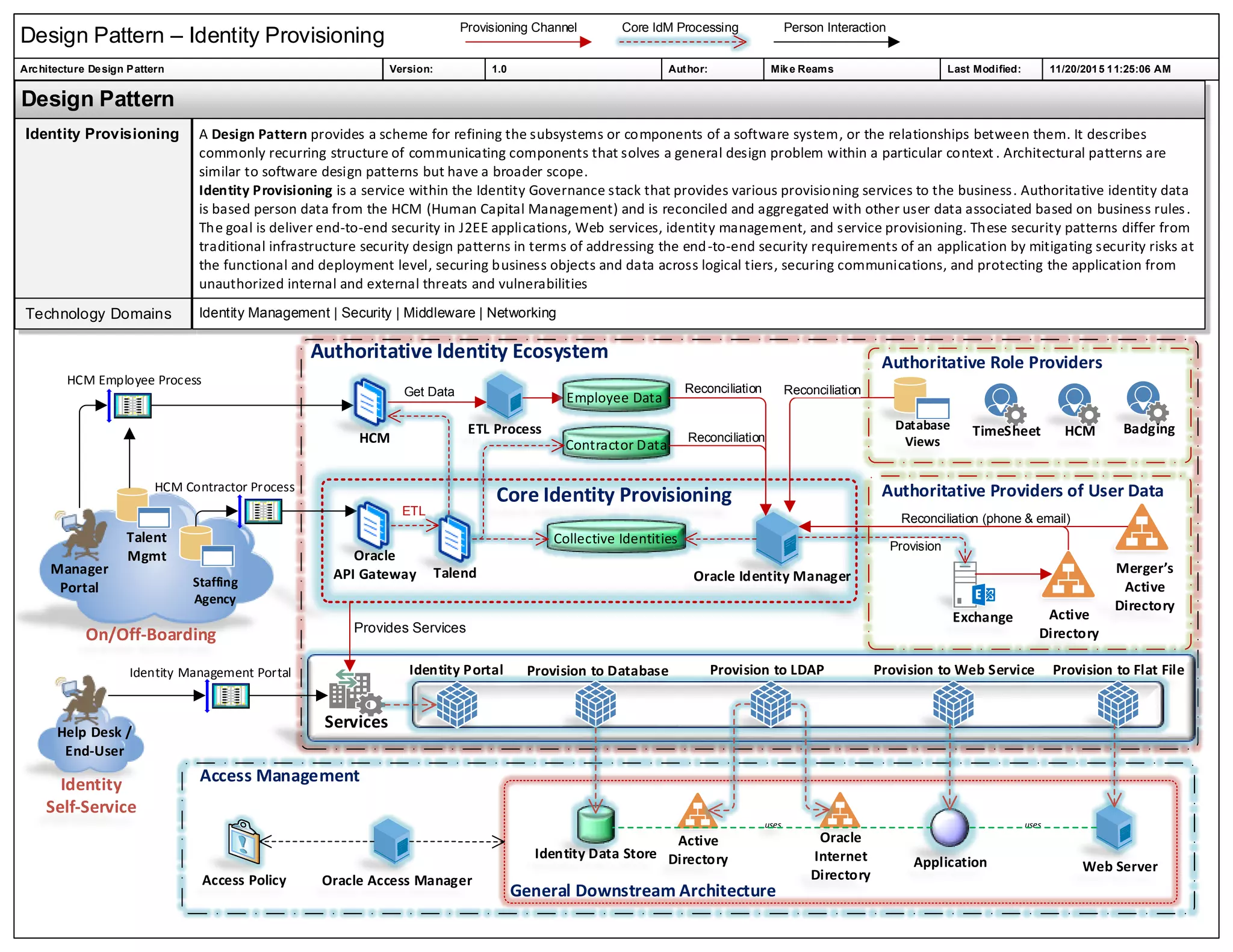
The document outlines a design pattern for identity provisioning architecture, detailing the architecture's role in providing security services within identity governance systems. It emphasizes the need for end-to-end security in applications while addressing risks related to communications, unauthorized access, and data management. Additionally, it describes the interactions and components involved in identity management, including various data sources and processes for reconciliation.