Embed presentation
Downloaded 65 times
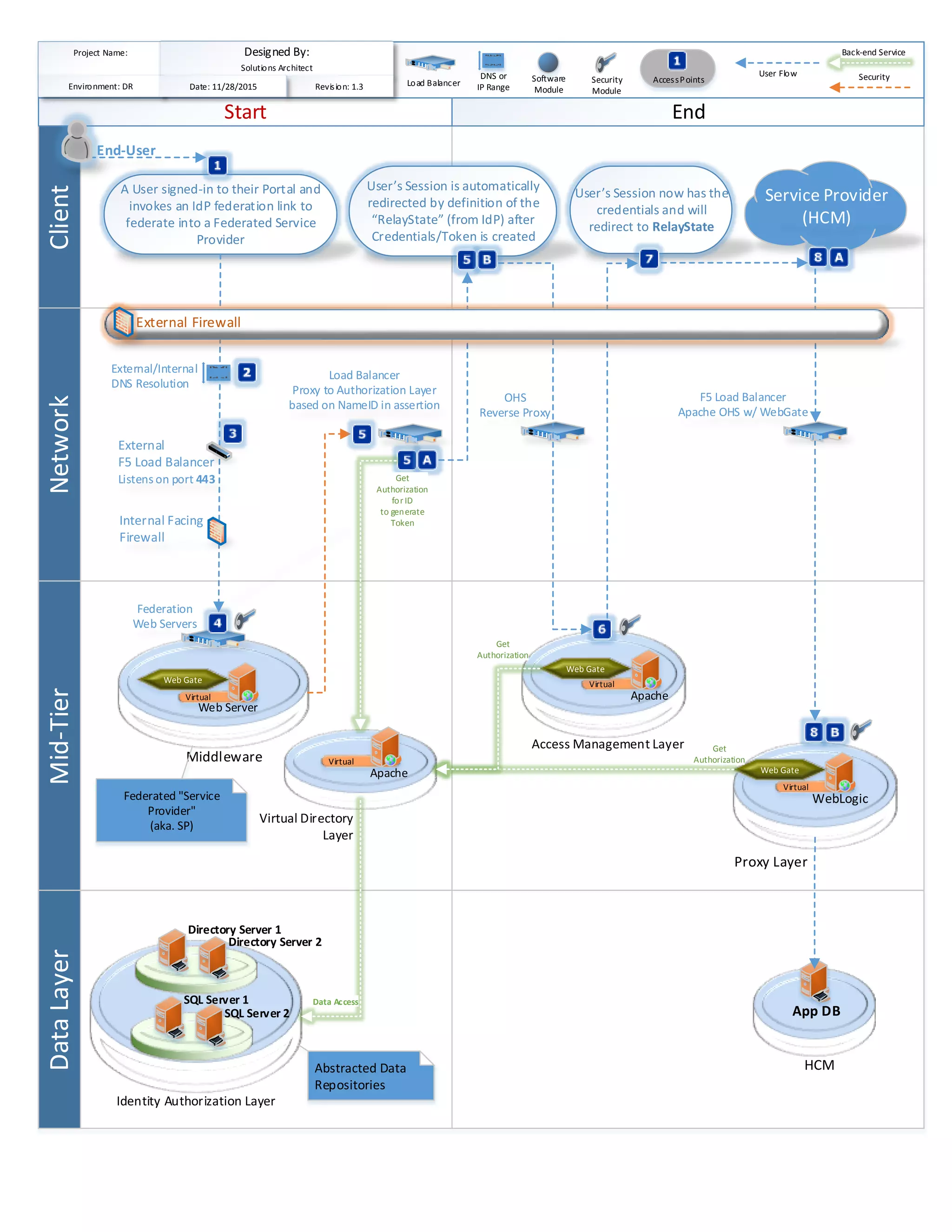

The document outlines a technical architecture involving a client network, mid-tier data layer, and various components such as web servers and load balancers for federating user identities and authorization processes. It specifies the flow of user authentication through an identity provider (IdP) and security modules managing access to a web application environment. Key elements include relay state management, external/internal DNS resolution, and the integration of directory and SQL servers for data access.
