Design Pattern Logical Model
•
2 likes•404 views
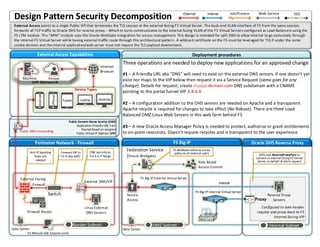
External Access points to a single Public VIP that terminates the TLS session at the external facing F5 Virtual Server. The back-end VLAN interface of F5 from the same session, forwards all TCP traffic to Oracle OHS for reverse proxy. - Which in turns communicates to the internal facing VLAN of the F5 Virtual Servers configured as Load Balancers using the F5 LTM module. The “APM” module uses the Oracle WebGate integration for access management http://mikereams.com
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (19)
How to Create Observable Integration Solutions Using WSO2 Enterprise Integrator

How to Create Observable Integration Solutions Using WSO2 Enterprise Integrator
(ATS6-DEV04) Building Web MashUp applications that include Accelrys Applicati...

(ATS6-DEV04) Building Web MashUp applications that include Accelrys Applicati...
Troubleshooting and Best Practices with WSO2 Enterprise Integrator

Troubleshooting and Best Practices with WSO2 Enterprise Integrator
Viewers also liked
Viewers also liked (16)
Where is the “C” in health systems strengthening by Dr Alfonso Rosales, WVUS

Where is the “C” in health systems strengthening by Dr Alfonso Rosales, WVUS
How Technology has changed the Architecture? (Mobile Apps Only) �

How Technology has changed the Architecture? (Mobile Apps Only) �
Similar to Design Pattern Logical Model
SFSCON23 - Andrea Avancini Michele Santuari Alberto Sillitti - A comparison o...

SFSCON23 - Andrea Avancini Michele Santuari Alberto Sillitti - A comparison o...South Tyrol Free Software Conference
Similar to Design Pattern Logical Model (20)
FTP Client Buildup1. IntroductionThe project is related to bui

FTP Client Buildup1. IntroductionThe project is related to bui
2008-10-14 Managing your Red Hat Enterprise Linux guests with RHN Satellite

2008-10-14 Managing your Red Hat Enterprise Linux guests with RHN Satellite
VMworld 2013: vCloud Hybrid Service Jump Start Part Two of Five: vCloud Hybri...

VMworld 2013: vCloud Hybrid Service Jump Start Part Two of Five: vCloud Hybri...
2009-08-24 Managing your Red Hat Enterprise Linux Guests with RHN Satellite

2009-08-24 Managing your Red Hat Enterprise Linux Guests with RHN Satellite
Realizing the True Potential of On-Demand IT: Enterprise Cloud Architectures

Realizing the True Potential of On-Demand IT: Enterprise Cloud Architectures
SFSCON23 - Andrea Avancini Michele Santuari Alberto Sillitti - A comparison o...

SFSCON23 - Andrea Avancini Michele Santuari Alberto Sillitti - A comparison o...
Oracle Enterprise Manager - EM12c R5 Hybrid Cloud Management

Oracle Enterprise Manager - EM12c R5 Hybrid Cloud Management
Migrate Heroku & OpenShift Applications to IBM BlueMix

Migrate Heroku & OpenShift Applications to IBM BlueMix
More from Mike Reams
More from Mike Reams (13)
Knowledge Transfer Training Presentation for Identity Lifecycle Manager

Knowledge Transfer Training Presentation for Identity Lifecycle Manager
Design Pattern for Federated Single Sign-On Access

Design Pattern for Federated Single Sign-On Access
High-level Architecture viewpoint of a Troux Infrastructure

High-level Architecture viewpoint of a Troux Infrastructure
Visio Diagram Scripting and Server Management flow

Visio Diagram Scripting and Server Management flow
Visual representation as an architectural artifact

Visual representation as an architectural artifact
Recently uploaded
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptxnull - The Open Security Community
Recently uploaded (20)
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service

WhatsApp 9892124323 ✓Call Girls In Kalyan ( Mumbai ) secure service
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx

Making_way_through_DLL_hollowing_inspite_of_CFG_by_Debjeet Banerjee.pptx
Snow Chain-Integrated Tire for a Safe Drive on Winter Roads

Snow Chain-Integrated Tire for a Safe Drive on Winter Roads
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
How to Remove Document Management Hurdles with X-Docs?

How to Remove Document Management Hurdles with X-Docs?
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Design Pattern Logical Model
- 1. Deployment procedures Three operations are needed to deploy new applications for an approved change #1 – A Friendly URL aka “DNS” will need to exist on the external DNS servers. If one doesn’t yet exist nor maps to the VIP below then request it via a Service Request (same goes for any change). Details for request; create myapp.domain.com DNS subdomain with a CNAME pointing to the portal funnel VIP X.X.X.X #2 – A configuration addition to the OHS servers are needed on Apache and a transparent Apache recycle is required for changes to take effect (No Reboot). There are three Load Balanced DMZ Linux Web Servers in this web farm behind F5 #3 – A new Oracle Access Manager Policy is needed to protect, authorize or grant entitlements to on-prem resources. Doesn’t require recycles and is transparent to the user experience Public Domain Name Service (DNS) Application Friendly URL’s are Routed Based on assigned Public Virtual IP Address (VIP) Public DNS Forwarding External Access points to a single Public VIP that terminates the TLS session at the external facing F5 Virtual Server. The back-end VLAN interface of F5 from the same session, forwards all TCP traffic to Oracle OHS for reverse proxy. - Which in turns communicates to the internal facing VLAN of the F5 Virtual Servers configured as Load Balancers using the F5 LTM module. The “APM” module uses the Oracle WebGate integration for access management. This design is intended for split DNS to allow internal to go exclusively through the internal F5 Virtual Server while having external traffic route through this architectural pattern. A wildcard certificate on the F5 must be leveraged for TLS if under the same cookie domain and the internal application/web server must not require the TLS payload downstream. Oracle OHS Reverse ProxyF5 Big-IPPerimeter Network - Firewall External Access Capabilities Machine External DNS/VIP Person iPhone Laptop DesktopTablet Android F5 Big-IP External Virtual Server Border Subnet Secure Access DMZ Subnet Data Center Device Types Internet Browser Linux External DNS ServersFirewall Router 15 Minute Idle Session Limit Design Pattern Security Decomposition Anti-IP Spoofing Rules are needed External Facing Firewall Forward VIP to F5 IP (No NAT) DNS useonly an X.X.X.X IP Range Configured to take header request and proxy back to F5 Internal facing VIP Switch Data Center Reverse Proxy Servers Internal Proxy F5 Big-IP Internal Virtual Server External Internal Job/Process Web Service SSO Internal Subnet Federation Service (Oracle Webgate) Web Farm Role Based Access Control F5 WebGate enforces access policy to all external users OHS uses ReverseProxyPass to connect to internal facing F5 Virtual Server on behalf of client request
