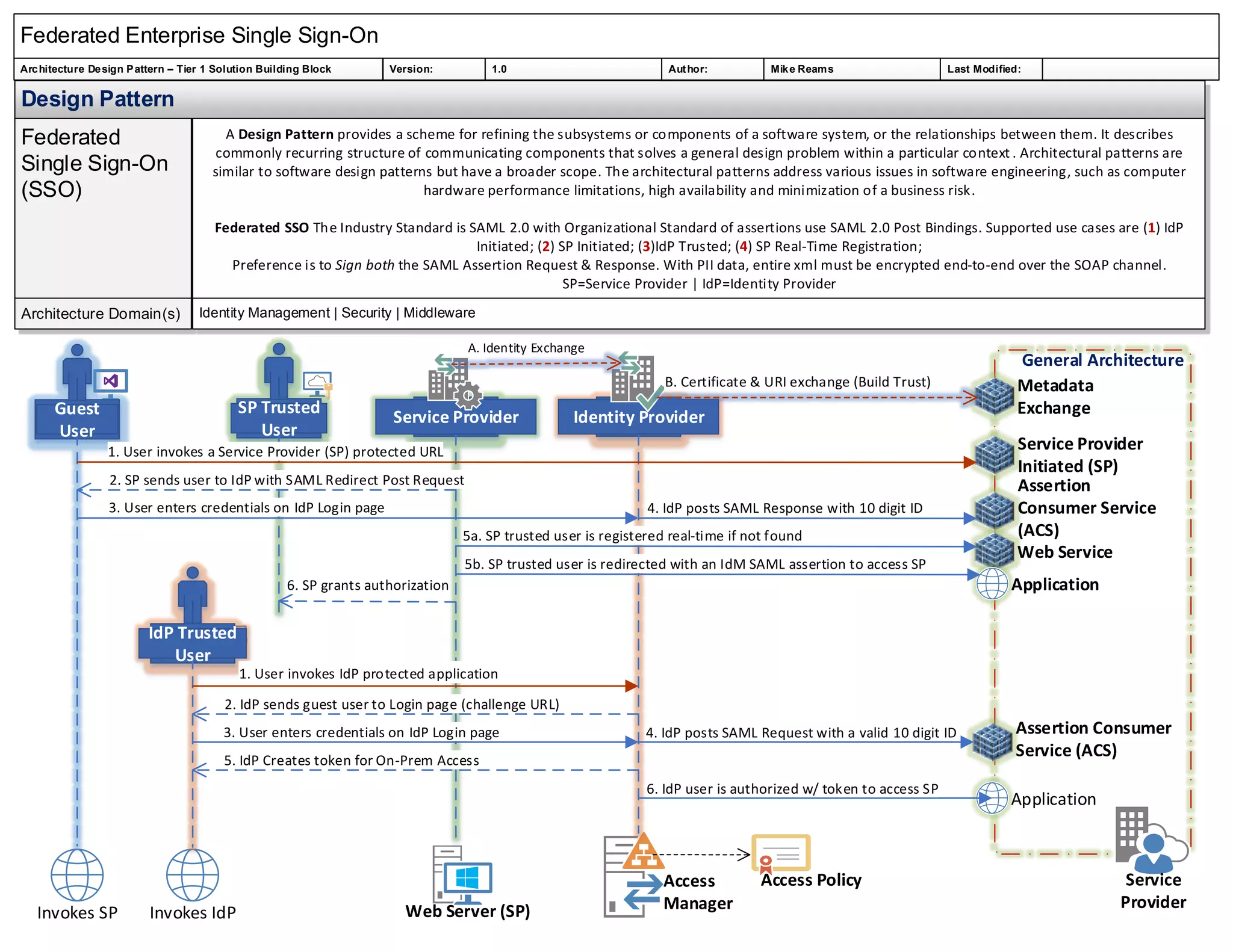
The document outlines the federated enterprise single sign-on (SSO) architecture design pattern, detailing components and their interactions in a software system. It emphasizes the use of SAML 2.0 as the industry standard for federated SSO and describes supported use cases, security measures, and the architecture involving identity and service providers. Key processes such as identity exchange, authorization, and real-time registration are also summarized.