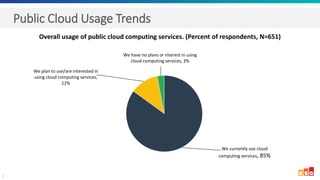
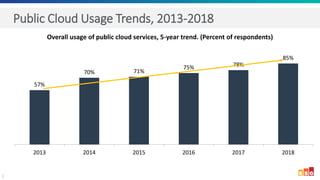
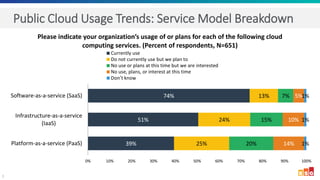
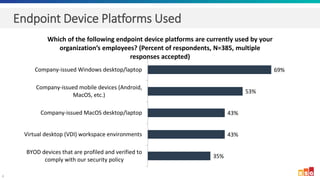
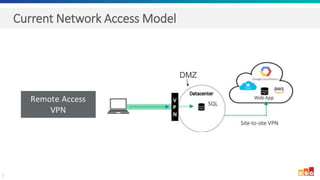
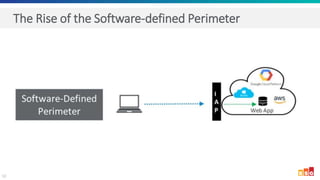
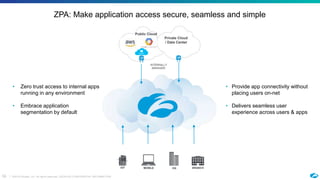
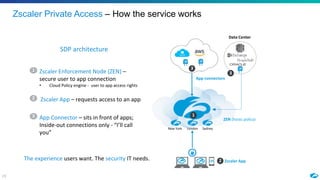
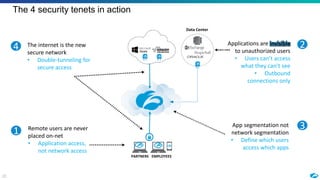
The document discusses the increasing adoption of public cloud services and the need for secure access models, highlighting the role of Software-Defined Perimeters (SDPs) in achieving zero trust security. It emphasizes that modern organizations are transitioning away from traditional VPNs to SDPs for improved security, visibility, and application segmentation. Real-world use cases showcase the effectiveness of Zscaler's SDP solutions in enhancing security and simplifying access for remote users across various industries.