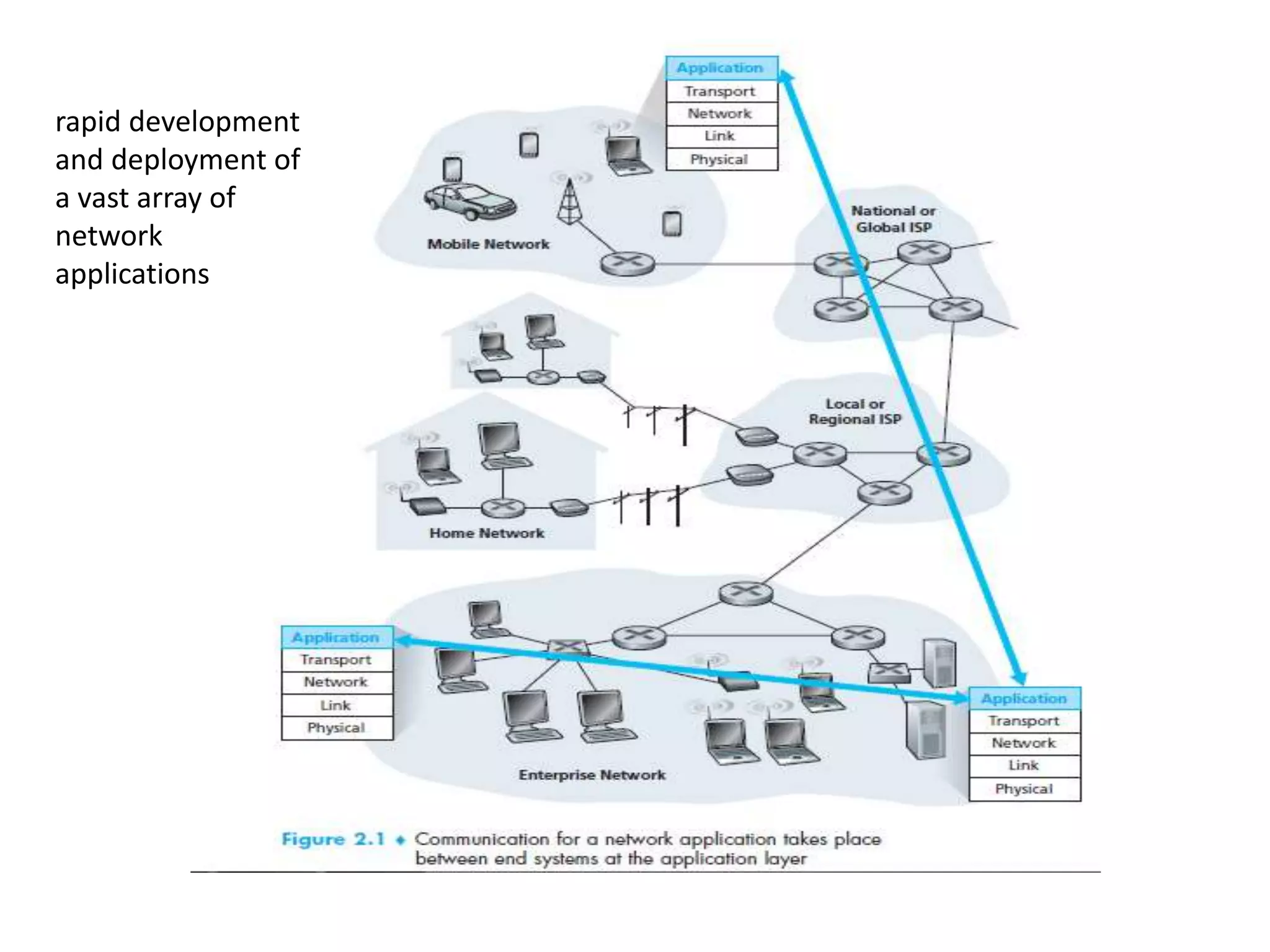
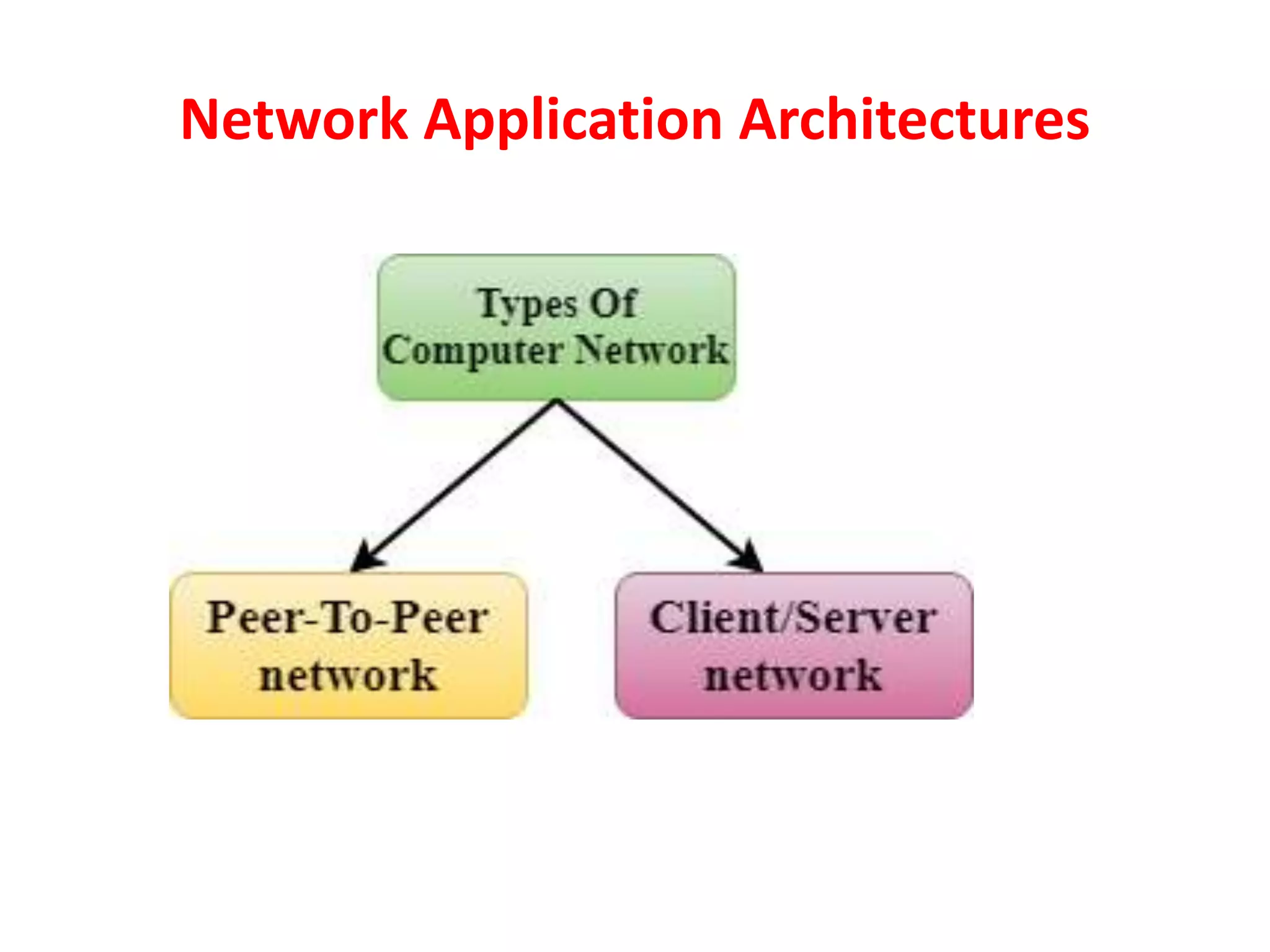
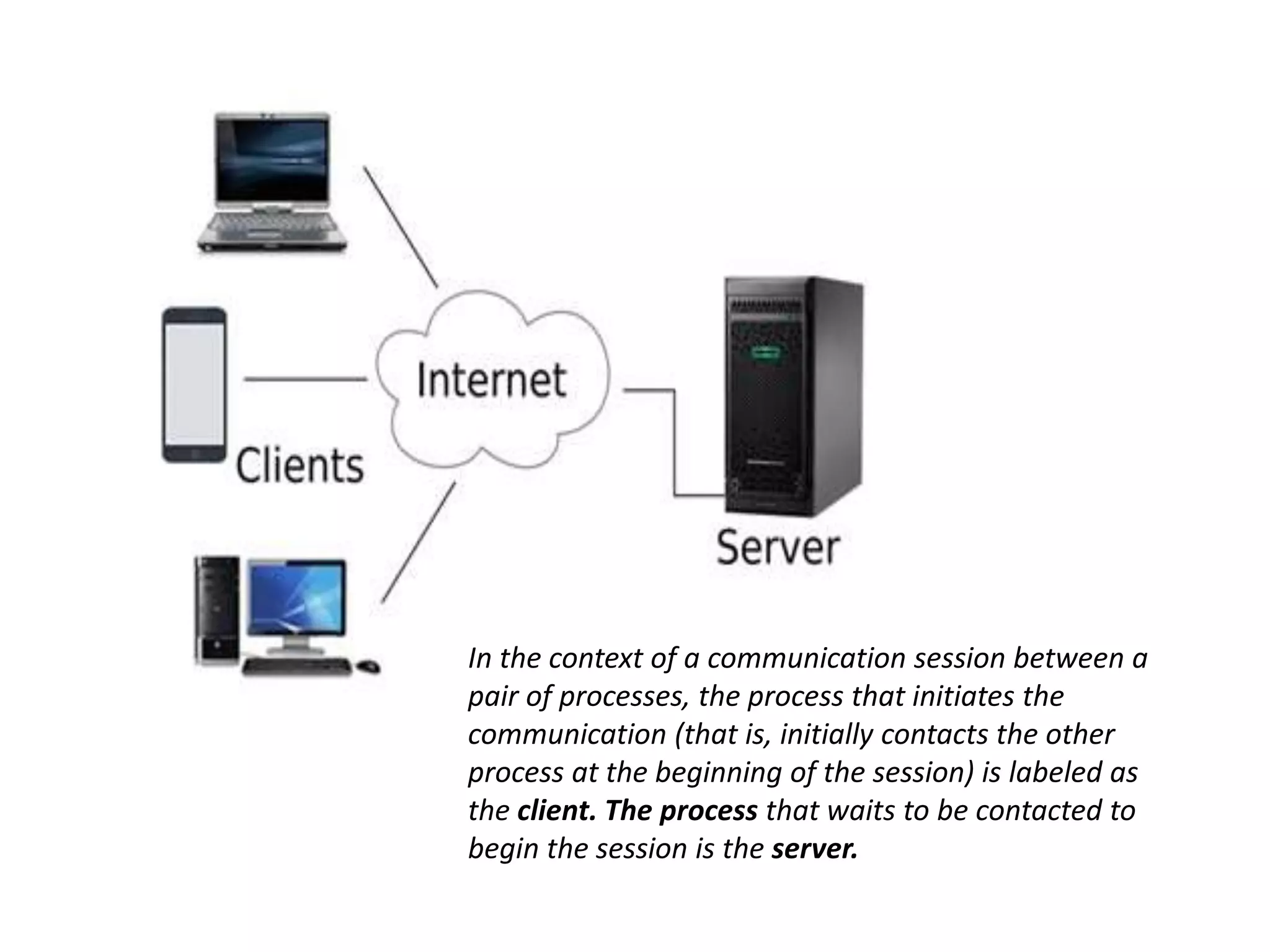
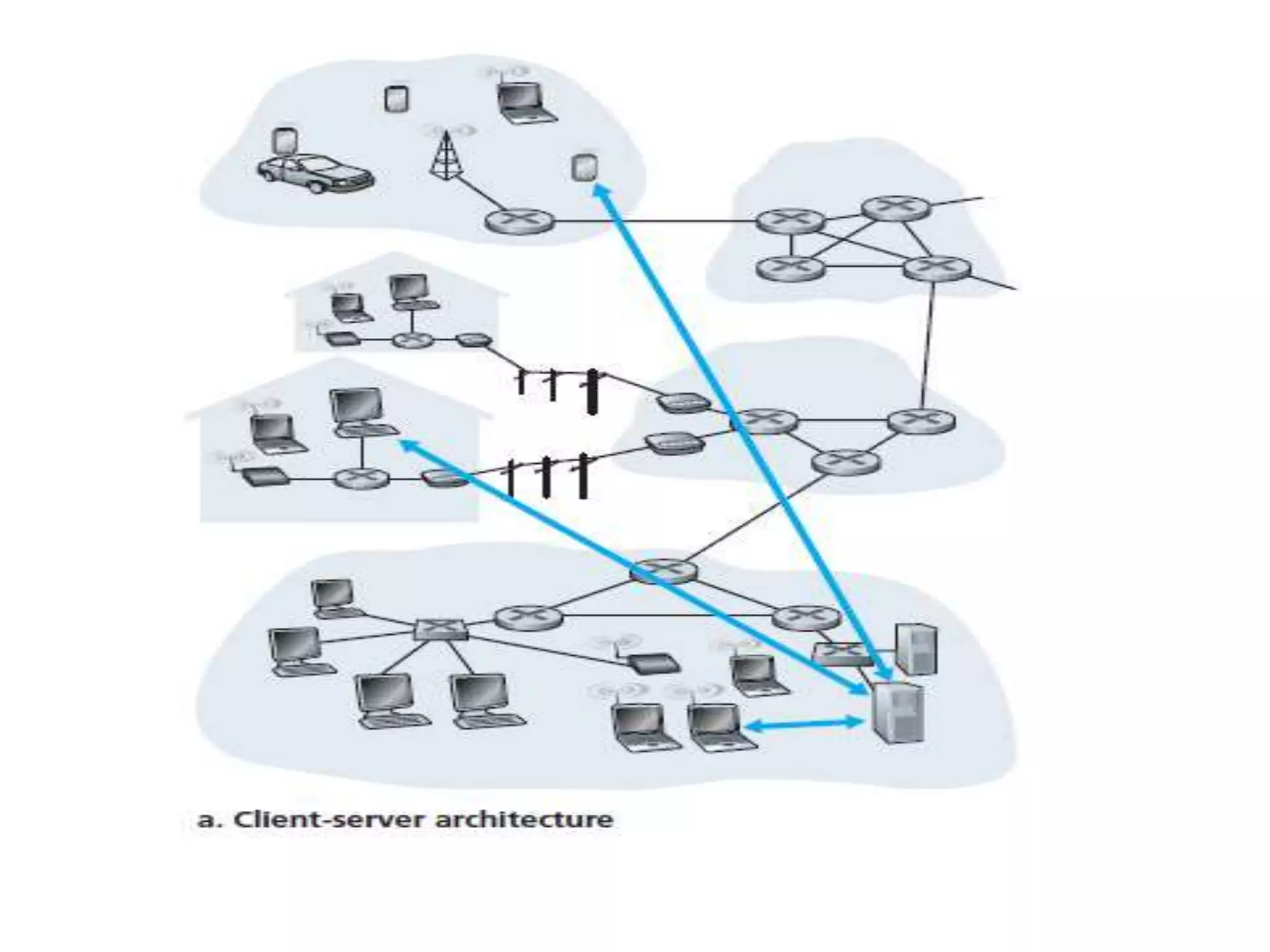
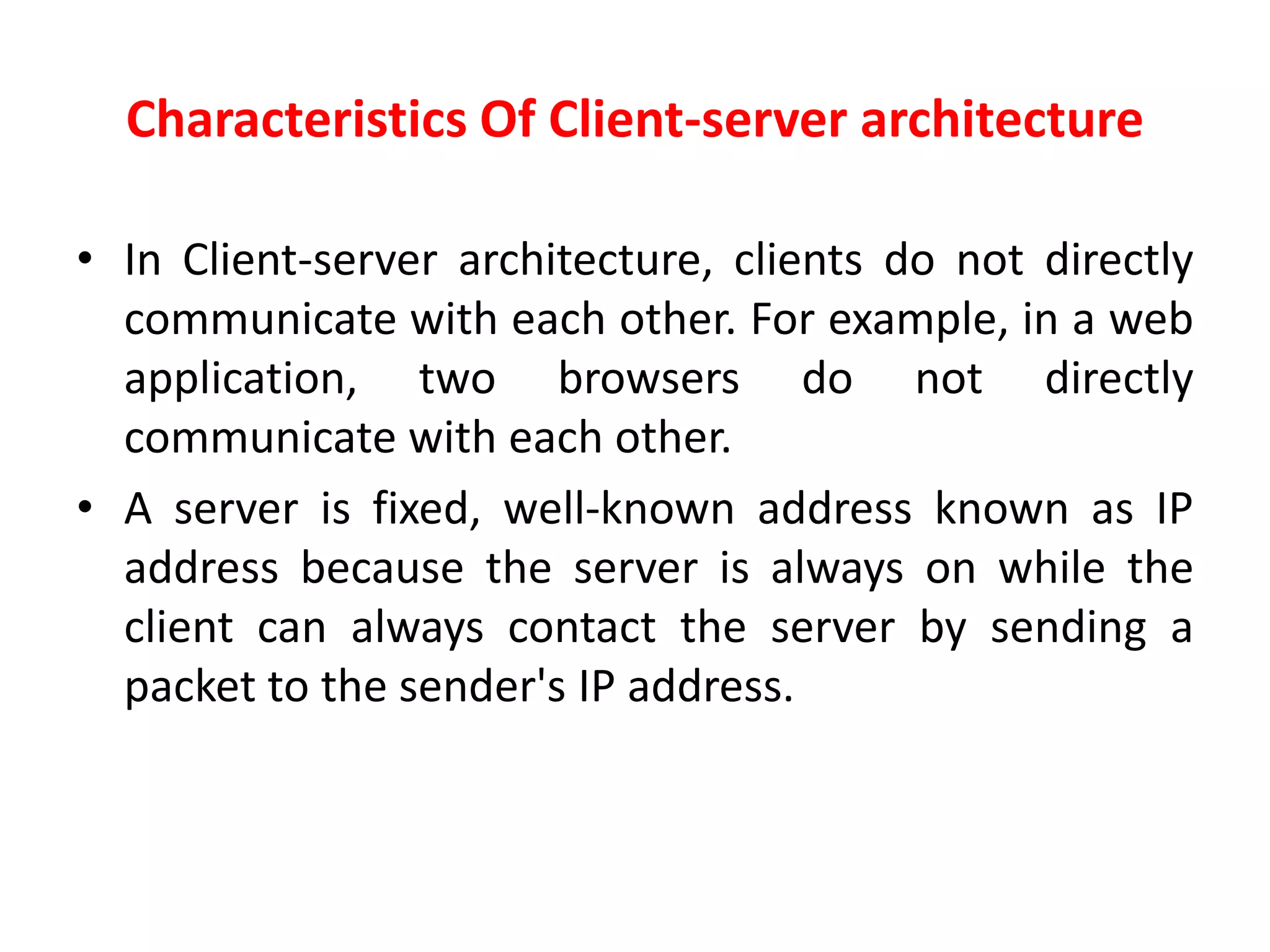
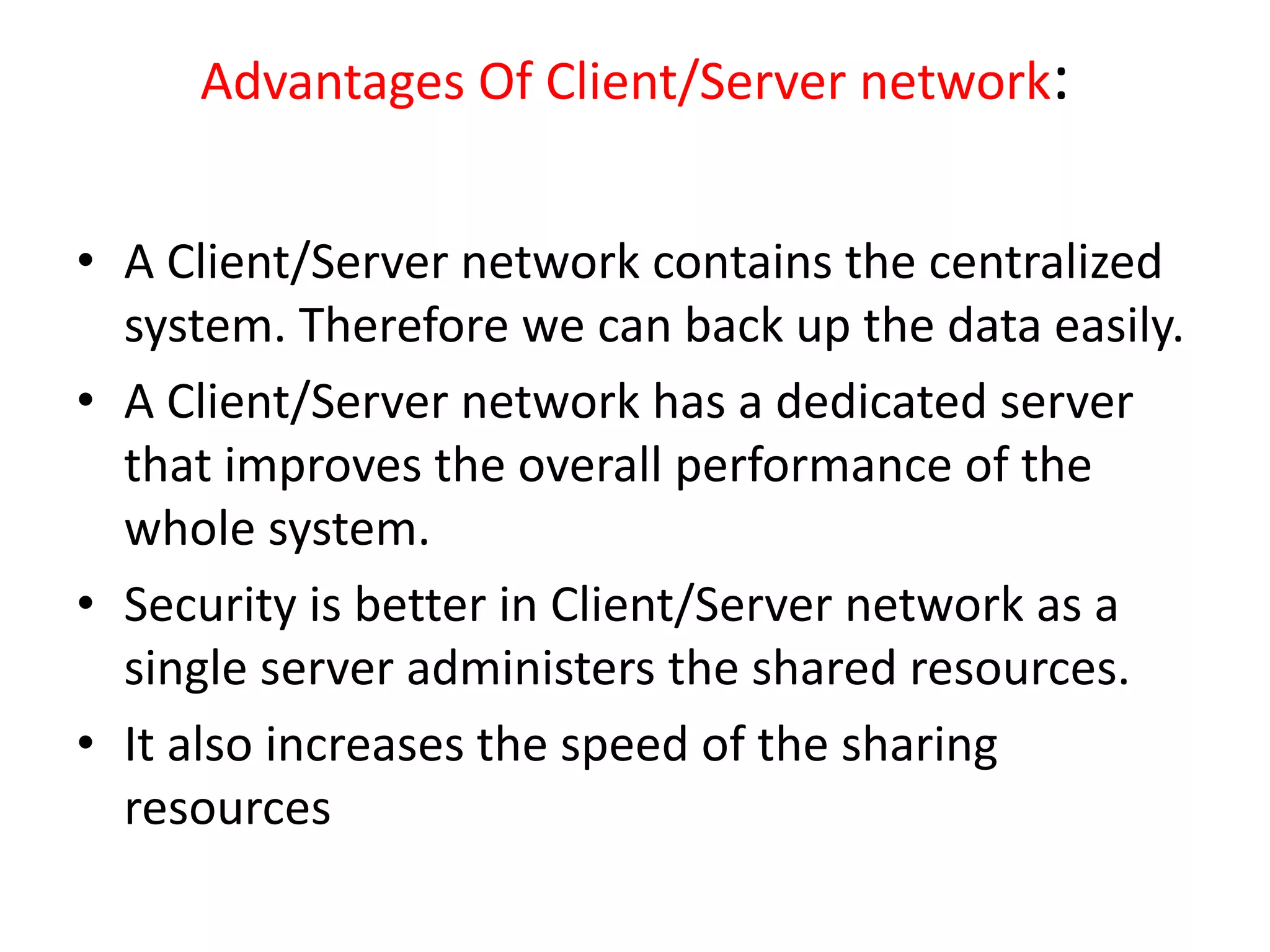
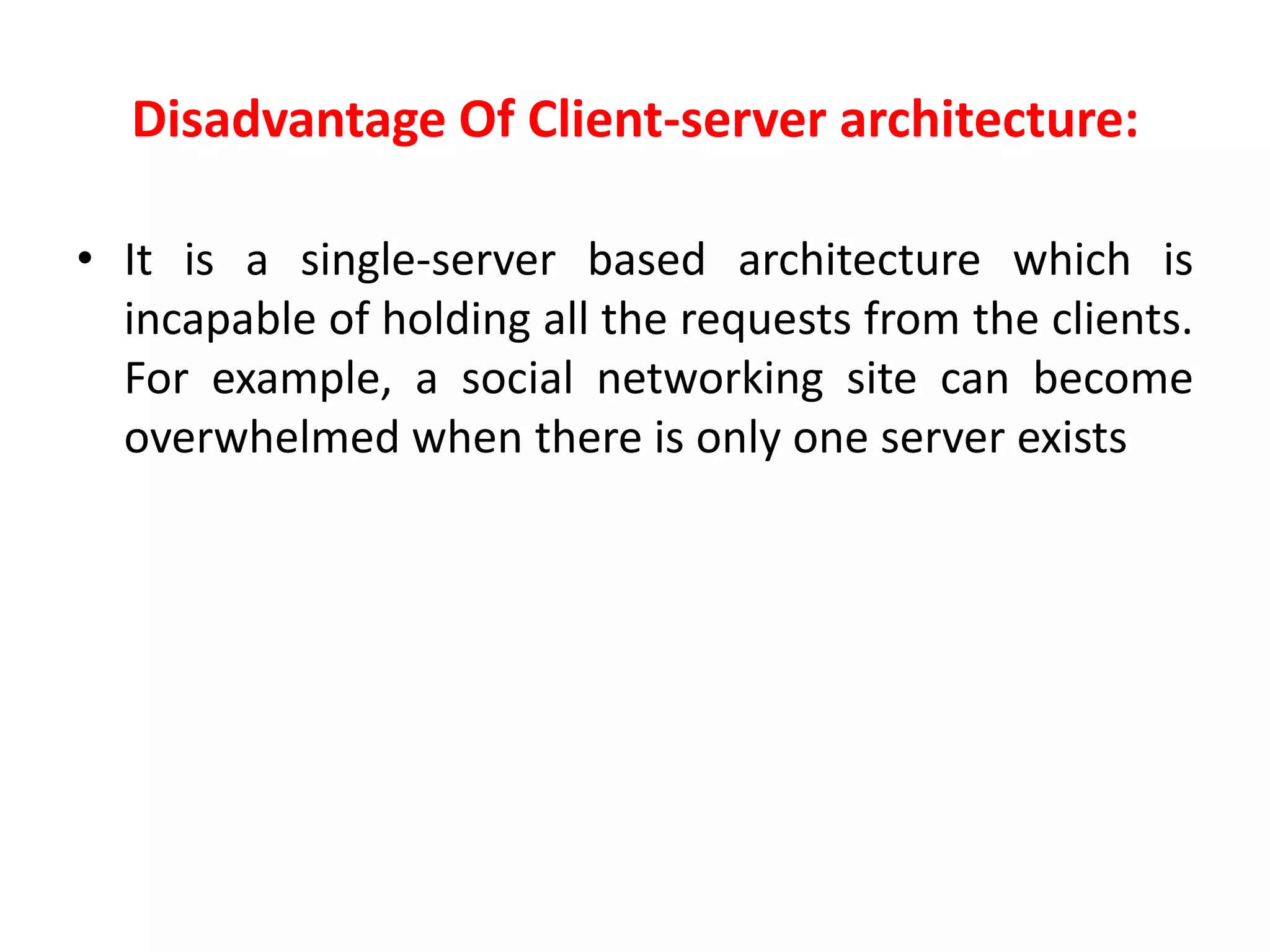
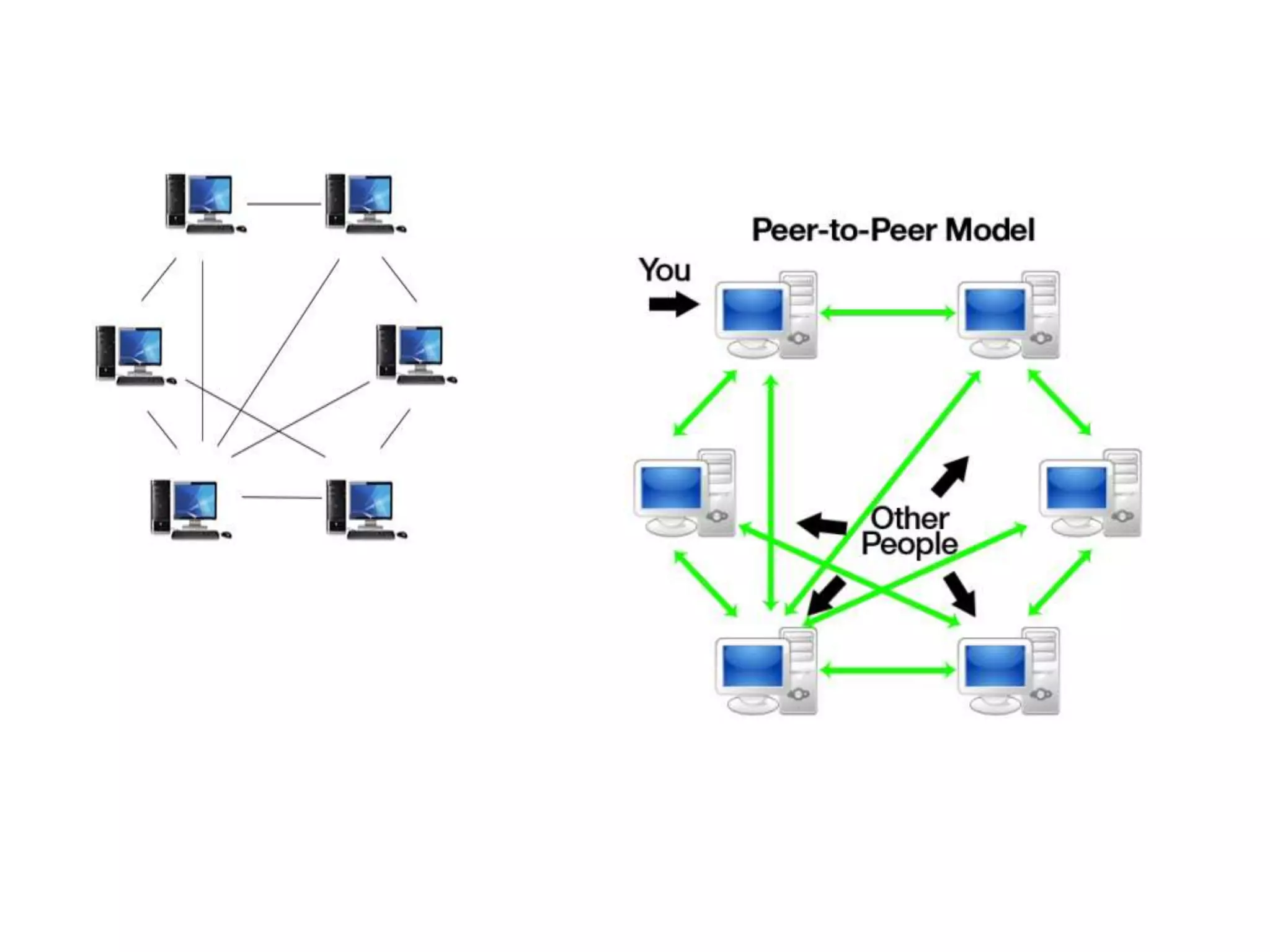
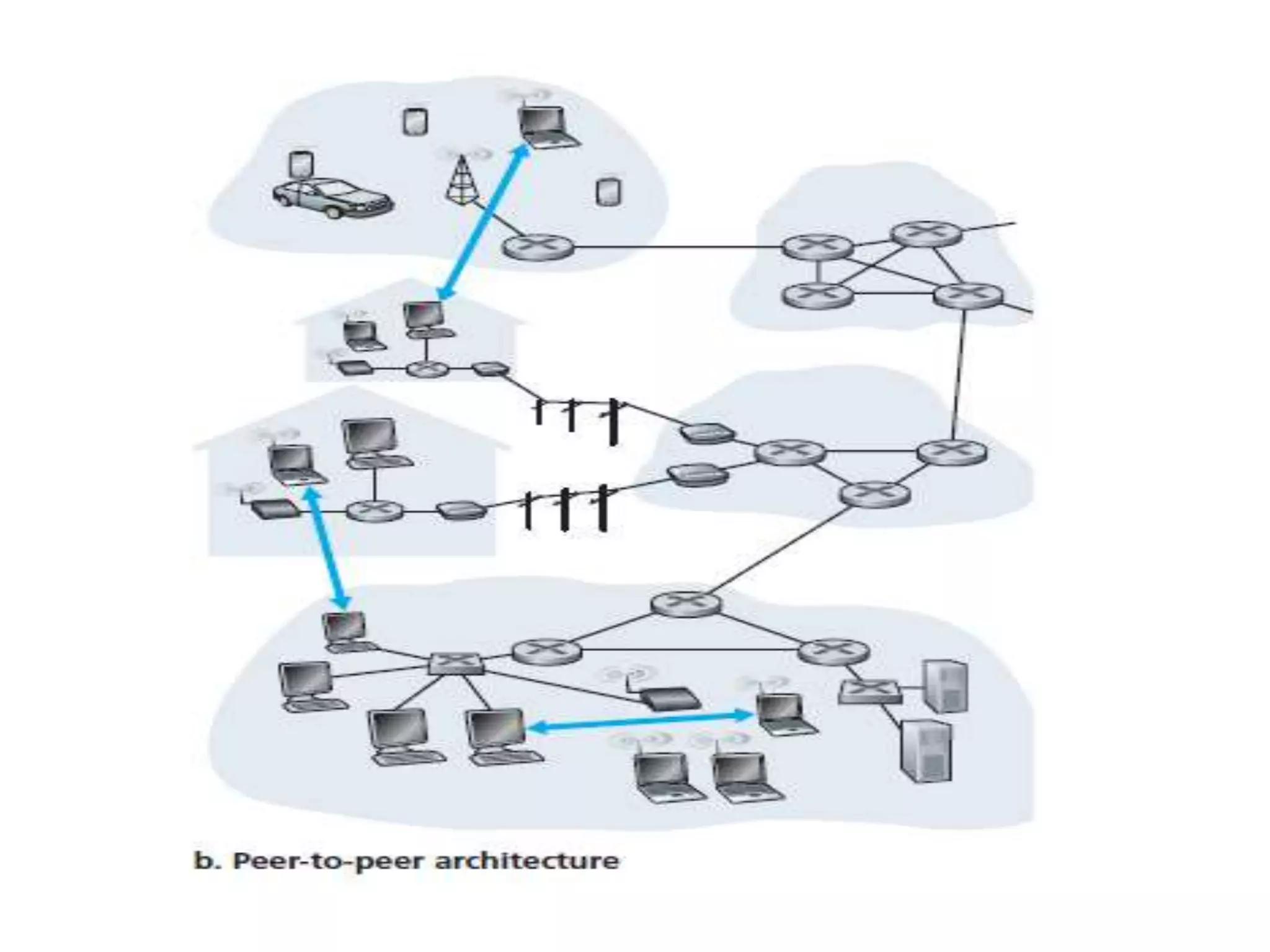
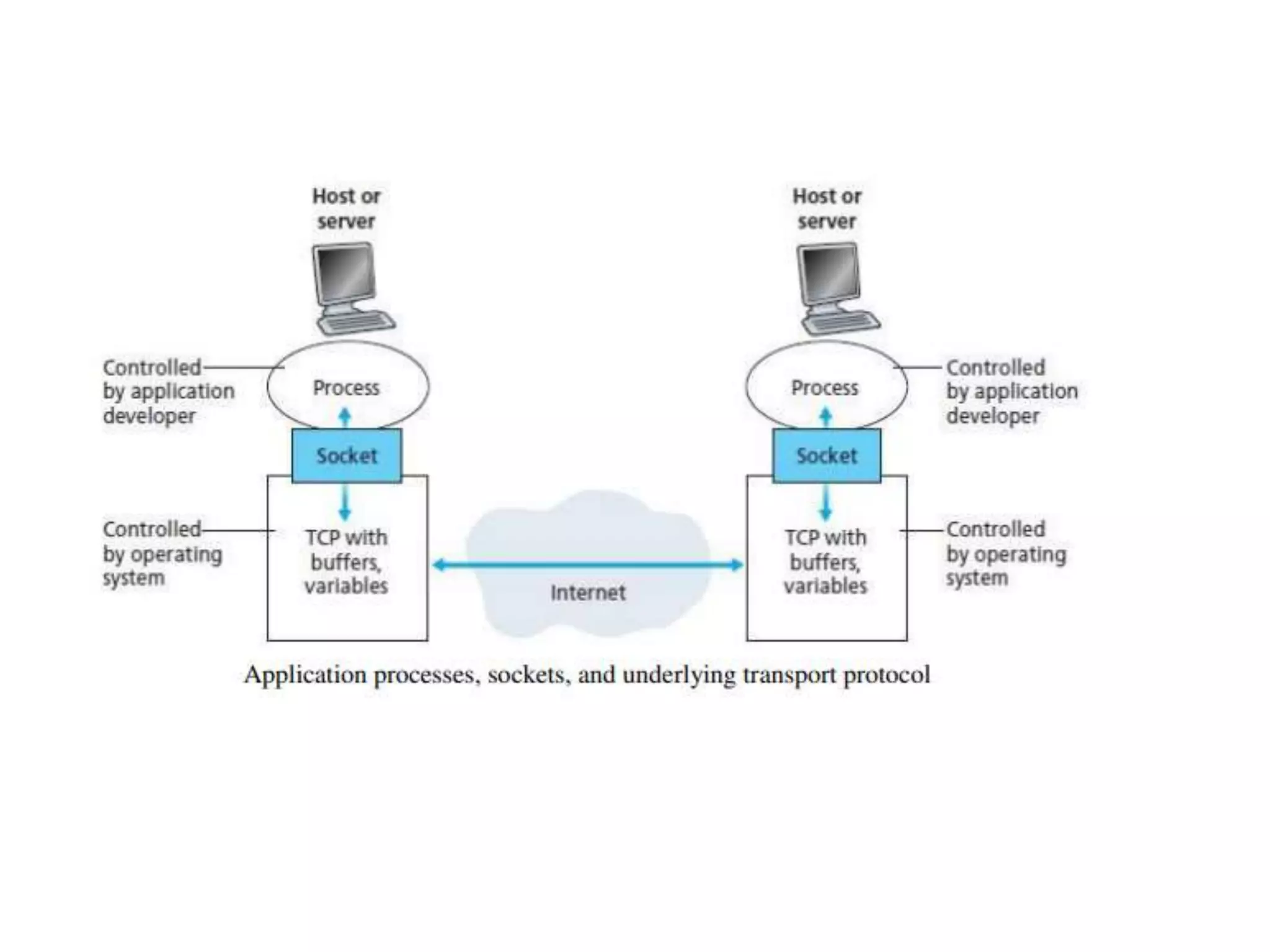
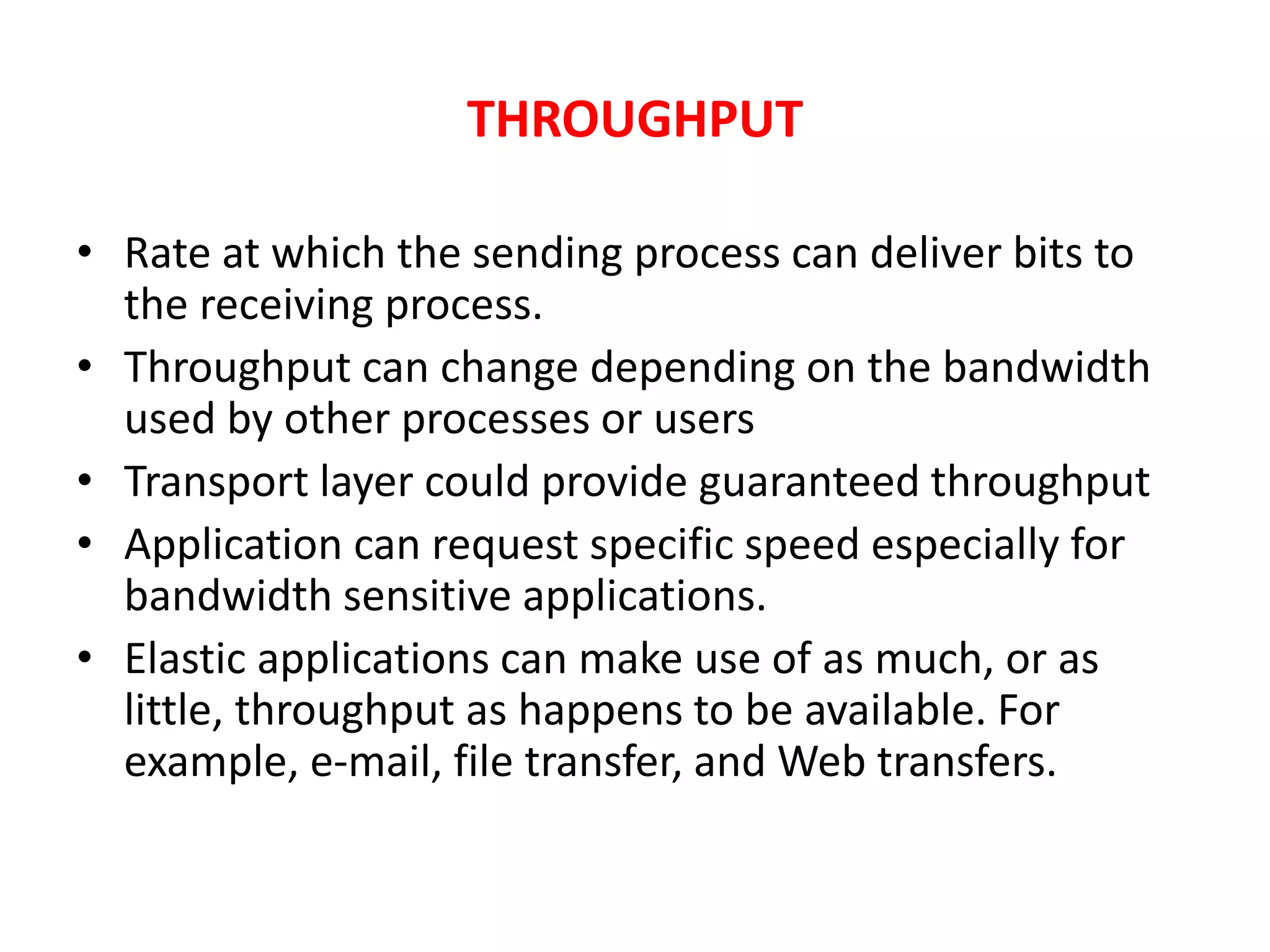
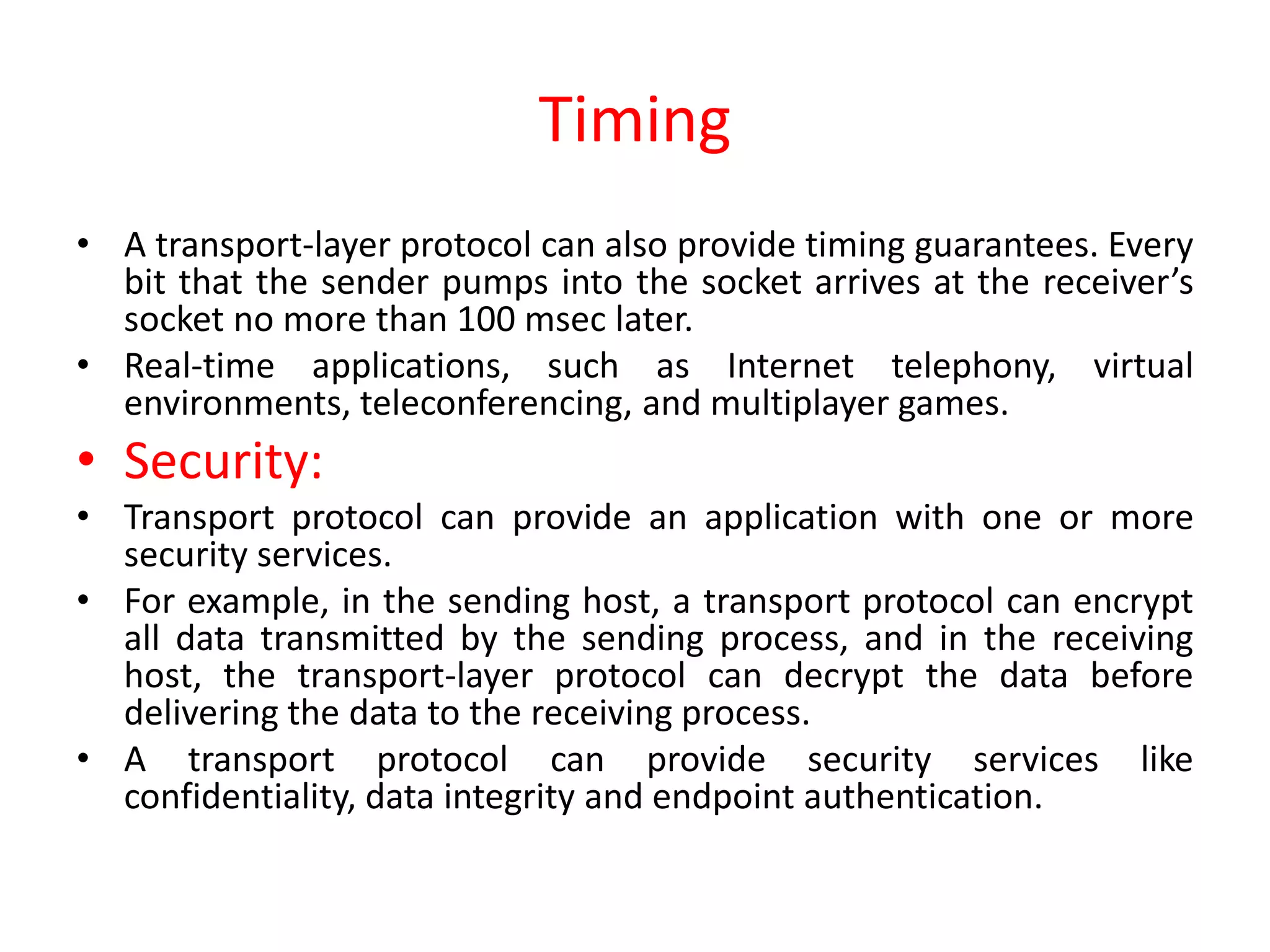
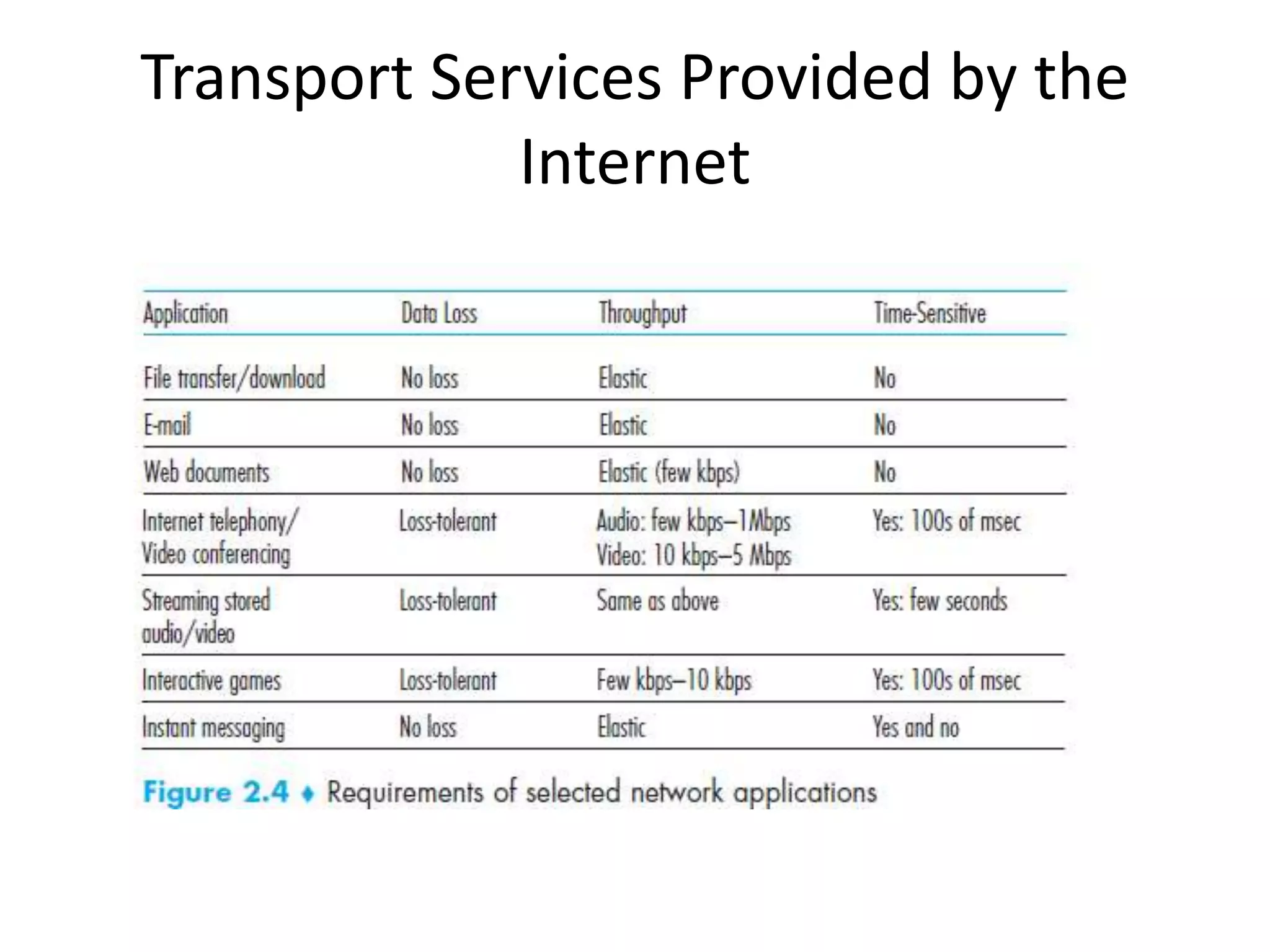
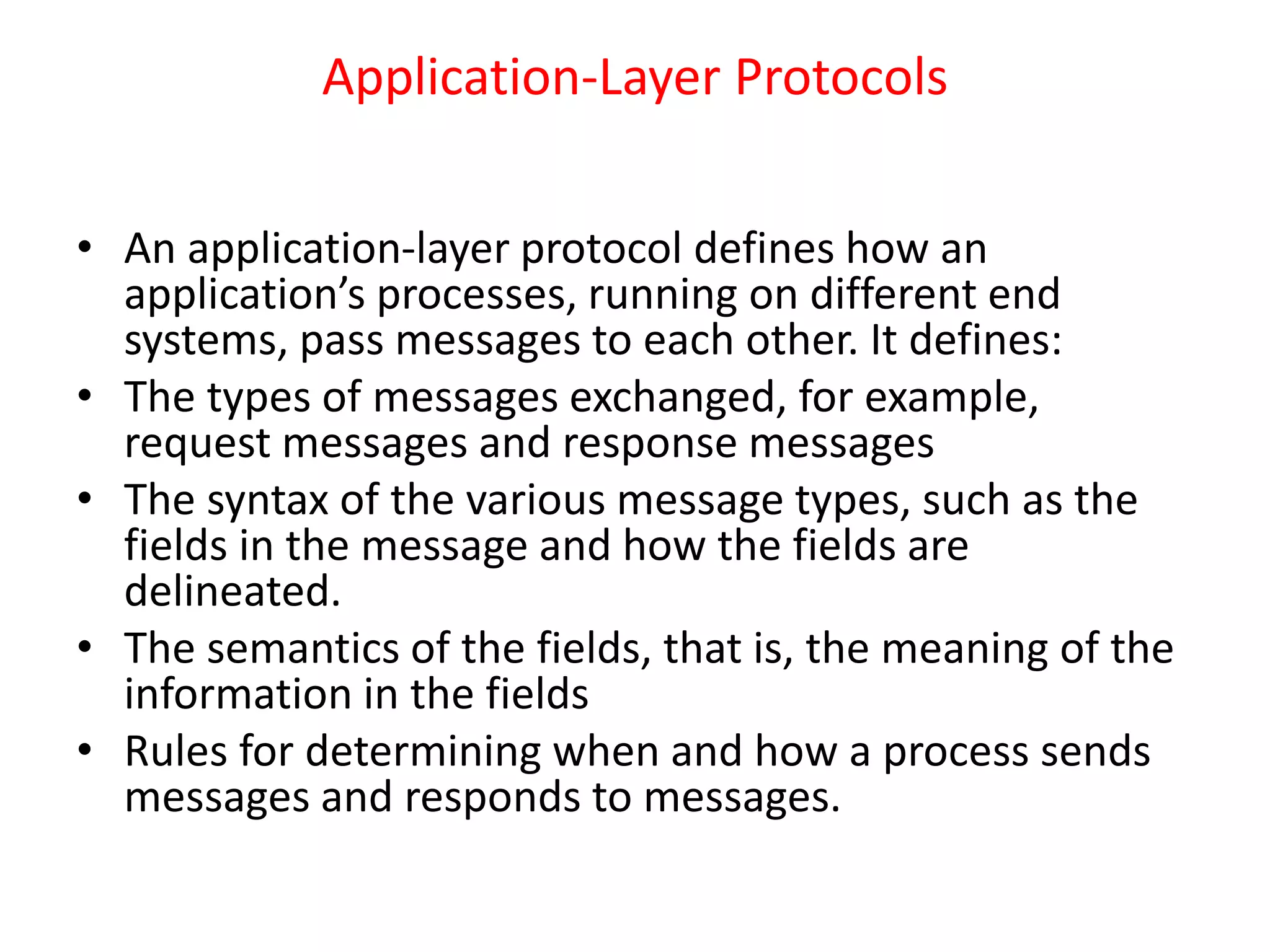
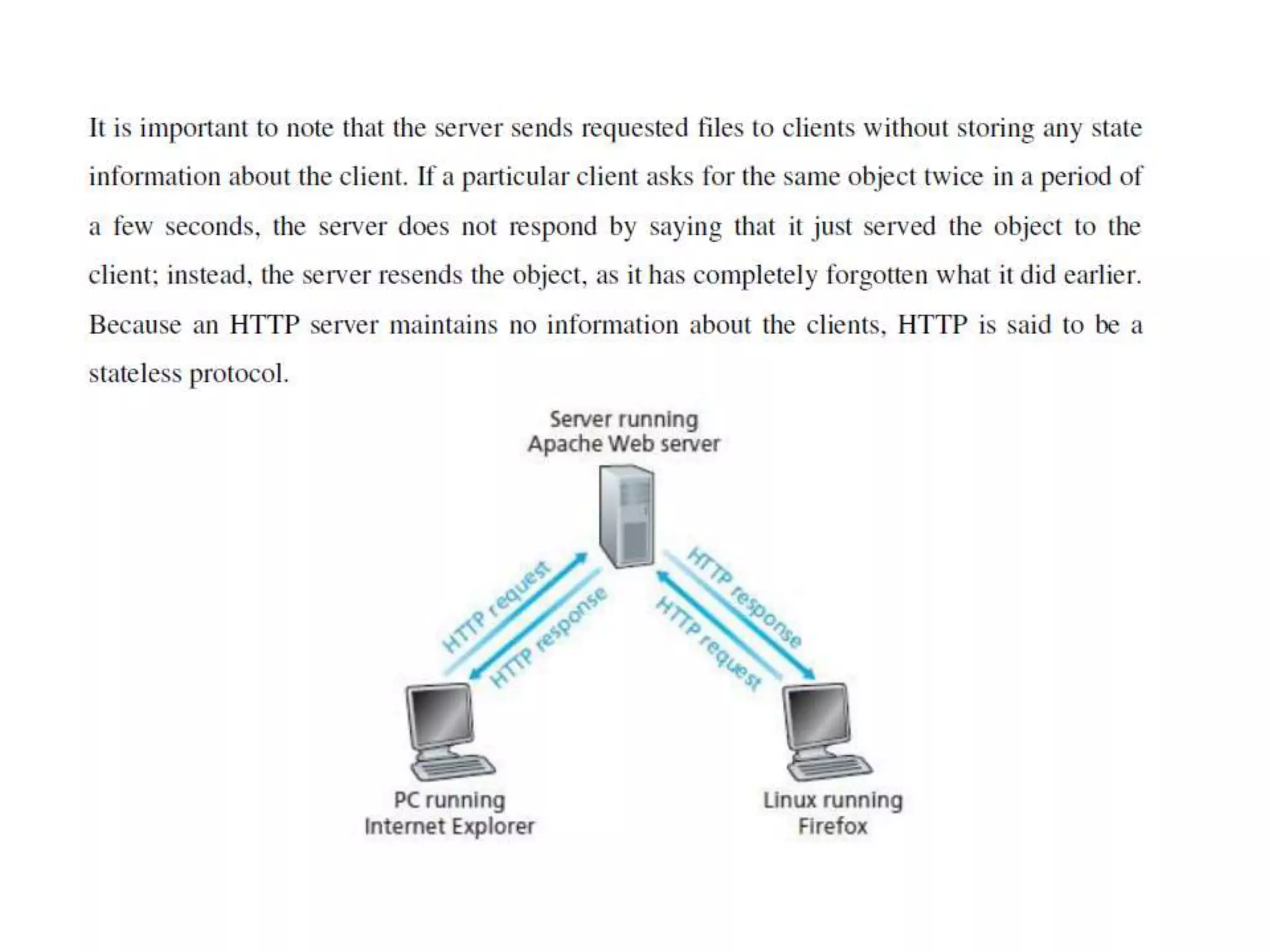
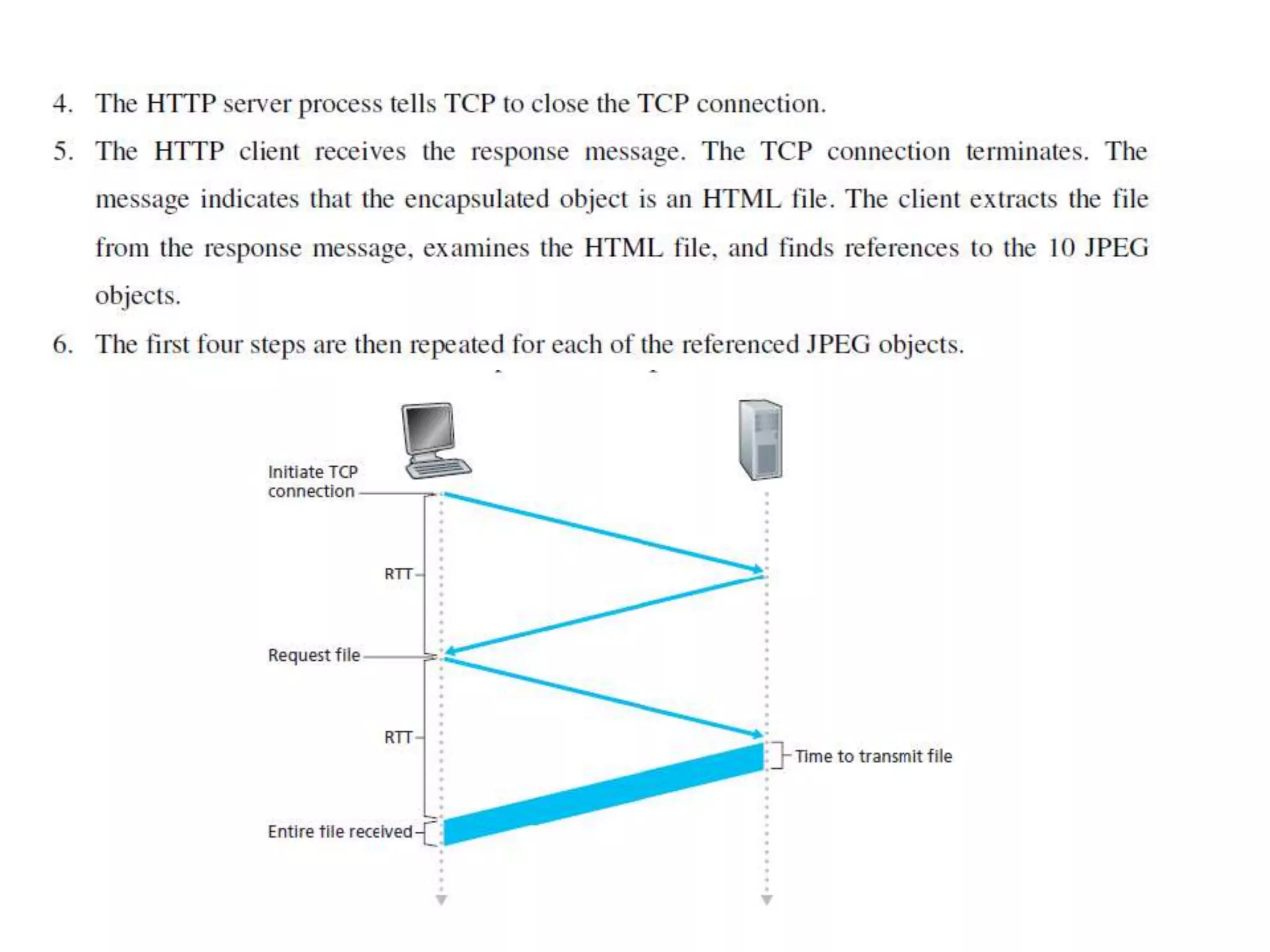
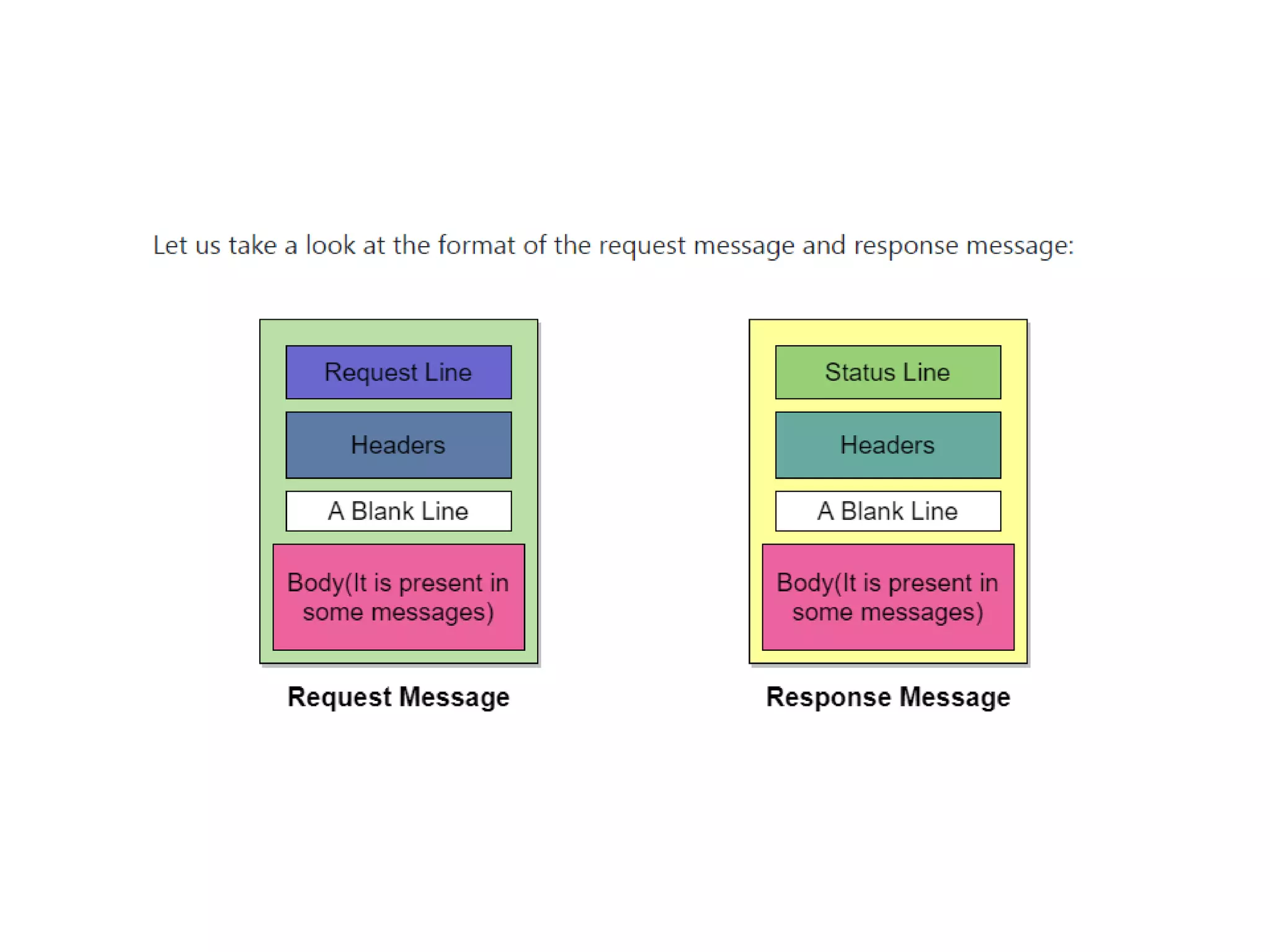
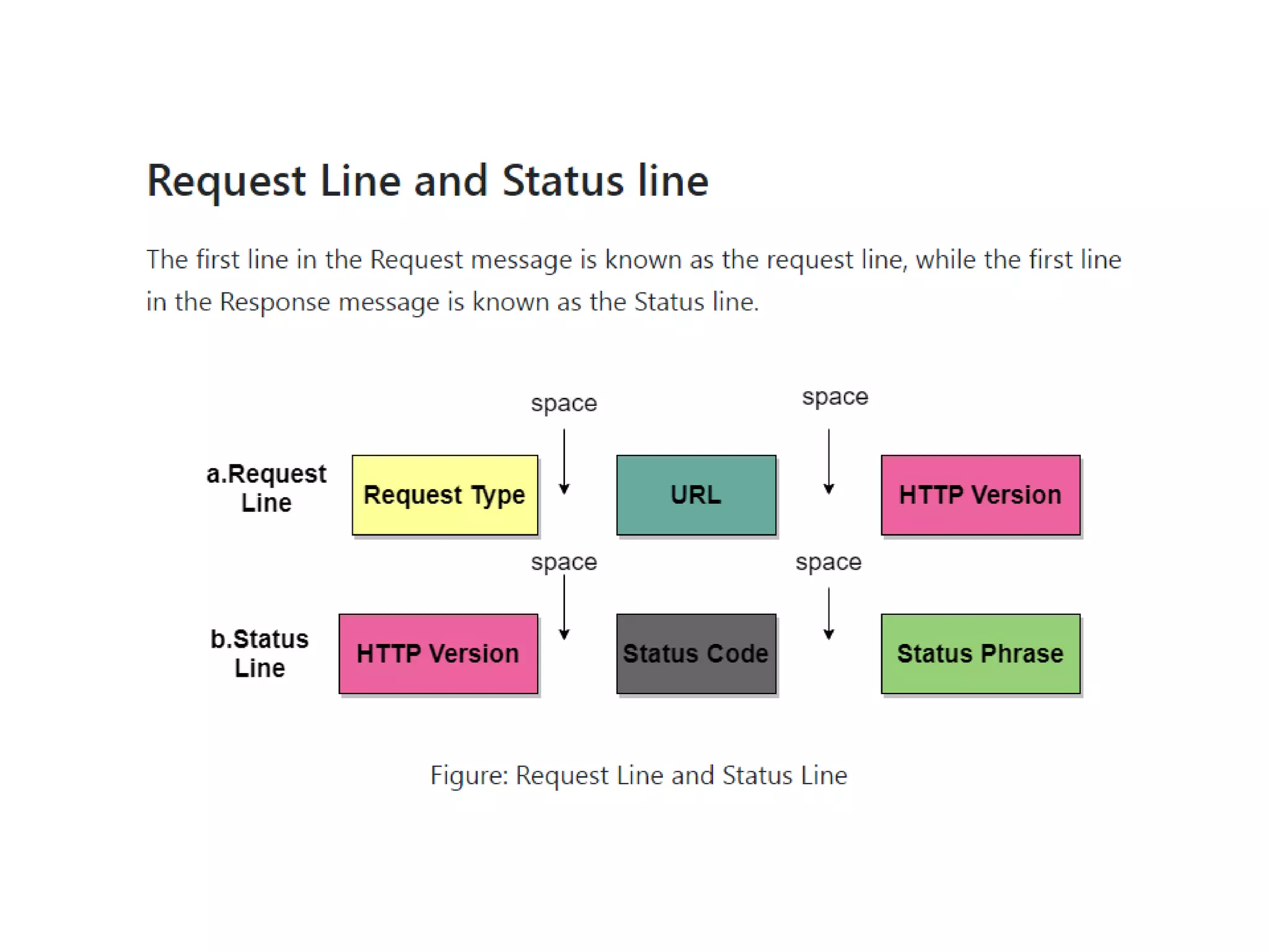
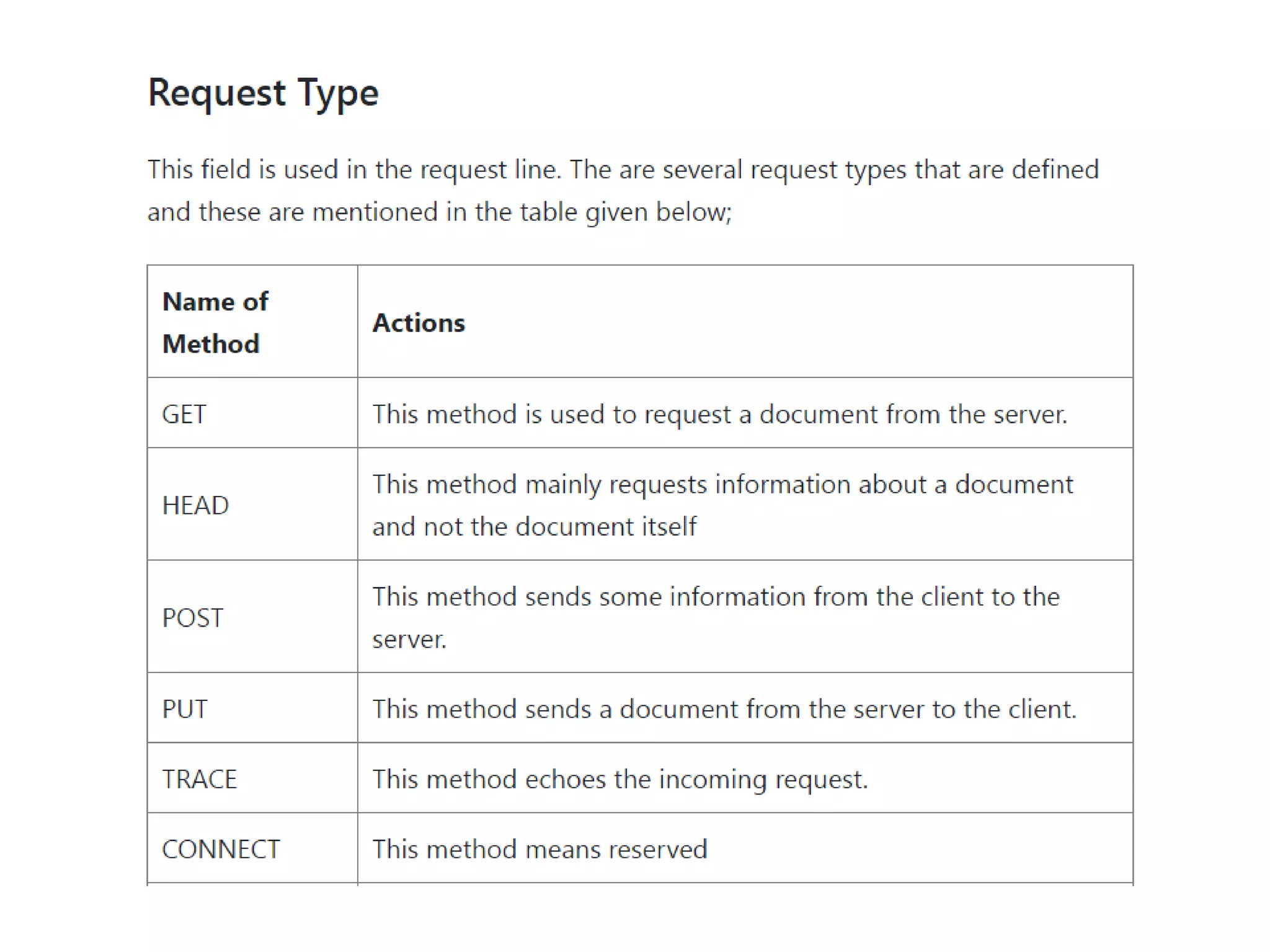
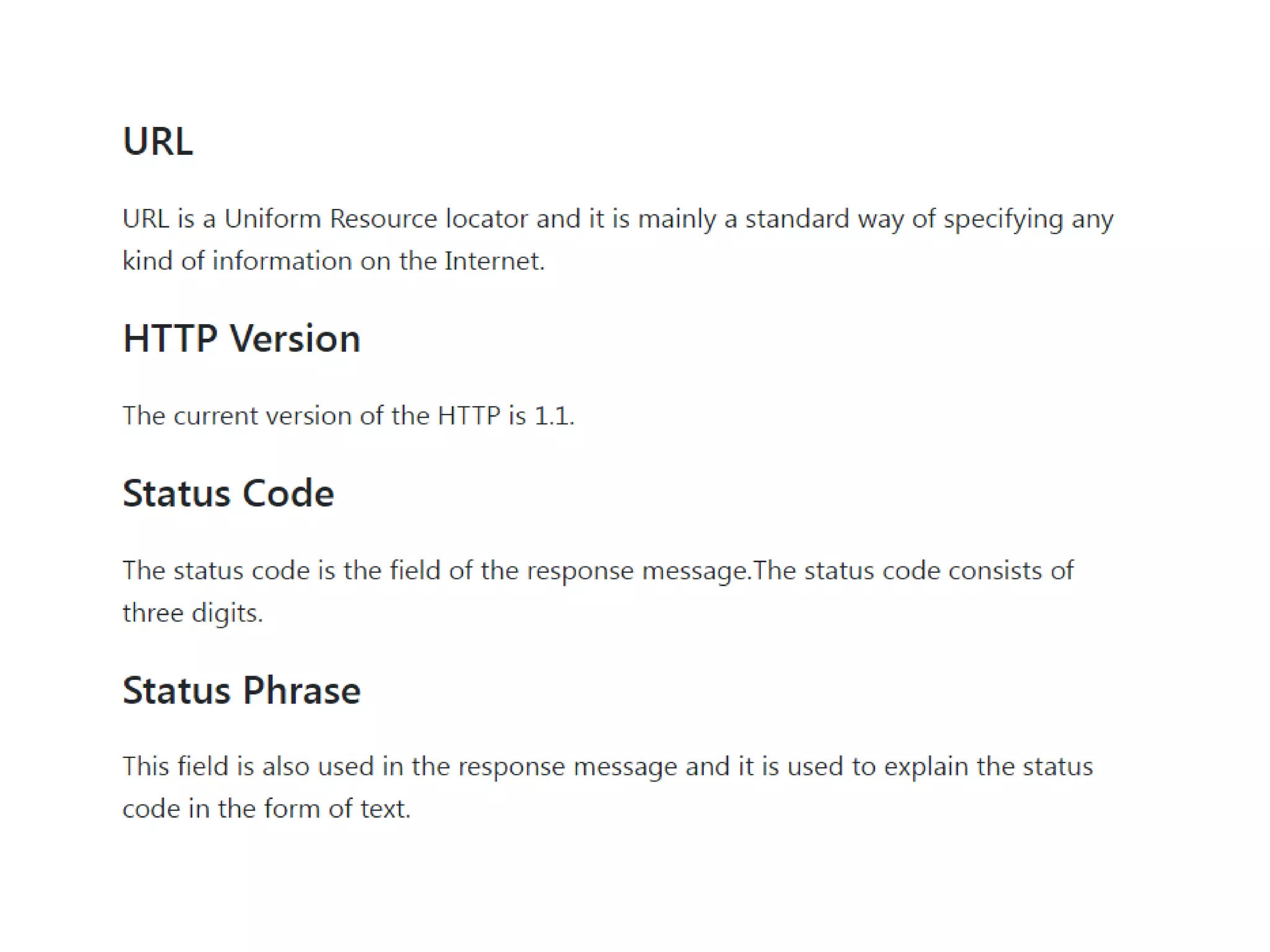
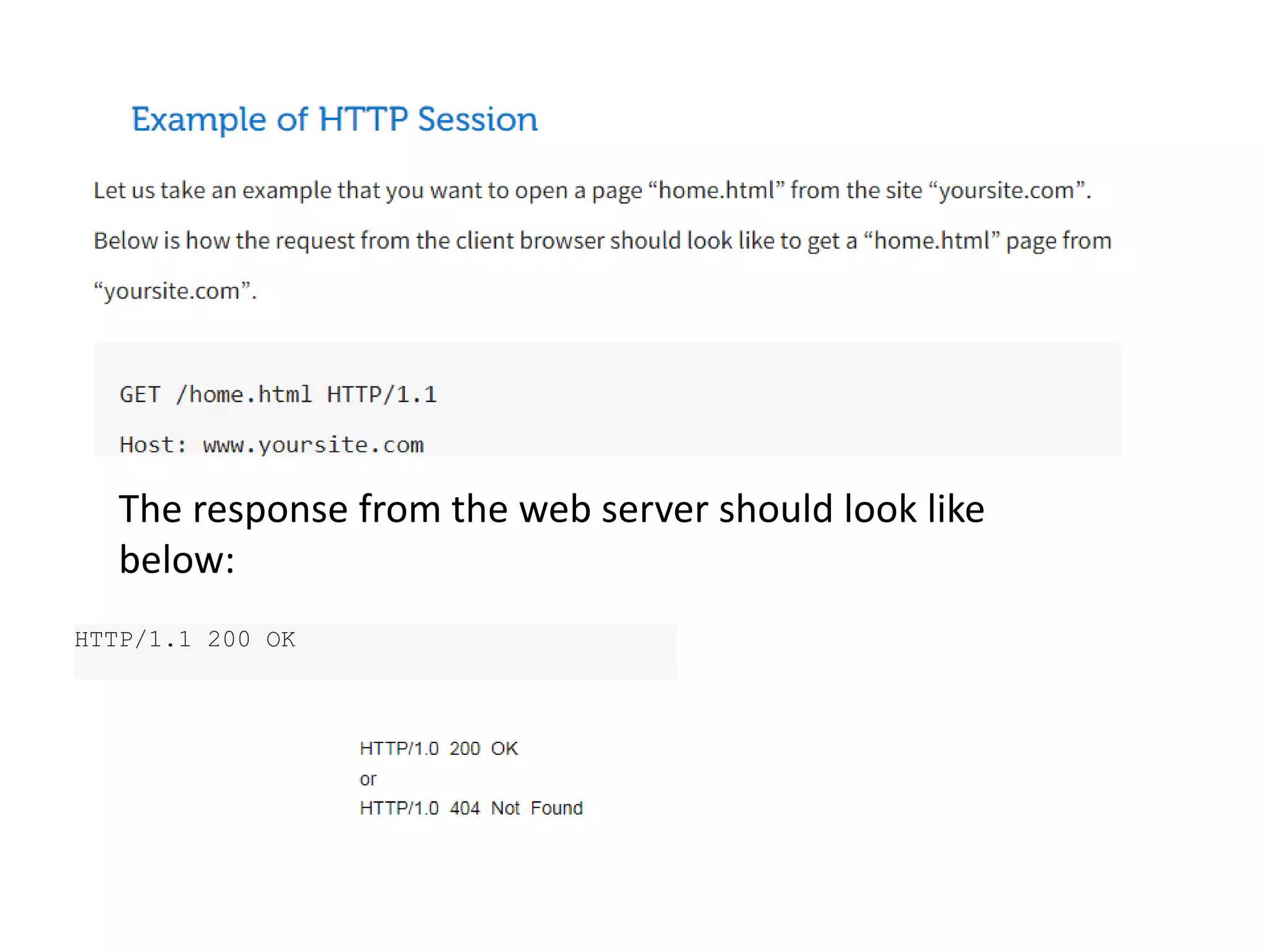
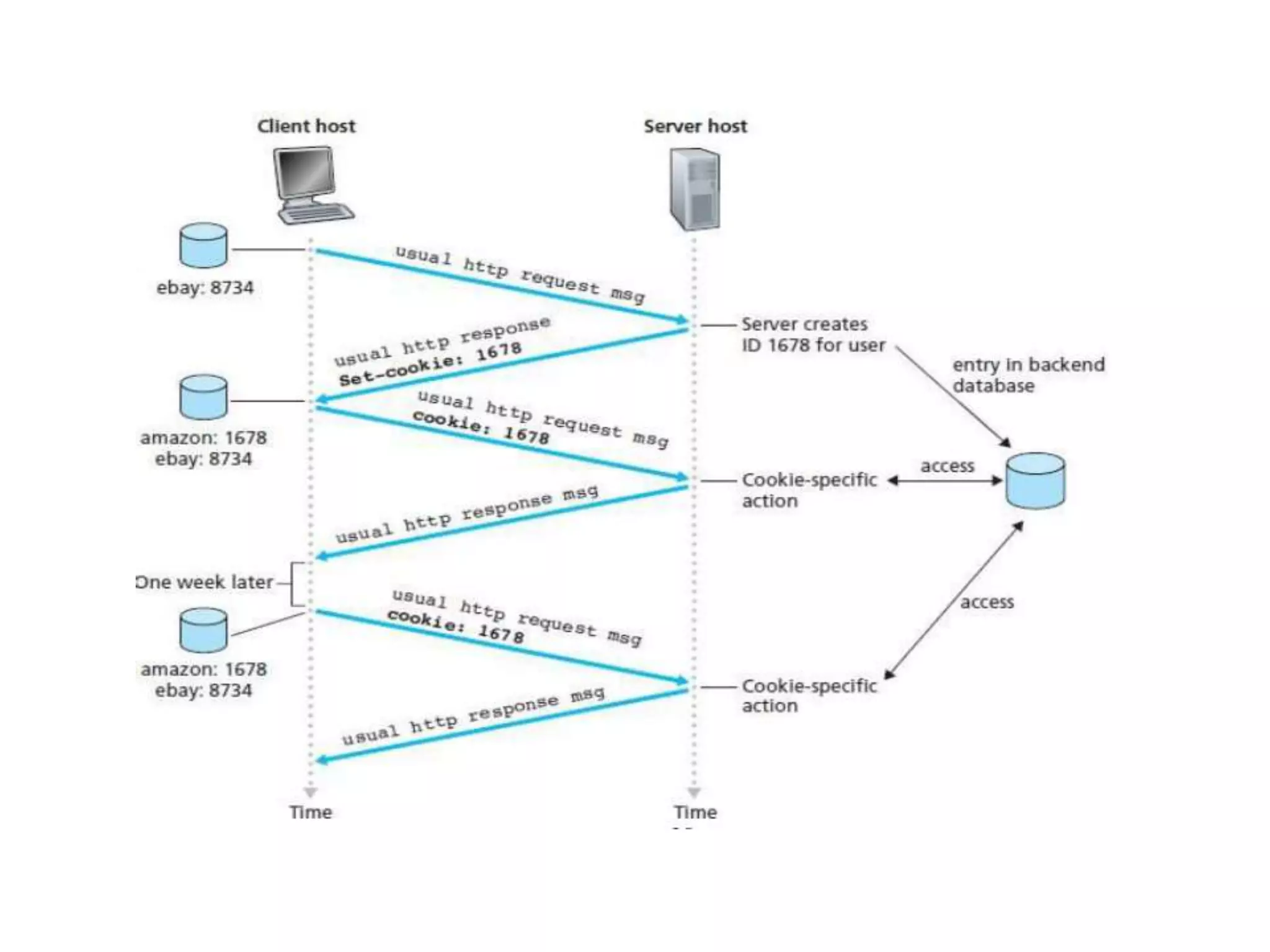
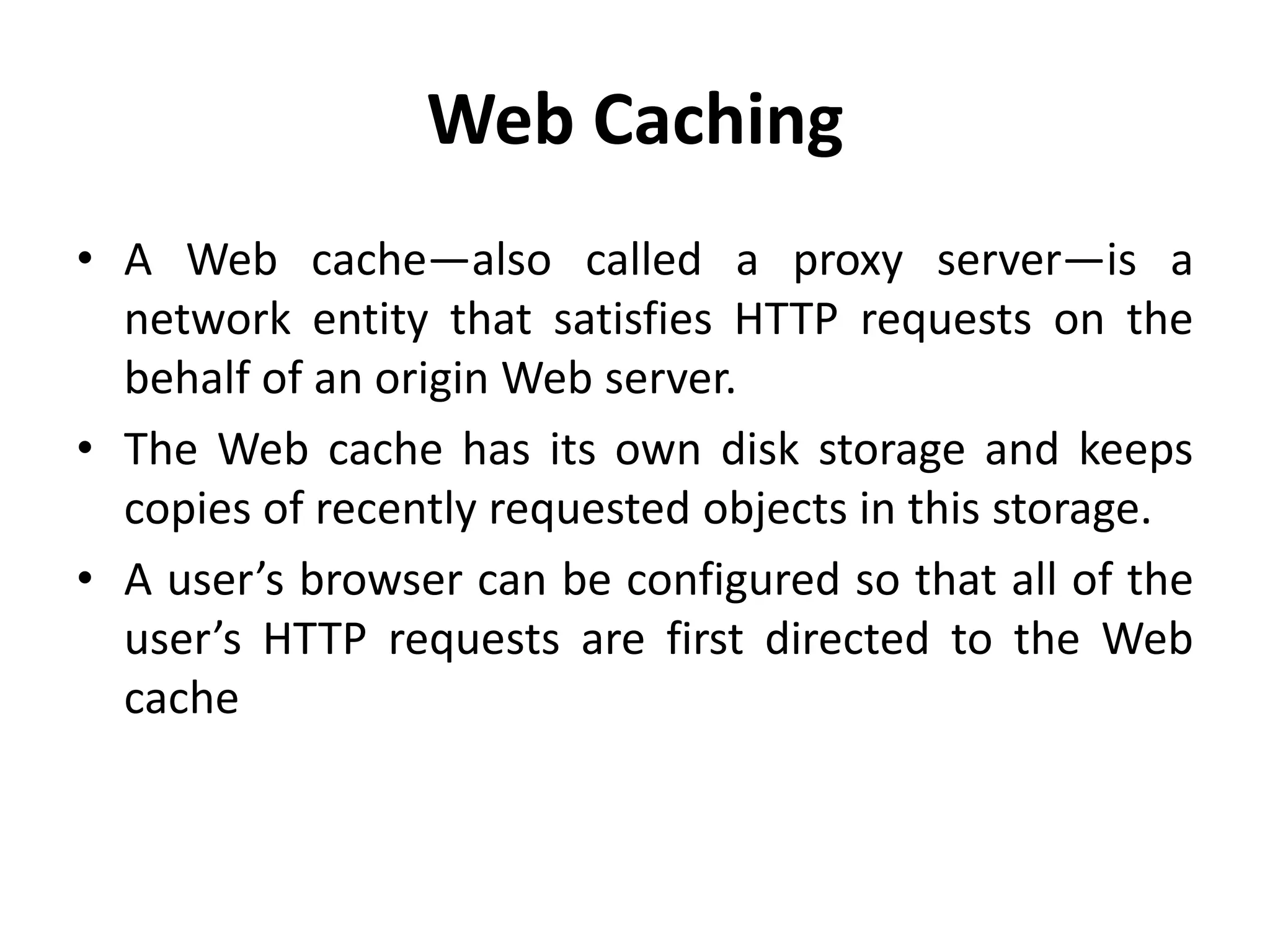
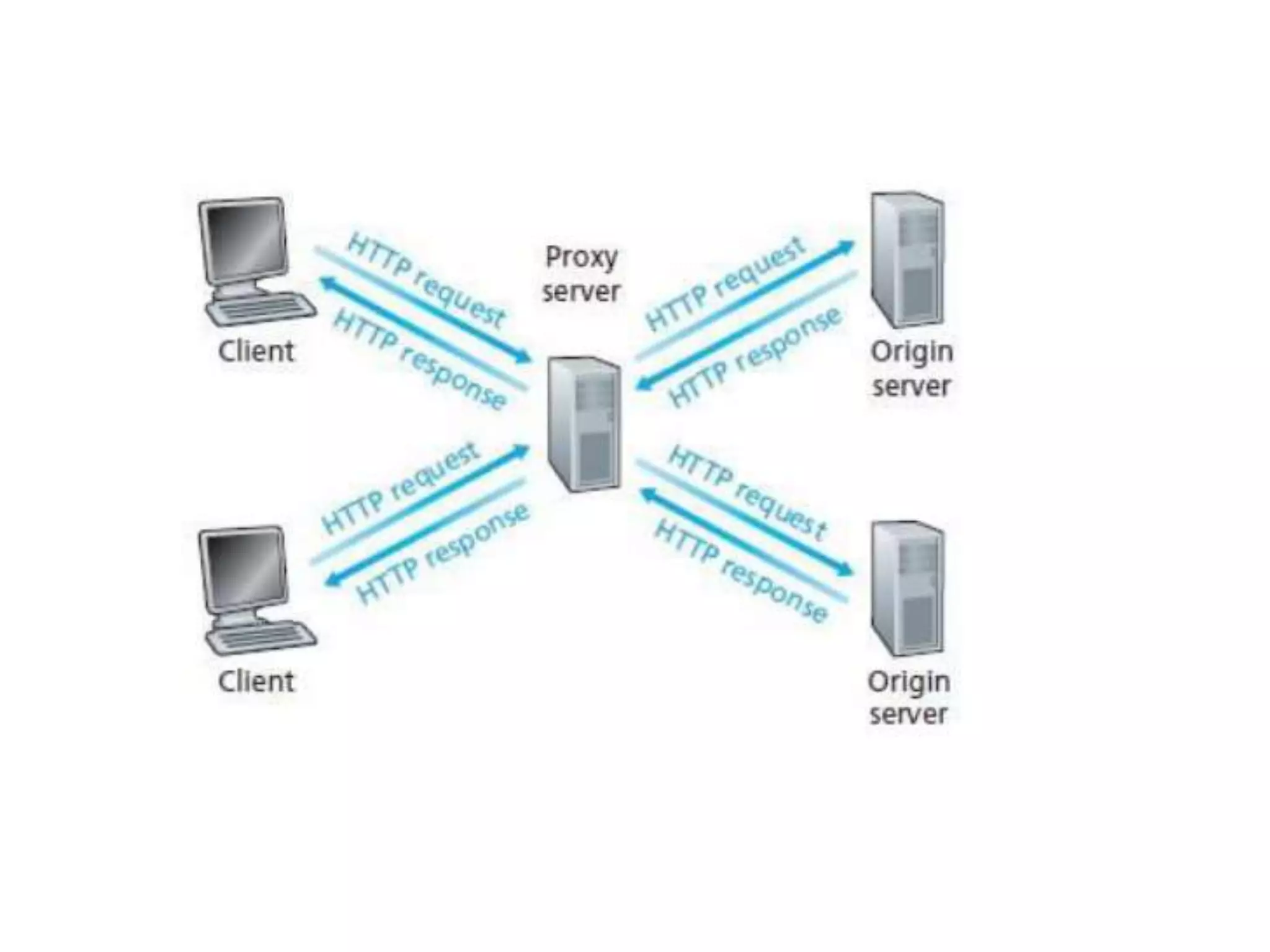
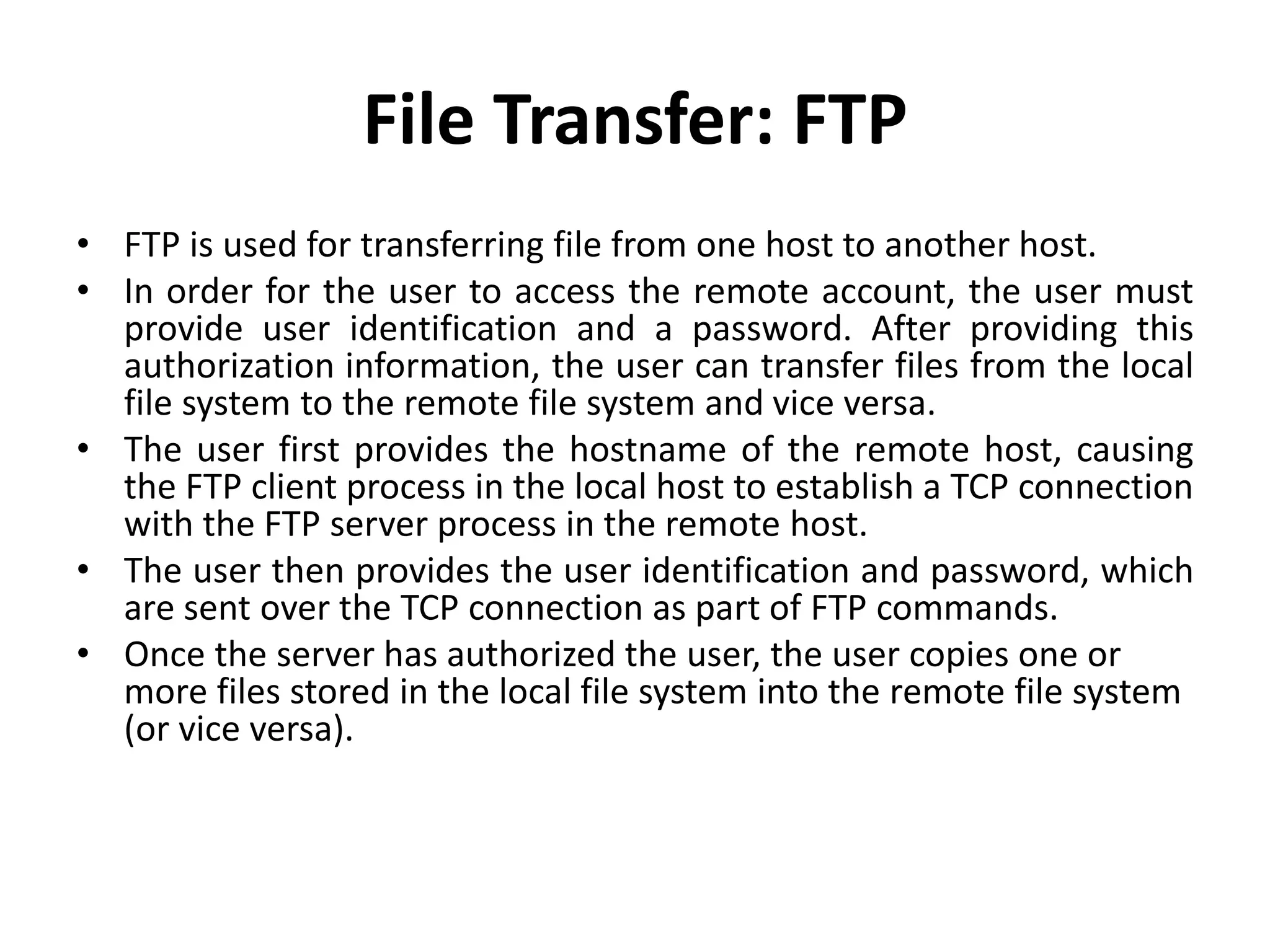
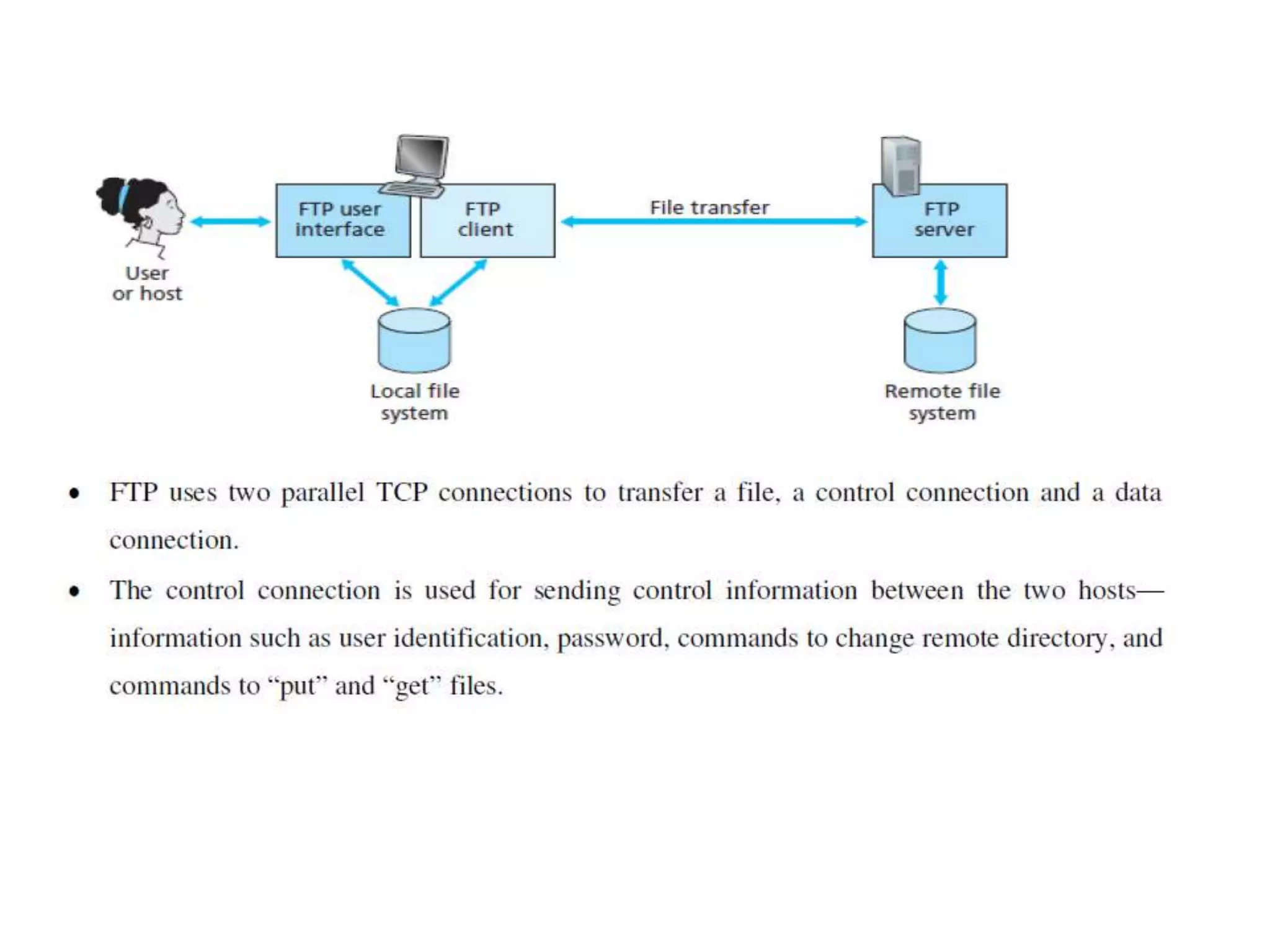
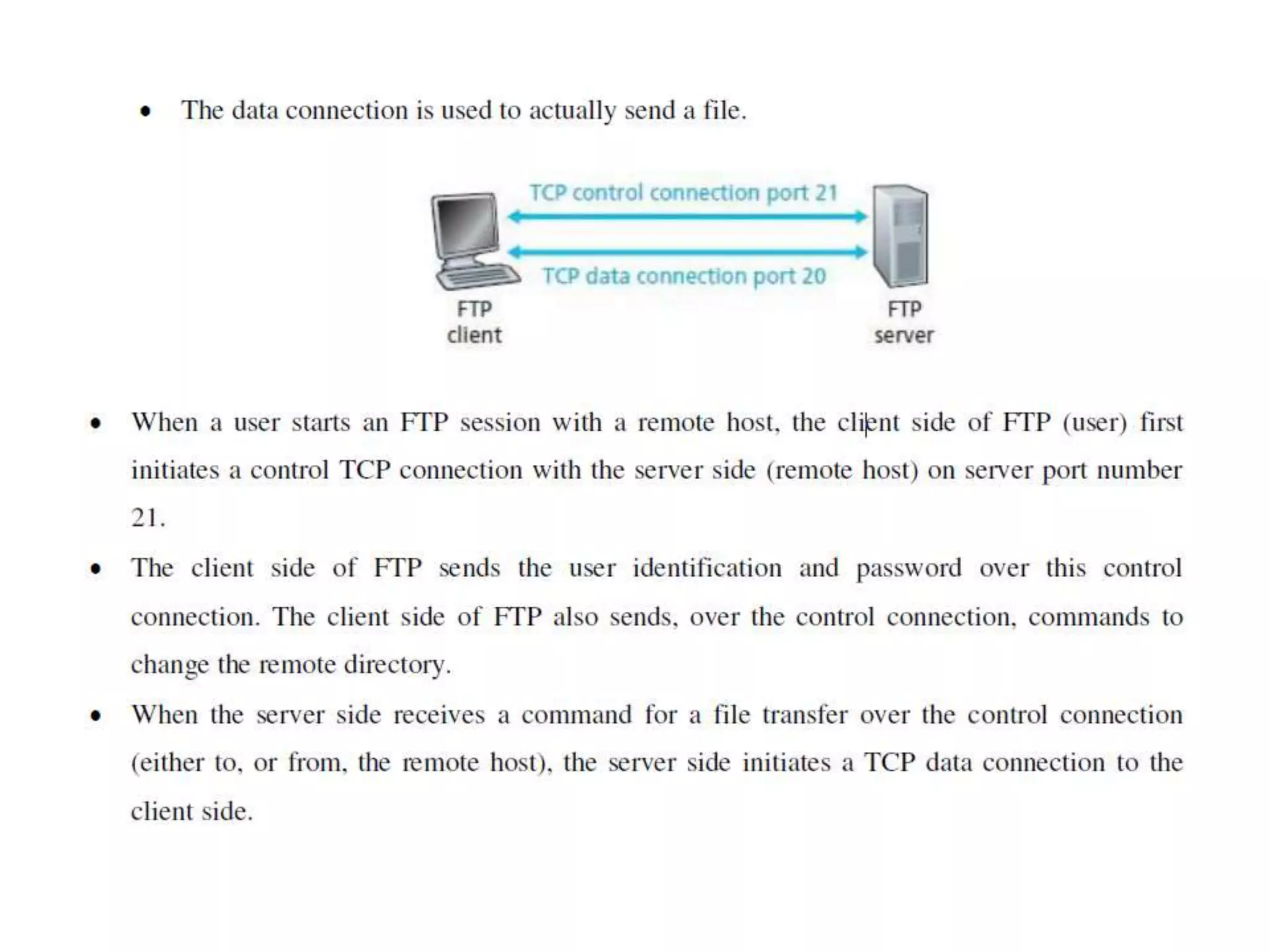
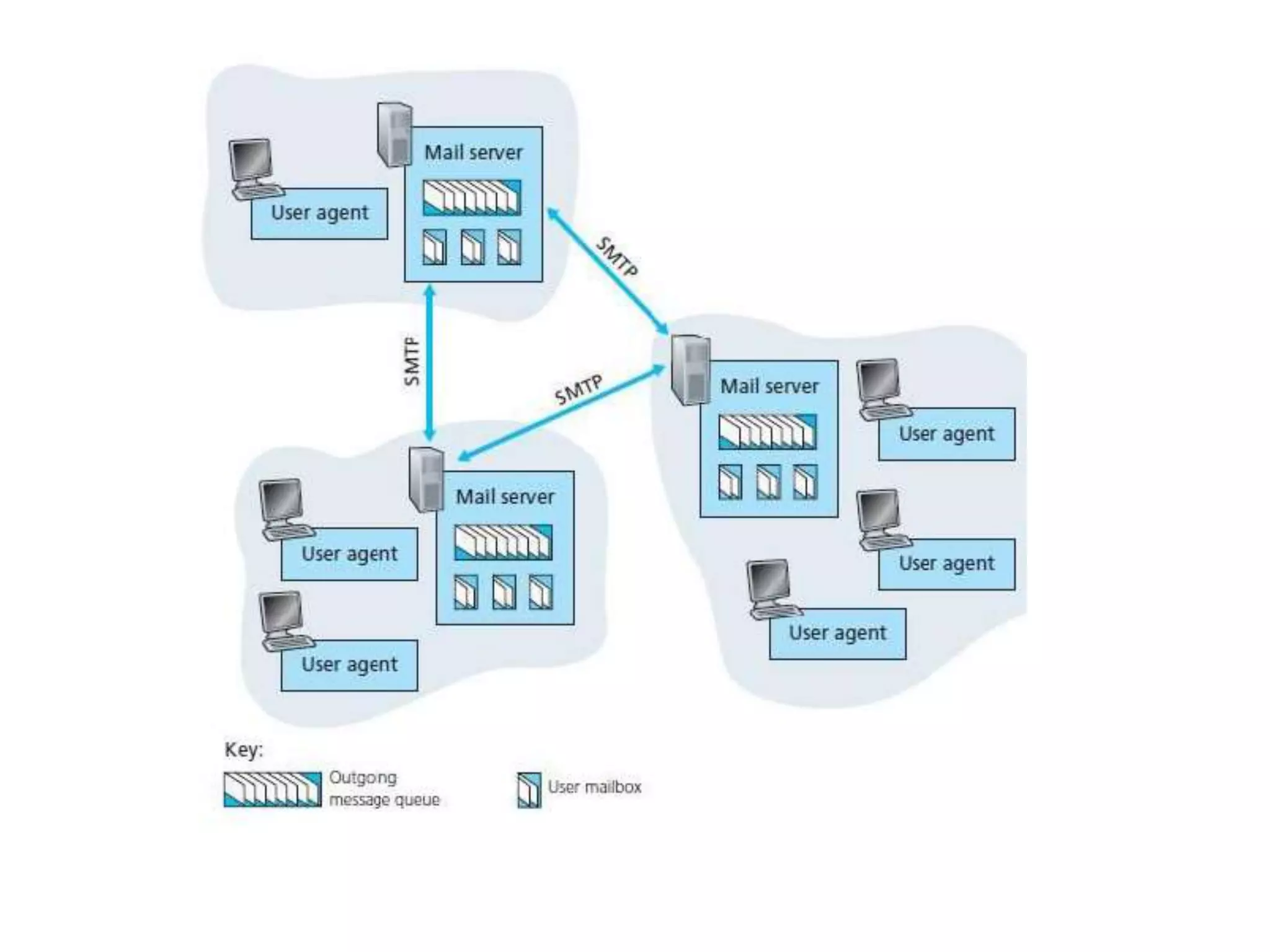
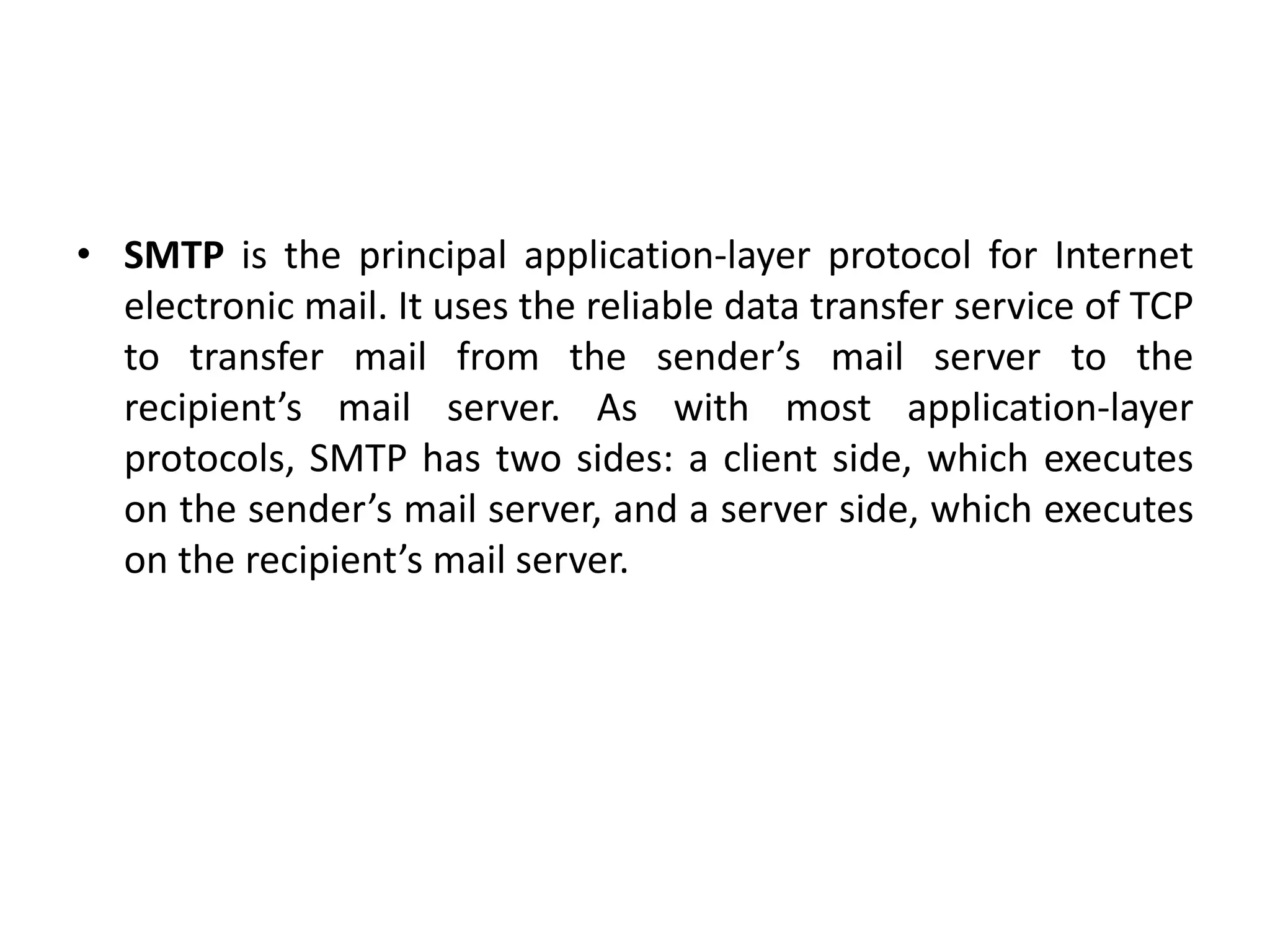
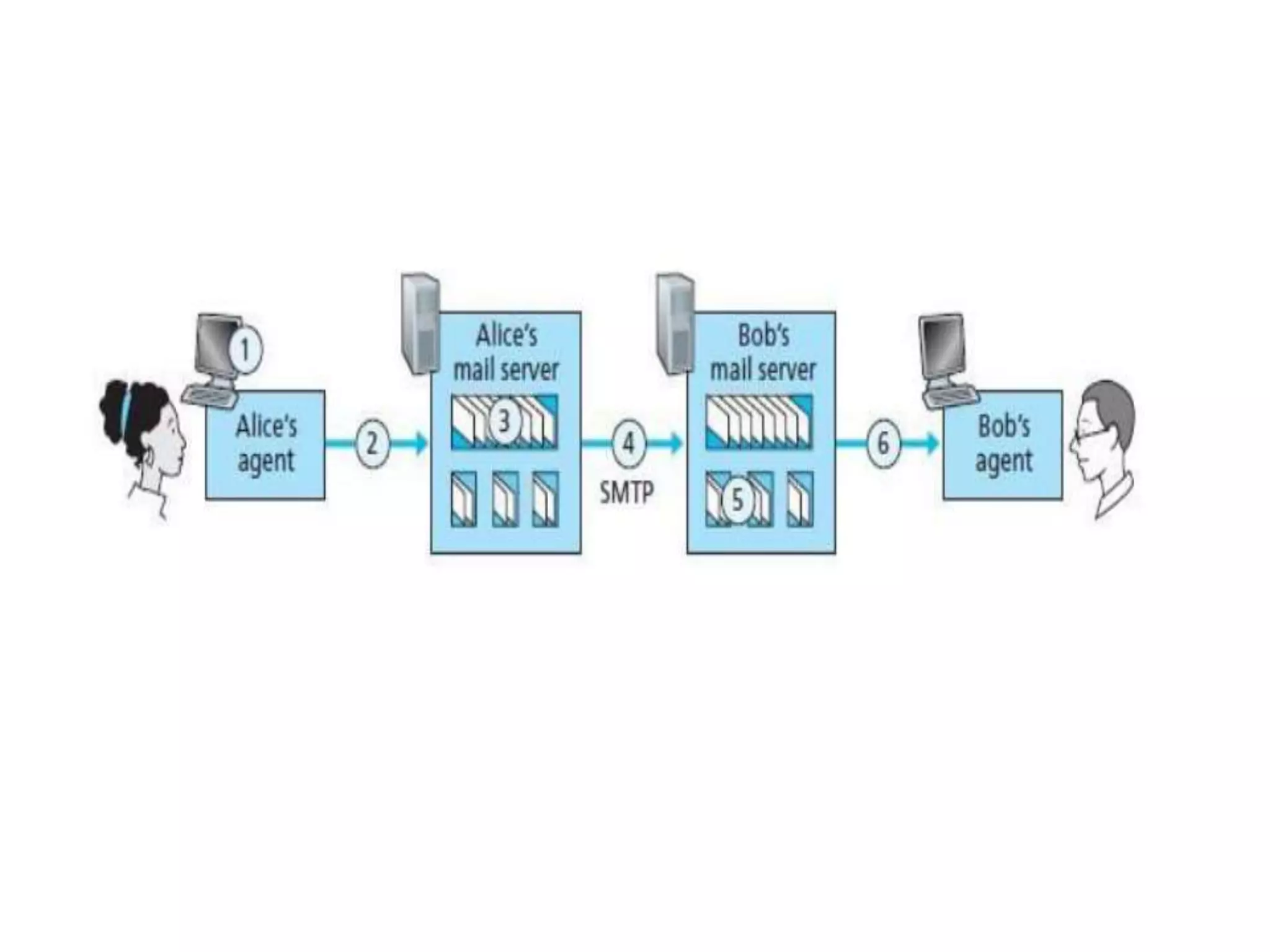
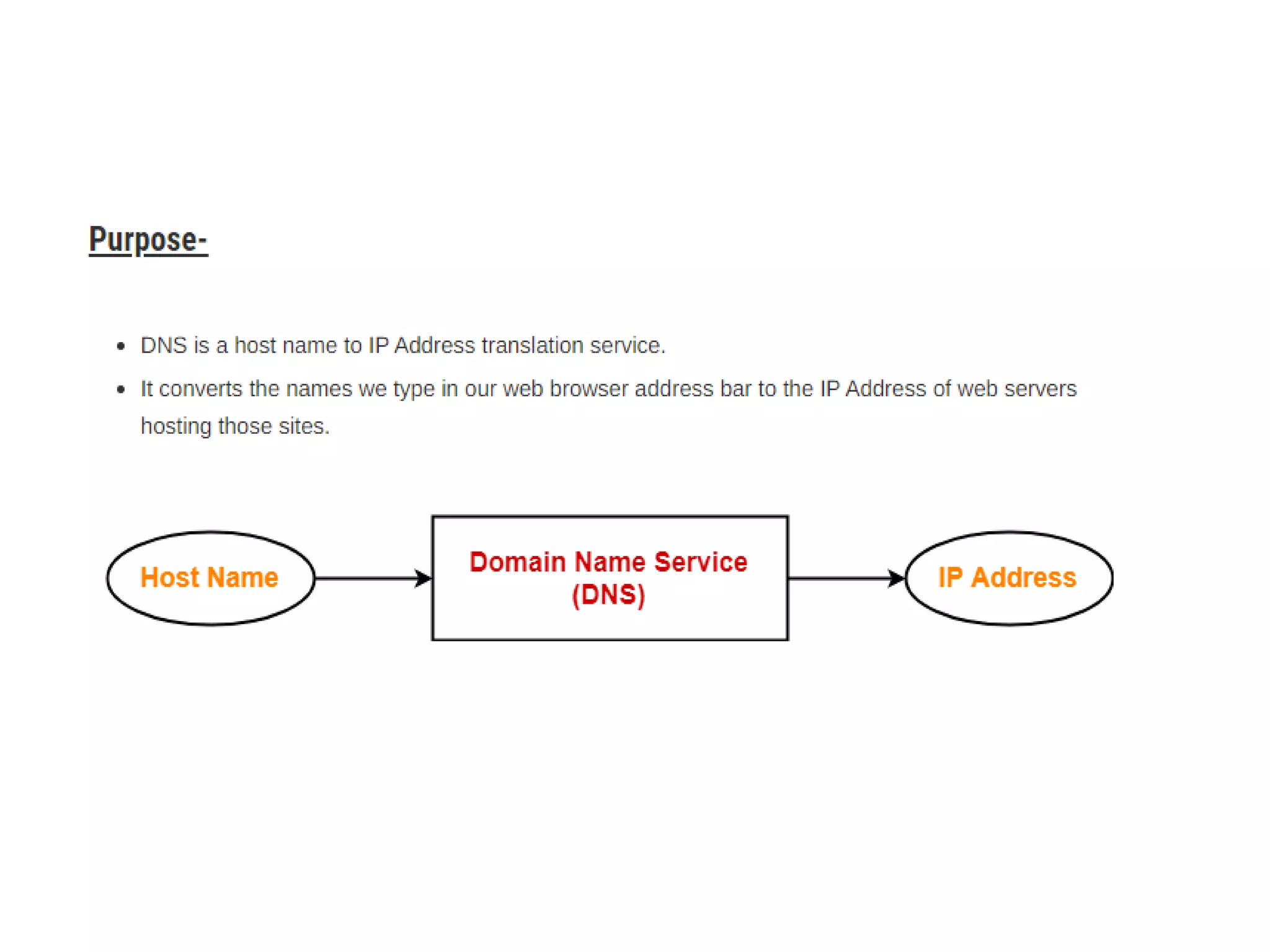
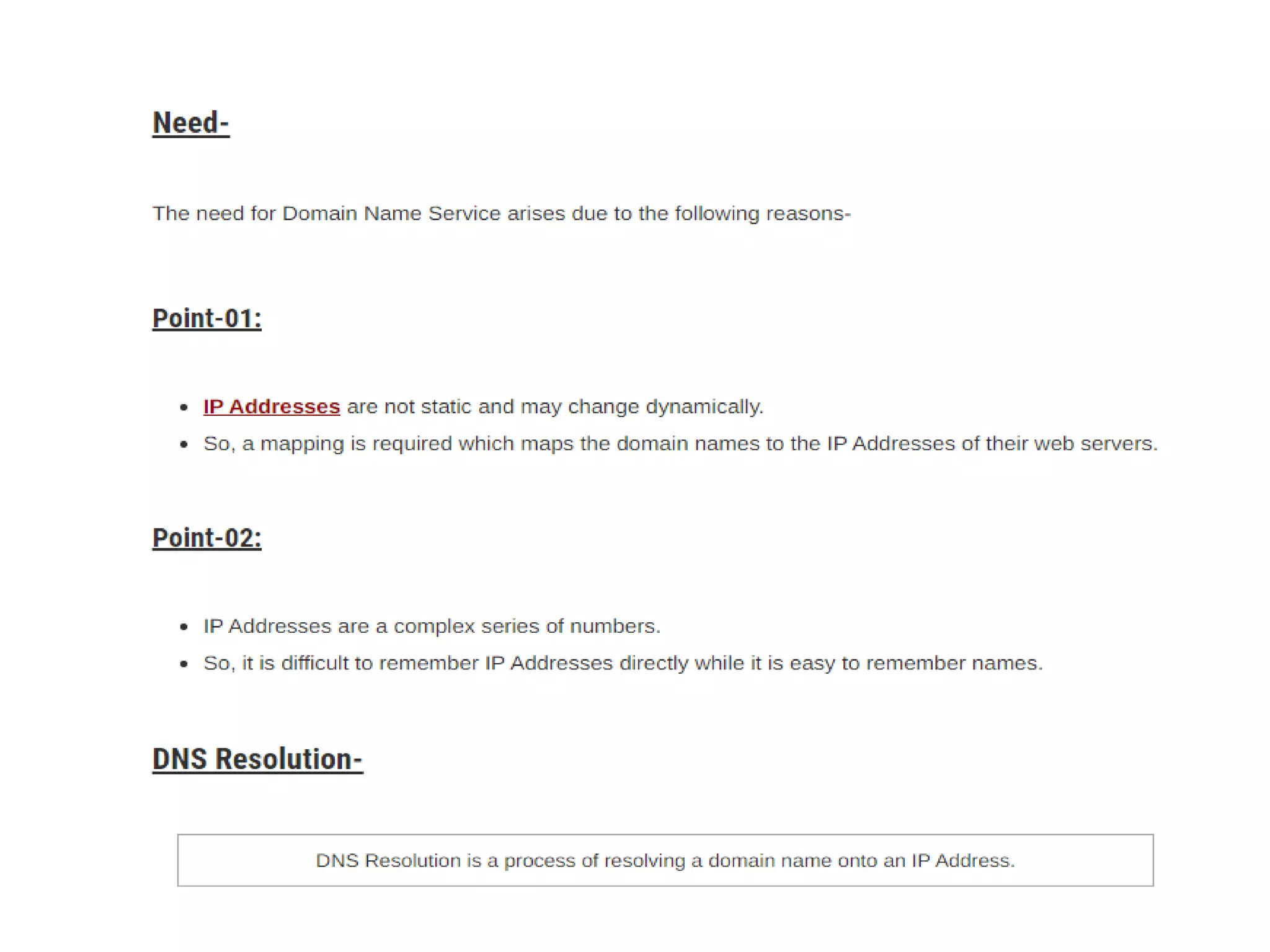
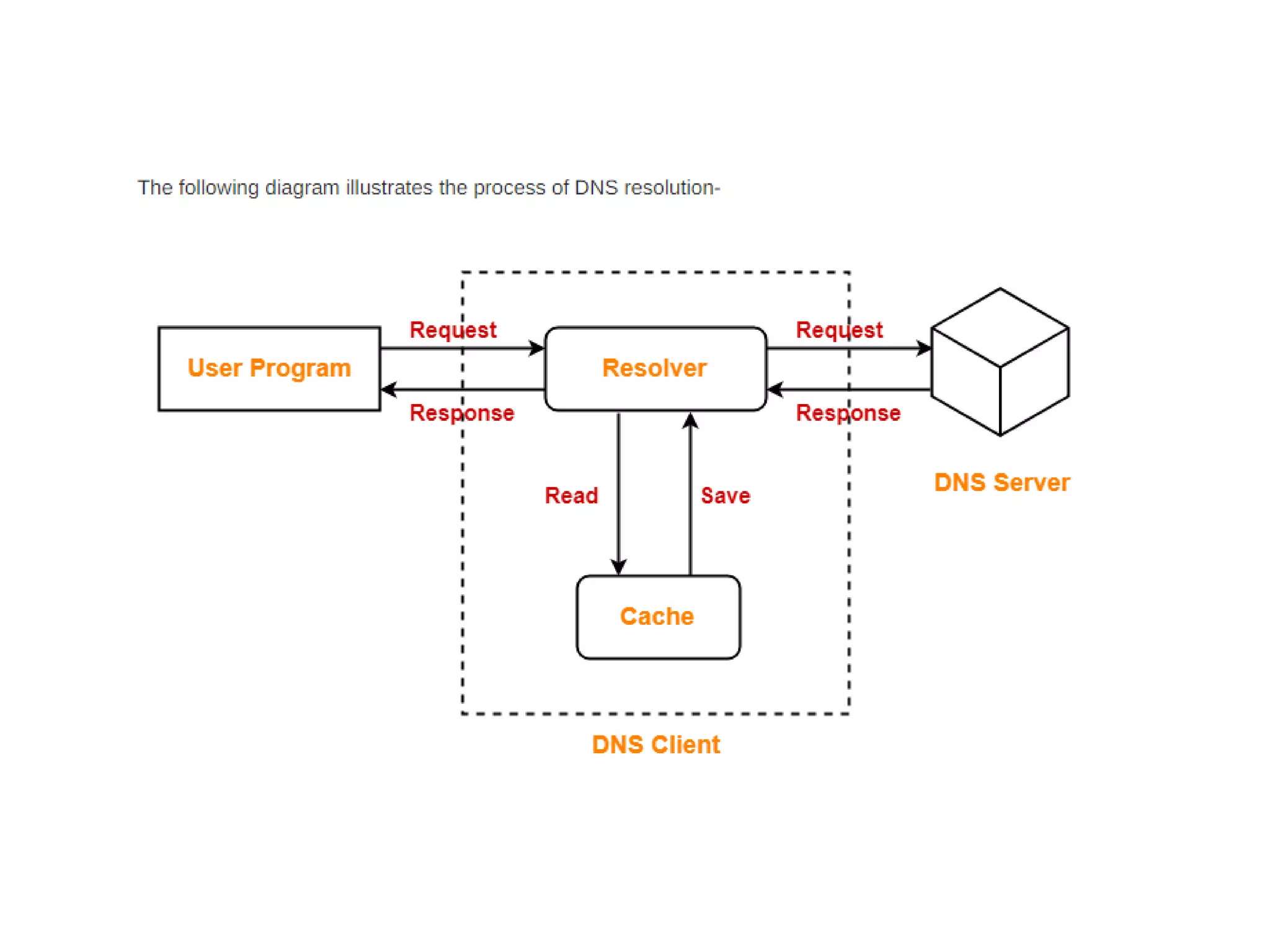
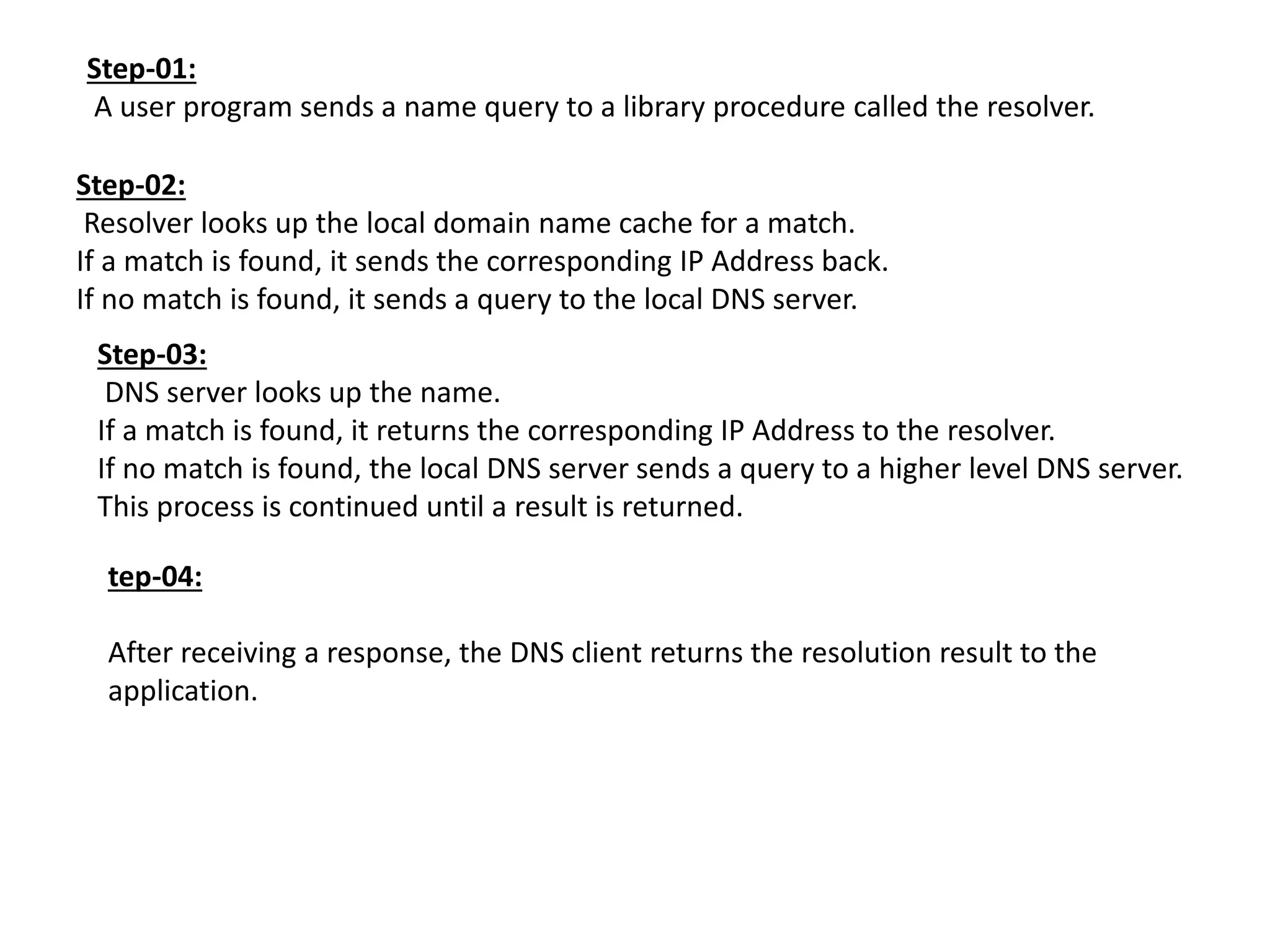
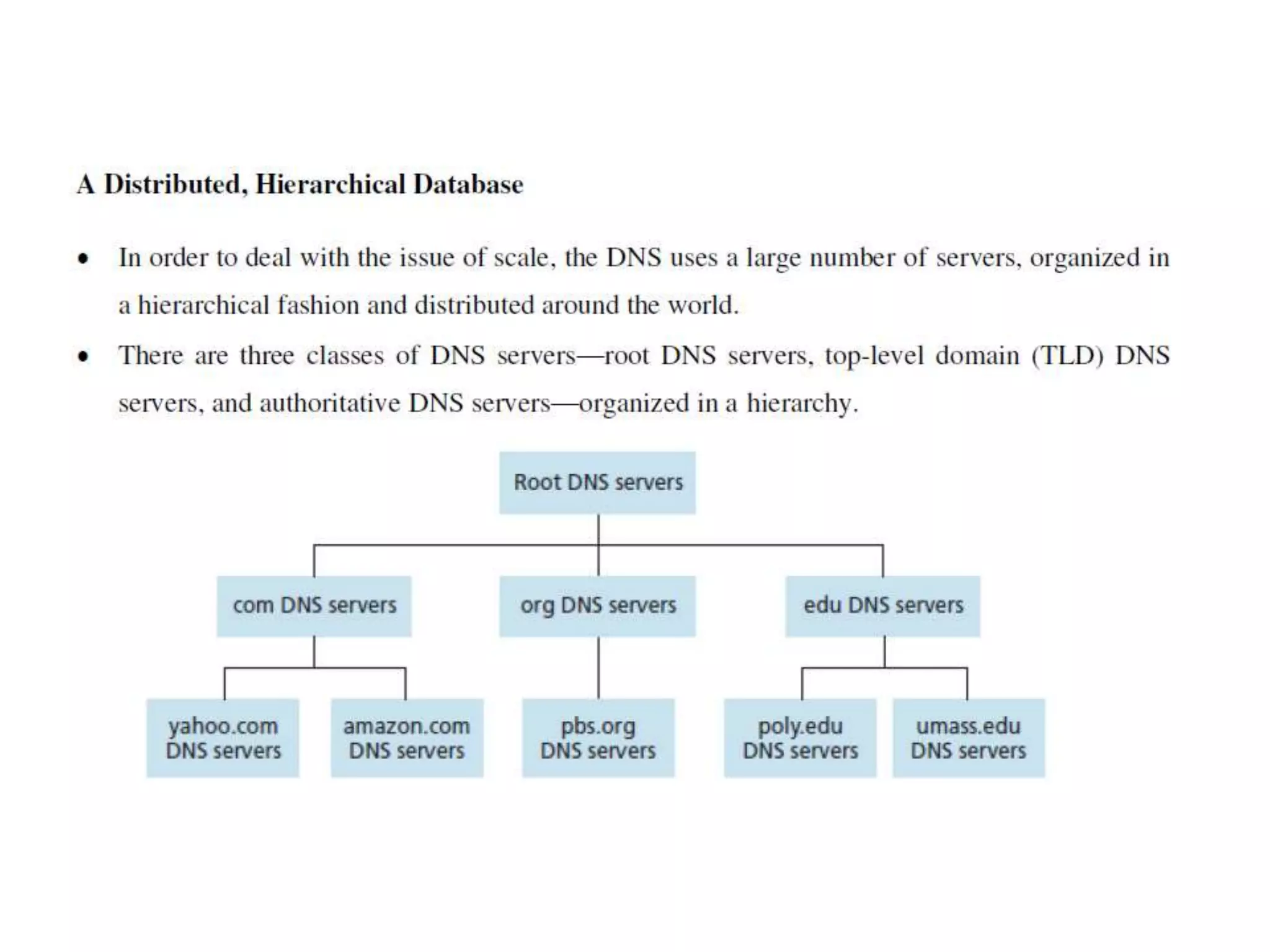
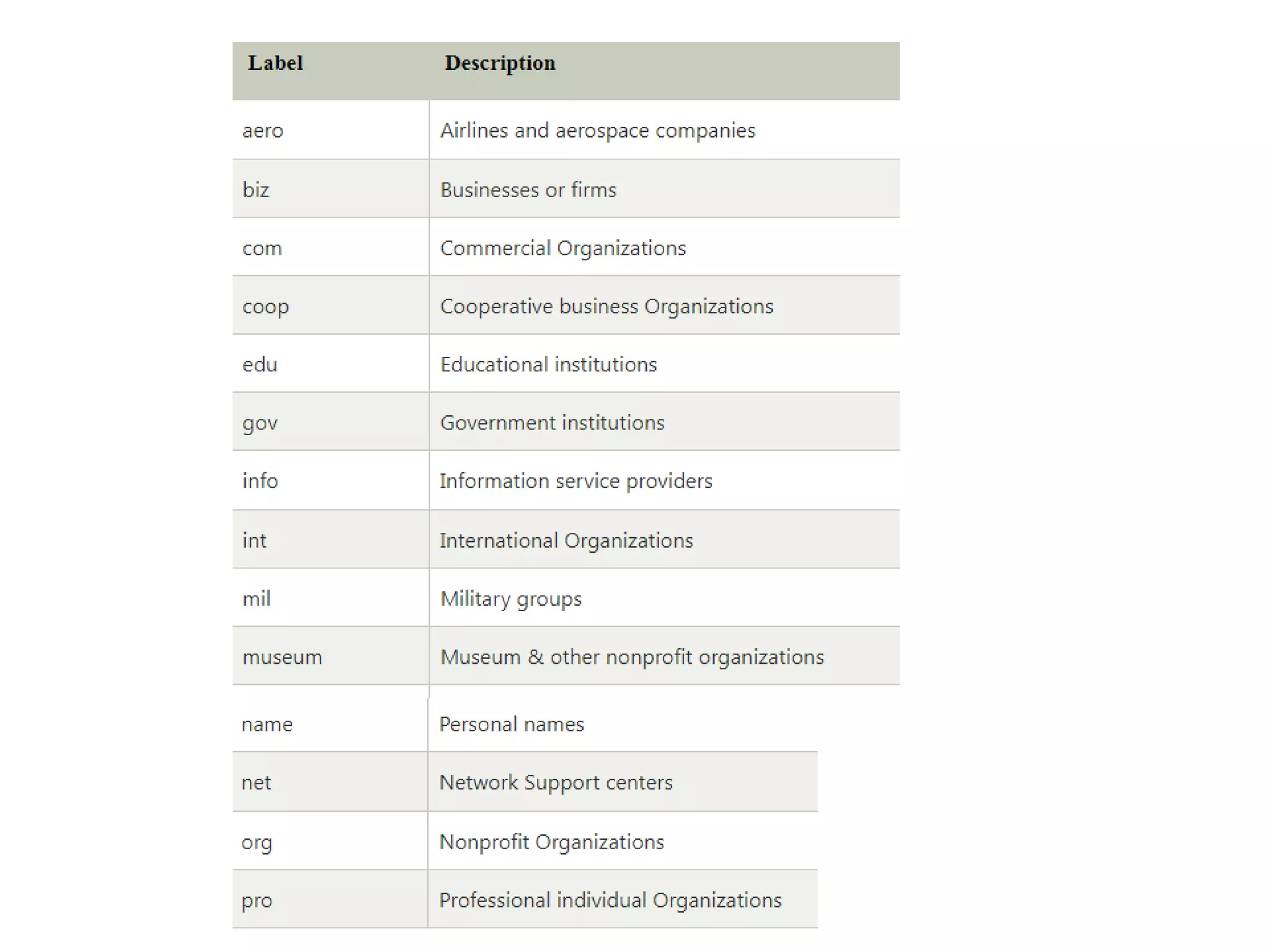
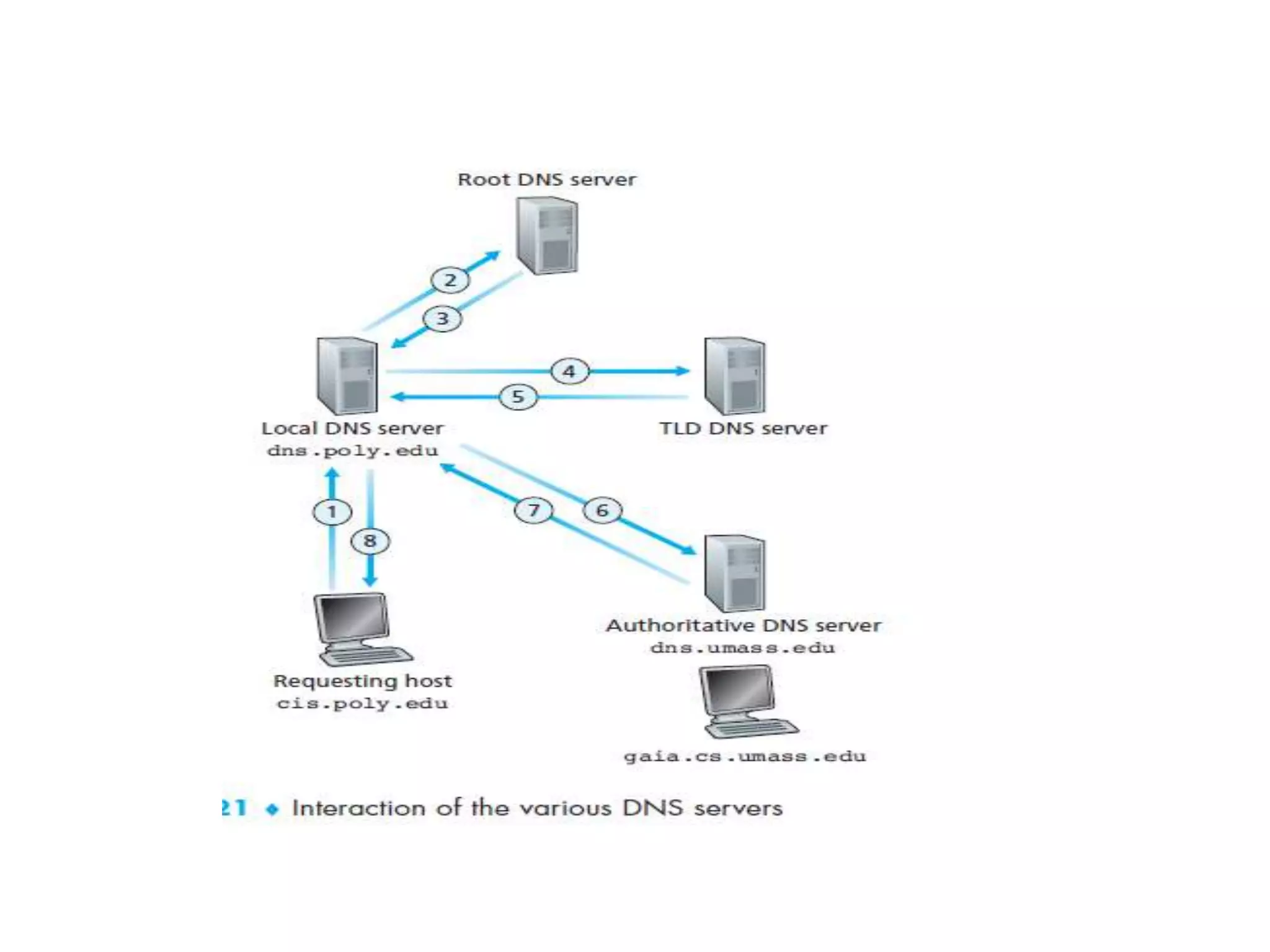
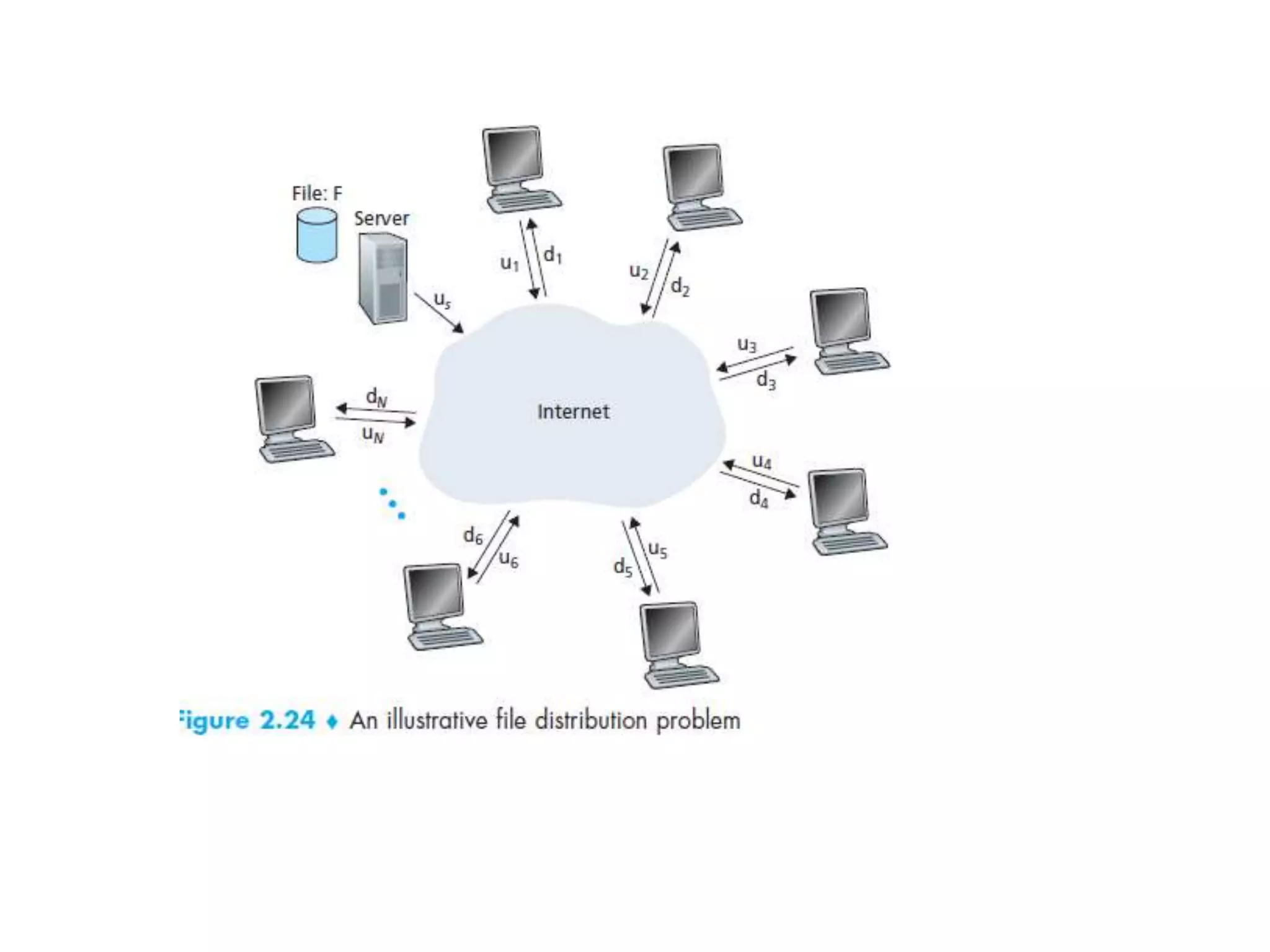
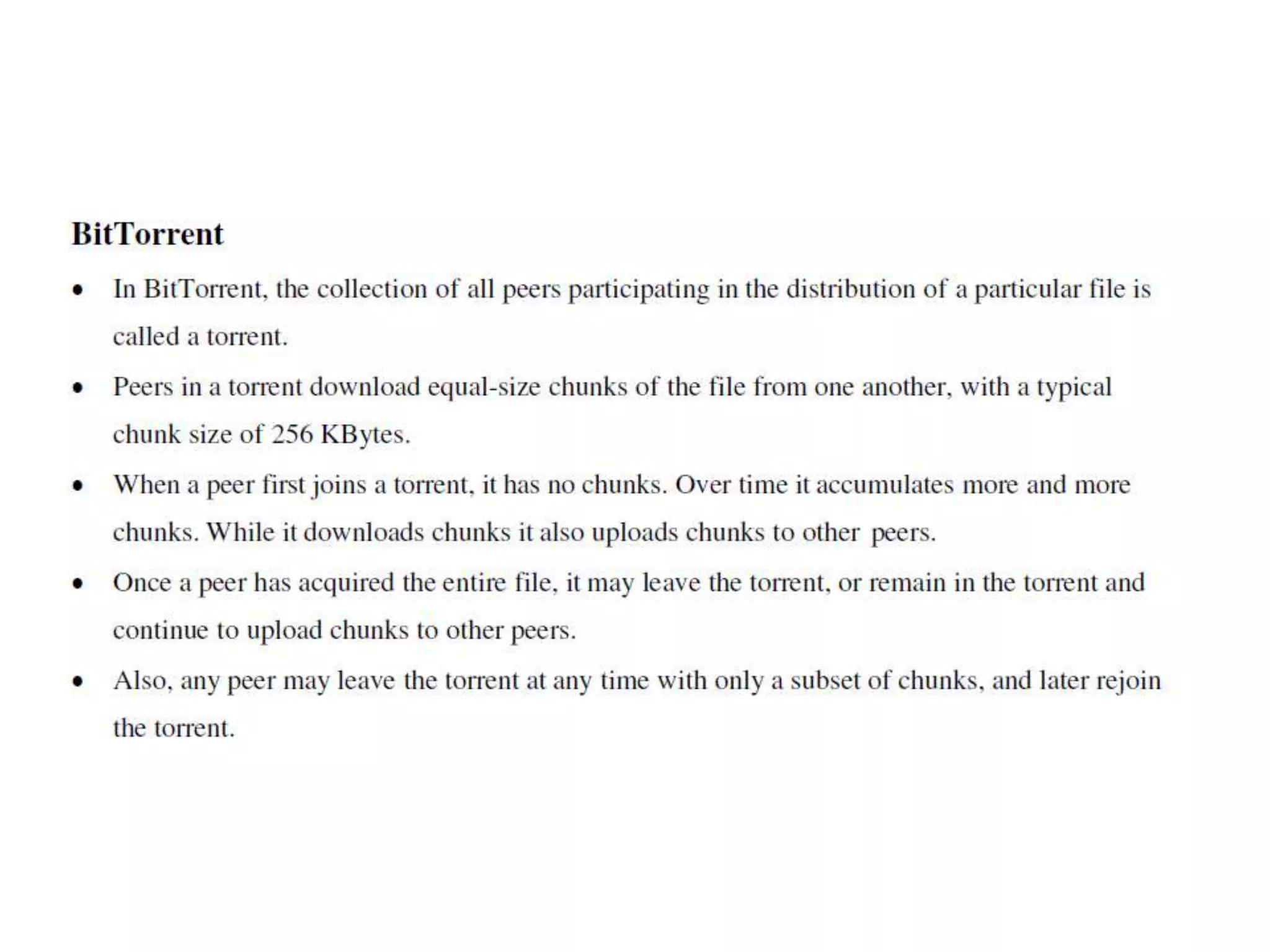
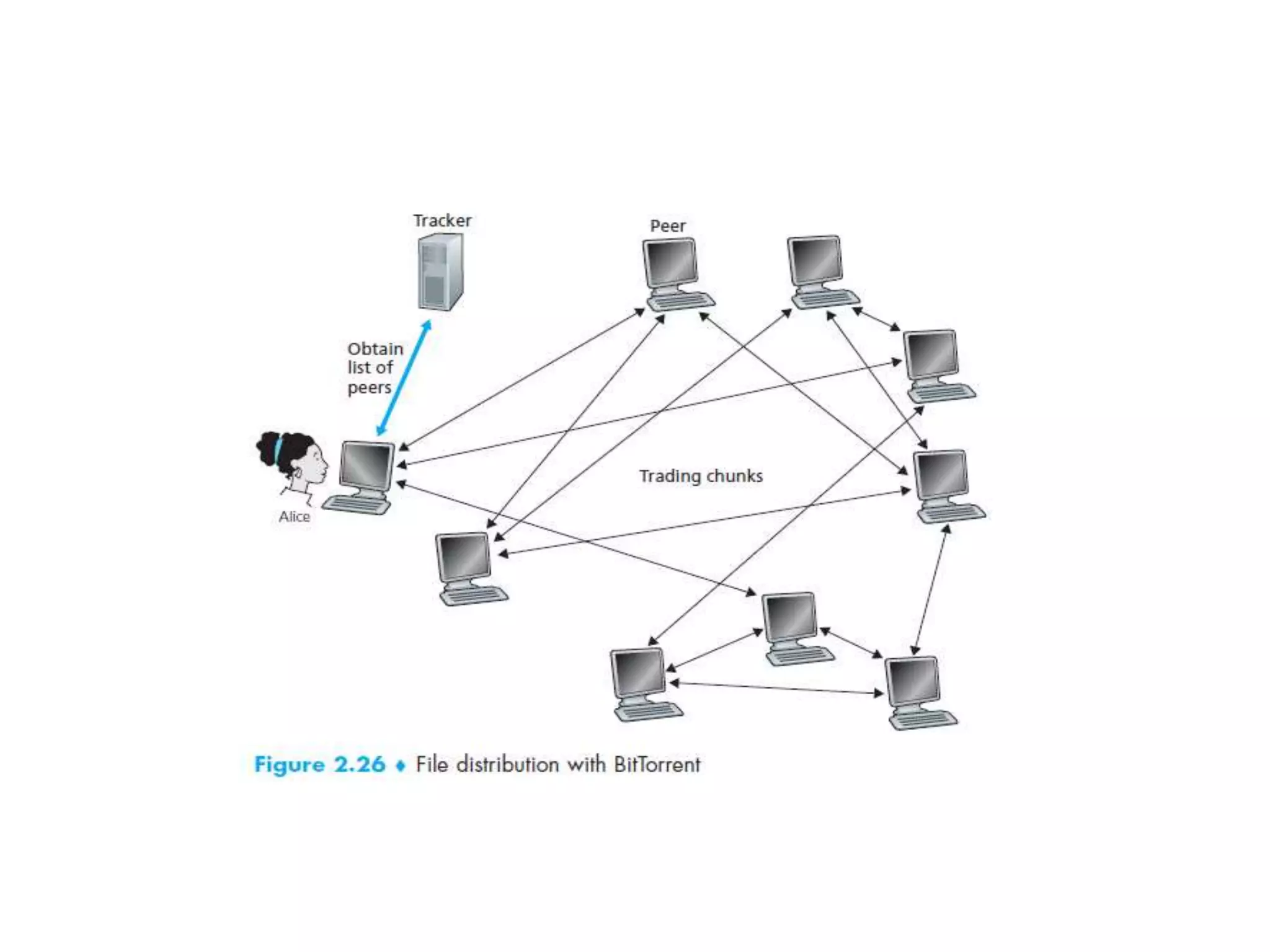
This document discusses principles of network applications. It describes how network applications involve programs running on different end systems that communicate over a network. It provides examples of the browser and web server communicating in a web application, and programs sharing files in a P2P system. The document outlines that when developing a new application, software must be written to run on multiple end systems, and can be written in languages like C, Java or Python. It also describes processes communicating by exchanging messages, and different network application architectures like client-server and peer-to-peer.